2014-08-15 - MAGNITUDE EK FROM 212.38.166[.]26 - RELUCTANTRID[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- The first run was on a VM using IE 8 and was infected through a CVE-2013-2551 IE exploit, and it also has a CVE-2014-0515 Flash exploit.
- The second run was on a VM using IE 10 and was infected through a Java exploit.
- Of the six different file hashes recovered, I noticed Zemot/Rerdom and CryptoWall ransomware.
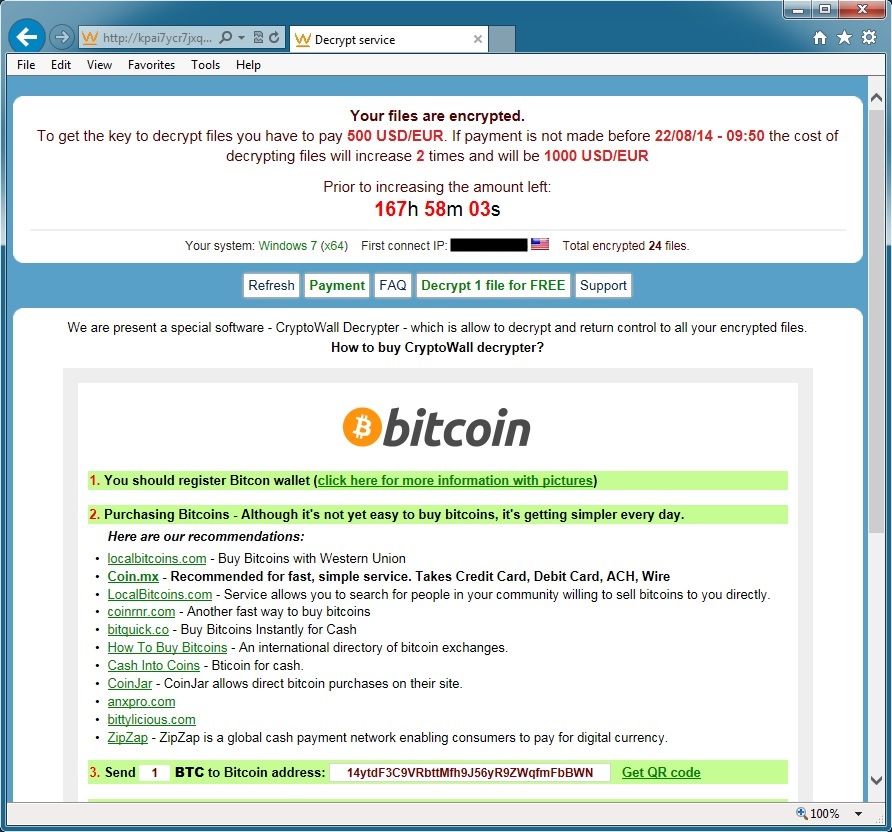
- Bitcoin address for the CryptoWall ransom payment is: 14ytdF3C9VRbttMfh9J56yR9ZWqfmFbBWN
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 212.38.166[.]26 - 439.ae.e49.bf1a.261.7406bb.cf.7e.990b821.auznoezoynhc.reluctantrid[.]in - Mangitude EK - first run
- 212.38.166[.]26 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - Magnitude EK - second run
- various IP addresses - various domains - Post-infection traffic (see below)
MAGNITUDE EK - FIRST RUN USING IE 8 - INFECTED THROUGH IE EXPLOIT CVE-2013-2551 (ALL TIMES UTC):
- 13:54 - 439.ae.e49.bf1a.261.7406bb.cf.7e.990b821.auznoezoynhc.reluctantrid[.]in - GET /
- 13:54 - 439.ae.e49.bf1a.261.7406bb.cf.7e.990b821.auznoezoynhc.reluctantrid[.]in - GET /11fe3f1f2d6d1e381ab477f53829b7e5/b9714256dc39bc5cbe2bdef8351d8cb9
- 13:54 - 439.ae.e49.bf1a.261.7406bb.cf.7e.990b821.auznoezoynhc.reluctantrid[.]in - GET /11fe3f1f2d6d1e381ab477f53829b7e5/18db5f58b7036a2898e8c4e55f306932
- 13:54 - 212.38.166[.]26 - GET /?f5832f595ab0e04e342d7331b2c3892f [!]
- 13:54 - 212.38.166[.]26 - GET /?ba2b6362fa7524a7ce2a3921a4c2ce9a [!]
- 13:55 - 212.38.166[.]26 - GET /?a30c38615052b3cadab7fee5194fb4a9
- 13:55 - 212.38.166[.]26 - GET /?4dd7462d4fdf020796aa413cee6a3f1c [!]
