2014-07-25 - UPATRE FROM EMAIL ATTACHMENT LEADS TO CRYTPOWALL RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-07-25-Upatre-infection-with-CryptoWall.pcap.zip
- 2014-07-25-Cryptowall-ransomware-and-Upatre-samples.zip
NOTES:
- The malware is Upatre, and when I executed it on a VM, it dropped CryptoWall ransomware.
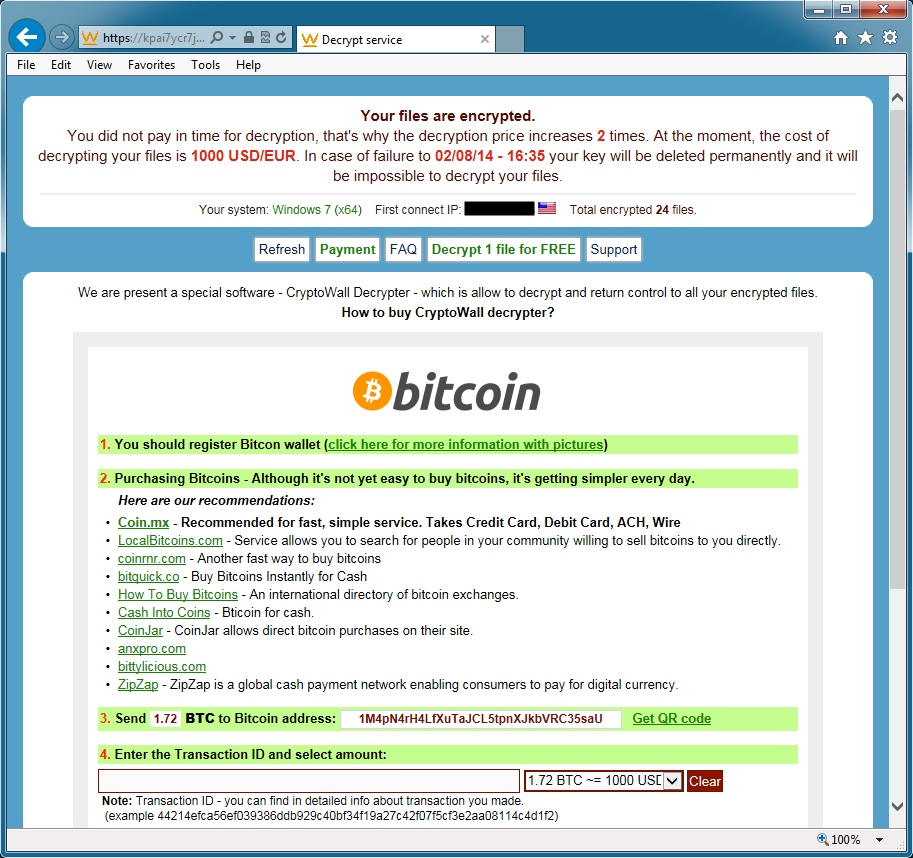
- This CryptoWall ransomware sample used 1M4pN4rH4LfXuTaJCL5tpnXJkbVRC35saU as the bitcoin address for the ransom payment.
TODAY'S EMAIL
Saw the following email today:
MESSAGE TEXT:
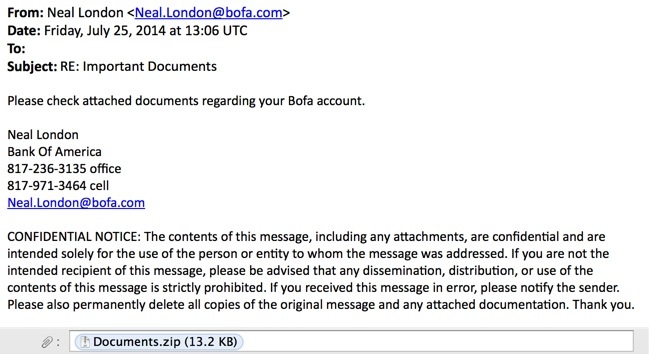
From: Neal London <Neal.London@bofa[.]com>
Date: Friday, July 25, 2014 at 13:06 UTC
To:
Subject: RE: Important Documents
Please check attached documents regarding your Bofa account.
Neal London
Bank Of America
817-236-3135 office
817-971-3464 cell
Neal.London@bofa[.]com
CONFIDENTIAL NOTICE: The contents of this message, including any attachments, are confidential and are intended solely for the use of the person or entity to whom the message was addressed. If you are not the intended recipient of this message, please be advised that any dissemination, distribution, or use of the contents of this message is strictly prohibited. If you received this message in error, please notify the sender. Please also permanently delete all copies of the original message and any attached documentation. Thank you.
