2014-01-30 - INFECTION FROM ATTACHMENT IN ASPROX BOTNET EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-01-30-infection-traffic-from-attachment-in-Asprox-botnet-email.pcap.zip
- 2014-01-30-malware-from-the-infection.zip
NOTES:
For this blog entry, I infected a physical host with malware from an Asprox botnet email sent on 27 Jan 2014. The infected host became part of the botnet and sent more Asprox emails.
Let's take a closer look at what happened...
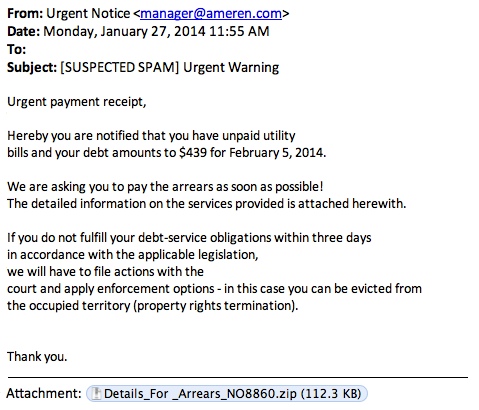
ASPROX BOTNET EMAIL FROM 27 JAN 2014
Here's one of the emails that came through on 27 Jan 2014:
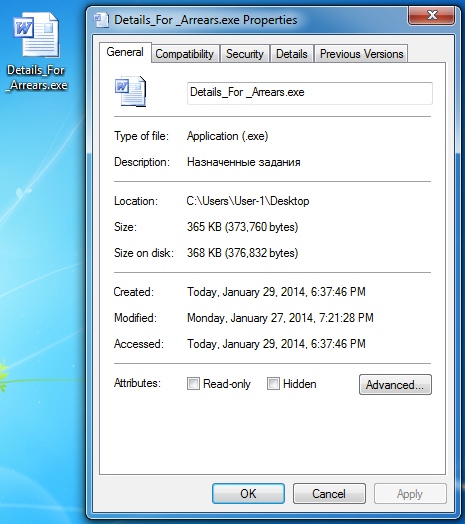
Here's the malware EXE extracted from the attachment:
INFECTING A HOST ON WEDNESDAY EVENING, 29 JAN 2014
The alerts shown below from Security Onion are in UTC, while the pcap shows my local time (US central time zone):
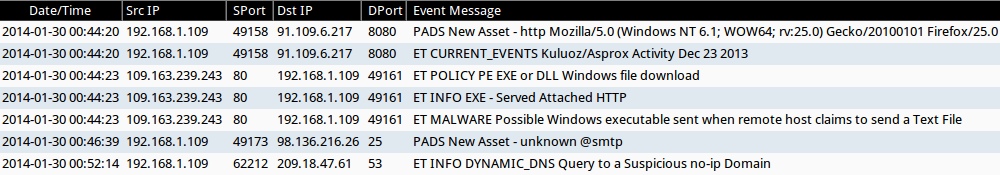
Here are highlights from the traffic as the host became infected (all times GMT):
- 00:44:20 UTC - 91.109.6[.]217:8080 - no domain - POST /763012C7B352704311B5D92CD06A884C2116DE79AE
- 00:44:20 UTC - HTTP/1.1 200 OK
- 00:44:22 UTC - 91.239.15[.]212:80 - net-translscl[.]com - GET /b/shoe/159
- 00:44:23 UTC - HTTP/1.1 404 Not Found
- 00:44:23 UTC - 109.163.239[.]243:80 - bee-smoka[.]com - GET /libs30.15/jquery/
- 00:44:24 UTC - HTTP/1.1 200 OK (text/plain)
- 00:46:31 UTC - 78.46.240[.]107:8080 - no domain - POST /cb/board.pl
- 00:46:32 UTC - HTTP/1.1 200 OK
- 00:47:37 UTC - 188.0.91[.]16:80 - presto-uniel[.]com - GET /b/eve/acbb88d5bb1755d71952f9ac
- 00:47:40 UTC - HTTP/1.1 200 OK (text/html)
- 00:52:08 UTC - 50.31.146[.]101:8080 - no domain - POST /cb/board.pl
- 00:52:08 UTC - HTTP/1.1 200 OK
- 00:55:46 UTC - 5.228.165[.]172:80 - presto-uniel[.]com - POST /b/opt/EF662A19043ECF1413921216
- 00:55:56 UTC - HTTP/1.1 200 OK (text/html)
- 00:55:56 UTC - 5.228.165[.]172:80 - presto-uniel[.]com - GET /b/letr/DD782227D0AB9925C7074427
