2014-07-08 - KULUOZ INFECTION FROM ATTACHMENT IN ASPROX BOTNET EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
TODAY'S EMAILS
SCREENSHOTS:
SUBJECT LINES:
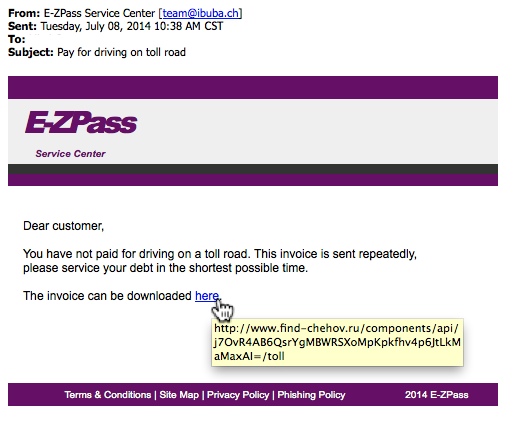
- Pay for driving on toll road
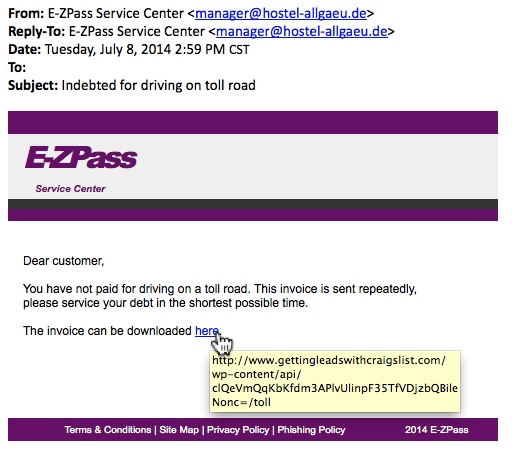
- Indebted for driving on toll road
MESSAGE:
Dear customer,
You have not paid for driving on a toll road. This invoice is sent repeatedly,
please service your debt in the shortest possible time.
The invoice can be downloaded here.
LINKS FROM THE EMAILS TO THE MALWARE:
- 89.111.177[.]168 - www.find-chehov[.]ru/components/api/j7OvR4AB6QsrYgMBWRSXoMpKpkfhv4p6JtLkMaMaxAI=/toll
- 66.147.244[.]62 - www.gettingleadswithcraigslist[.]com/wp-content/api/clQeVmQqKbKfdm3APlvUlinpF35TfVDjzbQBileNonc=/toll
NOTE: The account for www.gettingleadswithcraigslist[.]com was suspended by the time I checked the link
PRELIMINARY MALWARE ANALYSIS
ZIP FILE:
File name: E-ZPass_San_Antonio.zip
File size: 58,028 bytes
MD5 hash: b667faf93d1b846ee4d0b9656d0d282b
Detection ratio: 4 / 54
First submission: 2014-07-08 20:24:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/611c8bff331db2f7a2c79c96b897264cb96dccd292460507acb6e0ed29b6f167/analysis/
EXTRACTED MALWARE:
File name: E-ZPass_San_Antonio.exe
File size: 86,016 bytes
MD5 hash: 351c4b6611117ab2f5f8af8710e0bd52
Detection ratio: 5 / 54
First submission: 2014-07-08 20:25:45 UTC
VirusTotal link: https://www.virustotal.com/en/file/16d1f3f1f9c095e8a1fda728edab565065d91adcd04cf691ac1433222f37f11b/analysis/
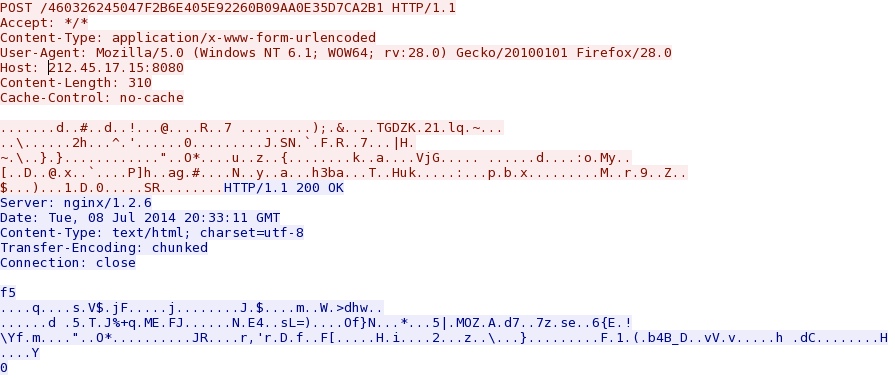
TRAFFIC FROM SANDBOX ANALYSIS OF MALWARE
2014-07-08 20:34 UTC - 212.45.17[.]15:8080 - 212.45.17[.]15:8080 - POST /460326245047F2B6E405E92260B09AA0E35D7CA2B1
ALERTS
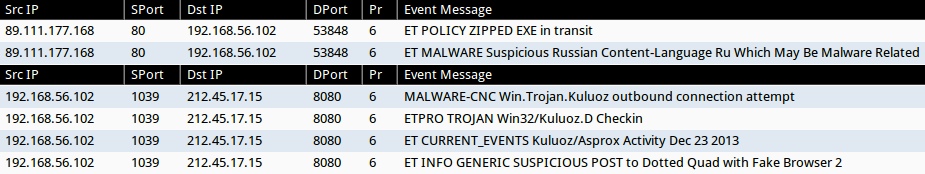
Alerts from the initial malware download:
- 89.111.177[.]168:80 - [1:2001404:5] ET POLICY ZIPPED EXE in transit
- 89.111.177[.]168:80 - [1:2012228:1] ET MALWARE Suspicious Russian Content-Language Ru Which May Be Malware Related
Alerts from sandbox anlaysis of the malware:
- 212.45.17[.]15:8080 - [1:31244:2] MALWARE-CNC Win.Trojan.Kuluoz outbound connection attempt
- 212.45.17[.]15:8080 - [1:2807771:1] ETPRO TROJAN Win32/Kuluoz.D Checkin
- 212.45.17[.]15:8080 - [1:2017895:5] ET CURRENT_EVENTS Kuluoz/Asprox Activity Dec 23 2013
- 212.45.17[.]15:8080 - [1:2018359:1] ET INFO GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 2
Click here to return to the main page.