2013-12-27 - STYX EXPLOIT KIT DELIVERS SIMDA MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2013-12-27-Styx-EK-traffic.pcap.zip 1.6 MB (1,642,771 bytes)
- 2013-12-27-Styx-EK-malware.zip 1.3 MB (1,336,591 bytes)
NOTES:
Here's a quick post for some malware traffic I captured on the evening of December 26th (27 Dec 2013 in GMT). Someone was looking for pictures of Emma Watson on Google, and one of the search results generated some exploit traffic. Fortunately, the user's computer wasn't infected. I replicated the search in a vulnerable VM, saw a Styx exploit kit deliver a CVE 2013-2460 exploit, and witnessed a Simda malware infection.
The vulnerable VM was monitored by Security Onion with the Emerging Threats Open signature set. The VM was running a Windows 7 with IE 10 and Java 7 update 15.
SNORT EVENTS
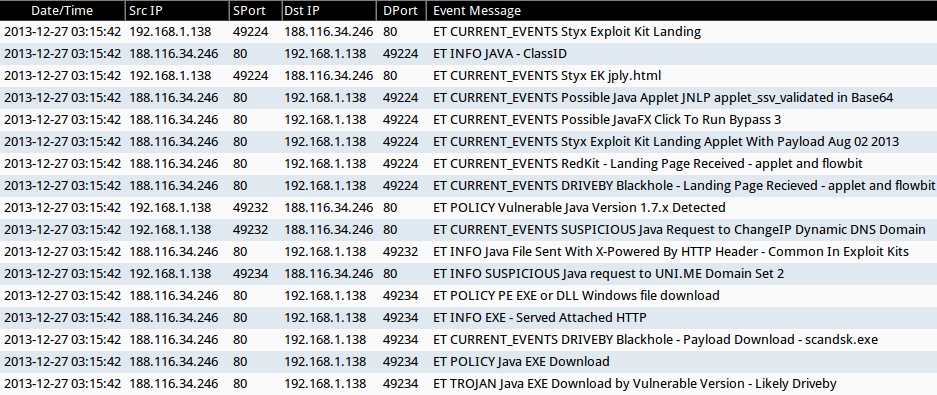
- 192.168.1[.]138 port 49224 -> 188.116.34[.]246 port 80 - ET CURRENT_EVENTS Styx Exploit Kit Landing
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49224 - ET INFO JAVA - ClassID
- 192.168.1[.]138 port 49224 -> 188.116.34[.]246 port 80 - ET CURRENT_EVENTS Styx EK jply.html
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49224 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated in Base64
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49224 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 3
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49224 - ET CURRENT_EVENTS Styx Exploit Kit Landing Applet With Payload Aug 02 2013
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49224 - ET CURRENT_EVENTS RedKit - Landing Page Received - applet and flowbit
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49224 - ET CURRENT_EVENTS DRIVEBY Blackhole - Landing Page Received - applet and flowbit
