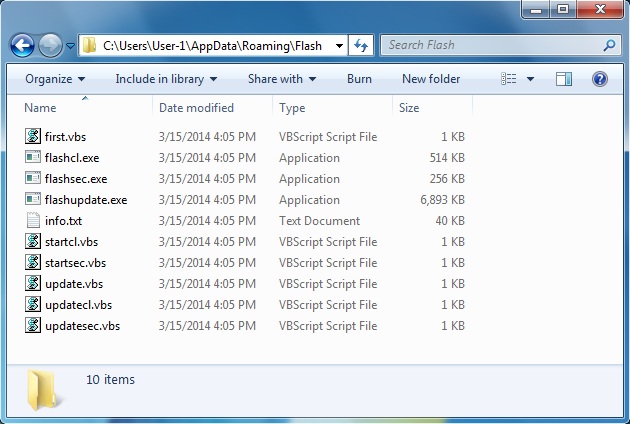
2014-03-15 - STYX EK DROPS SIMDA, BITCOIN MINER, AND MORE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I ran across a link for Styx EK and used it to infect a physical host running Windows 7.
- The image below shows most (but not all) of the post-infection additional malware:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 204.27.57[.]194 - transit.thundernova[.]ca - Styx EK delivering exploit
- 204.27.57[.]194 - 436sfdh.safebrowsing-cant-stop-me[.]info - Styx EK delivering malware payload
- Various IP addresses - various domains - Post-infection traffic (see below)
INITIAL INFECTION BY STYX EK
- 04:05:11 UTC - 204.27.57[.]194:80 - transit.thundernova[.]ca - GET /WcLyBChoVsGiB/i.html
- 04:05:12 UTC - 204.27.57[.]194:80 - transit.thundernova[.]ca - GET /WcLyBChoVsGiB/ToeBzl.html
- 04:05:14 UTC - 204.27.57[.]194:80 - transit.thundernova[.]ca - GET /favicon.ico
- 04:05:19 UTC - 204.27.57[.]194:80 - transit.thundernova[.]ca - GET /WcLyBChoVsGiB/gmkCPZN.jar
- 04:05:19 UTC - 204.27.57[.]194:80 - transit.thundernova[.]ca - GET /WcLyBChoVsGiB/gmkCPZN.jar
- 04:05:20 UTC - 204.27.57[.]194:80 - 436sfdh.safebrowsing-cant-stop-me[.]info - GET /WcLyBChoVsGiB/soft_1.exe&h=14
POST-INFECTION SIMDA.C CHECKIN
- 04:05:25 UTC - 79.142.66[.]240:80 - report.7myws9ei79qg7i31q[.]com - GET /?KUO331=%96%C9%D2%9F%[long string]
- 04:05:25 UTC - 79.142.66[.]240:80 - report.7myws9ei79qg7i31q[.]com - GET /?79a179s43=%96%C9%D2%9F%[long string]
- 04:05:25 UTC - 79.142.66[.]240:80 - report.7myws9ei79qg7i31q[.]com - GET /?317i31q20=%96%C9%D2%9F%[long string]
- 04:05:26 UTC - 79.142.66[.]240:80 - report.7myws9ei79qg7i31q[.]com - GET /?555555i12=%96%C9%D2%9F%[long string]
- 04:05:38 UTC - 79.142.66[.]240:80 - report.7myws9ei79qg7i31q[.]com - GET /?CEIQ13=%96%C9%D2%9F%[long string]
- 04:05:42 UTC - 79.142.66[.]240:80 - report.e17k3y7ce1aaaaaa31[.]com - GET /?17931q931=%96%C9%D2%9F%[long string]
- 04:05:42 UTC - 79.142.66[.]240:80 - report.e17k3y7ce1aaaaaa31[.]com - GET /?QG5543=%96%C9%D2%9F%[long string]
- 04:05:42 UTC - 79.142.66[.]240:80 - report.e17k3y7ce1aaaaaa31[.]com - GET /?C1sK30=%96%C9%D2%9F%[long string]
- 04:05:43 UTC - 79.142.66[.]240:80 - report.e17k3y7ce1aaaaaa31[.]com - GET /?G1i917=%96%C9%D2%9F%[long string]
- 04:05:43 UTC - 79.142.66[.]240:80 - report.e17k3y7ce1aaaaaa31[.]com - GET /?555qG5558=%96%C9%D2%9F%[long string]
- 04:06:19 UTC - 79.142.66[.]240:80 - report.e17k3y7ce1aaaaaa31[.]com - GET /?MY1c55=%96%C9%D2%9F%[long string]
- 04:06:20 UTC - 79.142.66[.]240:80 - report.e17k3y7ce1aaaaaa31[.]com - GET /?MY3157=%96%C9%D2%9F%[long string]
- 04:06:20 UTC - 79.142.66[.]240:80 - report.e17k3y7ce1aaaaaa31[.]com - GET /?O7oC63=%96%C9%D2%9F%[long string]
- 04:06:20 UTC - 79.142.66[.]240:80 - report.e17k3y7ce1aaaaaa31[.]com - GET /?g93aAA18=%96%C9%D2%9F%[long string]
POST-INFECTION CALLBACK FOR ADDITIONAL MALWARE
- 04:05:25 UTC - 5.149.248[.]85:80 - report.7myws9ei79qg7i31q[.]com - POST /