- 00:56:12 UTC - HTTP/1.1 200 OK (application/octet-stream)
- 00:56:12 UTC - 5.228.165[.]172:80 - presto-uniel[.]com - POST /b/opt/5F1A7708B17DC063A6D11D61
- 00:56:28 UTC - HTTP/1.1 200 OK (text/html)
- 00:56:29 UTC - 5.228.165[.]172:80 - presto-uniel[.]com - GET /b/letr/9F78D7B2E2AE774DF502AA4F
- 00:57:05 UTC - HTTP/1.1 200 OK (application/octet-stream)
MALWARE DROPPED DURING THE ORIGINAL INFECTION
This is where the original malware copied itself after it was executed:
Path and file name: C:\Users\[username]\AppData\Local\irtjggll.exe
File size: 373,760 bytes
MD5 hash: 0ccb0f978a9a9066a22534ac108c6ef1
Time created: 2014-01-30 00:42:17 GMT
After a quick look, I found these EXE files within the user's AppData directory:
Path and file name: C:\Users\[username]\AppData\Local\lxrqqowx.exe
File size: 77,824 bytes
MD5 hash: 773521dcc3ca8be57e8202ae37cf20dd
Time created: 2014-01-30 00:44:21 GMT
Path and file name: C:\Users\[username]\AppData\Roaming\Vyifiqe\tumeyxk.exe
File size: 298,219 bytes
MD5 hash: 6bffa1c615694909638f68350b396682
Time created: 2014 00:47:34 GMT
Path and file name: C:\Users\[username]\AppData\Local\qpmxbuji.exe
File size: 139,264 bytes
MD5 hash: 7b37752da4193ad2cdfba83f4a98503e
Time created: 2014-01-30 00:48:35 GMT
Path and file name: C:\Users\[username]\AppData\Local\Temp\UpdateFlashPlayer_78a0e7bb.exe
File size: 145,721 bytes
MD5 hash: df5ab239bdf09a8716cabbdfa1d6a724
Time created: 2014-01-30 00:53:15 GMT
Path and file name: C:\Users\[username]\AppData\Local\Temp\UpdateFlashPlayer_9453f040.exe
File size: 298,219 bytes
MD5 hash: b2534de2f7bb39ba7dbee16b6667fabf
Time created: 2014-01-30 00:53:15 GMT
POST INFECTION EMAIL ACTIVITY
The infected host began sending emails at 00:46 UTC, and it made several hundred attempts before I powered down the host. Most of the attempts were denied by the mail servers. The first 2 seconds of the activity saw 48 attempts to send emails.
