2014-05-04 - ANGLER EK FROM 209.159.153[.]186 - THREE.MDFCKEL[.]BIZ
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The past few days, I've noticed the same two different payloads from Angler EK--both saved as a DLL to the user's AppData\Local\Temp folder.
- The file hashes may change, but the dropped files and post-infection traffic remain the same.
- These two pcap files are the latest examples... Just another trend I've noticed, so I've documented it in this blog post.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 198.57.189[.]147 - www.doblatuproductividad[.]com - 32x32 gate leading to exploit kit
- 209.159.153[.]186 - three.mdfckel[.]biz - Angler EK
FIRST EXAMPLE: ANGLER EK - GLUPTEBA PAYLOAD
- 22:31:22 UTC - three.mdfckel[.]biz - GET /5e8j3fub7d
- 22:31:24 UTC - three.mdfckel[.]biz - GET /92XKH3W5nhPI7Nneah4-jFg7oGS7nRtGpHjSQN6rZwFZNNG6hfQJjHXwoQnqD4u7hT7n_o-XFbo=
- 22:31:25 UTC - three.mdfckel[.]biz - GET /0KoLVEZIYogHW68m2BKp6B14pR-JxfCXuQj5iEU5ZSM1r2d44BxwVo8ZqodFNRemavdR_C_HuFw=
- 22:31:29 UTC - three.mdfckel[.]biz - GET /zQCtHnCXzZsVVZQP9HOLUjM0ewaOQKKsR77BmUnd4mPulnWmTLZZXDTNL5HjDKvYM0_IFMmON_M=
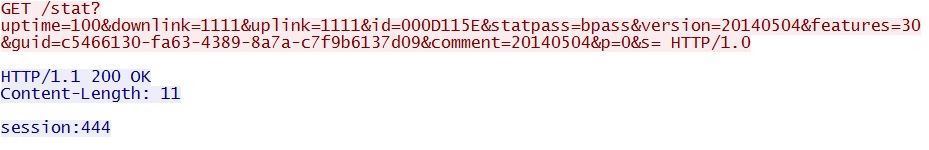
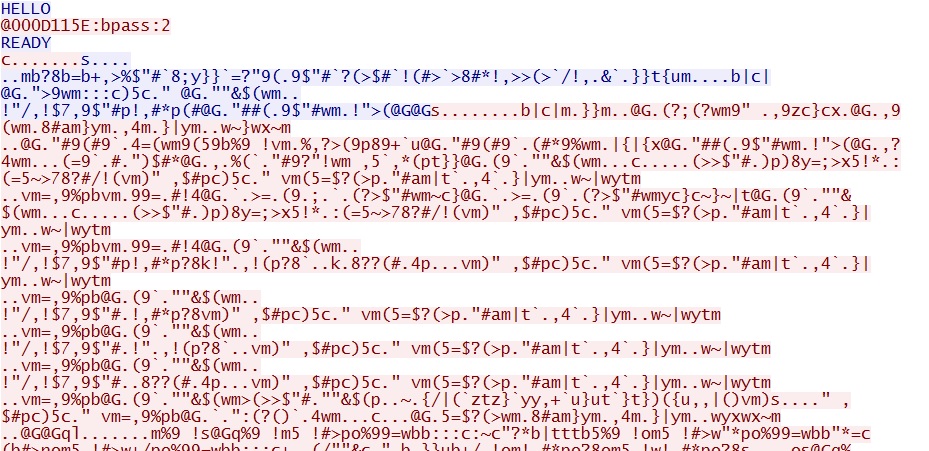
- 22:31:34 UTC - 95.211.138[.]72:8000 - GET /stat?uptime=100&downlink=1111&uplink=1111&id=000D115E&statpass=bpass&version=20140504&features=30&guid=
