2014-07-09 - ZUPONCIC EK FROM 178.33.152[.]221 - MZ.WATCHWEEDSEPISODES[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
This is the second time I've run across Zuponcic. I first saw it on 2014-03-17. Here are some good blog posts about this exploit kit and the associated malware:
- https://blog.fox-it.com/2013/12/19/not-quite-the-average-exploit-kit-zuponcic/
- https://malwageddon.blogspot.com/2013/08/zuponcic-is-it-bird-is-it-plane-no-its.html
- https://c-apt-ure.blogspot.com/2013/12/ponmocup-hunter-is-re-tired.html
The Fox-IT article states, "When a victim does not have Java enabled or the browser used is not Internet Explorer, a ZIP file is presented." I originally discovered this infection chain while investigating a ZIP file delivered by Zuponcic on 2014-07-07.
When I tried Zuponcic with Java 7 update 13, the exploit kit didn't send a Java exploit or a ZIP file--instead, it asked me to download an 839 KB JAR file.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 103.241.1[.]49 - www.dioxinnz[.]com - Compromised website
- 31.210.96[.]156 - plapplatong.workoutebook[.]com - Redirect
- 178.33.152[.]221 - mz.watchweedsepisodes[.]net - Zuponcic EK (first two characters are variable)
- 93.115.88[.]220 - 93.115.88[.]220 - First post-infection callback
- 64.210.128[.]29 - www.sanctionedmedia[.]com - Second post-infection callback
EXAMPLE 1 - ZUPONCIC EK USES JAVA EXPLOIT:
- 05:50:21 UTC - 103.241.1[.]49:80 - www.dioxinnz[.]com - GET /
- 05:50:26 UTC - 31.210.96[.]156:80 - plapplatong.workoutebook[.]com - GET /dcs0junic89k7m2gzez6wz0k8_7v8n/dcs.gif?&dcsdat=1340252801
661&dcssip=office.microsoft[.]com&dcsuri=/en-us/images/results.aspx&dcsqry=?qu=people&dcsref=http%3A%2F%2Fwww.dioxinnz[.]com%2F&[long string of characters] - 05:50:30 UTC - 178.33.152[.]221:80 - mz.watchweedsepisodes[.]net - GET /
- 05:50:31 UTC - 178.33.152[.]221:80 - mz.watchweedsepisodes[.]net - GET /js/java.js