- 04:05:25 UTC - 5.149.248[.]85:80 - update2.53ddc59xb5[.]com - GET /?cd=kdnSlMaplmKTZWqal8Zqb6qaa[long string]
- 04:05:42 UTC - 5.149.248[.]85:80 - report.e17k3y7ce1aaaaaa31[.]com - POST /
- 04:05:42 UTC - 5.149.248[.]85:80 - update.obtlyoohsvjjj[.]com - GET /?ob=kdnSlMapll7UkquirNKknqWuo[long string]
- 04:05:44 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /flashupdate64.exe
- 04:05:55 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /first.vbs
- 04:05:55 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /update.vbs
- 04:05:55 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /flashsec64.exe
- 04:05:56 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /startsec.vbs
- 04:05:56 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /updatesec.vbs
- 04:05:56 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /flashcl.exe
- 04:05:57 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /startcl.vbs
- 04:05:57 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /updatecl.vbs
- 04:05:57 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /info.txt
- 04:05:57 UTC - 5.149.248[.]85:80 - 5.149.248[.]85 - GET /Product2324_Distribution2399_Partner6407.exe
- 04:06:19 UTC - 5.149.248[.]85:80 - sdfe3454hhdf[.]com - GET /report.log
INSTALLER FOR UNWANTED PROGRAM
- 04:06:19 UTC - 23.21.53[.]17:80 - installer.ppdownload[.]com - GET /Installer/Flow?pubid=6407&[long string]
- 04:06:20 UTC - 54.243.247[.]108:80 - installer.ppdownload[.]com - GET /offers/DynamicOfferScreen?[long string]
- 04:06:20 UTC - 74.125.30[.]156:80 - stats.g.doubleclick[.]net - GET /dc.js
- 04:06:20 UTC - 198.232.124[.]224:80 - static.revenyou[.]com - GET /offers/images/Theme7/topLine.jpg
- 04:06:20 UTC - 198.232.124[.]224:80 - static.revenyou[.]com - GET /offers/images/Theme7/topComp.png
- 04:06:20 UTC - 74.125.30[.]156:80 - stats.g.doubleclick[.]net - GET /__utm.gif?utmwv=5.4.8dc&[long string]
- 04:06:21 UTC - 198.232.124[.]224:80 - static.revenyou[.]com - GET /offers/images/Theme7/bgImg.jpg
- 04:06:21 UTC - 198.232.124[.]224:80 - static.revenyou[.]com - GET /offers/images/Theme7/bodyImg.png
- 04:06:21 UTC - 198.232.124[.]224:80 - static.revenyou[.]com - GET /offers/images/Theme7/bottomLine.jpg
- 04:06:21 UTC - 198.232.124[.]224:80 - static.revenyou[.]com - GET /offers/images/Theme7/nextCase.jpg
- 04:06:21 UTC - 198.232.124[.]224:80 - static.revenyou[.]com - GET /offers/images/Theme7/button_over.png
- 04:06:21 UTC - 198.232.124[.]224:80 - static.revenyou[.]com - GET /offers/images/Theme7/button.png
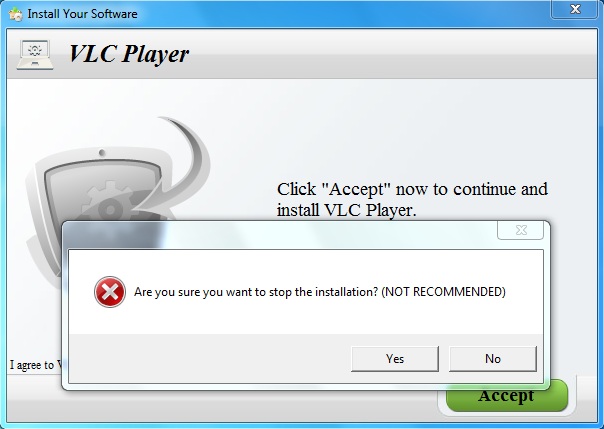
The unwanted program says it's a VLC player:
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
File name: 2014-03-15-Styx-EK-java-exploit.jpg
File size: 32,626 bytes
MD5 hash: 1edc4279c44c874bcb3e749db7e0e885
Detection ratio: 15 / 49
First submission: 2014-02-05 12:50:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/cd467699247c15883a1e8f5ea38b27ee3f8eb03f422107b808ed89d31bd998c4/analysis/
This Java exploit has been out for about a month and a half now...
