2014-10-01 - CRYPTOWALL 2.0 RANSOMWARE INFECTION FROM FAKE IRS EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2014-10-01-CryptoWall-2.0-ransomware-infection-on-a-VM.pcap.zip
- 2014-10-01-CryptoWall-2.0-ransomware-infection-from-sandbox-analysis.pcap.zip
- 2014-10-01-CryptoWall-2.0-ransomware-sample.zip
NOTES:
- 564 kB of encrypted data was downloaded by the malware. That might be the actual CryptoWall ransomware, but I couldn't find any dropped files related to that on the infected VM.
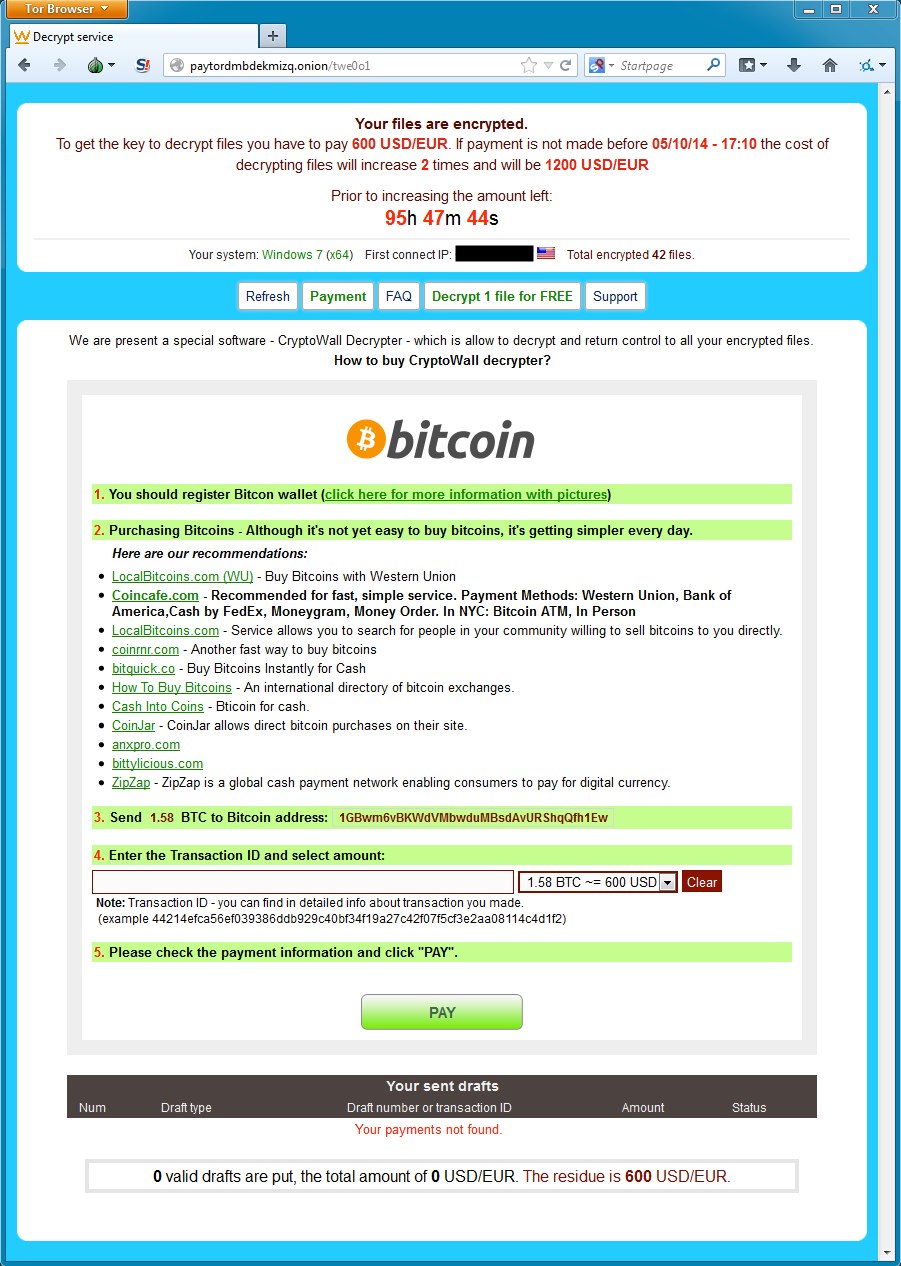
- The BitCoin address for the ransom payment is: 1GBwm6vBKWdVMbwduMBsdAvURShqQfh1Ew
- I can't remember any previous CryptoWall ransomware example calling itself "CryptoWall 2.0" as seen in today's VM infection:
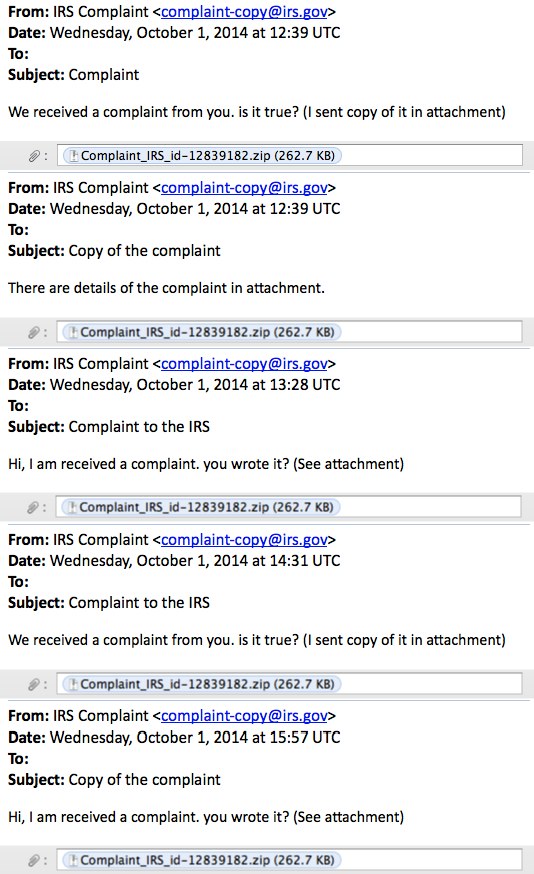
EXAMPLE OF THE EMAILS
SCREENSHOTS:
MESSAGE TEXT:
Received: from static.vdc.vn (static.vdc[.]vn [113.161.198[.]196] (may be forged))From: IRS Complaint <complaint-copy@irs[.]gov>