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT
File name: Documents.zip
File size: 9,986 bytes
MD5 hash: b99d38332e6939baa2c2a057a37daefc
Detection ratio: 16 / 53
First submission: 2014-07-25 15:58:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/256d3022d6a0446708000e7cf4d34f0a0671058edf67c7de00033e50a65becd6/analysis/
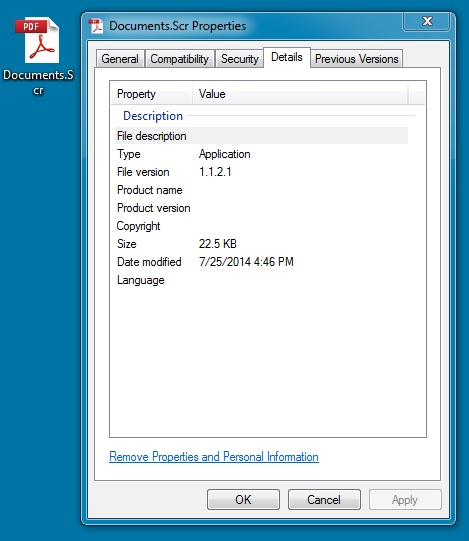
EXTRACTED MALWARE (UPATRE):
File name: Documents.Scr
File size: 23,040 bytes
MD5 hash: dc4d0bd7fb9e647501c3b0d75aa2be65
Detection ratio: 6 / 52
First submission: 2014-07-25 16:10:27 UTC
VirusTotal link: https://www.virustotal.com/en/file/9dc39f7ba4b6b31c7b55303c656e44c1782ed45e9de5a5aeca19cf018f2af9d9/analysis/
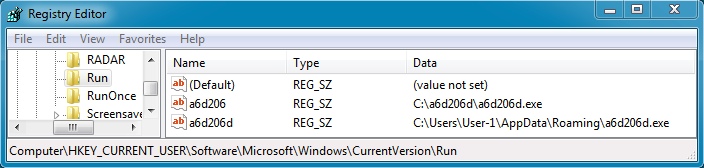
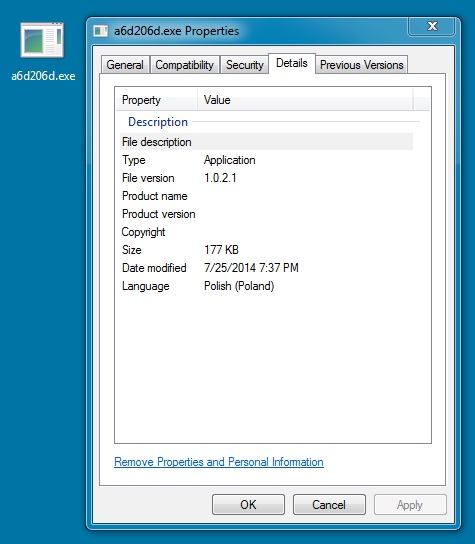
CRYPTOWALL RANSOMWARE DROPPED ON AN INFECTED VM:
File name: a6d206d.exe
File size: 181,760 bytes
MD5 hash: 57dab9371bd0710200810d8796040e8e
Detection ratio: 4 / 53
First submission: 2014-07-25 16:46:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/6bb8d45a46f4c56f8286e02779600971d1b2eeddcf7dea0b1d1e62191f8323ed/analysis/
TRAFFIC FROM THE INFECTION
HTTP GET REQUESTS:
- 2014-07-25 15:58:16 UTC - 94.23.247[.]202:80 - 94.23.247[.]202 - GET /2507stat/BTIG-HT/0/51-SP3/0/
- 2014-07-25 15:58:17 UTC - 94.23.247[.]202:80 - 94.23.247[.]202 - GET /2507stat/BTIG-HT/1/0/0/
- 2014-07-25 15:58:18 UTC - 81.169.145[.]169:80 - martinglahn[.]de - GET /Graphics/Logo/tor.rar
- 2014-07-25 15:58:27 UTC - 94.23.247[.]202:80 - 94.23.247[.]202 - GET /2507stat/BTIG-HT/41/5/4/
- 2014-07-25 15:58:49 UTC - 109.95.159[.]1:80 - pannanawydaniu[.]com[.]pl - GET /wp-content/themes/marriage/w8z0ana
OTHER TRAFFIC:
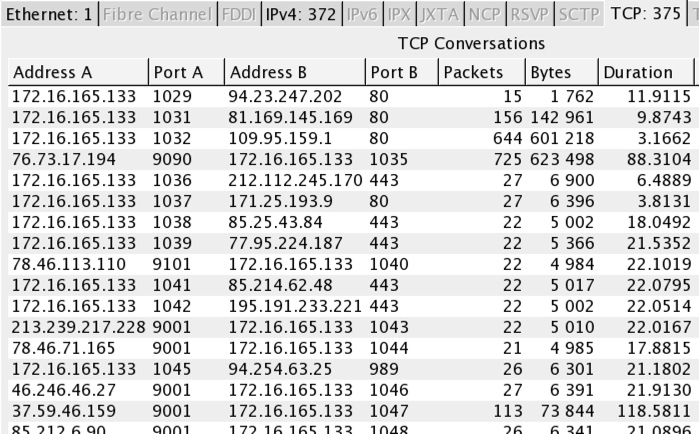
- 372 different IP addresses were noted in the sandbox pcap, which is mostly Tor traffic.