- 00:46:39 UTC - 184.173.124[.]234:25 - C: MAIL FROM: <service_notice@mnduscourt[.]com>
- 00:46:39 UTC - 74.125.196[.]26:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:39 UTC - 65.55.92[.]184:25 - C: MAIL FROM: <support317@mnduscourt[.]com>
- 00:46:39 UTC - 98.136.216[.]25:25 - C: MAIL FROM: <manager@mnduscourt[.]com>
- 00:46:39 UTC - 98.136.216[.]26:25 - C: MAIL FROM: <service.389@mnduscourt[.]com>
- 00:46:39 UTC - 66.196.118[.]35:25 - C: MAIL FROM: <service_notice@mnduscourt[.]com>
- 00:46:39 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:39 UTC - 98.138.112[.]38:25 - C: MAIL FROM: <manager@mnduscourt[.]com>
- 00:46:39 UTC - 150.70.162[.]143:25 - C: MAIL FROM: <service.601@mnduscourt[.]com>
- 00:46:39 UTC - 65.54.188[.]110:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:39 UTC - 192.185.29[.]98:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:39 UTC - 98.136.217[.]192:25 - C: MAIL FROM: <support.8@mnduscourt[.]com>
- 00:46:39 UTC - 65.54.188[.]110:25 - C: MAIL FROM: <manager@mnduscourt[.]com>
- 00:46:39 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:39 UTC - 74.125.196[.]27:25 - C: MAIL FROM: <notice559@mnduscourt[.]com>
- 00:46:39 UTC - 66.94.25[.]228:25 - C: MAIL FROM: <service_notice@mnduscourt[.]com>
- 00:46:39 UTC - 65.55.92[.]136:25 - C: MAIL FROM: <support317@mnduscourt[.]com>
- 00:46:39 UTC - 65.39.178[.]143:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:39 UTC - 173.194.78[.]26:25 - C: MAIL FROM: <support.8@mnduscourt[.]com>
- 00:46:39 UTC - 98.136.216[.]25:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:39 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <service_notice@mnduscourt[.]com>
- 00:46:39 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <manager@mnduscourt[.]com>
- 00:46:39 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <service.389@mnduscourt[.]com>
- 00:46:39 UTC - 65.55.92[.]168:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:39 UTC - 65.55.92[.]168:25 - C: MAIL FROM: <manager@mnduscourt[.]com>
- 00:46:39 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <manager@mnduscourt[.]com>
- 00:46:39 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:39 UTC - 74.125.196[.]27:25 - C: MAIL FROM: <service.146@mnduscourt[.]com>
- 00:46:39 UTC - 65.54.188[.]110:25 - C: MAIL FROM: <support317@mnduscourt[.]com>
