2013-07-28 - EMAIL ATTACHMENT LEADS TO MALWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-07-28-malware-infection-from-email-attahcment.pcap.zip 1.5 MB (1,543,237 bytes)
- 2013-07-28-email-example-and-malware.zip 582.4 kB (582,381 bytes)
2025 UPDATE:
- I included a sanitized copy of an email with the same malware attachment, which is now in the email and malware archive.
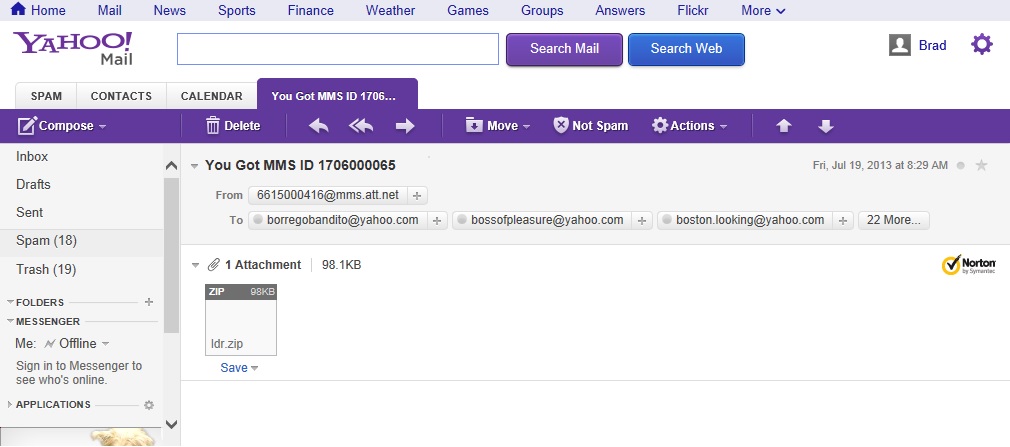