Date: Wednesday, October 1, 2014 at 12:39 UTC
To:
Subject: Complaint
We received a complaint from you. is it true? (I sent copy of it in attachment)
Received: from HZYZBRWYXN ([114.203.105[.]188])From: IRS Complaint <complaint-copy@irs[.]gov>
Date: Wednesday, October 1, 2014 at 12:39 UTC
To:
Subject: Copy of the complaint
There are details of the complaint in attachment.
Received: from ([81.137.205[.]62])
From: IRS Complaint <complaint-copy@irs[.]gov>
Date: Wednesday, October 1, 2014 at 13:28 UTC
To:
Subject: Complaint to the IRS
Hi, I am received a complaint. you wrote it? (See attachment)
Received: from QHYCGGETN ([72.54.201[.]18])
From: IRS Complaint <complaint-copy@irs[.]gov>
Date: Wednesday, October 1, 2014 at 14:31 UTC
To:
Subject: Complaint to the IRS
We received a complaint from you. is it true? (I sent copy of it in attachment)
Received: from rrcs-67-78-159-70.se.biz.rr[.]com (67.78.159[.]70)From: IRS Complaint <complaint-copy@irs[.]gov>
Date: Wednesday, October 1, 2014 at 15:57 UTC
To:
Subject: Copy of the complaint
Hi, I am received a complaint. you wrote it? (See attachment)
PRELIMINARY MALWARE ANALYSIS
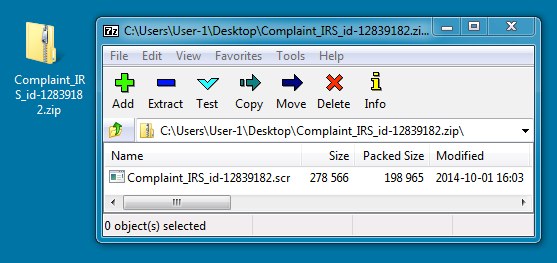
EMAIL ATTACHMENT:
File name: Complaint_IRS_id-12839182.zip
File size: 199,121 bytes
MD5 hash: ea4df0aa8ed7ac496482480da3ac8608
Detection ratio: 22 / 54
First submission: 2014-10-01 12:14:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/7293fa4fcba16746926947d6262f9e43cd87cc52a21a0d9a5c5e96d33a4dd2e2/analysis/
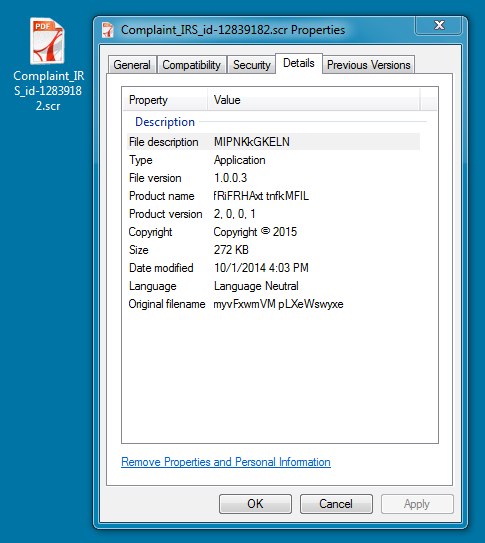
EXTRACTED MALWARE:
File name: Complaint_IRS_id-12839182.scr
File size: 278,566 bytes
MD5 hash: 31c2d25d7d0d0a175d4e59d0b3b2ec94
Detection ratio: 17 / 55
First submission: 2014-10-01 12:17:50 UTC
VirusTotal link: https://www.virustotal.com/en/file/a0454c319093a3c5e4ce84569de9a680aa4028c208f9607880967d43f3b22666/analysis/