- 05:50:33 UTC - 178.33.152[.]221:80 - mz.watchweedsepisodes[.]net - GET /tr.gif
- 05:50:35 UTC - 178.33.152[.]221:80 - mz.watchweedsepisodes[.]net - GET /favicon.ico
- 05:50:37 UTC - 173.194.127[.]209:80 - www.google[.]com - GET /
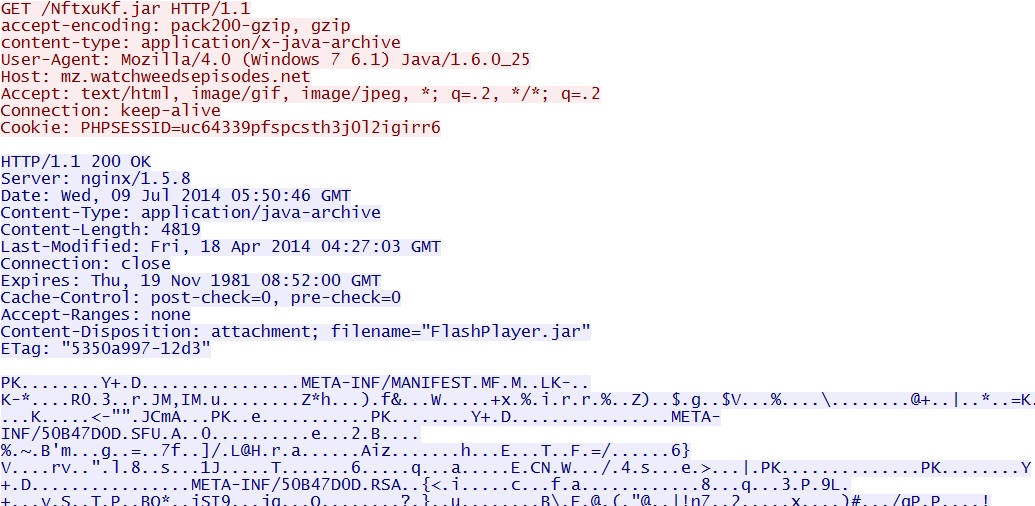
- 05:50:46 UTC - 178.33.152[.]221:80 - mz.watchweedsepisodes[.]net - GET /NftxuKf.jar
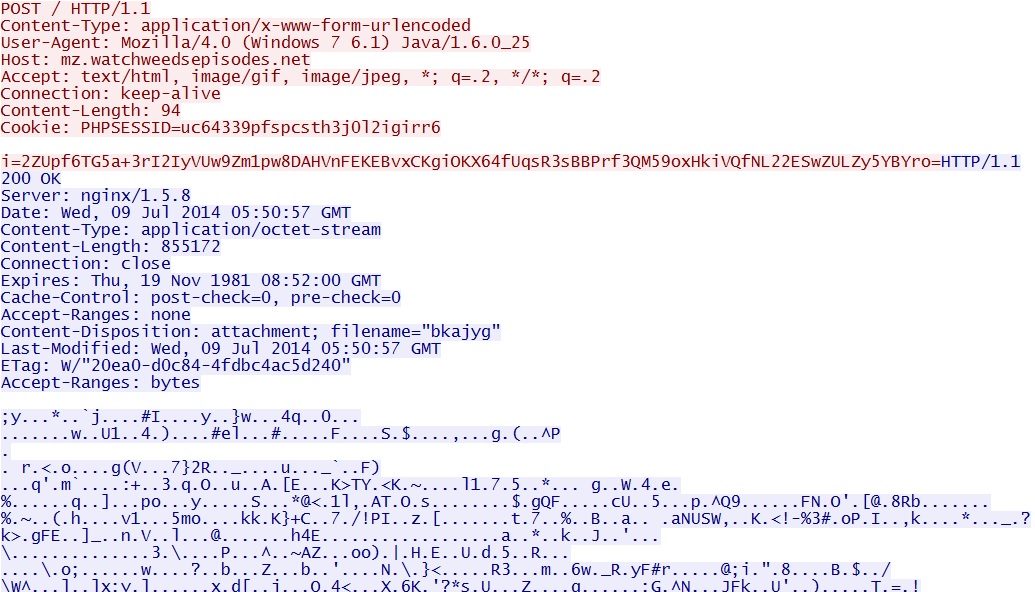
- 05:50:56 UTC - 178.33.152[.]221:80 - mz.watchweedsepisodes[.]net - POST /
- 05:51:15 UTC - 93.115.88[.]220:80 - 93.115.88[.]220 - GET /list/topics/imghp
- 05:51:29 UTC - 93.115.88[.]220:80 - 93.115.88[.]220 - GET /list/topics/imghp
- 05:51:34 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - GET /version2.XML
- 05:51:39 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smfeed2.php
- 06:01:44 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php
- 06:01:49 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php
- 06:01:54 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php
- 06:01:59 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php
- 06:02:04 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php
- 06:02:09 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php [repeats serveral times]
EXAMPLE 2 - ZUPONCIC EK SENDS 839 KB JAVA ARCHIVE:
- 05:07:27 UTC - 103.241.1[.]49:80 - www.dioxinnz[.]com - GET /
- 05:07:28 UTC - 31.210.96[.]156:80 - plapplatong.workoutebook[.]com - GET /dcs0junic89k7m2gzez6wz0k8_7v8n/dcs.gif?&dcsdat=1340252801
661&dcssip=office.microsoft[.]com&dcsuri=/en-us/images/results.aspx&dcsqry=?qu=people&dcsref=http%3A%2F%2Fwww.dioxinnz[.]com%2F&[long string of characters] - 05:07:30 UTC - 178.33.152[.]221:80 - ms.watchweedsepisodes[.]net - GET /
- 05:08:38 UTC - 216.146.43.70:80 - checkip.dyndns[.]com - GET /
- 05:08:43 UTC - 93.115.88[.]220:80 - 93.115.88[.]220 - GET /redir/article/home
