2013-07-14 - DOTKACHEF EXPLOIT KIT FROM 209.240.135[.]142 - WWW.LAPOSTGROUP[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-07-14-DotkaChef-EK-traffic.pcap.zip 209.7 kB (209,731 bytes)
- 2013-07-14-DotkaChef-EK-malware.zip 463.0 kB (463,004 bytes)
NOTES:
- This was my third blog entry, back when I began documenting exploit kit (EK) traffic, and I didn't realize this was DotkaChef EK.
- This PCAP is dated 2013-07-15 in UTC, which was 2013-07-14 Central time in the US (which is why this blog entry is dated 2013-07-14).
- On 2014-09-20, I updated this blog entry with more information, and changed the format to how I now report on EK traffic.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 184.72.236[.]84 - www.programmersheaven[.]com - Web site that was first viewed
- 75.101.156[.]151 - ads.communityheaven[.]com - Ad traffic with JJencoded script
- 103.31.186[.]24 - anava[.]biz - Redirect
- 209.240.135[.]142 - www.lapostgroup[.]com - DotkaChef EK
COMPROMISED WEBSITE AND REDIRECT:
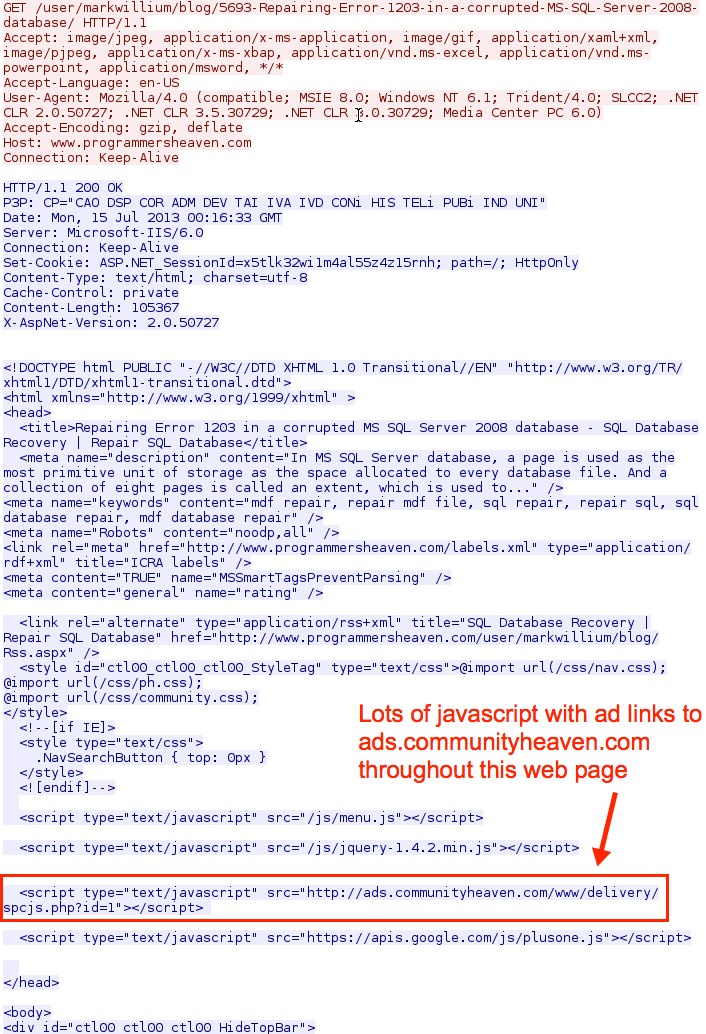
- 00:16:32 - 184.72.236[.]84 - www.programmersheaven[.]com - GET /user/markwillium/blog/5693-Repairing-Error-1203-in-a-corrupted-MS-SQL-Server-2008-database/