MALWARE PAYLOAD - SIMDA BACKDOOR
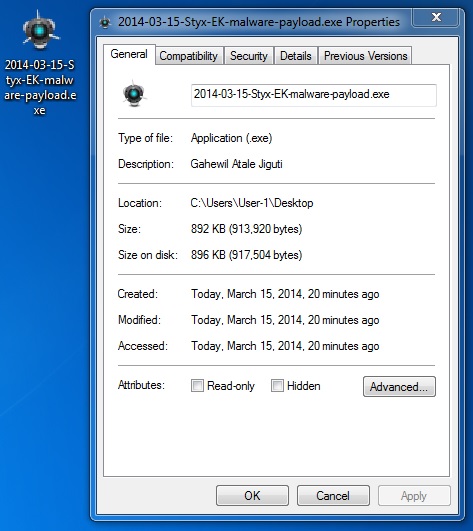
File name: 2014-03-15-Styx-EK-malware-payload.exe
File size: 913,920 bytes
MD5 hash: f388668fa7461565707ca2a36677fd3c
Detection ratio: 38 / 49
First submission: 2014-03-10 22:39:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/6f23f03fcaebd7eb12618d160826841c03a7efed154bce1d8645ffe43ba1c5b3/analysis/
FOLLOW-UP MALWARE (1 OF 4) - ADCLICKER / QHOST
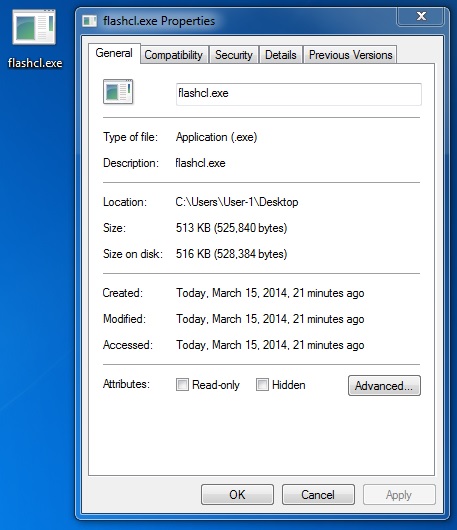
File name: flashcl.exe
File size: 525,840 bytes
MD5 hash: 30ad1e0db5af8e6f81da10e738d4b7b0
Detection ratio: 20 / 49
First submission: 2014-03-09 12:05:02 UTC
VirusTotal link: https://www.virustotal.com/en/file/996b88ebf3f91a665d75474db3a16169d9ebc4e8bbc096bdb452d7b3e51309e0/analysis/
FOLLOW-UP MALWARE (2 OF 4) - SIMDA
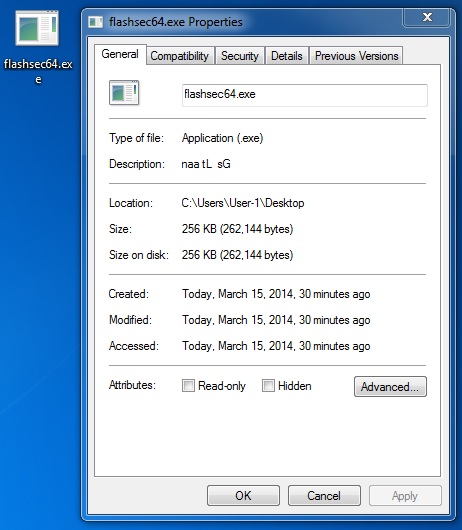
File name: flashsec64.exe
File size: 262,144 bytes
MD5 hash: 982e0df10b9f06e3baabf77fbd4524be
Detection ratio: 27 / 49
First submission: 2014-03-05 12:59:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/49eaba8ade344ea08d5b989729781a8406c8687d69f09505c2646257ba286939/analysis/
FOLLOW-UP MALWARE (3 OF 4) - BITCOIN MINER
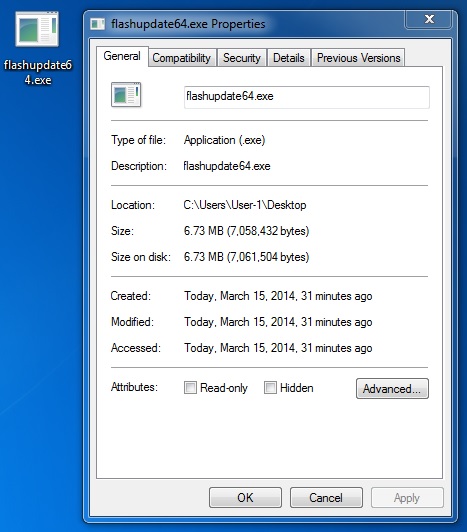
File name: flashupdate64.exe
File size: 7,058,432 bytes
MD5 hash: 66f0ba29674e859221d6c142a7b99ed7
Detection ratio: 14 / 49
First submission: 2014-01-26 05:27:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/41cff4db42730a6d9b2a8c69ebc94df571c35b5983824747512f23352c9d0aae/analysis/