- 192.168.1[.]138 port 49232 -> 188.116.34[.]246 port 80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 192.168.1[.]138 port 49232 -> 188.116.34[.]246 port 80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to ChangeIP Dynamic DNS Domain
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49232 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 192.168.1[.]138 port 49234 -> 188.116.34[.]246 port 80 - ET INFO SUSPICIOUS Java request to UNI.ME Domain Set 2
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49234 - ET POLICY PE EXE or DLL Windows file download
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49234 - ET INFO EXE - Served Attached HTTP
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49234 - ET CURRENT_EVENTS DRIVEBY Blackhole - Payload Download - scandsk.exe
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49234 - ET POLICY Java EXE Download
- 188.116.34[.]246 port 80 -> 192.168.1[.]138 port 49234 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
INFECTION CHAIN OF EVENTS
ORIGINAL REFERER:
- 03:31:16 - 192.168.1[.]138 port 49209 - 173.194.115[.]80 port 80 - www.google[.]com - GET /url?sa=t&ct=j&q=&esrc=s&source=web&cd=1&ved=0CCwQFjAA&url=http%3A%2F%2Fwww.butch-femme[.]com%2Farchive%2Findex.php%2Ft-7747.html&[long string]
A SERIES OF REDIRECTS:
- 03:31:17 - 192.168.1[.]138 port 49220 - 66.225.230[.]141 port 80 - www.butch-femme[.]com - GET /archive/index.php/t-7747.html
- 03:31:17 - 66.225.230[.]141 port 80 - 192.168.1[.]138 port 49220 - HTTP/1.1 302 Moved Temporarily
- 03:31:17 - 192.168.1[.]138 port 49219 - 93.170.131[.]2 port 80 - gqillqigqilqigqiqlqiigqilqiiiqgg.esmtp[.]biz - GET /1.php
- 03:31:17 - 93.170.131[.]2 port 80 - 192.168.1[.]138 port 49219 - HTTP/1.1 302 Found
- 03:31:18 - 192.168.1[.]138 port 49223 - 194.116.187[.]24 port 80 - bholaschildrenfoundation[.]com - GET /cache/joomfish-cache/cache.php
- 03:31:18 - 194.116.187[.]24 port 80 - 192.168.1[.]138 port 49223 - HTTP/1.1 302 Moved Temporarily