SCREENSHOTS AND INFO FROM THE TRAFFIC
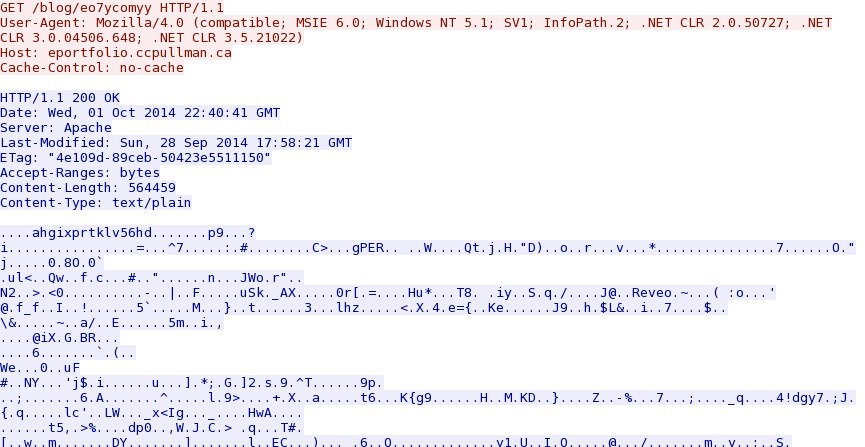
Sandbox analysis: 2014-10-01 22:09:34 UTC - 65.19.161[.]34 port 80 - eportfolio.ccpullman[.]ca - GET /blog/eo7ycomyy
No event triggered on this line for VRT, ET, or ETPRO signatures (that I could tell)
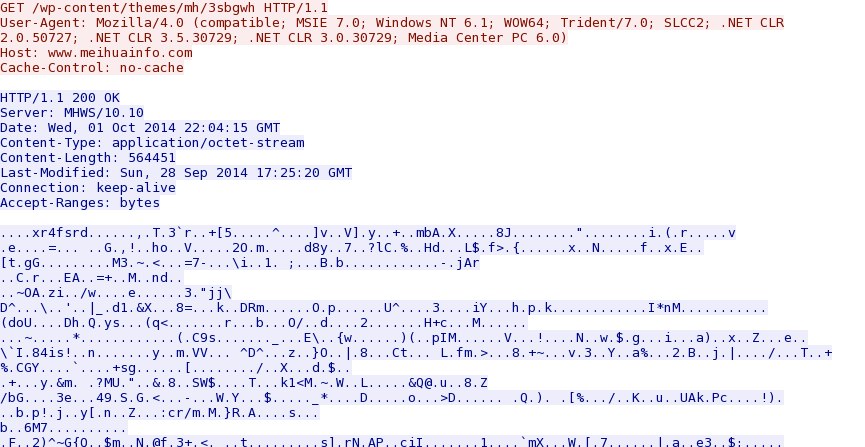
From my infected VM pcap: 2014-10-01 22:07:48 UTC - 42.62.40[.]145 port 80 - www.meihuainfo[.]com - GET /wp-content/themes/mh/3sbgwh
Triggered rule: ET TROJAN Unknown Locker DL URI Struct Jul 25 2014 (sid:2018787)
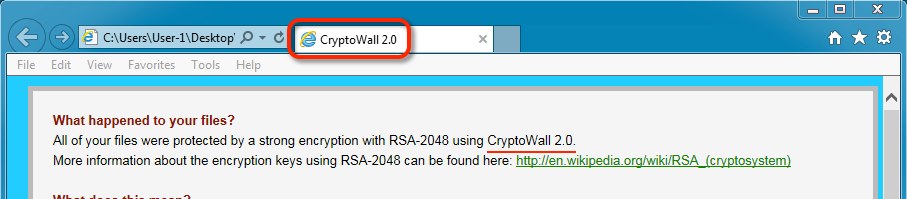
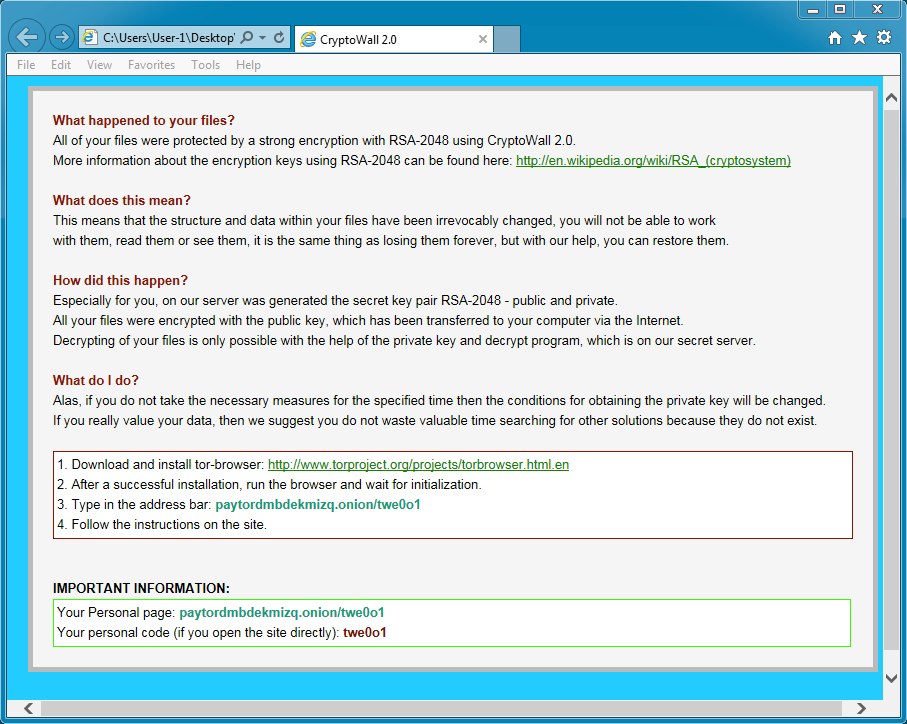
Decrypt instructions (specifying this is CryptoWall 2.0):
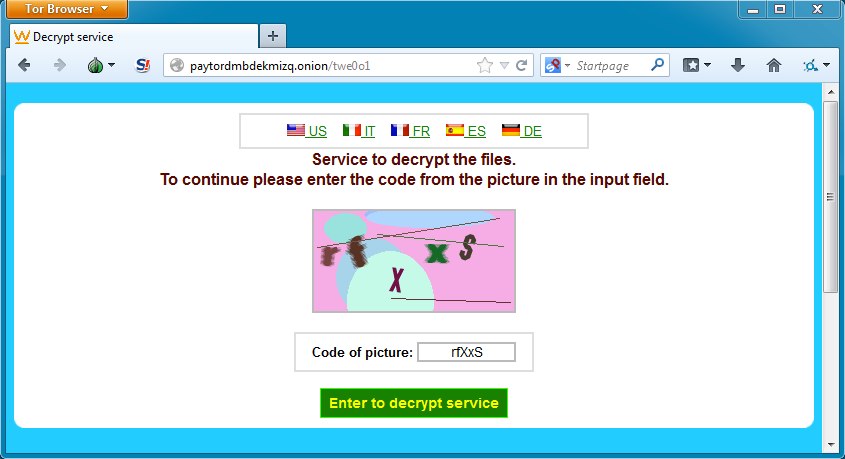
After installing a tor browser, I got the captcha for the decrypt service:
Which takes us to the ransom payment page:
Click here to return to the main page.