2014-06-19 - NUCLEAR EK FROM 5.135.28[.]118 - 2624633428-6.DISBARMENTSCORE.CO7[.]US
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- VirusTotal indicates the Flash exploit used in this traffic is a CVE-2014-0515 Flash exploit.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 95.211.188[.]216 - stat.litecsys[.]com - First ad redirect
- 95.211.188[.]217 - static.sumibi[.]org - Second ad redirect
- 5.135.28[.]118 - 4e63f29dvtlp.disbarmentscore.co7[.]us and 2624633428-6.disbarmentscore.co7[.]us - Nuclear EK
AD TRAFFIC REDIRECTING TO NUCLEAR EK:
- 15:31:59 UTC - 95.211.188[.]216:80 - stat.litecsys[.]com - GET /d2.php?ds=true&dr=7519651950
- 15:32:00 UTC - 95.211.188[.]217:80 - static.sumibi[.]org - HEAD /pop2.php?acc=%F1%1C%B8%ABs7A%7Dk%21%A5%B0J%AC%A0%255%EE
%0DZ1Z%0D9&nrk=8596163981 - 15:32:01 UTC - 95.211.188[.]217:80 - static.sumibi[.]org - GET /pop2.php?acc=%F1%1C%B8%ABs7A%7Dk%21%A5%B0J%AC%A0%255%EE
%0DZ1Z%0D9&nrk=8596163981
NUCLEAR EK:
- 15:32:02 UTC - 5.135.28[.]118:80 - 4e63f29dvtlp.disbarmentscore.co7[.]us - GET /
- 15:32:08 UTC - 5.135.28[.]118:80 - 2624633428-6.disbarmentscore.co7[.]us - GET /1403171040.swf
- 15:32:15 UTC - 5.135.28[.]118:80 - 2624633428-6.disbarmentscore.co7[.]us - GET /1403171040.jar
- 15:32:16 UTC - 5.135.28[.]118:80 - 2624633428-6.disbarmentscore.co7[.]us - GET /f/1403171040/2
- 15:32:18 UTC - 5.135.28[.]118:80 - 2624633428-6.disbarmentscore.co7[.]us - GET /f/1403171040/2/2
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-06-19-Nuclear-EK-flash-exploit.swf
File size: 4,062 bytes
MD5 hash: f95006970f34a6ca5bcd0b32b92dd48d
Detection ratio: 5 / 54
First submission: 2014-06-18 09:07:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/179c76bab67a75911b537abcb968cbd7ccbe42f212eab5d91b484ac24432064a/analysis/
NOTE: Some of the vendors in this VirusTotal entry have identified the Flash exploit as CVE-2014-0515
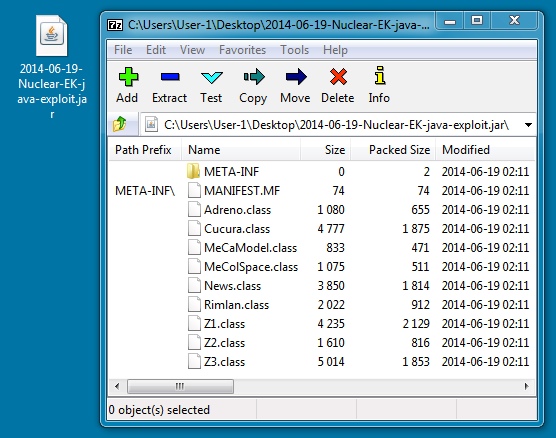
JAVA EXPLOIT
File name: 2014-06-19-Nuclear-EK-java-exploit.jar
File size: 12,414 bytes
MD5 hash: f9c0027ccaeefa616e392132b02fbce7
Detection ratio: 2 / 54
First submission: 2014-06-19 00:22:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/69bf8fdc5510b6ee3c624d5b58043466aebb3301e1ae9ce96f66d7abc883c4fe/analysis/
MALWARE PAYLOAD
File name: 2014-06-19-Nuclear-EK-malware-payload.exe
File size: 222,208 bytes
MD5 hash: 87223f535afd8b11dd79c6f39fc059d9
Detection ratio: 4 / 52
First submission: 2014-06-19 16:40:18 UTC
VirusTotal link: https://www.virustotal.com/en/file/0282b70848a917cdeb0900ae67ba12fd051c6b147484e34b312198183a12b7b1/analysis/
ALERTS
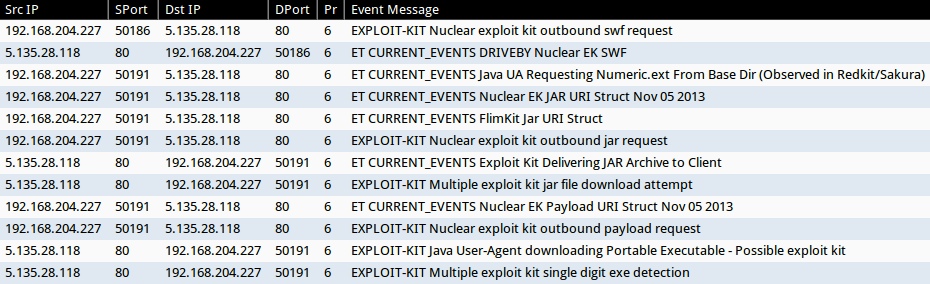
Emerging Threats and ETPRO rulesets:
- 5.135.28[.]118:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 5.135.28[.]118:80 - ET CURRENT_EVENTS Java UA Requesting Numeric.ext From Base Dir (Observed in Redkit/Sakura) (sid:2017199)
- 5.135.28[.]118:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 5.135.28[.]118:80 - ET CURRENT_EVENTS FlimKit Jar URI Struct (sid:2017152)
- 5.135.28[.]118:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 5.135.28[.]118:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
Sourcefire VRT ruleset:
- 5.135.28[.]118:80 - EXPLOIT-KIT Nuclear exploit kit outbound swf request (sid:31237)
- 5.135.28[.]118:80 - EXPLOIT-KIT Nuclear exploit kit outbound jar request (sid:30219)
- 5.135.28[.]118:80 - EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- 5.135.28[.]118:80 - EXPLOIT-KIT Nuclear exploit kit outbound payload request (sid:30220)
- 5.135.28[.]118:80 - EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit (sid:25042)
- 5.135.28[.]118:80 - EXPLOIT-KIT Multiple exploit kit single digit exe detection (sid:28423)
NOTE: These alerts were taken from Sguil on Security Onion
p>Click here to return to the main page.