- 03:31:18 - 192.168.1[.]138 port 49211 - 74.220.203[.]53 port 80 - answers-to[.]com - GET /includes/domit/1.php
- 03:31:18 - 74.220.203.53 port 80 - 192.168.1[.]138 port 49211 - HTTP/1.1 302 Moved Temporarily
- 03:31:18 - 192.168.1[.]138 port 49218 - 146.255.46[.]1 port 80 - uskana[.]tv - GET /web/administrator/help/en-GB/css/all4.php
- 03:31:19 - 146.255.46[.]1 port 80 - 192.168.1[.]138 port 49218 - HTTP/1.1 302 Moved Temporarily
- 03:31:19 - 192.168.1[.]138 port 49222 - 93.95.103.12 port 80 - essnk.ru - GET /templates/madeyourweb/1.php?uid=11860
- 03:31:19 - 93.95.103.12 port 80 - 192.168.1[.]138 port 49222 - HTTP/1.1 302 Found
- 03:31:19 - 192.168.1[.]138 port 49212 - 188.116.34[.]246 port 80 - www3.k88t9rilh62bvw1nu39.4pu[.]com - GET /?vfoiwabm=mtbYzbSUiOLUnHWlaqqfnI6ipZ%2BjqVfi6Z92qpejn6qRmqOkbpyY&208a6d38=%01%01%01%01%08%02%08%00%08%07
- 03:31:19 - 188.116.34[.]246 port 80 - 192.168.1[.]138 port 49212 - HTTP/1.1 302 Moved Temporarily
EXPLOIT DOMAIN TRAFFIC:
- 03:31:19 - 192.168.1[.]138 port 49224 - 188.116.34[.]246 port 80 - www1.v5ipk3gc8hug1du9459.4pu[.]com - GET /mdpgg?z3okclu3b7=npXZ[very long string]
- 03:31:19 - 188.116.34[.]246 port 80 - 192.168.1[.]138 port 49224 - HTTP/1.1 200 OK (text/html)
- 03:31:19 - 192.168.1[.]138 port 49224 - 188.116.34[.]246 port 80 - www1.v5ipk3gc8hug1du9459.4pu[.]com - GET /ff464b.js
- 03:31:20 - 188.116.34[.]246 port 80 - 192.168.1[.]138 port 49224 - HTTP/1.1 200 OK (text/javascript)
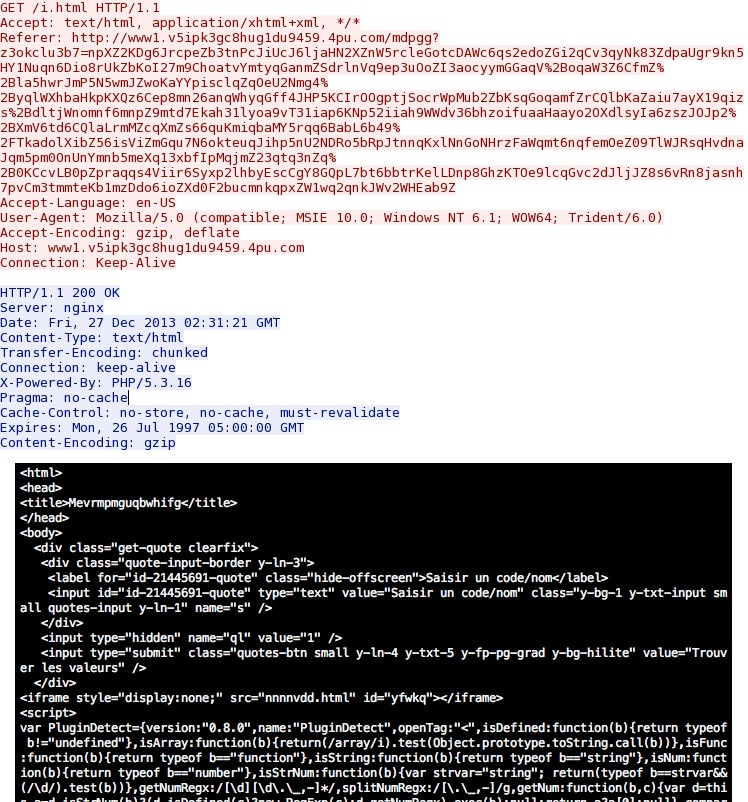
- 03:31:21 - 192.168.1[.]138 port 49224 - 188.116.34[.]246 port 80 - www1.v5ipk3gc8hug1du9459.4pu[.]com - GET /i.html
- 03:31:21 - 188.116.34[.]246 port 80 - 192.168.1[.]138 port 49224 - HTTP/1.1 200 OK (text/html)
- 03:31:21 - 192.168.1[.]138 port 49224 - 188.116.34[.]246 port 80 - www1.v5ipk3gc8hug1du9459.4pu[.]com - GET /nnnnvdd.html
- 03:31:21 - 188.116.34[.]246 port 80 - 192.168.1[.]138 port 49224 - HTTP/1.1 200 OK (text/html)