- 13:55 - 212.38.166[.]26 - GET /?c72a531a335a2e3784a896768a413aef [!]
- 13:55 - 212.38.166[.]26 - GET /?2d22d21a41e9bd821ed892f0cb1457d6 [!]
NOTE: [!] shows where a malware payload was returned.
MAGNITUDE EK - SECOND RUN USING IE 10 - INFECTED THROUGH JAVA EXPLOIT (ALL TIMES UTC):
- 14:09 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /
- 14:09 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/b8647fb9aa713ac725d2792f4c43d78e
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/e824a30b76e33042cb6e15d9bed6bf20
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/73c218154269b5cf9873a41b45600fb8
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/e824a30b76e33042cb6e15d9bed6bf20
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/9f8d0e090a9d6b90588015126d9faf18
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/9f8d0e090a9d6b90588015126d9faf18
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/e824a30b76e33042cb6e15d9bed6bf20
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/9f8d0e090a9d6b90588015126d9faf18
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/e824a30b76e33042cb6e15d9bed6bf20
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/0 [!]
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/priajv.class
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/priajv.class
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/1 [!]
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/2
- 14:10 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/3 [!]
- 14:11 - b5f1d7d.01c.26.f2.05a8.648d81f.8d4b5.ac.eydiwptf.reluctantrid[.]in - GET /cf9deeb331dc8c76f3df25a2325732e3/4 [!]
NOTE: [!] shows where a malware payload was returned. I only recovered 3 of the 4 payloads in the second run.
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT (CVE-2014-0515):
File name: 2014-08-15-Magnitude-EK-flash-exploit.swf
File size: 5,334 bytes
MD5 hash: a25806d43e0eeb62e98fadc32cc18320
Detection ratio: 3 / 54
First submission: 2014-08-15 14:42:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/a5fb9f7882b2153945e62100f5d541d1bda2c28d6a46bbe9c64f4c9374a7f5b9/analysis/
JAVA EXPLOIT:
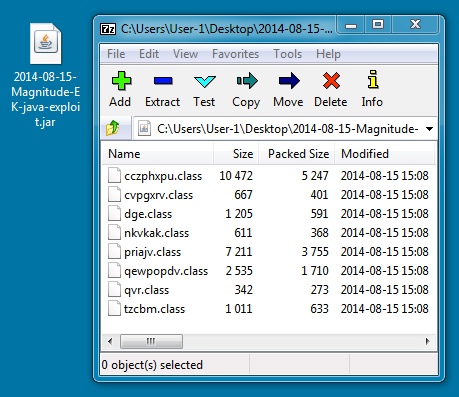
File name: 2014-08-15-Magnitude-EK-java-exploit.jar
File size: 13,932 bytes
MD5 hash: f4ab6fb1991af2ed3d97663757f018ab
Detection ratio: 2 / 54
First submission: 2014-08-15 14:43:12 UTC
VirusTotal link: https://www.virustotal.com/en/file/c81a53e9f8491d35cdee980546baba4a94af0cd7aaaf79cf4f6feafebe03474c/analysis/
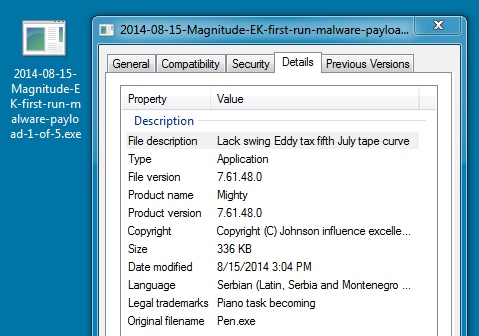
FIRST RUN MALWARE PAYLOAD 1 OF 5:
File name: 2014-08-15-Magnitude-EK-first-run-malware-payload-1-of-5.exe
File size: 344,108 bytes
MD5 hash: 0f3108797ea57a411efc35c836a0cd8a
Detection ratio: 2 / 54
First submission: 2014-08-15 14:43:41 UTC
VirusTotal link: https://www.virustotal.com/en/file/c59581f629a1d4ea1ba890808b894c3bc27c69b0c1ffa103638979b5a1d94d58/analysis/
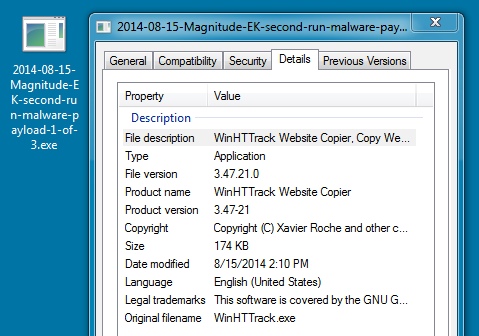
