2014-09-17 - MALWARE INFECTION FROM EMAIL LINK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-09-17-phishing-email-tracking.csv.zip
- 2014-09-17-phishing-malware-sandbox-analysis.pcap.zip
- 2014-09-17-infection-traffic-on-a-VM.pcap.zip
- 2014-09-17-malware-and-artifacts.zip
NOTES:
- Today's example came from a mail server registered to Oracle--I included a text file with header lines showing where this email supposedly came from.
- This particular campaign feels like it's from the Asprox botnet, but I could be wrong.
Emails from this campaign so far today.
EXAMPLE OF THE EMAILS
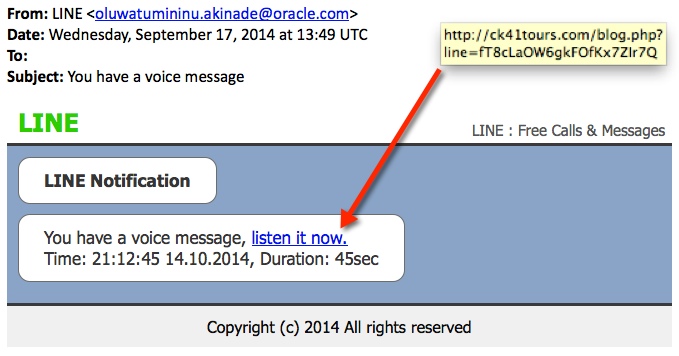
SCREENSHOT:
MESSAGE TEXT:
From: LINE <oluwatumininu.akinade@oracle[.]com>
Date: Wednesday, September 17, 2014 at 13:49 UTC
To:
Subject: You have a voice message
LINE
LINE : Free Calls & Messages
LINE Notification You have a voice message, listen it now.
Time: 21:12:45 14.10.2014, Duration: 45sec
Copyright (c) 2014 All rights reserved
HTTP REQUEST THAT DOWNLOADED THE MALWARE:
- 2014-09-17 14:34 UTC - 27.254.96[.]21 - ck41tours[.]com - GET /blog.php?line=fT8cLaOW6gkFOfKx7ZIr7Q
PRELIMINARY MALWARE ANALYSIS
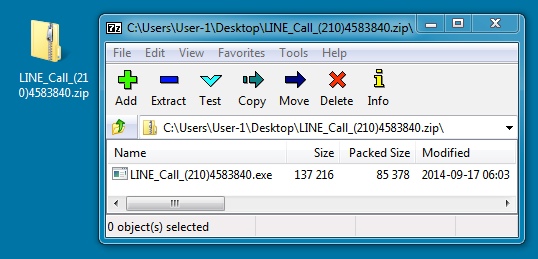
ZIP ARCHIVE DOWNLOADED FROM LINK IN EMAIL:
File name: LINE_Call_(210)4583840.zip
File size: 85,528 bytes
MD5 hash: 07d51f610538b0f225a32acd49d2cfdb
Detection ratio: 15 / 54
First submission: 2014-09-17 20:27:40 UTC
VirusTotal link: https://www.virustotal.com/en/file/1cb21dc352b36bca0facffcbb63ca7355532f65ebb393af9fc9403f8d96d9f1e/analysis/
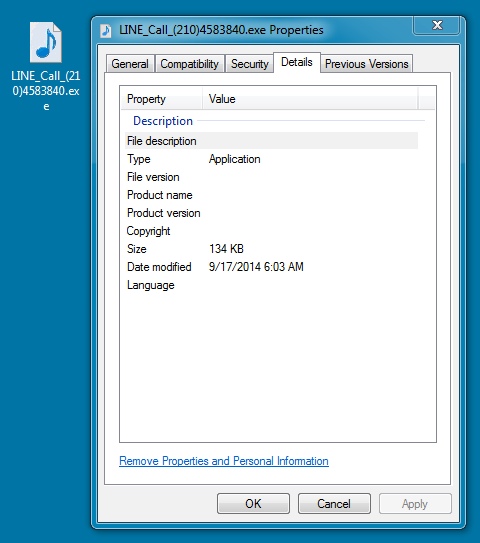
EXTRACTED MALWARE:
File name: LINE_Call_(210)4583840.exe
File size: 137,216 bytes
MD5 hash: 1b2339a1be6d8587816ad632b71e1eaf
Detection ratio: 14 / 55
First submission: 2014-09-17 14:24:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/7e2125c9df781020a45e653baf3355ae2aadf76c9da5228370ff961ab34174cd/analysis/
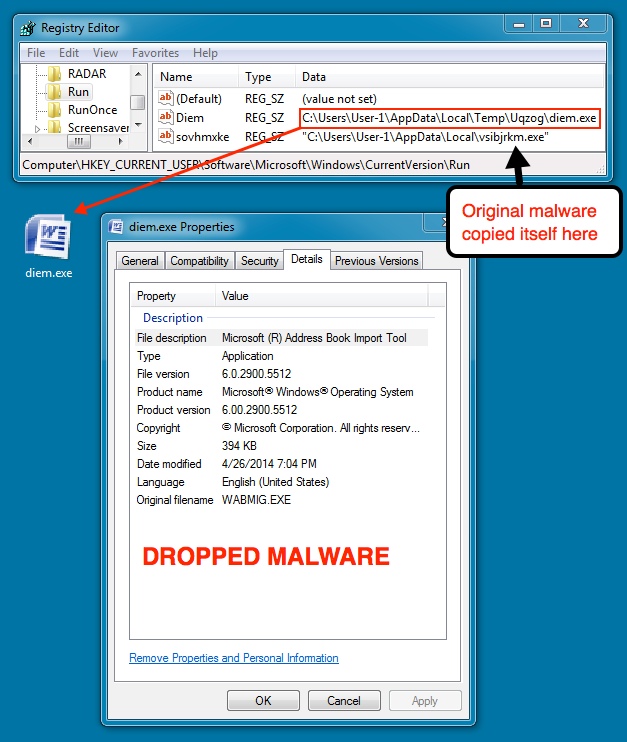
DROPPED FILE WHEN EXECUTING MALWARE ON A VM:
File name: diem.exe
File size: 403,968 bytes
MD5 hash: cde53f22d8d79a1c4627dbed7b3614b8