- 00:16:33 - 75.101.156[.]151 - ads.communityheaven[.]com - GET /www/delivery/spc.php?zones=1%7C2[long string of characters]
- 00:16:33 - 75.101.156[.]151 - ads.communityheaven[.]com - GET /www/delivery/[various other HTTP GET requests]
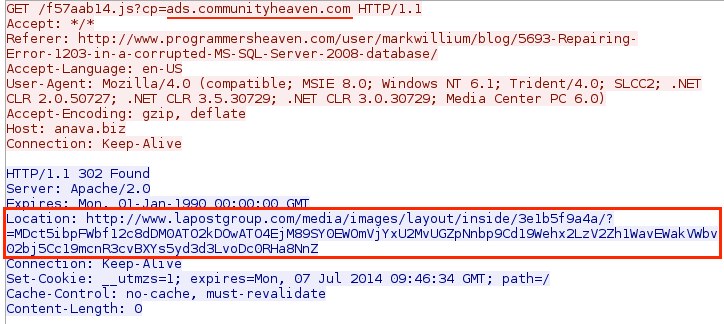
- 00:16:34 - 103.31.186[.]24 - anava[.]biz - GET /f57aab14.js?cp=ads.communityheaven[.]com
DOTKACHEF EK:
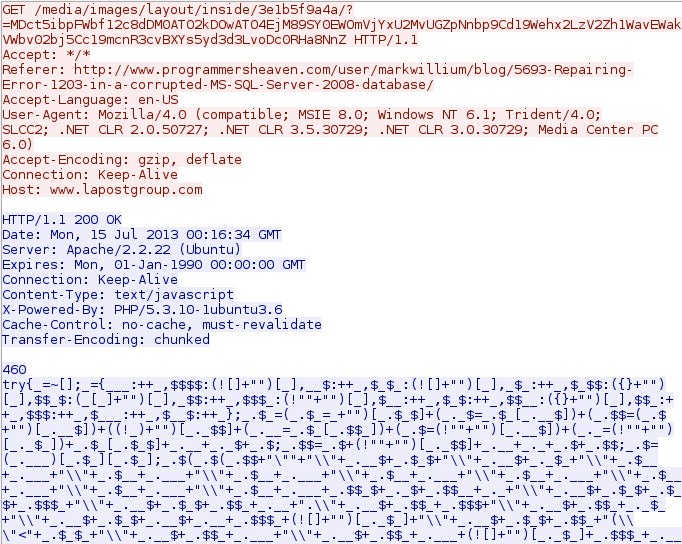
- 00:16:35 - 209.240.135[.]142 - www.lapostgroup[.]com - GET /media/images/layout/inside/3e1b5f9a4a/?=MDct5ibpFWbf12c8dDM0ATO2kDOwATO4EjM89SY0EWOm
VjYxU2MvUGZpNnbp9Cd19Wehx2LzV2Zh1WavEWakVWbv02bj5Cc19mcnR3cvBXYs5yd3d3LvoDc0RHa8NnZ - 00:16:47 - 209.240.135[.]142 - www.lapostgroup[.]com - GET /media/images/layout/inside/3e1b5f9a4a/?f=s&k=2189008969040714
- 00:16:47 - 209.240.135[.]142 - www.lapostgroup[.]com - GET /media/images/layout/inside/3e1b5f9a4a/?f=s&k=2189008969040714
- 00:16:47 - 209.240.135[.]142 - www.lapostgroup[.]com - GET /media/images/layout/inside/3e1b5f9a4a/?f=s&k=2189008969040714
- 00:16:47 - 209.240.135[.]142 - www.lapostgroup[.]com - GET /media/images/layout/inside/3e1b5f9a4a/?f=s&k=2189008969040714
- 00:16:48 - 209.240.135[.]142 - www.lapostgroup[.]com - GET /media/images/layout/inside/3e1b5f9a4a/?f=s&k=2189008969040714
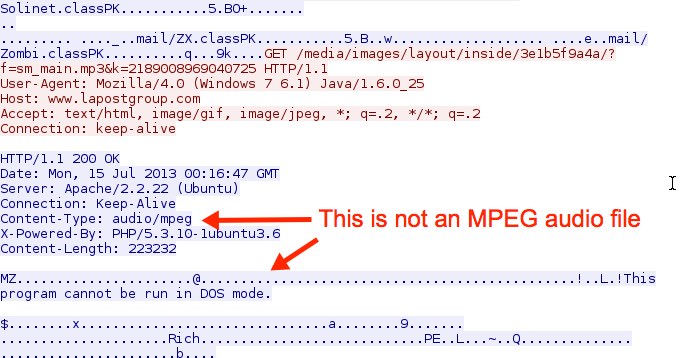
