2014-09-01 - POSSIBLE ZEUS MALWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-01-infection-traffic-by-malware-from-email-attachment.pcap.zip
- 2014-09-01-malware-from-email-attachment.zip
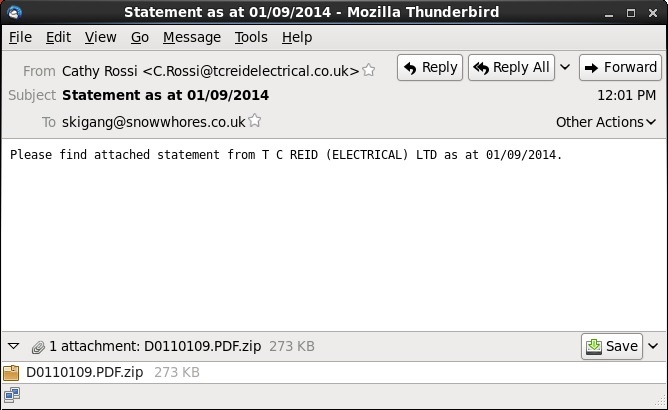
PHISHING EMAIL
SCREENSHOT:
MESSAGE TEXT:
Date: Mon, 01 Sep 2014 12:01:01 UTC
From: Cathy Rossi <C.Rossi@tcreidelectrical[.]co[.]uk>
To: skigang@snowwhores[.]co[.]uk
Subject: Statement as at 01/09/2014
Please find attached statement from T C REID (ELECTRICAL) LTD as at 01/09/2014.
Attachment: D0110109.PDF.zip (273 KB)
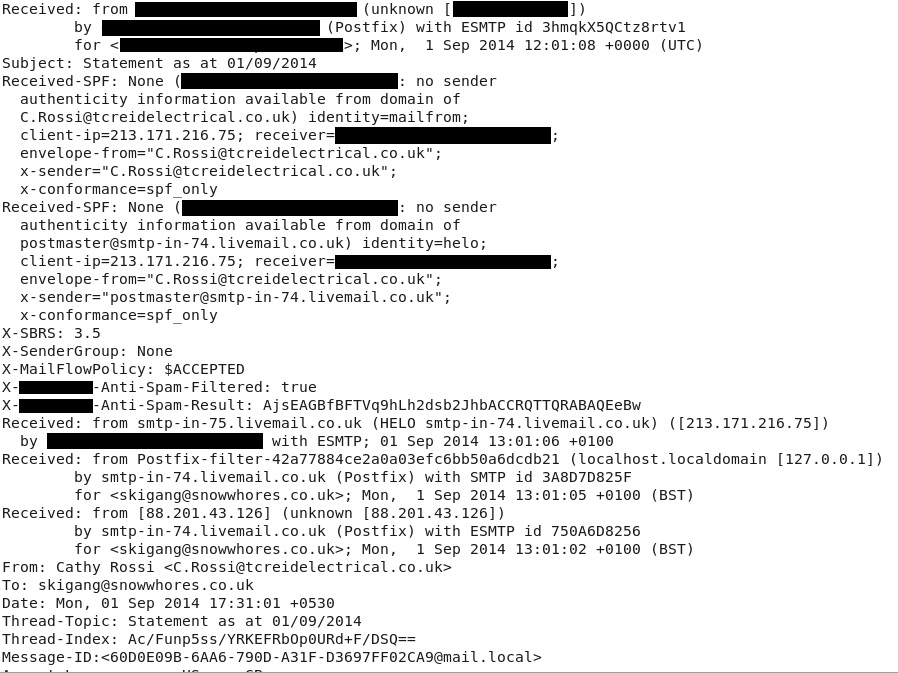
EMAIL HEADERS:
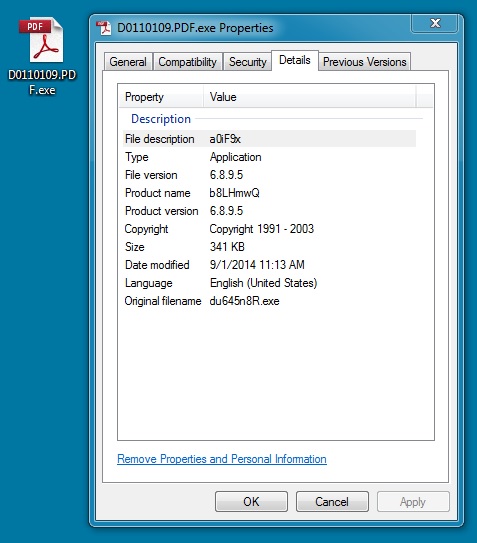
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
File name: D0110109.PDF.zip
File size: 279,827 bytes
MD5 hash: b95728c4d8edd9ad604c468ed2cc3810
Detection ratio: 18 / 55
First submission: 2014-09-01 11:27:25 UTC
VirusTotal link: https://www.virustotal.com/en/file/2203dc77f69ff84e439fb16b8d14b47fc9a5cfe3a6fa247b93dd72174db8920c/analysis/
File name: D0110109.PDF.exe