c5466130-fa63-4389-8a7a-c7f9b6137d09&comment=20140504&p=0&s= - 22:31:35 UTC - 95.211.138[.]72:444 - Glupteba callback traffic starts, destination port 444
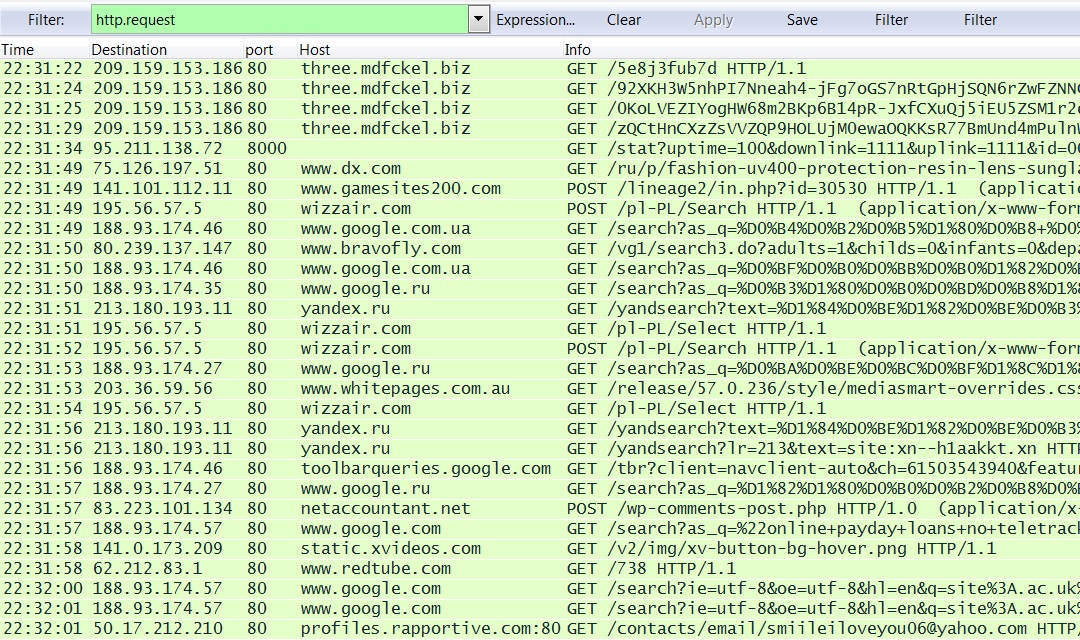
- 22:31:49 UTC - Click fraud style traffic starts
SECOND EXAMPLE: ANGLER EK - BLOCRYPT PAYLOAD
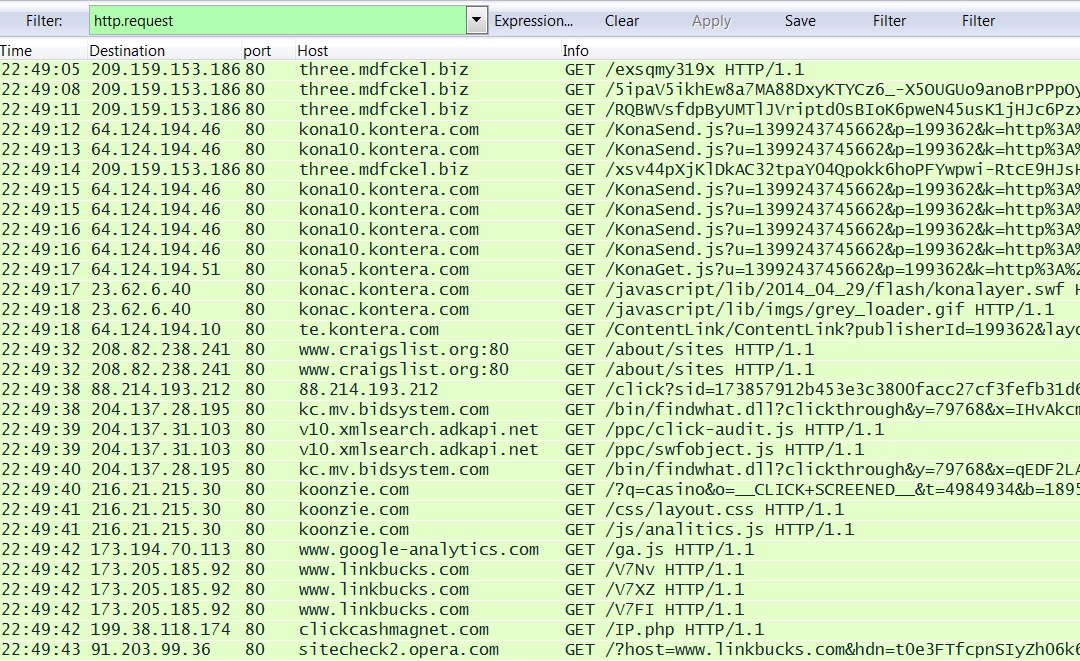
- 22:49:05 UTC - three.mdfckel[.]biz - GET /exsqmy319x
- 22:49:08 UTC - three.mdfckel[.]biz - GET /5ipaV5ikhEw8a7MA88DxyKTYCz6_-X5OUGUo9anoBrPPpOy4nm-SeMZWRZaHkWu_8PdKNoqcrlI=
- 22:49:11 UTC - three.mdfckel[.]biz - GET /RQBWVsfdpByUMTlJVriptd0sBIoK6pweN45usK1jHJc6PzxQNs_idY-eI3M-9qEWT7JyZzZso4Q=
- 22:49:14 UTC - three.mdfckel[.]biz - GET /xsv44pXjKlDkAC32tpaY04Qpokk6hoPFYwpwi-RtcE9HJsHdv91k918-Ai1bsR6AUVnuCZYL9Xg=
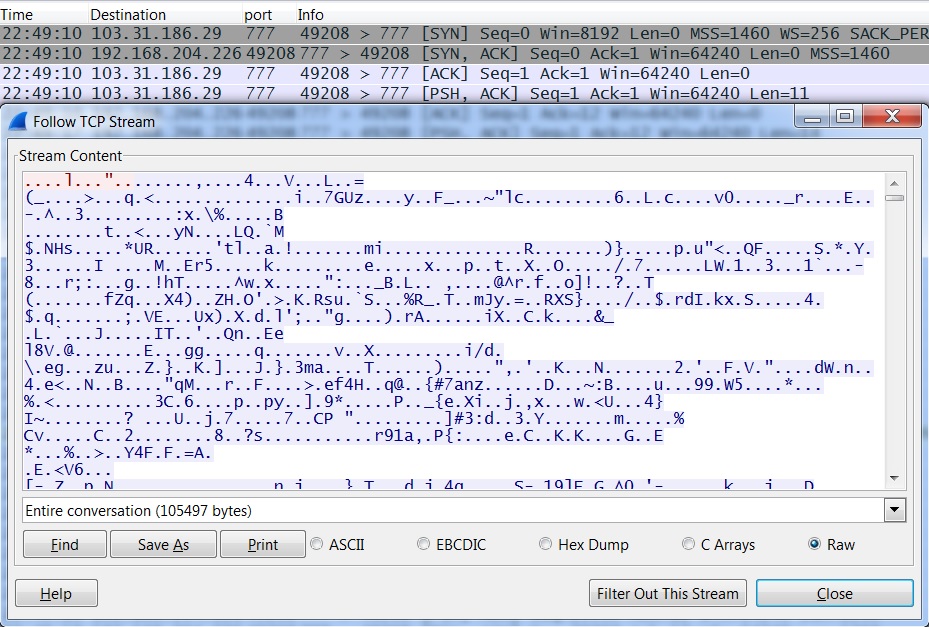
- 22:49:10 UTC - 103.31.186[.]29:777 - Blocrypt callback traffic starts, destination port 777, encrypted or otherwise obfurscated
- 22:49:12 UTC - Click fraud style traffic starts
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-05-04-Angler-EK-flash-exploit.swf
File size: 42,338 bytes
MD5 hash: ad199ca7aced985667a5d4d8fe3f602a
Detection ratio: 3 / 52
First submission: 2014-05-02 15:36:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/ef18d21e51863e2de4c27327c50c6ccde6ba6aee28bfcc0b768c6dfde0652c70/analysis/
File name: 2014-05-04-Angler-EK-flash-exploit-uncompressed.swf
File size: 71,657 bytes
MD5 hash: a47877b092e6b18ca3b09aaaf1070b57