FIRST RUN MALWARE PAYLOAD 2 OF 5 (ALSO SECOND RUN 2 OF 3):
File name: 2014-08-15-Magnitude-EK-first-run-malware-payload-2-of-5.exe
File name: 2014-08-15-Magnitude-EK-second-run-malware-payload-2-of-3.exe
File size: 401,408 bytes
MD5 hash: cb979cd2b04c9495e5acc1d07a6dda6b
Detection ratio: 4 / 53
First submission: 2014-08-15 14:43:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/562f7a5d993d4d4015ba596218418c08e38be747b35950853b950b22ad7dd7f2/analysis/
FIRST RUN MALWARE PAYLOAD 3 OF 5 (ALSO SECOND RUN 3 OF 3) - ZEMOT:
File name: 2014-08-15-Magnitude-EK-first-run-malware-payload-3-of-5.exe
File name: 2014-08-15-Magnitude-EK-second-run-malware-payload-3-of-3.exe
File size: 98,304 bytes
MD5 hash: 3661b4d7267372471e9ff775d85a805d
Detection ratio: 12 / 54
First submission: 2014-08-15 14:45:22 UTC
VirusTotal link: https://www.virustotal.com/en/file/f77b875e6b8fd507605db6e0fdb28f8680a7068dca1670aee7d2cec313341221/analysis/
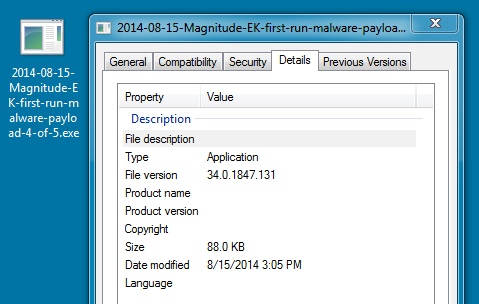
FIRST RUN MALWARE PAYLOAD 4 OF 5:
File name: 2014-08-15-Magnitude-EK-first-run-malware-payload-4-of-5.exe
File size: 90,112 bytes
MD5 hash: 719f257f40dccecbf8536714f12321a1
Detection ratio: 12 / 54
First submission: 2014-08-15 14:45:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/9e1e5defa192a7d125c8bba0be8a3ca887e9327db16a47fd562804bdbc34ca5d/analysis/
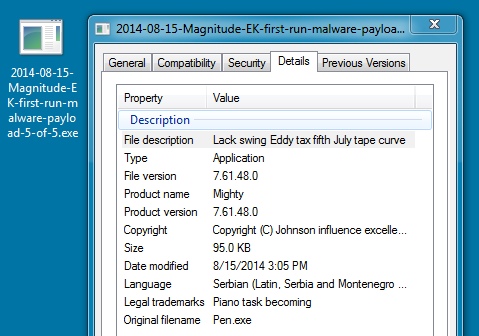
FIRST RUN MALWARE PAYLOAD 5 OF 5:
File name: 2014-08-15-Magnitude-EK-first-run-malware-payload-5-of-5.exe
File size: 97,280 bytes
MD5 hash: 45b815baa2e4585555436160b679cd87
Detection ratio: 3 / 54
First submission: 2014-08-15 14:45:54 UTC
VirusTotal link: https://www.virustotal.com/en/file/bb57bb6bd2a4824f26d2e173ba3a7e8f4f4f2ae92e6595e32842ec87d5ab36fb/analysis/
SECOND RUN MALWARE PAYLOAD 1 OF 3 - CRYPTOWALL:
File name: 2014-08-15-Magnitude-EK-second-run-malware-payload-1-of-3.exe
File size: 178,688 bytes
MD5 hash: 24ba0b21f3dd12f542c55670dba65c47
Detection ratio: 21 / 54
First submission: 2014-08-15 05:17:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/76dbc0b33a6431dce56b3b81b7815eb6620bae9ee0cd28a6f58f0596c28e74b4/analysis/
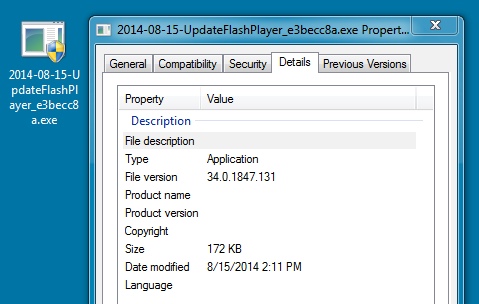
RERDOM MALWARE FOUND IN APPDATA\LOCAL\TEMP DIRECTORY:
File name: 2014-08-15-UpdateFlashPlayer_e3becc8a.exe
File size: 176,128 bytes
MD5 hash: 3e8696df786c549d0e3c287b262e11eb
Detection ratio: 4 / 53
First submission: 2014-08-15 14:48:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/dadbc9d67b3f128fe829026a5abcbb1d20e31df69af1fb56bf1a5f1353881730/analysis/
ALERTS FROM FIRST RUN (IE 8)
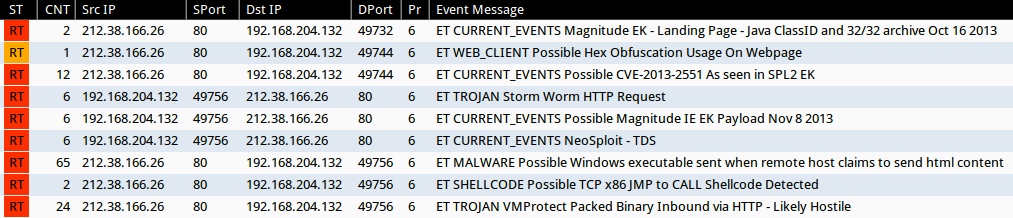
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013 (sid:2017602)
- 212.38.166[.]26:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK (sid:2017849)
- 212.38.166[.]26:80 - ET TROJAN Storm Worm HTTP Request (sid:2006411)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Possible Magnitude IE EK Payload Nov 8 2013 (sid:2017694)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS NeoSploit - TDS (sid:2015665)