- 00:16:48 - 209.240.135[.]142 - www.lapostgroup[.]com - GET /media/images/layout/inside/3e1b5f9a4a/?f=sm_main.mp3&k=2189008969040725
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT:
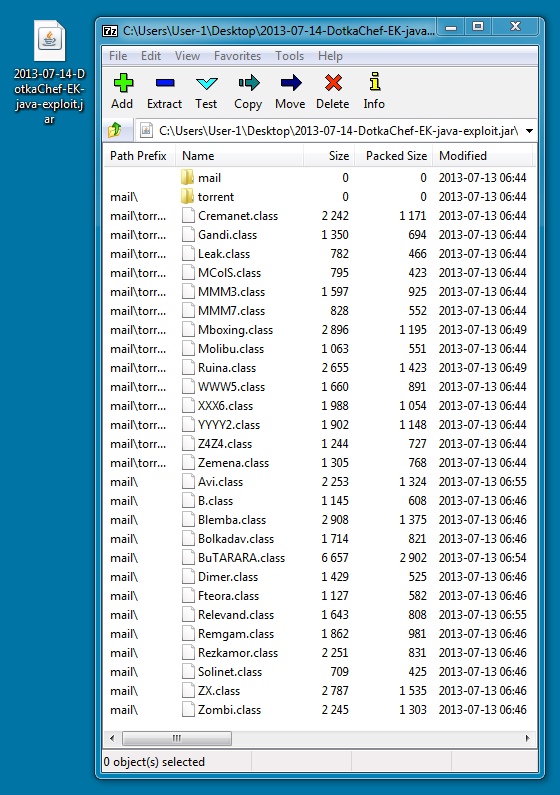
File name: 2013-07-14-DotkaChef-EK-java-exploit.jar
File size: 29.4 KB ( 29,376 bytes )
First submission: 2013-07-13 16:41:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/8e2bfb0f7d7955d086a7ca0ef221caf3a360fa1d396d26fc19557c5410ca5319/analysis/
MALWARE PAYLOAD:
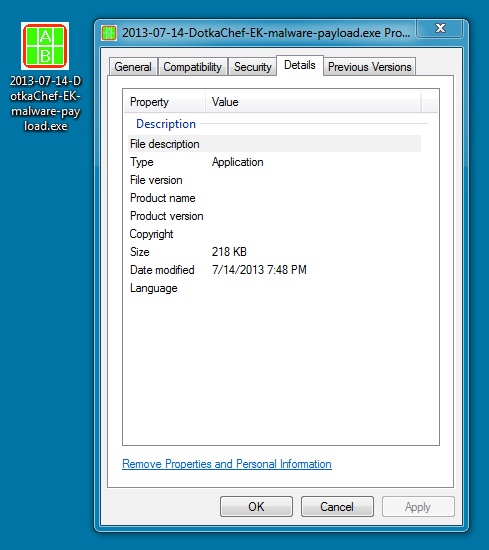
File name: 2013-07-14-DotkaChef-EK-malware-payload.exe
File size: 223.2 KB ( 223,232 bytes )
First submission: 2013-07-15 00:49:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/75941c19409c3c616bd1159fb192efe108bf188f01471c4df95b2b42ba817ddc/analysis/
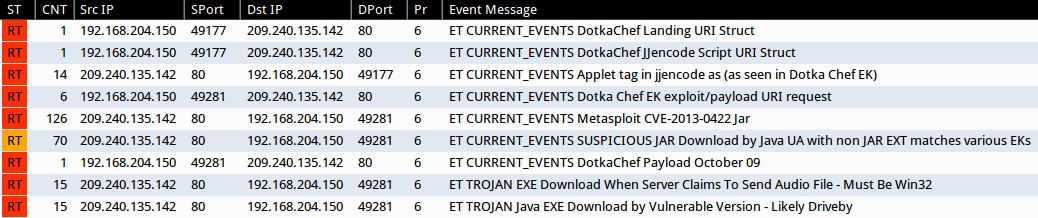
SIGNATURE HITS
Screenshot of Emerging Threats signature hits from Sguil on Security Onion (without ET POLICY or ET INFO events):
SCREENSHOTS FROM THE TRAFFIC
Page from the website that was first viewed:
Redirect (gate) pointing to DotkaChef EK landing page:
DotkaChef EK landing page:
DotkaChef EK delivering the java exploit:
DotkaChef EK delivering the malware payload:
Click here to return to the main page.