It's been a while since I received a malicious email, so when one appeared in a Yahoo webmail, it provided an opportunity for a blog post. This email had a malware attachment. Here's a screen shot of the email in my spam folder:
Let's find out where this email came from and what would happen if someone were to execute the attachment...
THE EMAIL
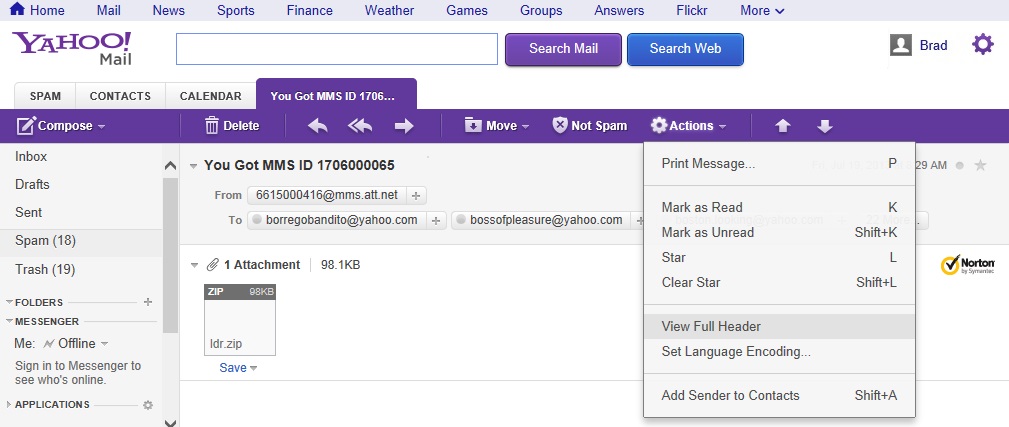
If you want to find out where an email came from, you need to look at the header for the message. For Yahoo webmail, go to "Actions" and select "View Full Header" as shown below:
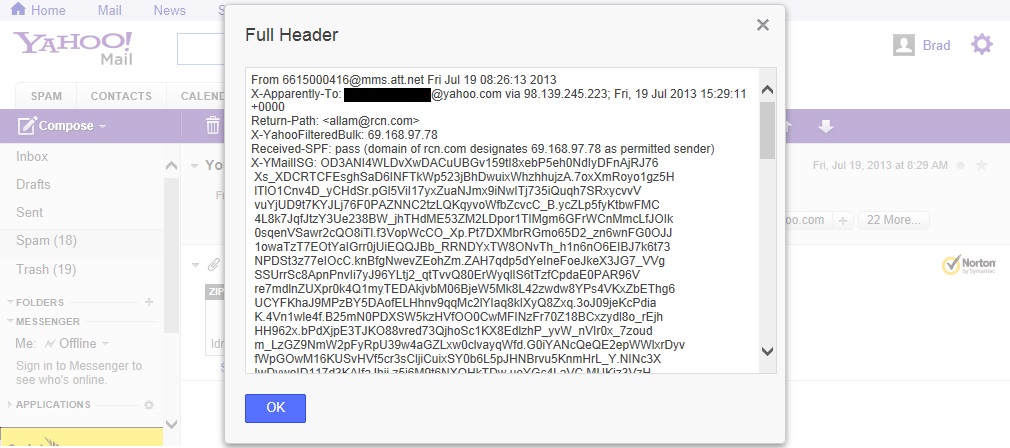
This brings up a window with the full header that you select, copy, and paste into a text editor.
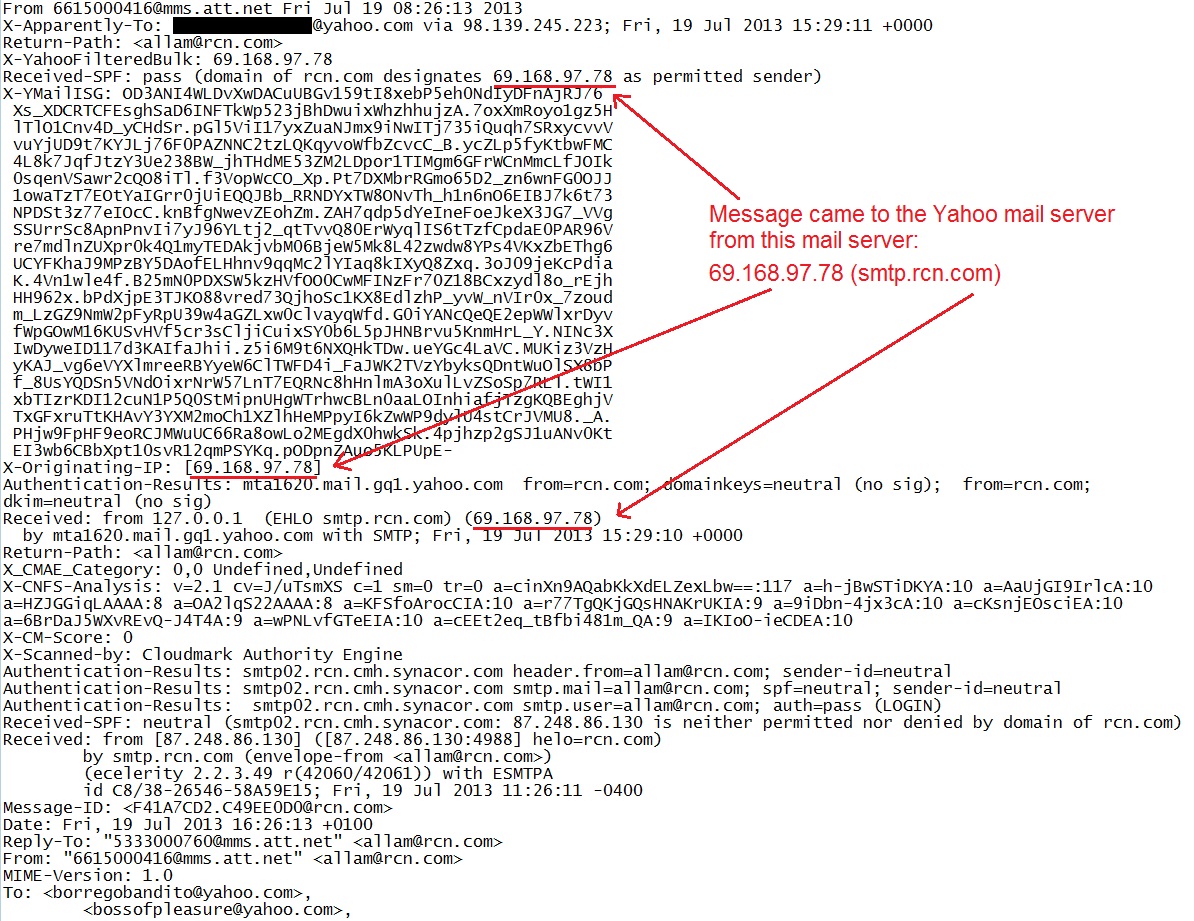
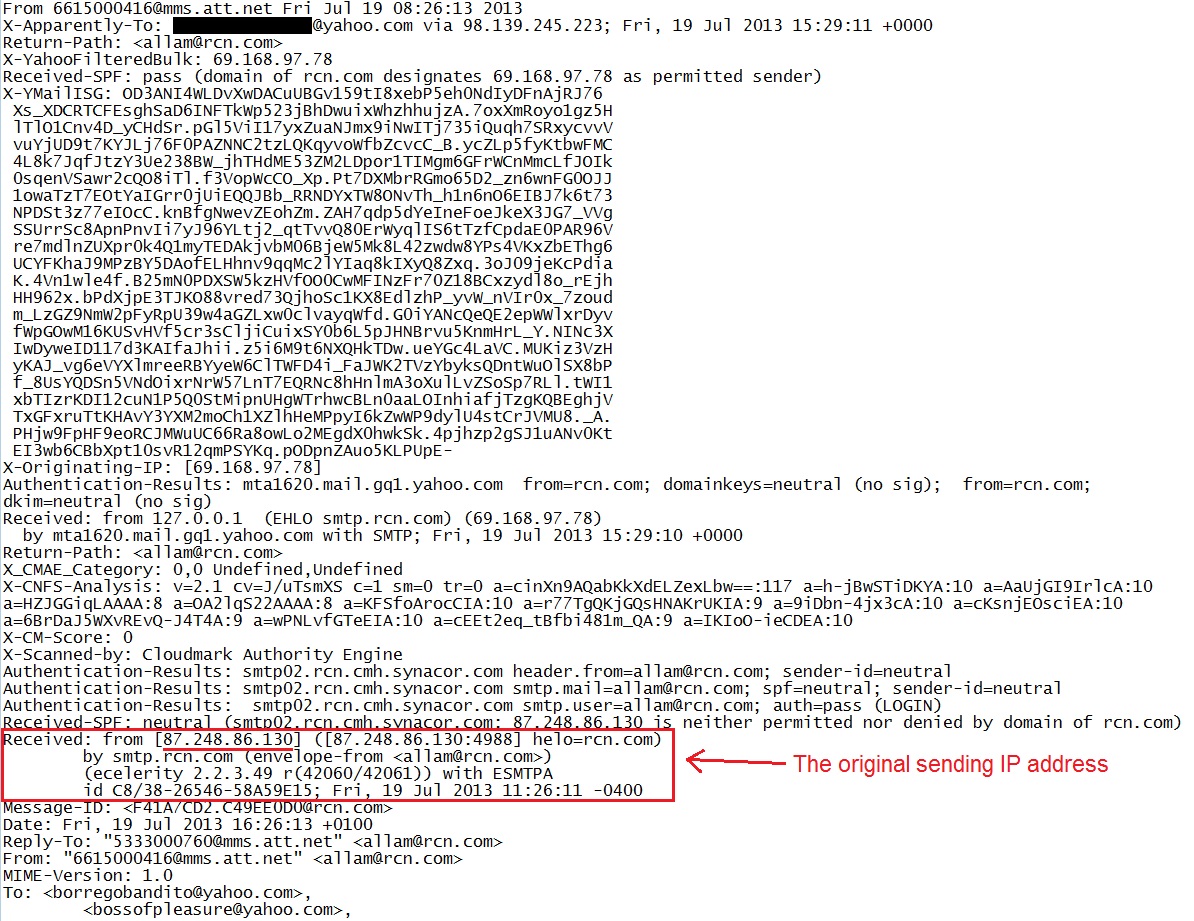
Once you copy and paste the text into a text editor, you can view the header lines much easier. As shown below, this email came from a mail server at 69.149.97[.]78 which is assigned to smtp.rcn[.]com.