- 03:31:26 - 192.168.1[.]138 port 49224 - 188.116.34[.]246 port 80 - www1.v5ipk3gc8hug1du9459.4pu[.]com - GET /jply.html
- 03:31:26 - 188.116.34[.]246 port 80 - 192.168.1[.]138 port 49224 - HTTP/1.1 200 OK (text/html)
JAVA EXPLOIT:
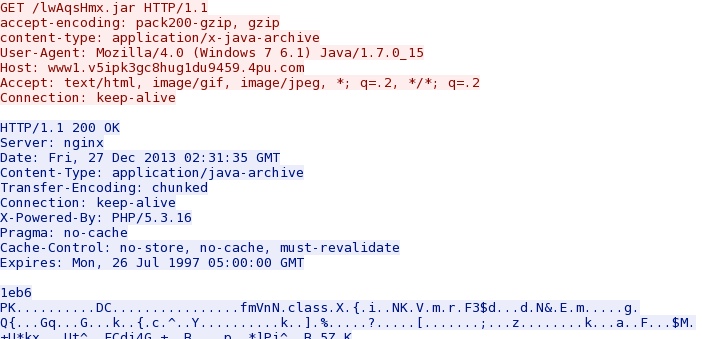
- 03:31:35 - 192.168.1[.]138 port 49232 - 188.116.34[.]246 port 80 - www1.v5ipk3gc8hug1du9459.4pu[.]com - GET /lwAqsHmx.jar
- 03:31:35 - 188.116.34[.]246 port 80 - 192.168.1[.]138 port 49233 - HTTP/1.1 200 OK (application/java-archive)
PAYLOAD (MALICIOUS EXE FILE):
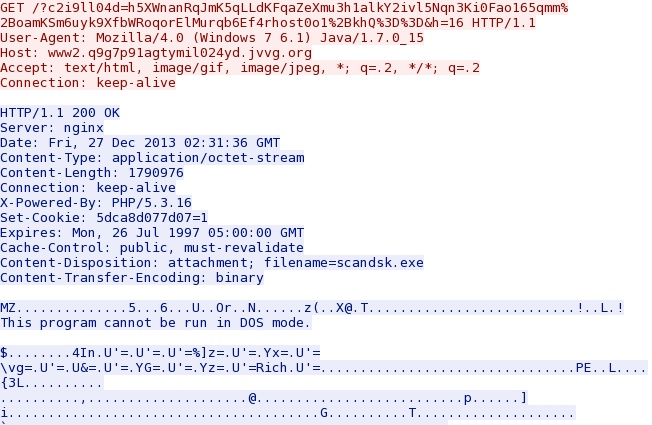
- 03:31:36 - 192.168.1[.]138 port 49234 - 188.116.34[.]246 port 80 - www2.q9g7p91agtymil024yd.jvvg.org - GET /?c2i9ll04d=h5XWnanRqJmK5qLLdKFqaZeXmu3h1alkY2ivl5Nqn3Ki0Fao165qmm%2BoamKSm6uyk9XfbWRoqorElMurqb6Ef4rhost0o1%2BkhQ%3D%3D&h=16
- 03:31:39 - 188.116.34[.]246 port 80 - 192.168.1[.]138 port 49234 - HTTP/1.1 200 OK (application/octet-stream)
TRAFFIC HIGHLIGHTS
Here's the Styx exploit landing page:
Here's the Java exploit (JAR file), apparently based on CVE-2013-2460:
Here's the malicious EXE delivered by the Java exploit:
PRELIMINARY MALWARE ANALYSIS
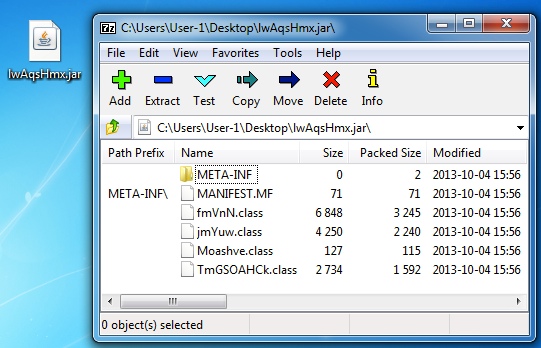
Java exploit used in this Styx EK traffic:
SHA256 hash: 3cdd8c6019b54233b5ed20d063f9b60c1facc948e398b90dca9d103e43d83e19
File name: lwAqsHmx.jar File size: 8.0 KB ( 7,997 bytes )
First submitted: 2013-10-31 00:02:35 GMT
Java archive contents:
According to Virus Total, this is probably a CVE-2013-2460 Java exploit.
EXE payload delivered by the Java exploit:
SHA256 hash: 1d002272794d91c5c2d3a8c7610b030b379307d0499fbc88310125d1bd245024
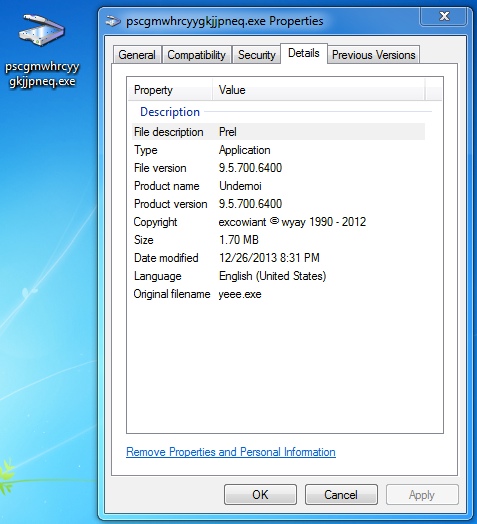
File name: pscgmwhrcyygkjjpneq.exe File size: 1.7 MB ( 1,790,976 bytes )
First submitted: 2013-12-27 03:51:13 GMT
Malware icon and details:
The Virus Total results indicate this is a version of Simda, a backdoor Trojan and/or password stealer.
Click here to return to the main page.