- 00:46:40 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:40 UTC - 65.55.92[.]184:25 - C: MAIL FROM: <manager@mnduscourt[.]com>
- 00:46:40 UTC - 65.55.92[.]184:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:40 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <service.389@mnduscourt[.]com>
- 00:46:40 UTC - 98.136.216[.]25:25 - C: MAIL FROM: <manager@mnduscourt[.]com>
- 00:46:40 UTC - 98.136.216[.]25:25 - C: MAIL FROM: <service_notice@mnduscourt[.]com>
- 00:46:40 UTC - 98.136.216[.]25:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:40 UTC - 98.136.216[.]25:25 - C: MAIL FROM: <support.2@mnduscourt[.]com>
- 00:46:40 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <manager@mnduscourt[.]com>
- 00:46:40 UTC - 98.136.216[.]25:25 - C: MAIL FROM: <support535@mnduscourt[.]com>
- 00:46:40 UTC - 65.55.92[.]168:25 - C: MAIL FROM: <support317@mnduscourt[.]com>
- 00:46:40 UTC - 74.125.196[.]26:25 - C: MAIL FROM: <support.2@mnduscourt[.]com>
- 00:46:40 UTC - 65.54.188[.]110:25 - C: MAIL FROM: <notice533@mnduscourt[.]com>
- 00:46:40 UTC - 65.55.92[.]136:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:40 UTC - 65.55.92[.]136:25 - C: MAIL FROM: <manager@mnduscourt[.]com>
- 00:46:40 UTC - 98.136.216[.]25:25 - C: MAIL FROM: <support.8@mnduscourt[.]com>
- 00:46:40 UTC - 98.136.216[.]25:25 - C: MAIL FROM: <service_notice@mnduscourt[.]com>
- 00:46:40 UTC - 98.136.216[.]25:25 - C: MAIL FROM: <support.5@mnduscourt[.]com>
- 00:46:40 UTC - 66.196.118[.]34:25 - C: MAIL FROM: <support.2@mnduscourt[.]com>
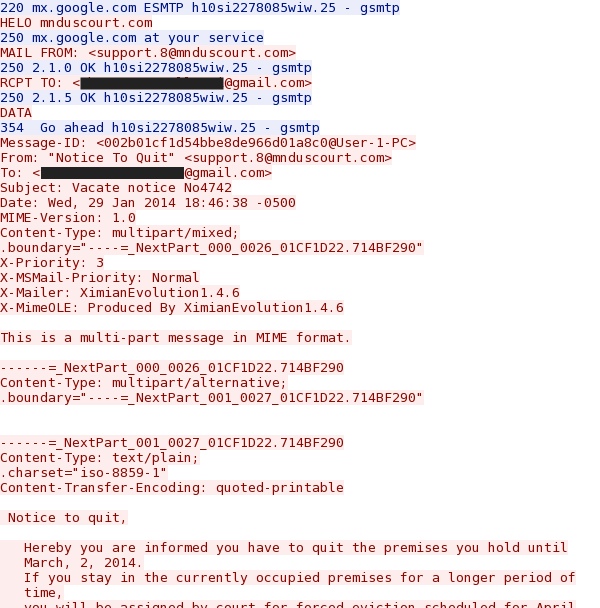
Here's an example of the SMTP traffic from my infected host:
The Google mail server rejected this message...
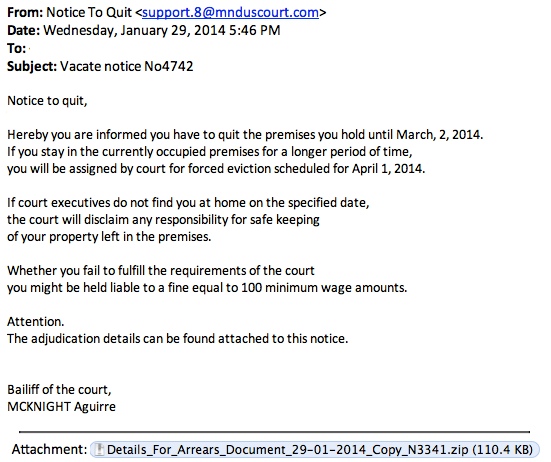
EMAIL SENT BY THE INFECTED HOST
I extracted an email from the SMTP traffic in the pcap to get a better look at the message being sent:
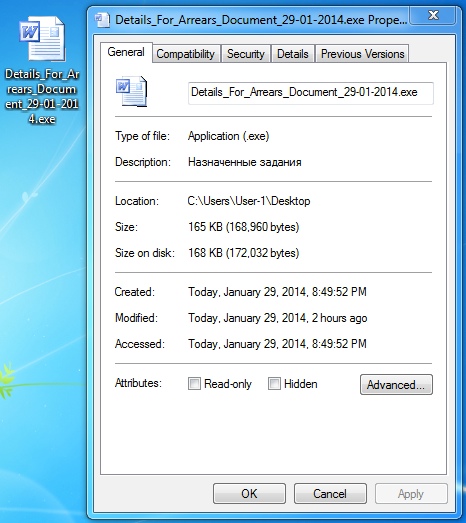
Here's the malware EXE extracted from the attachment:
The file had already been submitted to Virus Total about 8 hours before I submitted my copy:
File name: Details_For_Arrears_Document_29-01-2014.exe
File size: 168,960 bytes
MD5 hash: 3b636be10ba275b0cc7ecfca5fccc85e
VirusTotal link: https://www.virustotal.com/en/file/631f2bcf232bf006976f0c09b38d67b00dd780201771b59692a1acfe05ac478e/analysis/
First submitted: 2014-01-29 19:24:20 GMT
Click here to return to the main page.