2014-09-05 - SWEET ORANGE EK FROM 8.28.175[.]69 - NASHVILLE.LOCKMANENTERPRISES[.]NET:9290 & NATIONAL.LOCKMANENTERPRISES[.]ORG:9290
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This Sweet Orange EK example is not the same group who uses jquery_datepicker redirects and sends Qbot malware.
- Today's malvertizing-style infection chain usually point to Nuclear EK, so I was surprised to see Sweet Orange EK appear.
- The malware payload is a Zemot downloader that called for Rerdom.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 208.100.48[.]45 - www.centralpark[.]com - Original website
- 208.100.48[.]44 - ads.centralpark[.]com - Malicious ad traffic
- 50.7.108[.]162 - saw.piroscia[.]com - Redirect
- 8.28.175[.]69 - nashville.lockmanenterprises[.]net:9290 and national.LOCKMANENTERPRISES[.]ORG:9290 - Sweet Orange EK
- 65.34.68[.]192 - jufer-muirer[.]su - Post-infection traffic
- 109.251.107[.]244 - quret-huler[.]su - Post-infection traffic
ORIGINAL WEBSITE AND REDIRECT CHAIN:
- 2014-09-05 15:00:36 UTC - 208.100.48[.]45:80 - www.centralpark[.]com - GET /
- 2014-09-05 15:00:37 UTC - 208.100.48[.]44:80 - ads.centralpark[.]com - GET /www/delivery/ajs.php?zoneid=30&blockcampaign=1&cb=
61215276831&charset=utf-8&loc=http%3A//www.centralpark[.]com/&referer=http%3A//www.bing[.]com/search%3Fq%3Dwww.+centralpark+[.]com%26qs%3Dn%26
form%3DQBLH%26pq%3Dwww.+centralpark+[.]com%26sc%3D0-0%26sp%3D-1%26sk%3D%26cvid%3D8a9a52f2ae934a08bceaa6f3e3ec9219 - 2014-09-05 15:00:37 UTC - 50.7.108[.]162:80 - saw.piroscia[.]com - GET /js/ads/show_ads.js?ver=3
SWEET ORANGE EK:
- 2014-09-05 15:00:38 UTC - 8.28.175[.]69:9290 - nashville.lockmanenterprises[.]net:9290 - GET /redesign/wifi.php?styles=343
- 2014-09-05 15:00:38 UTC - 8.28.175[.]69:9290 - nashville.lockmanenterprises[.]net:9290 - GET /redesign/riOthW
- 2014-09-05 15:01:04 UTC - 8.28.175[.]69:9290 - national.LOCKMANENTERPRISES[.]ORG:9290 - GET /style.php?exec=129
- 2014-09-05 15:01:24 UTC - 8.28.175[.]69:9290 - nashville.lockmanenterprises[.]net:9290 - GET /redesign/agEviyR.jar
- 2014-09-05 15:01:24 UTC - 8.28.175[.]69:9290 - nashville.lockmanenterprises[.]net:9290 - GET /redesign/vqJZsPcG.jar
- 2014-09-05 15:01:24 UTC - 8.28.175[.]69:9290 - nashville.lockmanenterprises[.]net:9290 - GET /redesign/vqJZsPcG.jar
- 2014-09-05 15:01:24 UTC - 8.28.175[.]69:9290 - nashville.lockmanenterprises[.]net:9290 - GET /redesign/vqJZsPcG.jar
- 2014-09-05 15:01:24 UTC - 8.28.175[.]69:9290 - nashville.lockmanenterprises[.]net:9290 - GET /redesign/vqJZsPcG.jar
- 2014-09-05 15:01:24 UTC - 8.28.175[.]69:9290 - nashville.lockmanenterprises[.]net:9290 - GET /redesign/vqJZsPcG.jar
POST-INFECTION TRAFFIC:
- 2014-09-05 15:01:11 UTC - 65.34.68[.]192:80 - jufer-muirer[.]su - GET /b/shoe/1480
- 2014-09-05 15:01:14 UTC - 109.251.107[.]244:80 - quret-huler[.]su - GET /mod_articles-authl9.12/jquery/ [repeats several times]
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-05-Sweet-Orange-EK-flash-exploit.swf
File size: 5,156 bytes
MD5 hash: 543632124be9b7488f53167db1cb197c
Detection ratio: 4 / 54
First submission: 2014-09-04 13:54:55 UTC
VirusTotal link: https://www.virustotal.com/en/file/5fdaa4db0c66fe58c44dc66606c0db4271990bc3c5d6375d3b4476000cb22d6b/analysis/
MALWARE PAYLOAD:
File name: 2014-09-05-Sweet-Orange-EK-malware-payload.exe
File size: 174,963 bytes
MD5 hash: 470c1821d66be597a0426c704bfa0769
Detection ratio: 1 / 55
First submission: 2014-09-05 16:10:19 UTC
VirusTotal link: https://www.virustotal.com/en/file/497ee10ac654ba43bd1a44652460bb3d132822e279ca75c8856aed08361629b7/analysis/
ALERTS
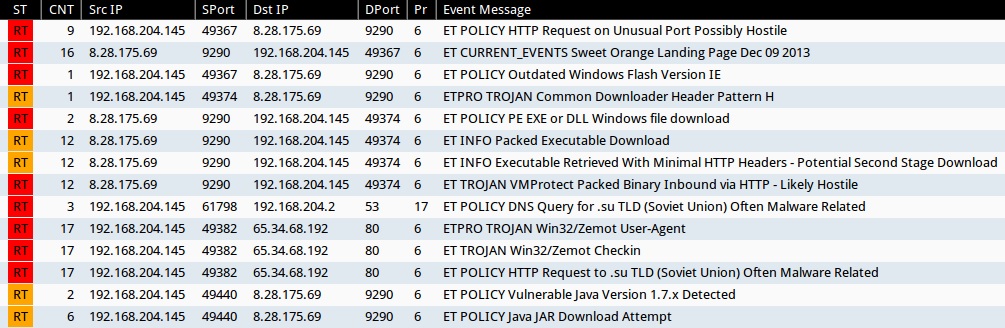
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 8.28.175[.]69:9290 - ET CURRENT_EVENTS Sweet Orange Landing Page Dec 09 2013 (sid:2017817)
- 8.28.175[.]69:9290 - ETPRO TROJAN Common Downloader Header Pattern H (sid:2803305)
- 8.28.175[.]69:9290 - ET TROJAN VMProtect Packed Binary Inbound via HTTP - Likely Hostile (sid:2009080)
- 65.34.68[.]192:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 65.34.68[.]192:80 - ET TROJAN Win32/Zemot Checkin (sid:2018643 and 2018644)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS:
- 2014-09-05 15:00:38 UTC - 8.28.175[.]69:9290 - [120:6:1] (http_inspect) HTTP RESPONSE GZIP DECOMPRESSION FAILED
- 2014-09-05 15:01:05 UTC - 8.28.175[.]69:9290 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-09-05 15:01:05 UTC - 8.28.175[.]69:9290 - [1:23256:5] FILE-EXECUTABLE Armadillo v1.71 packer file magic detected
- 2014-09-05 15:01:05 UTC - 8.28.175[.]69:9290 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 2014-09-05 15:01:10 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 15:01:12 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
- 2014-09-05 15:01:13 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query
Click here to return to the main page.