File size: 349,334 bytes
MD5 hash: 13d33a9ff6c77a3b7d08a4557d0a5e67
Detection ratio: 13 / 55
First submission: 2014-09-01 11:28:44 UTC
VirusTotal link: https://www.virustotal.com/en/file/dd96f70183fd6f9482243e04b02a75c66040bafa64f612aebc99b4302709f1d7/analysis/
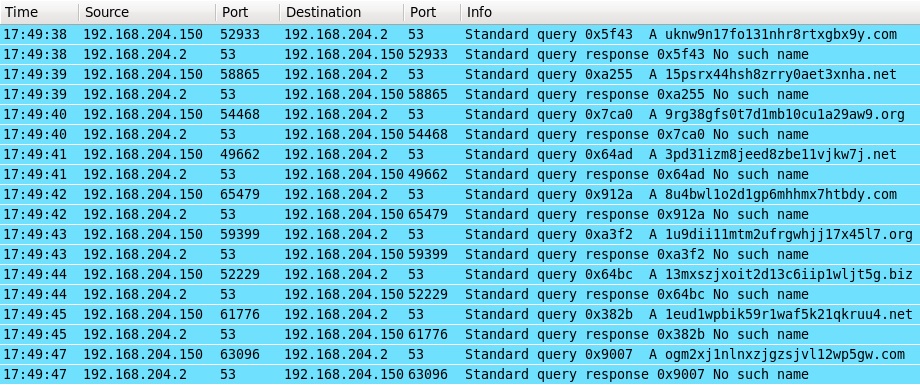
INFECTION TRAFFIC
FROM INFECTED VM:
Saw repeated Zeus-related DGA DNS requests, but no actual traffic from the infected VM.
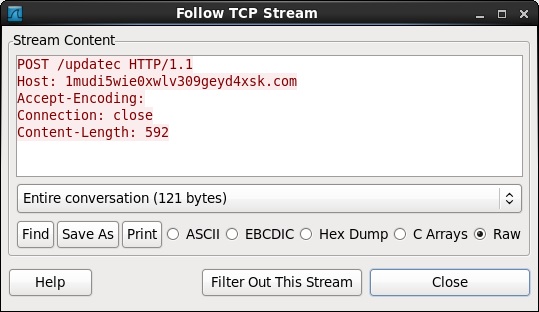
A sandbox analysis shows the HTTP POST requests, if the domains had actually resolved to an IP address:
POST /updatec HTTP/1.1
Host: 1mudi5wie0xwlv309geyd4xsk[.]com
Accept-Encoding:
Connection: close
Content-Length: 592
ALERTS FROM INFECTED VM (ONLY DNS QUERIES AND NO HTTP TRAFFIC)
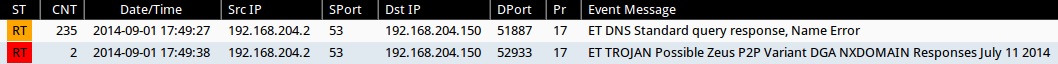
Emerging Threats and ETPRO rulesets from Sguil on Security Onion:
- ET DNS Standard query response, Name Error (sid:2001117)
- ET TROJAN Possible Zeus P2P? Variant DGA NXDOMAIN Responses July 11 2014 (sid:2018666)
Click here to return to the main page.