- 05:08:45 UTC - 93.115.88[.]220:80 - 93.115.88[.]220 - GET /redir/article/home
- 05:08:50 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - GET /version2.XML
- 05:18:56 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php
- 05:19:00 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php
- 05:19:05 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php
- 05:19:10 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php
- 05:19:15 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php
- 05:19:20 UTC - 64.210.128[.]29:80 - www.sanctionedmedia[.]com - POST /smlog.php [repeats serveral times]
PRELIMINARY MALWARE ANALYSIS
EXAMPLE 1 - JAVA EXPLOIT:
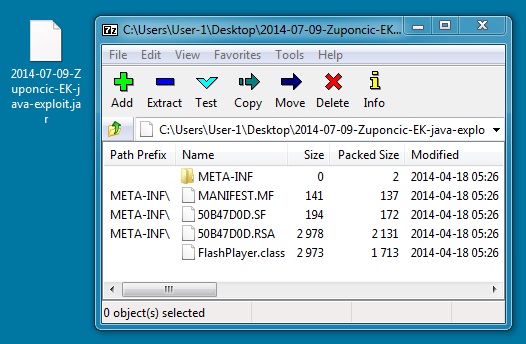
File name: 2014-07-09-Zuponcic-EK-java-exploit.jar
File size: 4,819 bytes
MD5 hash: c7e28d226100c06bfd346d0989658a0b
Detection ratio: 18 / 54
First submission: 2014-05-22 15:20:21 UTC
VirusTotal link: https://www.virustotal.com/en/file/16ab78dc36741b80c3e386b0993909dacce4768f06415cd8364b993585feb66b/analysis/
EXAMPLE 1 - MALWARE PAYLOAD:
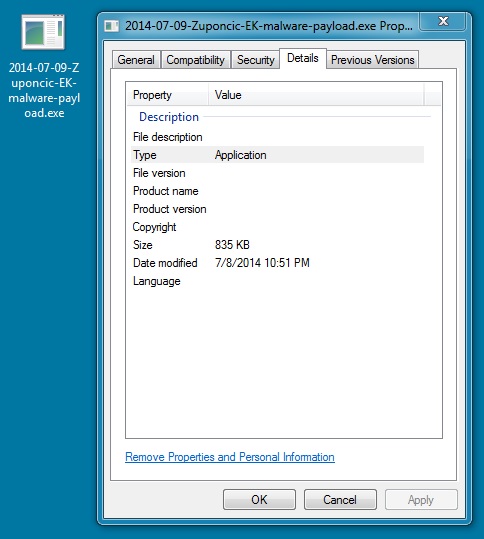
File name: 2014-07-09-Zuponcic-EK-malware-payload.exe
File size: 855,172 bytes
MD5 hash: b528871bc1e3ca5a9c9ec7037df0dcfb
Detection ratio: 17 / 54
First submission: 2014-07-09 05:58:33 UTC
VirusTotal link: https://www.virustotal.com/en/file/5913ce93f79398bba58ef7c884acc4ced43ee4d28c028b4657775f7764c26c37/analysis/
EXAMPLE 2 - ARCHIVE SENT WHEN JAVA WAS NOT VULNERABLE:
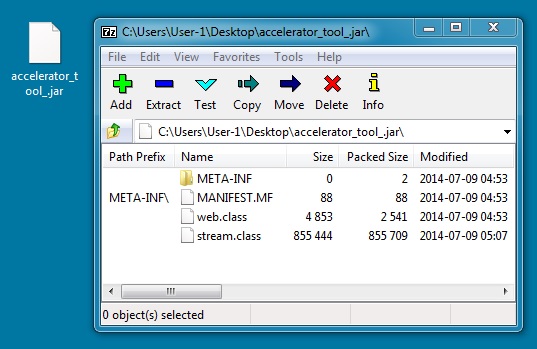
File name: accelerator_tool_.jar
File size: 858,838 bytes
MD5 hash: 181c5347a02f805e8bf8f561340bb325
Detection ratio: 5 / 54
First submission: 2014-07-09 06:48:56 UTC
VirusTotal link: https://www.virustotal.com/en/file/dd323b8ecb348df8f89c62fd1288130151bb0e630d8da9445737de00f4f33d52/analysis/