- 212.38.166[.]26:80 - ET MALWARE Possible Windows executable sent when remote host claims to send html content (sid:2009897)
- 212.38.166[.]26:80 - ET SHELLCODE Possible TCP x86 JMP to CALL Shellcode Detected (sid:2011803)
- 212.38.166[.]26:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 13:54:34 UTC - 212.38.166[.]26:80 - [1:26653:4] EXPLOIT-KIT Multiple exploit kit landing page - specific structure
- 13:54:34 UTC - 212.38.166[.]26:80 - [1:30766:1] EXPLOIT-KIT Magnitude exploit kit landing page
- 13:54:37 UTC - 212.38.166[.]26:80 - [1:29189:1] EXPLOIT-KIT Magnitude exploit kit Microsoft Internet Explorer Payload request (x6)
- 13:54:37 UTC - 212.38.166[.]26:80 - [1:17276:15] FILE-OTHER Multiple vendor Antivirus magic byte detection evasion attempt (x5)
- 13:54:37 UTC - 212.38.166[.]26:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download (x5)
- 13:54:37 UTC - 212.38.166[.]26:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x5)
ALERTS FROM SECOND RUN (IE 10)
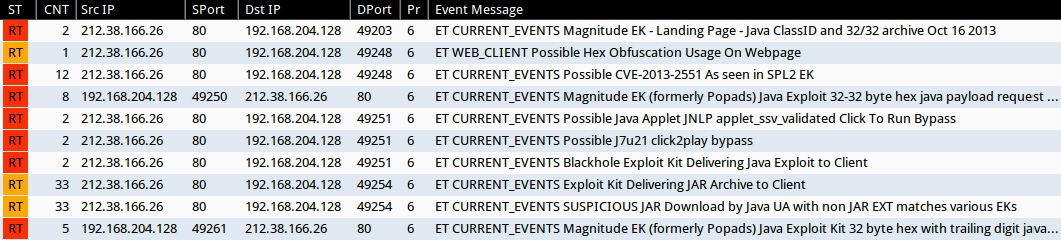
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013 (sid:2017602)
- 212.38.166[.]26:80 - ET WEB_CLIENT Possible Hex Obfuscation Usage On Webpage (sid:2012119)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK (sid:2017849)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013 (sid:2017603)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass (sid:2016797)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass (sid:2017509)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Java Exploit to Client (sid:2013961)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs (sid:2016540)
- 212.38.166[.]26:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit Kit 32 byte hex with trailing digit java payload request (sid:2015888)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 14:09:44 UTC - 212.38.166[.]26:80 - [1:26653:4] EXPLOIT-KIT Multiple exploit kit landing page - specific structure
- 14:09:44 UTC - 212.38.166[.]26:80 - [1:30766:1] EXPLOIT-KIT Magnitude exploit kit landing page
- 14:10:04 UTC - 212.38.166[.]26:80 - [1:30768:1] EXPLOIT-KIT Magnitude exploit kit Oracle Java payload request (x13)
- 14:10:08 UTC - 212.38.166[.]26:80 - [1:26524:5] BROWSER-PLUGINS Java security warning bypass through JWS attempt
- 14:10:17 UTC - 212.38.166[.]26:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt (x3)
ZEMOT INFECTION TRAFFIC
MALWARE:
File name: 2014-08-15-Magnitude-EK-first-run-malware-payload-3-of-5.exe
File name: 2014-08-15-Magnitude-EK-second-run-malware-payload-3-of-3.exe
MD5 hash: 3661b4d7267372471e9ff775d85a805d
VirusTotal link: https://www.virustotal.com/en/file/f77b875e6b8fd507605db6e0fdb28f8680a7068dca1670aee7d2cec313341221/analysis/
INFECTION TRAFFIC:
- 14:11:05 UTC - 46.119.105[.]213:80 - raing-gerut[.]su - GET /b/shoe/749634
- 14:11:07 UTC - 178.74.212[.]207:80 - dients-lihuret[.]su - GET /mod_articles-login-llget9/jquery/ [!]