FOLLOW-UP MALWARE (4 OF 4) - UNWANTED PROGRAM - OUTBROWSE
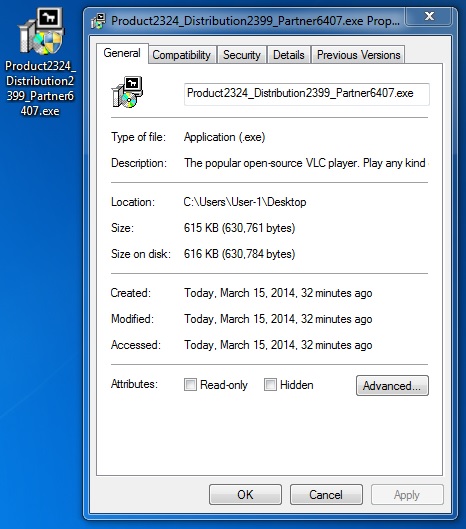
File name: Product2324_Distribution2399_Partner6407.exe
File size: 7ba7c951830f5b0f21c98c2a5b6d13bd
MD5 hash: 630,761 bytes
Detection ratio: 23 / 49
First submission: 2014-02-24 14:48:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/ead2ac697f81a7ced7e13b3512f609db4cd3ec37952c1da568c80ef70ebedbfc/analysis/
ALERTS
ALERTS FOR INFECTION TRAFFIC (from Sguil on Security Onion)
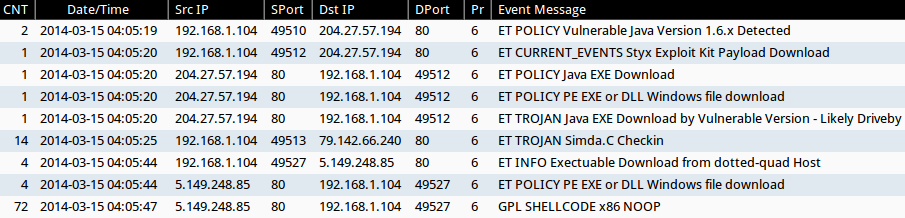
- 04:05:19 UTC - 204.27.57[.]194:80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 04:05:20 UTC - 204.27.57[.]194:80 - ET CURRENT_EVENTS Styx Exploit Kit Payload Download
- 04:05:20 UTC - 204.27.57[.]194:80 - ET POLICY Java EXE Download
- 04:05:20 UTC - 204.27.57[.]194:80 - ET POLICY PE EXE or DLL Windows file download
- 04:05:20 UTC - 204.27.57[.]194:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- 04:05:25 UTC - 79.142.66[.]240:80 - ET TROJAN Simda.C Checkin
- 04:05:44 UTC - 5.149.248[.]85:80 - ET INFO Exectuable Download from dotted-quad Host
- 04:05:44 UTC - 5.149.248[.]85:80 - ET POLICY PE EXE or DLL Windows file download
- 04:05:47 UTC - 5.149.248[.]85:80 - GPL SHELLCODE x86 NOOP
ADDITIONAL NOTES
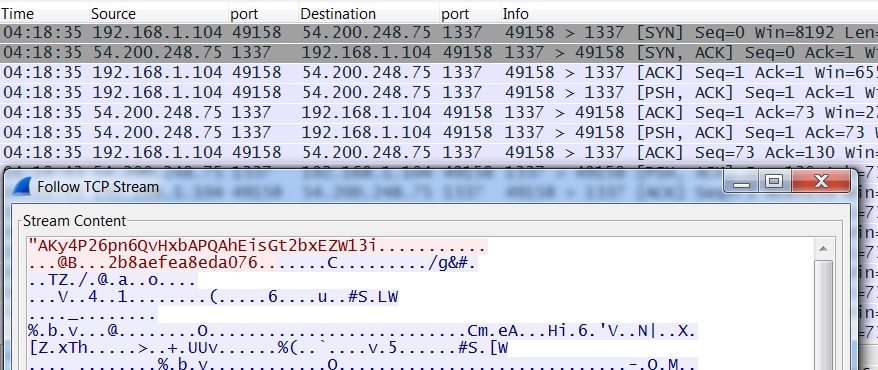
Also saw TCP traffic to 54.200.248[.]75 port 1337 from the infected host:
Click here to return to the main page.