- The Tor traffic had used 443 and other TCP ports with encrypted streams (21, 22, 80, 110, 9001 and several others).
ALERTS
Emerging Threats and ETPRO signature hits from Sguil after using tcpreplay on Security Onion for the sandbox analysis:
- 2014-07-25 15:58:18 UTC - 81.169.145[.]169:80 - ET TROJAN Common Upatre Header Structure 2 (sid:2018635)
- In another sandbox analysis, I saw several alerts on the Tor traffic for: ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group [various group numbers]
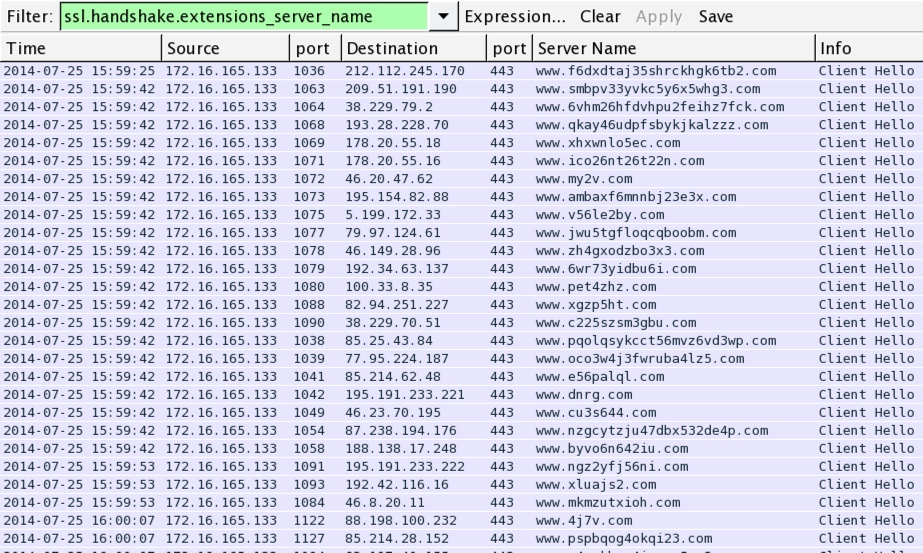
- The CryptoWall ransomware didn't do anything on the original infected VM; however, when I executed it on another VM, it generated the following alerts based on Tor traffic to kpai7ycr7jxqkilp.enter2tor[.]com:
- ET TROJAN Likely CryptoWall .onion Proxy DNS lookup (sid:2018609)
- ET TROJAN ABUSE.CH SSL Fingerprint Blacklist Malicious SSL certificate detected (CryptoWall C2) (sid:2018717) - 94.156.77.26:443
- ET TROJAN Likely CryptoWall .onion Proxy domain in SNI (sid:2018610) - 94.156.77.26:443
Sourcefire VRT signature reading the sandbox analysis pcap with Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 2014-07-25 16:00:33 UTC - 62.210.136[.]126:21 - [1:31179:2] SERVER-OTHER GnuTLS Server Hello Session ID heap overflow attempt
- I'd accidentally deleted all traffic for the CryptoWall ransomware infection in my VM, so I wasn't able to read the pcap for the Sourcefire VRT events.
CRYPTOWALL RANSOMWARE IN ACTION
Click here to return to the main page.