- 14:11:12 UTC - 178.74.212[.]207:80 - dients-lihuret[.]su - GET /mod_articles-login-llget9/jquery/ [!]
- 14:11:33 UTC - 178.74.212[.]207:80 - dients-lihuret[.]su - GET /mod_articles-login-llget9/jquery/ [!]
- 14:14:05 UTC - 37.229.189[.]208:80 - dients-lihuret[.]su - GET /mod_jshoppi-authssd5/soft64.dll
- 14:14:15 UTC - 134.249.11[.]2:80 - triple-bow[.]su - GET /b/eve/6d35b731d8e445a0f044de3f
- 14:15:27 UTC - 195.114.145[.]69:80 - triple-bow[.]su - POST /b/opt/AD19F51F54C9C7BBE118352A
- 14:15:27 UTC - 195.114.145[.]69:80 - triple-bow[.]su - GET /b/letr/493189686B4811B4DE99E325
- 14:15:28 UTC - 31.192.209[.]57:8080 - 31.192.209[.]57:8080 - POST /b/opt/1468F3281BD3F125AE0203B4
- 14:15:29 UTC - 31.192.209[.]57:8080 - 31.192.209[.]57:8080 - GET /b/letr/AC82485B52C6EB38E71719A9
- 14:15:29 UTC - 173.255.241[.]19:8080 - 173.255.241[.]19:8080 - POST /b/opt/3C69EB349618209923C9D208
- 14:15:30 UTC - 173.255.241[.]19:8080 - 173.255.241[.]19:8080 - POST /b/opt/FB219725228DDE9F975C2C0E
NOTE: [!] is where the follow-up Rerdom malware was downloaded.
ALERTS:
- ET TROJAN Win32/Zemot Checkin (sid:2018643)
- ET TROJAN Win32/Zemot Checkin (sid:2018644)
- ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:2018572)
- ET CURRENT_EVENTS Nuclear Exploit Kit exe.exe Payload (sid:2018914)
- ET TROJAN Win32/Zemot Config Download (sid:2018661)
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
- [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection
- [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection
- [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
CRYPTOWALL INFECTION TRAFFIC
MALWARE:
File name: 2014-08-15-Magnitude-EK-second-run-malware-payload-1-of-3.exe
MD5 hash: 24ba0b21f3dd12f542c55670dba65c47
VirusTotal link: https://www.virustotal.com/en/file/76dbc0b33a6431dce56b3b81b7815eb6620bae9ee0cd28a6f58f0596c28e74b4/analysis/
INFECTION TRAFFIC:
- 194.58.101[.]222 - dancewithmeseniorita[.]com
- 38.229.70[.]4 - kpai7ycr7jxqkilp.tor2web[.]org
- 194.58.101[.]195 - kpai7ycr7jxqkilp.totortoweb[.]com
ALERTS:
- ET TROJAN CryptoWall Check-in (sid:2018452)
- ET TROJAN Likely CryptoWall .onion Proxy DNS lookup (sid:2018609)
- ET CURRENT_EVENTS DNS Query to tor2web Domain (.onion proxy) (sid:2015576)
- ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (1) (sid:2016806)
- ET TROJAN Likely CryptoWall .onion Proxy domain in SNI (sid 2018610)
- [1:31450:1] MALWARE-CNC Win.Trojan.CryptoWall outbound connection attempt
- [1:31014:2] MALWARE-CNC Win.Trojan.Goon outbound communication
Bitcoin account for ransom payment: 14ytdF3C9VRbttMfh9J56yR9ZWqfmFbBWN
Click here to return to the main page.