Detection ratio: 11 / 52
First submission: 2014-09-17 20:58:05 UTC
VirusTotal link: https://www.virustotal.com/en/file/bfceabb1a3677800e58944899385d40f6edaf8a16bb0c2a4580fba69c09ad983/analysis/
SANDBOX TRAFFIC
FROM SANDBOX ANALYSIS OF THE MALWARE:
- 50.115.169[.]26 port 8090 - POST /index.php
- 58.83.159[.]94 port 443 - POST /index.php
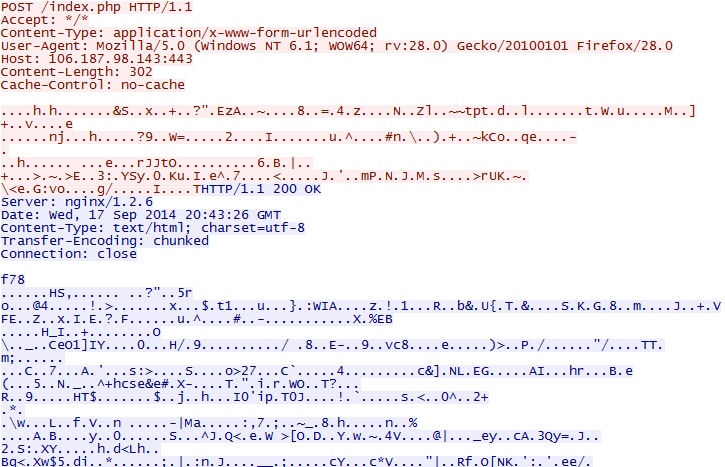
- 106.187.98[.]143 port 443 - POST /index.php
- 107.170.127[.]51 port 8080 - POST /index.php
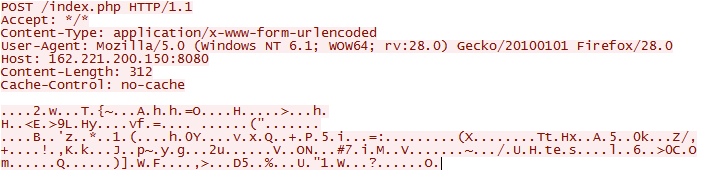
- 162.221.200[.]150 port 8080 - POST /index.php
- 184.107.222[.]130 port 8080 - POST /index.php
- 194.110.192[.]173 port 8080 - POST /index.php
- 206.183.111[.]208 port 8080 - POST /index.php
- 210.56.29[.]156 port 443 - POST /index.php
- 218.244.137[.]152 port 443 - POST /index.php
Example of the HTTP POST requests from the sandbox analysis.
INFECTED VM TRAFFIC
Running the malware on a VM generated DNS queries for warzine[.]su which was not seen in the sandbox analysis. It also received about 355 KB of data from 106.187.98[.]143 port 443 and dropped malware on the VM.
HTTP REQUESTS BY THE INFECTED VM:
- 20:44:23 UTC - 206.183.111[.]208:8080 - POST /index.php
- 20:44:24 UTC - 206.183.111[.]208:8080 - POST /index.php
- 30:44:26 UTC - 106.187.98[.]143:443 - POST /index.php
- 20:46:33 UTC - 106.187.98[.]143:443 - POST /index.php
DGA-STYLE DNS QUERIES FROM THE INFECTED VM:
- 13n2m4yotu7k3qy423bm0upo[.]net
- 17qjk1cwgfica14mugbq1y8zt4k[.]com
- 182g1q7tb9zkv1a2iv6zk9upep[.]net
- 18j5he41yqxw9q13mb8k21r5aakv[.]net
- 191qb6qwet9ic19x3cfz4vtnmh[.]org
- 19kyvp61l507js7pyes5gxb2pb[.]biz
- 1aghdssnqohcx100lmb310ad7p5[.]biz
- 1g2wa2mu5zczu1j0zxvx69hz8x[.]com
- 1mjtex4ouasyk1bbgp7y1rk5b8d[.]biz
- 1qhw0a8175bmth1ugrtot1esrl8u[.]net
- 1wm9t8i15y91le12bjlwl1qpoi6h[.]org
- 1xq2eaf1gb6o5d189t9hffbea1d[.]com
- 3388zltj0y8x9w709u1emaiwi[.]org
- 47gxpd1unfwx92sfpk2st34cu[.]com
- 63219bvih7zx1wvt1gh6gzdvk[.]net
- a5hko0egqhppxlhb9o1vjms8f[.]com
- yx0l1x1sdqm631bzlcgdnv0qg[.]org
- yy7kjm1kqk7tek78f5f13xmr3m[.]net
Click here to return to the main page.