However, this is not the original source of the message. An email can pass through one or more mail servers before it reaches its final destination. You can find the original sending IP address by looking for all of the "Received:" lines and finding the first one. According to the current standard for SMTP, RFC 5321, "An Internet mail program MUST NOT change or delete a Received: line that was previously added to the message header section" (Section 4.4).
As shown below, there are two "Received:" lines. The first one was Friday, 19 Jul 2013 at 15:26:11 GMT (11:26:11 -0400) while the second line has a time of 15:29:10 GMT. The first "Received:" line has 87.249.16.130 as the sending IP address, which is the original sender.
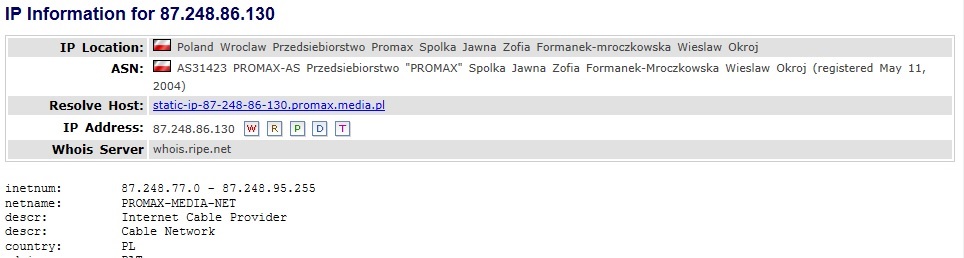
Who is the original sender? A whois check shows 87.249.16[.]130 is a Polish IP address that belongs to an Internet service provider.
We've figured out the origin of this phishing email, so let's examine the malware.
THE MALWARE
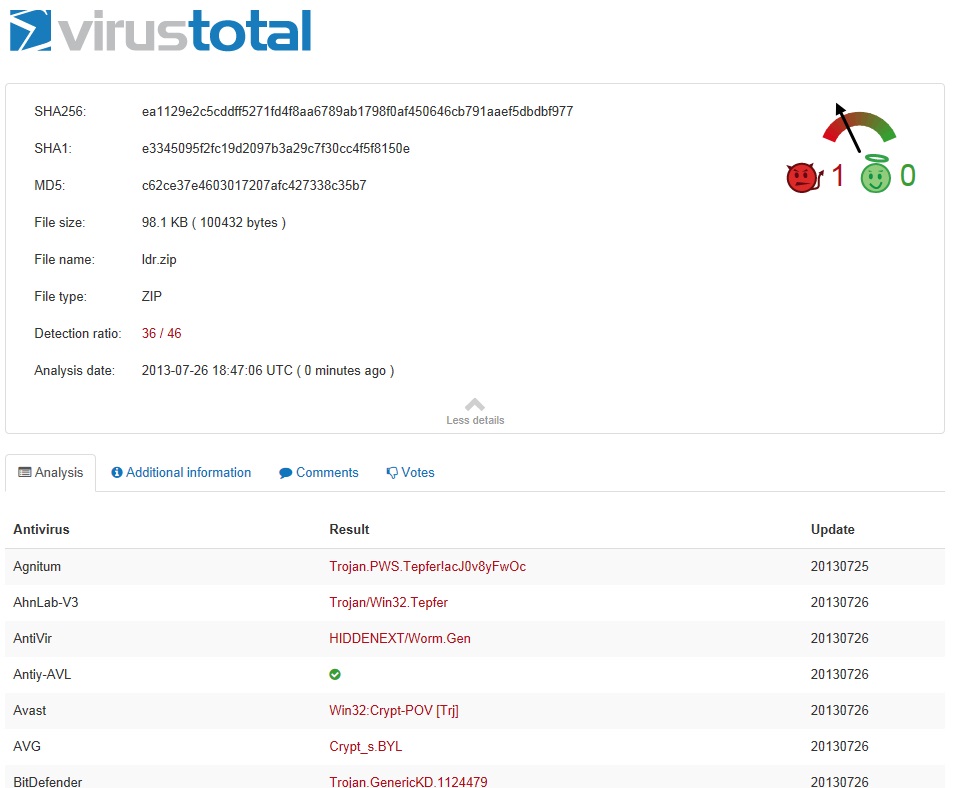
A quick check of the attachment ldr.zip on VirusTotal shows it's fairly-well identified as malware.
If you open the zip archive, it shows a file named Photo_19.07.2013_ID3698006402.jpeg.exe. Since Windows default settings hide the file extension, you might not see the ".exe" file extension. The file has an icon for a PDF file, even though it appears to be masquerading as a JPEG.
TRAFFIC GENERATED BY THE MALWARE
I ran the malware on a default Windows 7 SP 1 computer (a physical host, not a VM) that was monitored by another host with a default installation of Security Onion. This malware generated three Snort-based events as shown below:
- ET TROJAN Fareit/Pony Downloader Checkin 2
- ET INFO Executable Download from dotted-quad Host
- ET POLICY PE EXE or DLL Windows file download
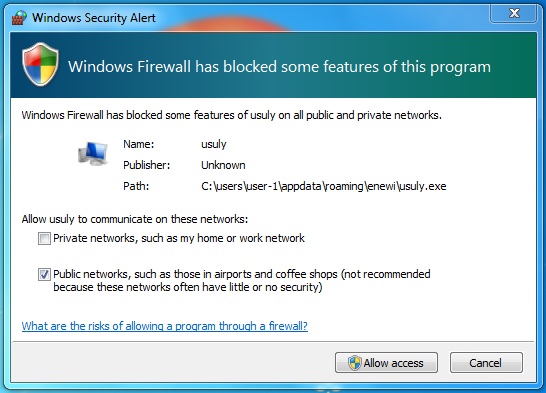
When running the malware on the Windows computer, a Windows firewall alert popped up:
The malware generated the following DNS requests:
- nursenextdoor[.]com ( resolved to 209.15.210[.]130 )
- dreamonseniorswish[.]org ( resolved to 209.15.120[.]130 )
- prospexleads[.]com ( no resolution, Server failure )
- phonebillssuck[.]com ( resolved to 50.57.171[.]207 )
- staggmarine[.]com ( resolved to 198.57.193[.]220 )
- www.fixingsocialsecurity[.]org ( resolved to 207.150.212[.]69 )
- www.keurslager-demeulder[.]be ( resolved to 176.62.165[.]177 )
I recorded the traffic approximately 10 minutes after executing the malware. It generated the following traffic:
- 209.15.210[.]130 ( nursenextdoor[.]com ) port 443 - responded with RST to each SYN segment sent. No connection established
- 209.15.210[.]130 ( dreamonseniorswish[.]org ) port 443 - responded with RST to each SYN segment sent. No connection established
- Several DNS queries on prospexleads[.]com
- 50.57.171[.]207 ( phonebillssuck[.]com ) port 8080 - POST /forum/viewtopic.php HTTP/1.0
- HTTP/1.1 200 OK (text/html)
- 80.74.139[.]60 ( no domain, just the IP address ) port 80 - GET /2Tv.exe HTTP/1.0
- HTTP/1.1 404 Not Found (text/html)
- 198.57.193[.]220 ( staggmarine[.]com ) port 80 - GET /JP8.exe HTTP/1.0
- HTTP/1.1 404 Not Found (text/html)
- 207.150.212[.]69 ( www.fixingsocialsecurity[.]org ) port 80 - GET /Dam.exe HTTP/1.0
- HTTP/1.1 200 OK (application/x-msdownload)
- 176.62.165[.]177 ( www.keurslager-demeulder[.]be ) port 80 - GET /1ivvH7dR.exe HTTP/1.0
- HTTP/1.1 404 Not Found (text/html)
- UDP traffic to 66 different IP addresses, with some examples shown below:
- UDP traffic - infected host port 6376 - 196.210.183[.]125 port 64673
- UDP traffic - infected host port 6376 - 64.179.175[.]117 port 8321
- UDP traffic - infected host port 6376 - 81.29.247[.]130 port 2734
- UDP traffic - infected host port 6376 - 83.228.15[.]193 port 16115
- UDP traffic - infected host port 6376 - 107.210.68[.]185 port 7286
- UDP traffic - infected host port 6376 - 130.251.186[.]103 port 8650
- UDP traffic - infected host port 6376 - 71.43.167[.]82 port 4598
- UDP traffic - infected host port 6376 - 24.172.32[.]162 port 3489