Below is the ZIP file from Zuponcic I originally investigated - sent on 2014-07-07 at 21:17 UTC from 178.33.152[.]221 - so.watchweedsepisodes[.]net:
ZIP file: video__tool.zip - MD5 hash: cb0e736622f2e3cc7eda6797f5479669 - 598,325 bytesVirusTotal link: https://www.virustotal.com/en/file/0f8fc6b69bba014f6afef7712f87fd1fd9ca2d578a5b13e7be1941a317167f06/analysis/
Extracted file: video__tool.exe - MD5 hash: 91a55427a929b49e9295243008c9522a - 997,744 bytesVirusTotal link: https://www.virustotal.com/en/file/51bd10fe9c08fe3d9bb5e6754f2bea5c31d1dd3cb666b1cb2c68ed9fb1a87585/analysis/
ALERTS (EXAMPLE 1)

Emerging Threats and ETPRO rulesets:
- 2014-07-09 05:50:30 UTC - 178.33.152[.]221:80 - ET CURRENT_EVENTS Unknown Java Exploit Version Check with hidden applet (sid:2014136)
- 2014-07-09 05:50:31 UTC - 178.33.152[.]221:80 - ET CURRENT_EVENTS Zuponcic Hostile JavaScript (sid:2015982)
- 2014-07-09 05:50:46 UTC - 178.33.152[.]221:80 - ET CURRENT_EVENTS Zuponcic Hostile Jar (sid:2015981)
- 2014-07-09 05:50:46 UTC - 178.33.152[.]221:80 - ET CURRENT_EVENTS Zuponcic EK Java Exploit Jar (sid:2015971)
- 2014-07-09 05:51:34 UTC - 64.210.128[.]29:80 - ETPRO MALWARE AdWare.MSIL.Sancmed.p Checkin (sid:2807371)
Sourcefire VRT ruleset:
- 2014-07-09 05:50:22 UTC - local host]:53 - PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority (sid:254)
- 2014-07-09 05:50:30 UTC - 178.33.152[.]221:80 - EXPLOIT-KIT Zuponcic exploit kit redirection received (sid:26960)
- 2014-07-09 05:50:32 UTC - 178.33.152[.]221:80 - BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt (sid:23878)
- 2014-07-09 05:50:34 UTC - 178.33.152[.]221:80 - GPL WEB_CLIENT web bug 0x0 gif attempt (sid:2102925)
- 2014-07-09 05:50:14 UTC - [local host]:53 - BLACKLIST DNS request for known malware domain fasternation.net - Win.Trojan.Pirminay (sid:26971)
NOTE: These Snort evenets were taken from Sguil on Security Onion. This list does not include ET INFO or ET POLICY rules.