Detection ratio: 2 / 52
First submission: 2014-05-05 03:17:34 UTC
VirusTotal link: https://www.virustotal.com/en/file/0cf82d9d581b9c32a42069ab1cd97edaa92a90e069735845d6204b05a2d0fd37/analysis/
SILVERLIGHT EXPLOIT
File name: 2014-05-04-Angler-EK-silverlight-exploit.xap
File size: 52,655 bytes
MD5 hash: 255df5955eefb9df86974da8c9fcb35b
Detection ratio: 2 / 52
First submission: 2014-05-05 03:18:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/c445ce05db65eed21a4790f9c9951777e36cfa202d3f1c597ad7f5d643906626/analysis/
MALWARE PAYLOAD: GLUPTEBA
File name: 2014-05-04-Angler-EK-malware-payload-01.exe
File size: 77,105 bytes
MD5 hash: 76b839eae030b2b920eb31be0e44399b
Detection ratio: 7 / 51
First submission: 2014-05-05 02:17:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/e41bd5e64c3617876fe1ac9d7dcb3079a6a64b6ca6a260257f4992d8c79f7a3b/analysis/
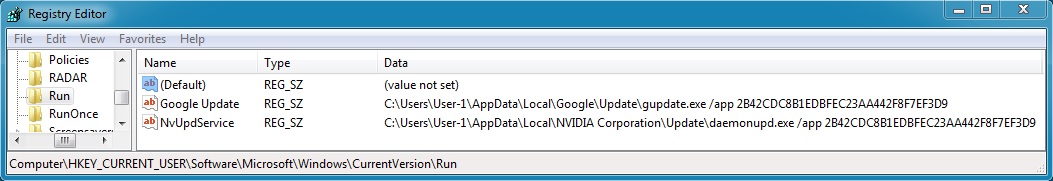
Registry key changed: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Name: Google Update
Value: C:\Users\User-1\AppData\Local\Google\Update\gupdate.exe /app 2B42CDC8B1EDBFEC23AA442F8F7EF3D9
Name: NvUpdService
Value: C:\Users\User-1\AppData\Local\NVIDIA Corporation\Update\daemonupd.exe /app 2B42CDC8B1EDBFEC23AA442F8F7EF3D9
NOTE: Both of these EXE files have the same hash--they are the same piece of malware.
File name: 2014-05-04-Angler-EK-dropped-malware-01.exe
File size: 129,024 bytes