- UDP traffic - infected host port 6376 - 98.95.183[.]150 port 5323
- UDP traffic - infected host port 6376 - 217.114.113[.]148 port 8355
- UDP traffic - infected host port 6376 - 216.21.197[.]54 port 5930
- UDP traffic - infected host port 6376 - 78.134.87[.]163 port 5570
- UDP traffic - infected host port 6376 - 176.73.27[.]48 port 1759
- UDP traffic - infected host port 6376 - 108.94.123[.]69 port 7866
- UDP traffic - infected host port 6376 - 108.199.157[.]71 port 8003
- UDP traffic - infected host port 6376 - 220.241.89[.]237 port 2958
- UDP traffic - infected host port 6376 - 107.217.117[.]139 port 8593
- UDP traffic - infected host port 6376 - 50.158.14[.]182 port 1779
- UDP traffic - infected host port 6376 - 122.164.122[.]108 port 2379
- UDP traffic - infected host port 6376 - 178.238.233[.]29 port 9710
- UDP traffic - infected host port 6376 - 99.73.92[.]101 port 1879
- TCP traffic - infected host port 49188 - 178.238.233[.]29 port 9407
- TCP traffic - infected host port 49190 - 188.190.3[.]153 port 5610
- TCP traffic - infected host port 49191 - 188.190.3[.]153 port 5610
- TCP traffic - infected host port 49193 - 58.177.94[.]220 port 5939
- TCP traffic - infected host port 49197 - 89.205.37[.]79 port 7232
- TCP traffic - infected host port 49199 - 188.190.3[.]153 port 5610
The HTTP POST to www.phonebillssuck[.]com occurred when the malware checked in. The malware appears to be a downloader, and it generated four HTTP GET requests for more malware. Only one of these was successful--the request GET /Dam.exe returned a malicious EXE file. The post-infection UDP and TCP traffic appears to be endoced or otherwise encrypted.
VIRUS TOTAL RESULTS ON THE MALWARE
File name: Photo_19.07.2013_ID3698006402.jpeg.exe
File size: 122.9 KB ( 122,880 bytes )
File name: Dam.exe
File size: 310.8 KB ( 310,784 bytes )
FINAL NOTES
In this blog entry, we examined an email with a malicious attachment. We examined the email and reviewed some of the traffic generated by the malware.
Click here to return to the main page.