HIGHLIGHTS FROM THE TRAFFIC
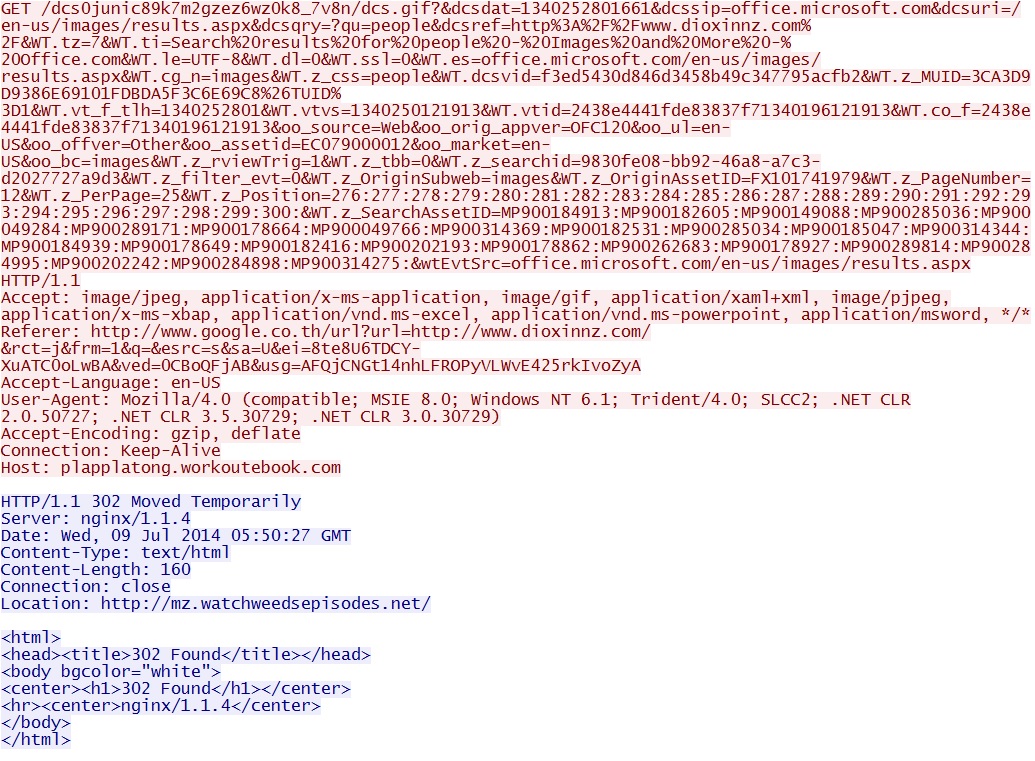
Example 1 - Going to the compromised website from a Google search returns a 302 redirect:
Example 1 - Redirect points to the Zuponcic EK landing page:
Example 1 - Zuponcic EK delivers Java exploit:
Example 1 - Encrypted EXE payload sent after successful Java exploit:
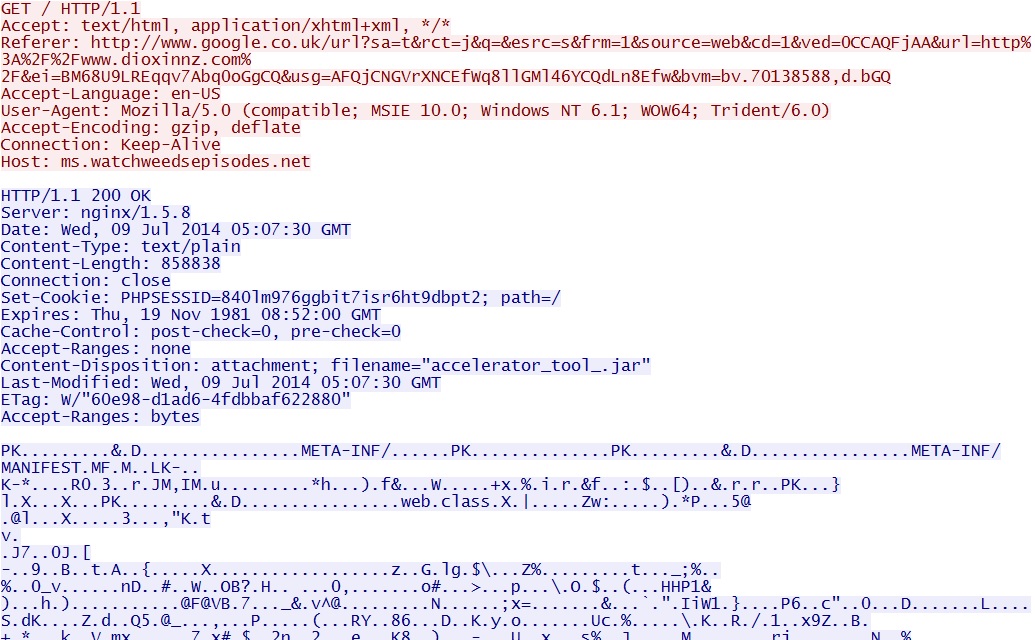
Example 2 - Zuponcic EK sent a Java archive to download when I used a VM running Java 7 update 13:
Click here to return to the main page.