MD5 hash: d83665e11921a3e0525e1d4d9e1d04f1
Detection ratio: 3 / 51
First submission: 2014-05-04 13:30:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/ec6ef3dc932ca1e74a18b4edb214e128ca59beba5ec0f2eec8957399c31ebd38/analysis/
MALWARE PAYLOAD: BLOCRYPT
File name: 2014-05-04-Angler-EK-malware-payload-02.exe
File size: 153,088 bytes
MD5 hash: 4ba6b80b42f487492afd12b98de7903c
Detection ratio: 4 / 51
First submission: 2014-05-05 02:17:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/32a9fa746519d36dc58717cf111e7ea8d993093ea7100cd8d5cbb881e7351656/analysis/
Registry key changed: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Name: CryptoUpdate
Value: C:\Windows\system32\rundll32.exe "C:\Users\User-1\AppData\Roaming\Microsoft\Crypto\RSA\cert_v44_1.tpl",Crypt
File name: 2014-05-04-Angler-EK-dropped-malware-02.dll
File size: 105,472 bytes
MD5 hash: ca2aaeca0a13cd503a2d495da27637ad
Detection ratio: 6 / 52
First submission: 2014-04-05 08:56:34 UTC (first submitted over 4 weeks ago)
VirusTotal link: https://www.virustotal.com/en/file/71905f51226e9e1436776a3c2445a241550febf8c46d896f22d60afb73bb00de/analysis/
ALERTS
ALERTS FOR ANGLER EK - GLUPTEBA PAYLOAD (from Sguil on Security Onion):
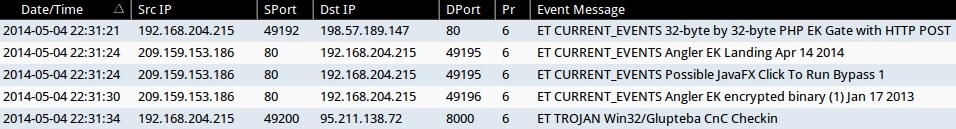
- 2014-05-04 22:31:21 UTC - 198.57.189[.]147:80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST
- 2014-05-04 22:31:24 UTC - 209.159.153[.]186:80 - ET CURRENT_EVENTS Angler EK Landing Apr 14 2014
- 2014-05-04 22:31:24 UTC - 209.159.153[.]186:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 1
- 2014-05-04 22:31:30 UTC - 209.159.153[.]186:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013
- 2014-05-04 22:31:34 UTC - 95.211.138[.]72:8000 - ET TROJAN Win32/Glupteba CnC Checkin
ALERTS FOR ANGLER EK - BLOCRYPT PAYLOAD:
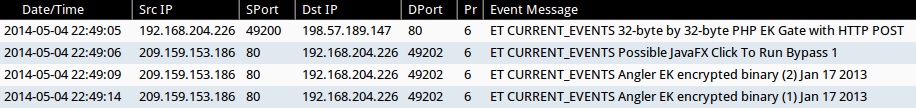
- 2014-05-04 22:49:05 UTC - 198.57.189[.]147:80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST
- 2014-05-04 22:49:06 UTC - 209.159.153[.]186:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 1
- 2014-05-04 22:49:09 UTC - 209.159.153[.]186:80 - ET CURRENT_EVENTS Angler EK encrypted binary (2) Jan 17 2013
- 2014-05-04 22:49:14 UTC - 209.159.153[.]186:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013
HIGHLIGHTS FROM THE TRAFFIC
2014-05-04-Angler-EK-traffic-01.pcap - Glupteba checkin:
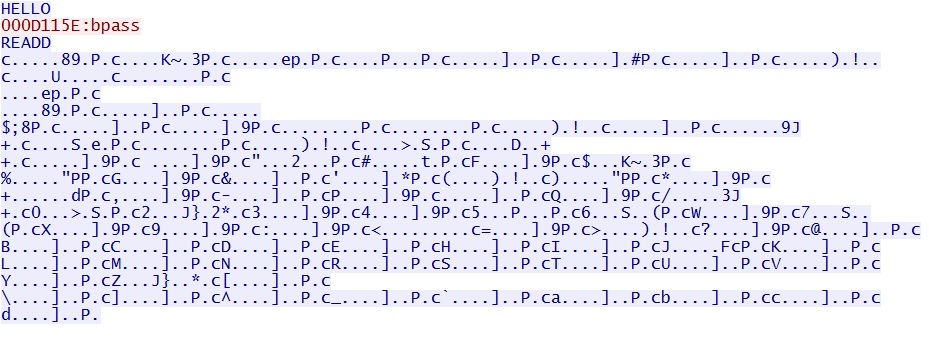
2014-05-04-Angler-EK-traffic-01.pcap - Glupteba traffic on TCP port 444:
2014-05-04-Angler-EK-traffic-01.pcap - Click fraud style traffic seen with Glupteba payload:
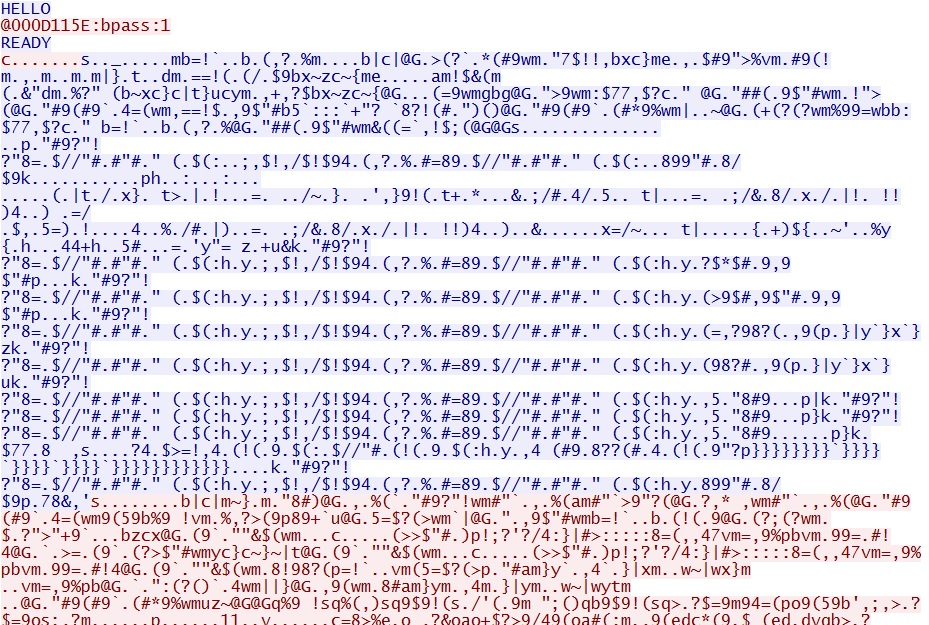
2014-05-04-Angler-EK-traffic-02.pcap - Some of the Blocrypt traffic on TCP port 777:
2014-05-04-Angler-EK-traffic-02.pcap - Click fraud style traffic seen with Blocrypt payload:
Click here to return to the main page.